Certified in Planning and Inventory Management (CPIM 8.0) Questions and Answers
Which of the following BEST describes web service security conformance testing as it relates to web services security testing?
Which authentication method is used by an email server to verify that a sender’s Internet Protocol (IP) address is authorized to send messages by the sending domain?
An organization wants to ensure the security of communications across its environment. What is the BEST way to provide confidentiality of data from handheld wireless devices to the internal network?
A firm that currently produces all items to stock is implementing the concept of postponement in all new product designs. Which of the following outcomes is most likely to result?
Which of the following is a system architecture in a data protection strategy?
How would blockchain technology support requirements for sharing audit information among a community of organizations?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
The demand for an item has increasing forecast error, whereas all other factors remain constant. Which of the following remains constant while maintaining the same customer service level?
A systems engineer has been tasked by management to provide a recommendation with a prioritized, focused set of actions to help the organization stop high-risk cyber attacks and ensure data security. What should the systems engineer recommend the organization use to accomplish this?
Up-to-date Information about production order status is required to do which of the following tasks?
What document MOST likely states an organization’s values?
One of the most useful tools for analyzing the sustainable footprint is:
An example of an assignable cause of variation in process performance is:
A champion is assigned to lead a threat modeling exercise. Which of the following will be the FIRST thing to consider?
An organization suffered a loss to an asset at a frequency that was different than the initially estimated Annualized Rate of Occurrence (ARO). What is the appropriate course of action?
An organization’s security assessment recommended expanding its secure software development framework to include testing Commercial Off-The-Shelf (COTS) products before deploying those products in production. What is the MOST likely reason for this recommendation?
A security team is analyzing the management of data within the human resources systems, as well as, the intended use of the data, and with whom and how the data will be shared. Which type of assessment is the team MOST likely performing?
An organization has integrated its enterprise resource planning system into its centralized Identity and Access Management (IAM) system to automate provisioning of access. A security audit revealed that privileged access granted within the ERP system is not visible in the IAM system. Which of the following controls BEST mitigates this risk?
A Generic Routing Encapsulation (GRE) tunnel moves data across a third-party Internet Protocol (IP) network. What is the risk of using GRE tunnels?
Which of the following is a PRIMARY benefit of sharing assessment results among key organizational officials across information boundaries?
In a make-to-order (MTO) production environment, fluctuations in sales volumes are managed by adjustments to the:
After a recent cybersecurity incident, a manufacturing organization is interested in further hardening its Identity and Access Management (IAM) solution. Knowing that the organization limits the use of personal devices in the facility, which could BEST be implemented to enhance the manufacturing organization's IAM solution?
When an organization is recruiting for roles within the organization, at which stage of the employee life cycle are termination procedures incorporated?
Health information stored in paper form may be destroyed using which of the following methods?
Which of the following should be done FIRST when implementing an Identity and Access Management (IAM) solution?
Improving the performance of a constraint in a job shop environment will:
After a data loss event, an organization is reviewing its Identity and Access Management (IAM) governance process. The organization determines that the process is not operating effectively. What should be the FIRST step to effectively manage the IAM governance process?
What is the MOST effective way to begin a risk assessment?
Which of the following factors is used to determine safety stock?
What resources does a respondent have when contesting disciplinary action taken by the ISC2 Board of Directors?
Which specification enables organizations to ensure penetration test results are documented using open, machine-readable standards?
What is the PRIMARY benefit an organization obtains by cybersecurity framework to their cybersecurity program?
Which of the following methods is most often used to manage inventory planning variability across the supply chain?
How much data an organization can afford to lose is determined by the:
A security team leader needs to communicate the value of the security program. As the security team leader determines the return on security investments, what is the MOST important aspect to incorporate?
An organization implemented a threat modeling program focusing on key assets. However, after a short time it became clear that the organization was having difficulty executing the threat modeling program.
Which approach will MOST likely have been easier to execute?
A security engineer developing software for a professional services organization has a requirement that users cannot have concurrent access to data of clients that are competitors. Which security model should the security engineer implement to meet this requirement?
A company has a demand for 30 units of A, 40 units of B, and 50 units of C. These products are scheduled to run daily in batches of 10 as follows: ABC, ABC, ABC, CBC. What is this scheduling
technique called?
The horizon for forecasts that are input to the sales and operations planning (S&OP) process should be long enough that:
Which of the following strategies is most appropriate for a business unit with a low relative market share in a high-growth market?
Which security concept applies if an architecture diagram illustrates a particular user/role combination with access to an asset or applicaton?
