Check Point Certified Security Administrator R80 Questions and Answers
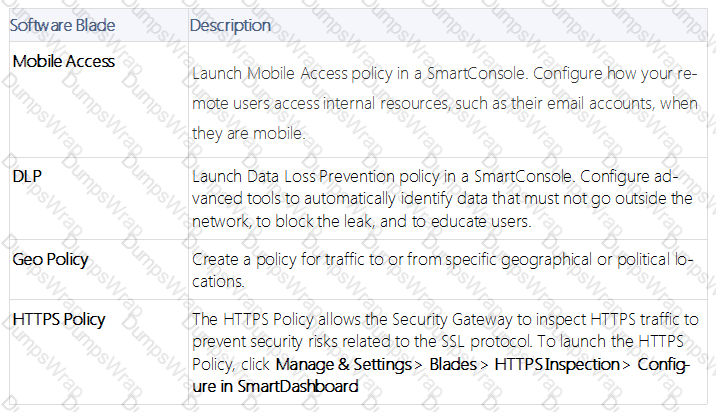
DLP and Geo Policy are examples of what type of Policy?
Which of the following is NOT a component of a Distinguished Name?
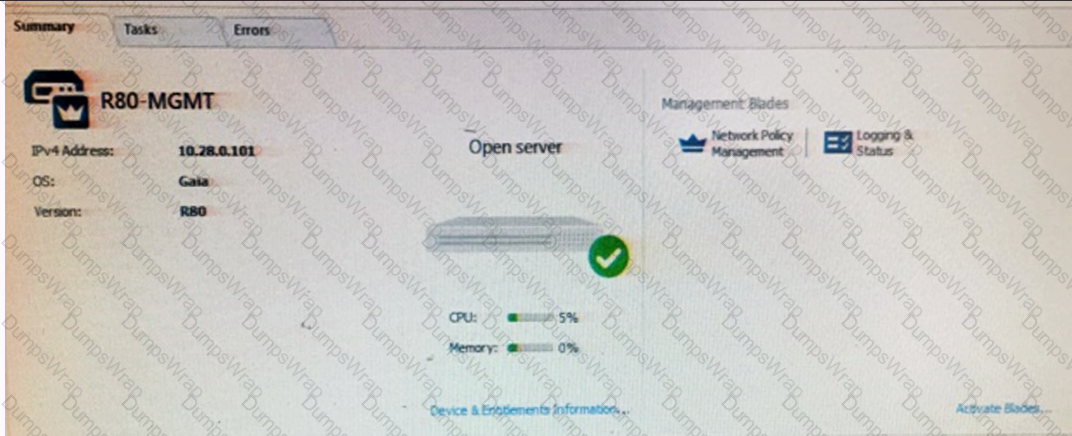
Tina is a new administrator who is currently reviewing the new Check Point R80 Management console interface. In the Gateways view, she is reviewing the Summary screen as in the screenshot below. What as an 'Open Server'?
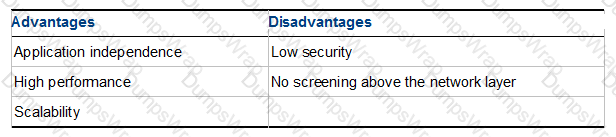
What is NOT an advantage of Packet Filtering?