Small, independent demands for components and subassemblies typically arise from which of the following sources?
A company with stable demand that uses exponential smoothing to forecast demand would typically use a:
What does the Role-Based Access Control (RBAC) method define?
A software organization is getting ready to launch a new application. A security engineer notices the application allows unrestricted access to files on the web server. Which of the following recommendations will BEST resolve this security issue?
Which of the following tactics can be employed effectively to reduce appraisal quality costs?
The Chief Security Officer (CSO) of an organization would like to have a network security assessment done by the security team. Which of the following is the FIRST step in the security testing methodology?
An organization is preparing to deploy Multi-Factor Authentication (MFA) to its workforce. The primary concerns of the organization are cost and security. The organization realizes that their entire workforce has computers and smartphones. Which of the following is BEST suited to address the organization's concerns?
A software development vendor wants to test the Application Programming Interface (API). The testers use and manipulate data to identify the various states of the application behavior. What is the kind of testing that is being used?
Which of the following is the MAIN element in achieving a successful security strategy?
A customer of a financial Institution denies that a transaction occurred. Which of the following is used to provide evidence evidence that the customer performed the transaction?
What is the BEST item to consider when designing security for information systems?
Open Authorized (OAuth) has been chosen as technology to use across applications in the enterprise. Which of the following statements is TRUE about an OAuth token?
A security specialist is responsible to improve the security awareness program of a medium-sized organization and tasked to track blocked targeted attacks. Which of the following BEST describes the outcome of the security specialist’s use of metrics for this task?
Capacity requirements planning (CRP) is applicable primarily In companies operating In an environment where:
A potentially life-threatening vulnerability is found in vendor software that is used to manage critical systems. Which of the following is generally considered the BEST method to disclose the vulnerability from an ethical hacking perspective?
The planned channels of Inventory disbursement from one or more sources to field warehouses are known as:
What is the process when a security assessor compiles potential targets from the attacker’s perspective, such as data flows, and interactions with users?
When resolving conflicts, which canon within the ISC2 Code of Ethics requires members to consider duties to principals and Individuals?
In which of the following circumstances is an organization MOST likely to report the accidental release of personal data to the European Union (EU) General Data Protection Regulation (GDPR) supervisory authority and affected users?
A financial services organization wants to deploy a wireless network. Which of the following is the WEAKEST option for ensuring a secure network?
Which of the following capacity planning methods uses the master production schedule (MPS) as its primary input?
A manufacturer begins production of an item when a customer order is placed. This is an example of a(n):
During an emergency management and planning session, an organization is discussing how to identify, prevent, prepare for, or respond to emergencies. Which of the following will provide the BEST possible outcome?
APerform drills on a recurring basis.
B.Harden all critical facilities.
C.Outsource to an external organization.
D.Allocate 100% of required funds.
Which of the following terms below BEST describes the measure of confidence that the security features, practices, procedures, and architecture of an information system accurately mediates and enforces security policy?
For a company that uses first in, first out (FIFO) inventory accounting, the actual use in production of a recently arrived shipment of more expensive components rather than lower-cost components
previously received will have which of the following results?
An information security auditor is creating an audit program to assess endpoint security controls for portable storage media movement. Which type of control will MOST likely be part of the program?
Which of the following actions hinders the transition from a push system to a pull system?
An organization has a legacy application used in production. Security updates are no longer provided, which makes the legacy application vulnerable. The legacy application stores Social Security numbers and credit card numbers. Which actions will BEST reduce the risk?
Which of the following techniques is BEST suited to preserve the confidentiality of a system’s data?
Which of the following is the BEST reason to conduct a penetration test?
A company’s Marketing and Sales departments have identified an opportunity to develop a new market for a product family and requested an increase in the production plan. Which of the following actions would be most appropriate to account for the new market opportunity?
An example of a cradle-to-cradle sustainability model would be:
The time spent In queue by a specific manufacturing job is determined by which of the following factors related to the order?
Which of the following is a methodology for threat modeling in application?
Which of the following is the fundamental difference between finite loading and other capacity planning approaches?
A security consultant is recommending the implementation of a security-focused Configuration Management (CM) process in an organization. What would be the BEST benefit the security consultant would include in the recommendation?
Which of the following production activity control (PAC) techniques focuses on optimizing output?
Which of the following systems would be the most cost-efficient for inventory management of a low value item?
A security analyst modifies the organization’s baselines to align the controls more closely with specific security and privacy requirements. Which security concept is this an example of?
Which of the following Secure Shell (SSH) remote access practices is MOST suited for scripted functions?
An organization is restructuring its network architecture in which system administrators from the corporate office need to be able to connect to the branch office to perform various system maintenance activities. What network architecture would be MOST secure?
In which of the following phases of the product life cycle is product price most effective in influencing demand?
An organization has been struggling to improve their security posture after a recent breach. Where should the organization focus their efforts?
A company's primary performance objective Is flexibility. Which of the following measurements is most important?
In Company XYZ, transaction-costing capability has been Integrated into the shop floor reporting system. A batch of 20 units was started in production. At the fourth operation, 20 units are reported as complete. At the fifth operation, 25 units are reported as complete. When all operations are complete, 20 units are checked into the stockroom. If the error at the fifth operation is undetected, which of the following conditions will be true?
An organization currently has a network with 55,000 unique Internet Protocol (IP) addresses in their private Internet Protocol version 4 (IPv4) network range and has acquired another organization and must integrate their 25,000 endpoints with the existing, flat network topology. If subnetting is not implemented, which network class is implied for the organization’s resulting private network segment?
After a recent threat modeling workshop, the organization has requested that the Chief Information Security Officer (CISO) implement zero trust (ZT) policies. What was the MOST likely threat identified in the workshop?
One of the benefits of Integrating a poka-yoke into the production process is that it can be used to:
An organization is retiring an old server out of the data center. This server was used to store and process sensitive information. The server is being sent off-site to a recycling center. Which declassification method should be performed prior to it being sent off-site?
Which of the following is the MOST important consideration in a full-scale disaster recovery test?
Which of the following statements correctly describes the relationship between the strategic plan and the business plan?
What priority control technique is most appropriate for a firm using a cellular production system?
What should an organization do to prepare for Disaster Recovery (DR) efforts?
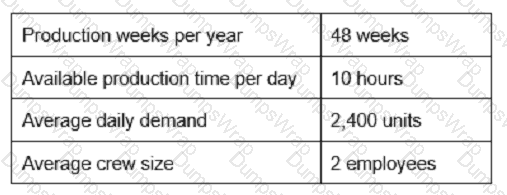
Given the following data, calculate the appropriate takt time:
Labor3 people
Work hours10 hours per day
Days4 days per week
Meetings with work area employees1/2 hour per day
Work area efficiency85%
Given the information above, what is the weekly theoretical capacity of this work area in hours?
Fishbone diagrams would help a service organization determine:
Which of the following represents the BEST metric when measuring the effectiveness of a security awareness program?
Moving average forecasting methods are best when demand shows:
An organization is migrating some of its applications to the cloud. The Chief Information Security Officer (CISO) is concerned about the accuracy of the reports showing which application should be migrated and how many applications reside on each server. As a result, the CISO is looking to establish asset management requirements. Which of these elements should be considered part of asset management requirements?
A cybersecurity analyst is responsible for identifying potential security threats and vulnerabilities in the organization's software systems. Which action BEST demonstrates the understanding and application of threat modeling concepts and methodologies?
A product manager wishes to store sensitive development data using a cloud storage vendor while maintaining exclusive control over passwords and encryption credentials. What is the BEST method for meeting these requirements?
Which of the following MUST exist for an activity to be considered an audit?
Which of the following should Business Impact Analysis (BIA) reports always include?
What is the BEST way to plan for power disruptions when implementing a Disaster Recovery Plan (DRP)?
Why would a network administrator monitor Internet of Things (IoT) security differently than the security of standards network devices?
An organization is running a cloud-based application to process the information obtained at point-of-sale devices. Which guideline should be applied to the application?
Which of the following vulnerability types is also known as a serialization flaw and affects the integrity of two processes interacting with the same resource at the same time?
An example of a flexibility metric for an organization Is:
A vendor has been awarded a contract to supply key business software. The vendor has declined all requests to have its security controls audited by customers. The organization insists the product must go live within 30 days. However, the security team is reluctant to allow the project to go live.
What is the organization's BEST next step?
An agency has the requirement to establish a direct data connection with another organization for the purpose of exchanging data between the agency and organization systems. There is a requirement for a formal agreement between the agency and organization. Which source of standards can the system owners use to define the roles and responsibilities along with details for the technical and security requirements?
While conducting an information asset audit, it was determined that several devices were running unpatched Operating Systems (0S). Further review Indicated the OS was no longer supported by the vendor. Which of the following BEST indicates the appropriate asset lifecycle stage of the devices?
Which of the following categories of web services testing describes correctness testing of web service security functionality?