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
Web Control Layer has been set up using the settings in the following dialogue:
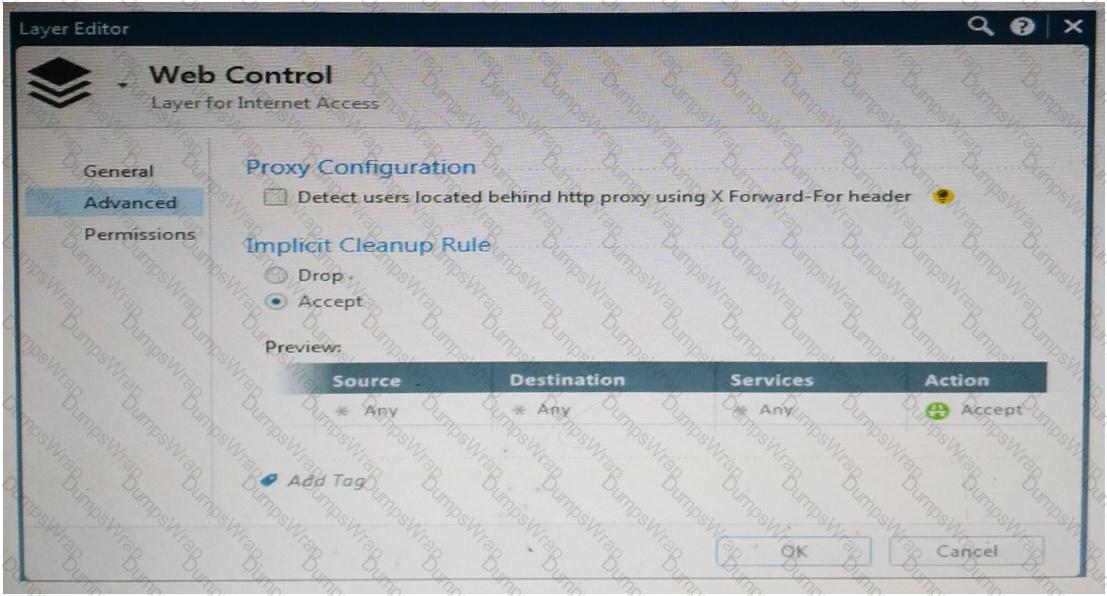
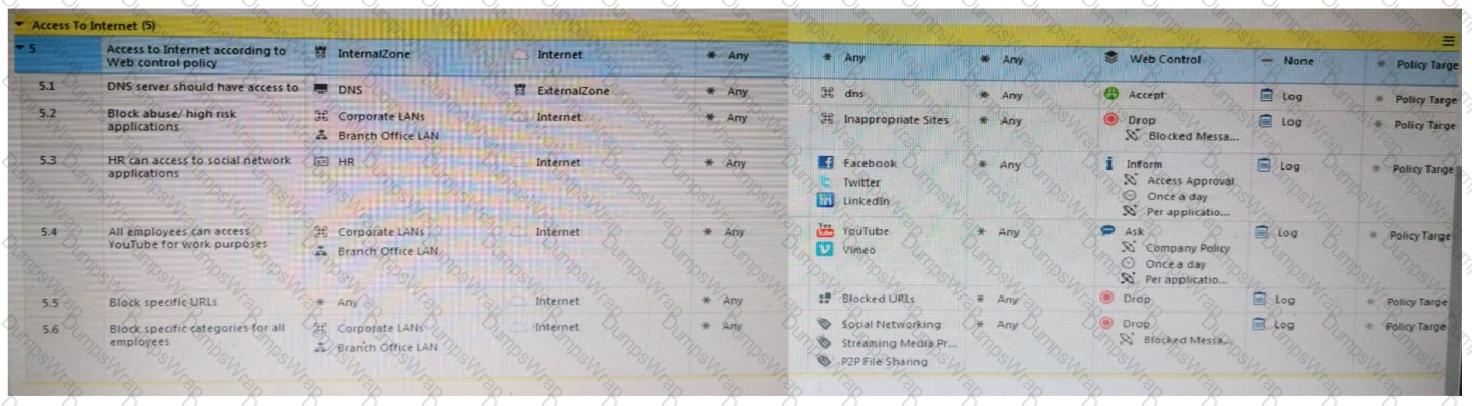
Consider the following policy and select the BEST answer.
Which of the following is NOT a license activation method?
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp.