A plant uses a level production strategy due to the high costs of hiring and letting go of skilled employees. The constrained resource is due to be upgraded in the fourth month of the planning horizon, and that will reduce capacity for that month by 17%.
Which of the following actions would be appropriate in this situation to maintain current levels of customer service and gross margin?
Which of the following threats MUST be included while conducting threat modeling for a Cloud Service Provider (CSP)?
What is the MOST beneficial principle of threat modeling?
An information system containing Protected Health Information (PHI) will be accessed by doctors, nurses, and others working in a hospital. The same application will be used by staff in the pharmacy department only for dispensing prescribed medication. Additionally, patients can log in to view medical history. The system owner needs to propose an access control model that considers environment, situation, compliance, and security policies while dynamically granting the required level of access. Which access control model is the MOST suitable?
Organization A provides scalable Information Technology (IT) infrastructure while Organization B provides security services to customers via Software as a Service (SaaS) model. Which document is used to express a set of intended actions between the organizations with respect to meeting the customers’ needs?
What is the following is the MAIN reason why hot-spot usually adopt open security mode in wireless networks?
During a security incident investigation, a security analyst discovered an unauthorized module was compiled into an application package as part of the application assembly phase. This incident occurred immediately prior to being digitally signed and deployed using a deployment pipeline.
Which of the following security controls would BEST prevent this type of incident in the future?
Which of the following statements best characterizes enterprise resources planning (ERP) systems?
Which of the following statements characterizes a pull system In distribution management?
Which of the following documents is the BEST reference to describe application functionality?
What is the MAIN purpose of risk and impact analysis?
To ensure the quality of its newly developed software, an organization is aiming to deploy an automated testing tool that validates the source code. What type of testing BEST supports this capability?
An organization provides customer call center operations for major financial service organizations around the world. As part of a long-term strategy, the organization plans to add healthcare clients to the portfolio. In preparation for contract negotiations with new clients, to which cybersecurity framework(s) should the security team ensure the organization adhere?
An attacker was able to identify an organization’s wireless network, collect proprietary network resource information, and capture several user credentials. The attacker then used that information to conduct a more sophisticated and impactful attack against the organization. Which method did the attacker MOST likely use to gather the initial information?
An organization discovered that malicious software was installed on an employee’s work laptop and allowed a competing vendor to access confidential files. The employee was fully aware of the policy not to install unauthorized software on the organization laptop. What is the BEST automated security practice for an organization to implement to avoid this situation?
Improvements in an Input/output control (I/O control) system will most likely lead to:
If all other factors remain the same, when finished goods inventory investment is increased, service levels typically will:
The question below is based on the following information:
Beginning inventory = 43Week 1Week 2Week 3
Forecast202020
Customer orders221710
Projected on-hand
Master production schedule (MPS)80
Available-to-promise (ATP)
What is the largest customer order that could be accepted for delivery at the end of week 3 without making changes to the master production schedule (MPS)?
In a lean environment, the batch-size decision for planning "A" items would be done by:
In the sales and operations planning (S&OP) process, the demand management function provides:
A healthcare organization is preparing an exercise test plan of its Disaster Recovery Plan (DRP) for the Electronic Medical Record (EMR) application. The Business Continuity (BC) analyst is reviewing the requirements of the DRP. The EMR must provide basic charting services within 4 hours, must not lose more than 15 minutes of data, and must be fully functional within 12 hours. At the completion of the exercise, the analyst is preparing a lessons learned report and notes that the EMR was available after 3 hours and 25 minutes of data was lost. Which PRIMARY requirement needs to be addressed because of the exercise?
Which of the following incorporates design techniques promoted by Crime Prevention Through Environmental Design (CPTED)?
An organization wants to ensure a risk does not occur. The action taken is to eliminate the attack surface by uninstalling vulnerable software. Which risk response strategy did the organization take?
Which of the following factors is the MOST important consideration for a security team when determining whether cryptographic erasure can be used for disposal of a device?
A web application is found to have SQL injection (SQLI) vulnerabilities. What is the BEST option to remediate?
A health care organization's new cloud-based customer-facing application is constantly receiving security events from dubious sources. What BEST describes a security event that compromises the confidentiality, integrity or availability of the application and data?
Which of the following methods most likely Introduces a temporary variance between the inventory balance and the inventory record?
Which of the following conditions is most likely to result in planned production that is greater than the total demand over the sales and operations planning (S&OP) horizon for a product family that is
made to stock?
As a result of a fault at a cloud service provider’s data center, the customer accounts of a utility organization were corrupted. Under the European Union’s (EU) General Data Protection Regulation (GDPR), which entity bears responsibility for resolving this?