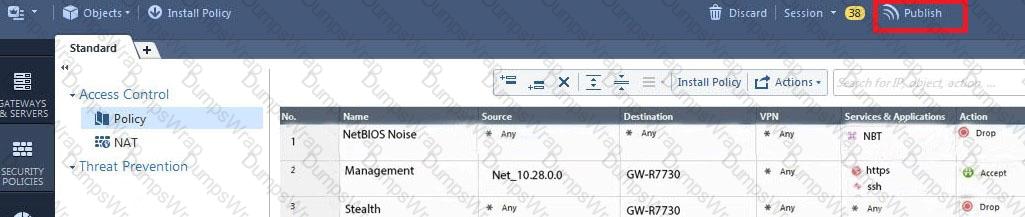
How will you describe the new “Publish” button in R80 Management Console?
What are the three authentication methods for SIC?
Tom has been tasked to install Check Point R80 in a distributed deployment. Before Tom installs the systems this way, how many machines will he need if he does NOT include a SmartConsole machine in his calculations?
Two administrators Dave and Jon both manage R80 Management as administrators for ABC Corp. Jon logged into the R80 Management and then shortly after Dave logged in to the same server. They are both in the Security Policies view. From the screenshots below, why does Dave not have the rule no.6 in his SmartConsole view even though Jon has it his in his SmartConsole view?
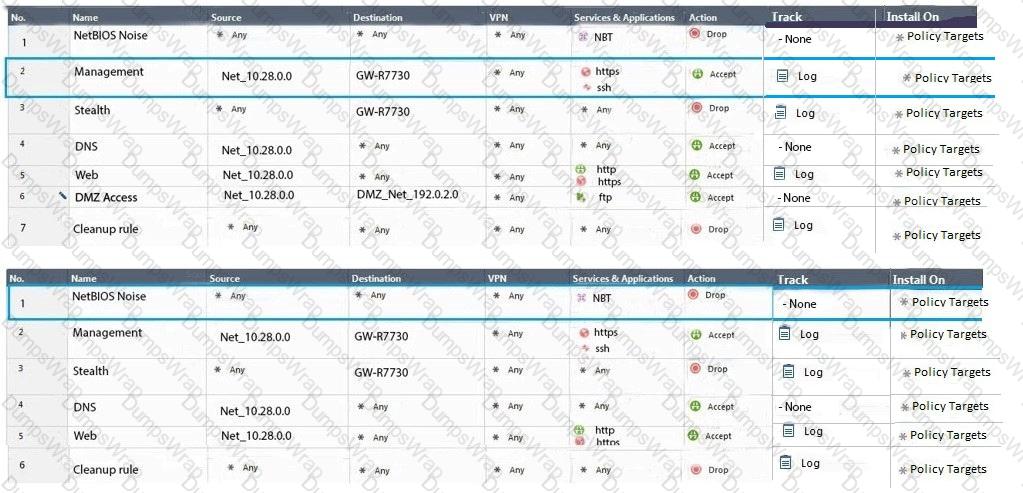
You are working with multiple Security Gateways enforcing an extensive number of rules. To simplify security administration, which action would you choose?
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server (Security Management Server)?
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
Which of the following is TRUE regarding Gaia command line?
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ________.
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain. Why does it not detect the windows domain?
What is the purpose of Captive Portal?
Which of the following is NOT an integral part of VPN communication within a network?
Fill in the blanks: The _________ collects logs and sends them to the _________ .
Which directory holds the SmartLog index files by default?
Fill in the blank: The IPS policy for pre-R80 gateways is installed during the _______ .
Office mode means that:
Which of the following is NOT an alert option?
Administrator wishes to update IPS from SmartConsole by clicking on the option “update now” under the IPS tab. Which device requires internet access for the update to work?
You want to reset SIC between smberlin and sgosaka.
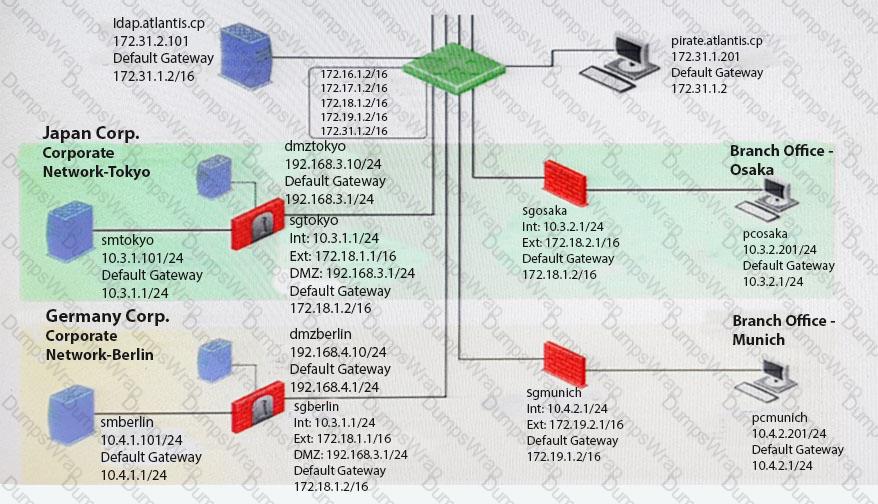
In SmartDashboard, you choose sgosaka, Communication, Reset. On sgosaka, you start cpconfig, choose Secure Internal Communication and enter the new SIC Activation Key. The screen reads The SIC was successfully initialized and jumps back to the menu. When trying to establish a connection, instead of a working connection, you receive this error message:
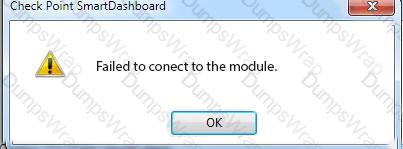
What is the reason for this behavior?
There are two R77.30 Security Gateways in the Firewall Cluster. They are named FW_A and FW_B. The cluster is configured to work as HA (High availability) with default cluster configuration. FW_A is configured to have higher priority than FW_B. FW_A was active and processing the traffic in the morning. FW_B was standby. Around 1100 am, its interfaces went down and this caused a failover. FW_B became active. After an hour, FW_A’s interface issues were resolved and it became operational. When it re-joins the cluster, will it become active automatically?
Why would an administrator see the message below?
To install a brand new Check Point Cluster, the MegaCorp IT department bought 1 Smart-1 and 2 Security Gateway Appliances to run a cluster. Which type of cluster is it?
Which Check Point software blade provides protection from zero-day and undiscovered threats?
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
Which of the following is NOT a set of Regulatory Requirements related to Information Security?
Which command is used to obtain the configuration lock in Gaia?
Fill in the blank: When LDAP is integrated with Check Point Security Management, it is then referred to as _______
What CLI utility allows an administrator to capture traffic along the firewall inspection chain?
Fill in the blank: The _________ software blade enables Application Security policies to allow, block, or limit website access based on user, group, and machine identities.
You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office. What is the correct order for pushing SIC certificates to the Gateway before shipping it?
1. Run cpconfig on the Gateway, select Secure Internal Communication, enter the activation key, and reconfirm.
2. Initialize Internal Certificate Authority (ICA) on the Security Management Server.
3. Configure the Gateway object with the host name and IP addresses for the remote site.
4. Click the Communication button in the Gateway object's General screen, enter the activation key, and click Initialize and OK.
5. Install the Security Policy.
What is the potential downside or drawback to choosing the Standalone deployment option instead of the Distributed deployment option?
Which of the following is NOT a VPN routing option available in a star community?
Which policy type is used to enforce bandwidth and traffic control rules?
Which component functions as the Internal Certificate Authority for R77?
Which NAT rules are prioritized first?
Which of these attributes would be critical for a site-to-site VPN?
In what way are SSL VPN and IPSec VPN different?
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of your firm's business partners. Which SmartConsole application should you use to confirm your suspicious?
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?
Which of the following authentication methods can be configured in the Identity Awareness setup wizard?
MegaCorp's security infrastructure separates Security Gateways geographically. You must request a central license for one remote Security Gateway.
How do you apply the license?