A reduction In purchased lot sizes will reduce which of the following items?
Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
Which of the following attributes describes a company with a global strategy?
Which of the following is the BEST activity to mitigate risk from ransomware on mobile devices and removable media in a corporate environment?
An organization is updating an Application Programming Interface (API) to support requests coming from mobile applications distributed on public application stores. The API’s primary function is to supply confidential documents when users request them within the mobile application. Which approach would BEST respond to this use case?
Which of the following tools is used to evaluate the impact that a production plan has on capacity?
What is the BEST reason to include a Hardware Security Module (HSM) in the key management system when securing cloud storage?
Which of the following concepts MOST accurately refers to an organization's ability to fully understand the health of the data in its system at every stage of the lifecycle?
An order winner during the growth stage of a product's life cycle is:
Which of the following is the MOST effective practice for tracking organizational assets when removed from the premises?
What is the main negative effect of changing the due dates of open orders?
Which of the following is the BEST solution to implement to mitigate the risk of data breach in the event of a lost or stolen mobile device?
An organization undergoing acquisition merged IT departments and infrastructure. During server decommissioning, some servers still in use by customers were mistakenly removed, causing order processing failures. Which type of review would have BEST avoided this scenario?
A security practitioner notices that workforce members retain access to information systems after transferring to new roles within the organization, which could lead to unauthorized changes to the information systems.
This is a direct violation of which common security model?
At which Open Systems Interconnection (OSI) layer does User Datagram Protocol (UDP) function?
Following the go-live of a new financial software, an organization allowed the Information Technology (IT) officer to maintain all rights and access permissions to help the organization staff should they have challenges in their day-to-day work. What is the BEST way to categorize the situation?
An attacker wants to decrypt a message and has no knowledge of what may have been in the original message. The attacker chooses to use an attack that will exhaust the keyspace in order to decrypt the message. What type of cryptanalytic attack is the attacker using?
A manufacturer has a forecasted annual demand of 1,000,000 units for a new product. They have to choose 1 of 4 new pieces of equipment to produce this product. Assume that revenue will be $10 per unit for all 4 options.
Which machine will maximize their profit if the manufacturer anticipates market demand will be steady for 3 years and there is no residual value for any of the equipment choices?
MachineFixed CostVariable Cost per UnitAnnual Capacity
AS100.000$6 00800,000 units
B$200,000$5 501.000,000 units
C$250,000$5 001,200,000 units
D$1 000.000$4 501 400.000 units
What is the BEST protection method to ensure that an unauthorized entry attempt would fail when securing highly sensitive areas?
If the total part failure rate of a machine is 0.00055 failures per hour, what would be the mean time between failures (MTBF) in hours?
What FIRST step should a newly appointed Data Protection Officer (DPO) take to develop an organization's regulatory compliance policy?
An organization is implementing improvements to secure the Software Development Life Cycle (SDLC). When should defensive three modeling occur?
An organization needs a firewall that maps packets to connections and uses Transmission Control Protocol/Internet Protocol (TCP/IP) header fields to keep track of connections. Which type of firewall will be recommended?
Which of the following mechanisms should a practitioner focus on for the MOST effective information security continuous monitoring?
In a large organization, the average time for a new user to receive access is seven days. Which of the following is the BEST enabler to shorten this time?
An information security professional is considering what type of classification label to place on an organization’s software code in order to implement proper access controls. The code is considered intellectual property data and would have a catastrophic impact to the organization if compromised or destroyed. Which of the following would be the MOST appropriate classification label to apply?
Zombieload, Meltdown, Spectre, and Fallout are all names of bugs that utilized which of the following types of attack?
Which of the following techniques would a group use to prioritize problems?
The security department was notified about vulnerabilities regarding users' identity verification in a web application. Which of the following vulnerabilities is the security professional MOST likely to test?
A company has the following production conditions:
Batch size: 1,000 items
Processing time: 4 minutes per item
Setup time: 2 hours
Utilization: 80%
Efficiency: 80%
Which of the following actions would result in the work being done in the least amount of time?
A security specialist is responsible to improve the security awareness program of a medium-sized organization and is tasked to track blocked targeted attacks. Which of the following BEST describes the outcome of the security specialist’s use of metrics for this task?
One of the findings in the recent security assessment of a web application reads: "It appears that security is an afterthought in the web application development process. It is recommended that security be addressed earlier in the development process." Which of these choices would BEST remediate this security finding?
A semiconductor manufacturer is writing a physical asset handling policy. Which of the following is MOST likely to be the rationale for the policy?