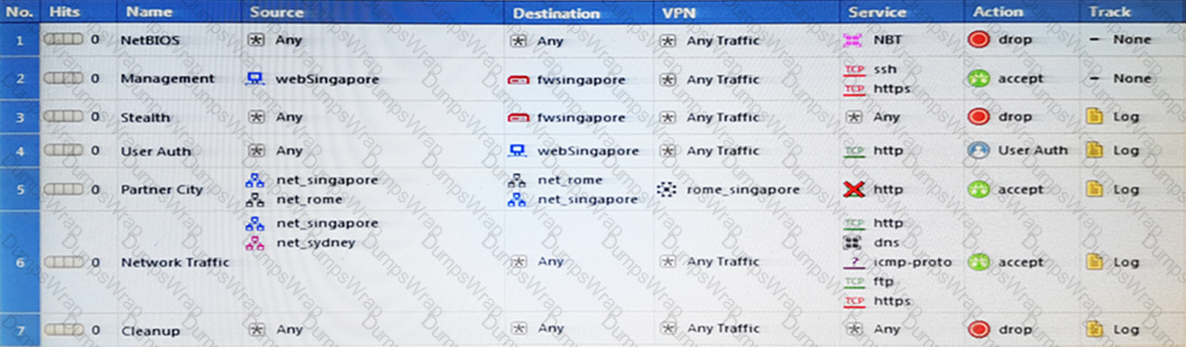
Review the rules. Assume domain UDP is enabled in the implied rules.

What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
Which rule is responsible for the user authentication failure?
When defining QoS global properties, which option below is not valid?
Which of the below is the MOST correct process to reset SIC from SmartDashboard?
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?
What is the Manual Client Authentication TELNET port?
When launching SmartDashboard, what information is required to log into R77?
VPN gateways must authenticate to each other prior to exchanging information. What are the two types of credentials used for authentication?
Which limitation of CoreXL is overcome by using (mitigated by) Multi-Queue?
You find a suspicious connection from a problematic host. You decide that you want to block everything from that whole network, not just the problematic host. You want to block this for an hour while you investigate further, but you do not want to add any rules to the Rule Base. How do you achieve this?
A digital signature:
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
What are the two types of NAT supported by the Security Gateway?
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
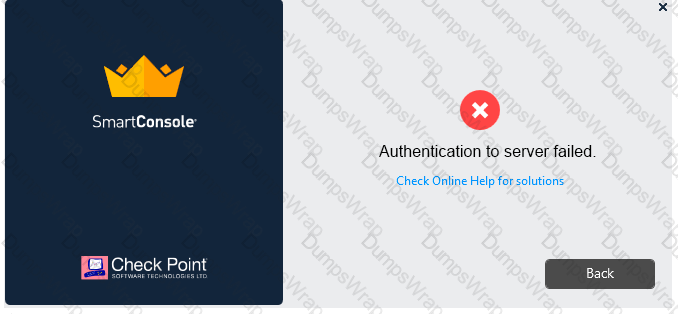
What is the most likely reason?
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers?
When defining group-based access in an LDAP environment with Identity Awareness, what is the BEST object type to represent an LDAP group in a Security Policy?
What are the three components for Check Point Capsule?
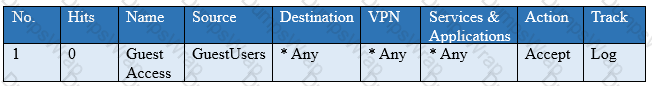
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
What is true about the IPS-Blade?
You are the Check Point administrator for Alpha Corp. You received a call that one of the users is unable to browse the Internet on their new tablet which is connected to the company wireless, which goes through a Check Point Gateway. How would you review the logs to see what is blocking this traffic?
You have discovered suspicious activity in your network. What is the BEST immediate action to take?
What object type would you use to grant network access to an LDAP user group?
Which of the following blades is NOT subscription-based and therefore does not have to be renewed on a regular basis?
Fill in the blank: Back up and restores can be accomplished through_________.
Fill in the blank: The position of an implied rule is manipulated in the __________________ window.
Which of the following situations would not require a new license to be generated and installed?
In ____________ NAT, the ____________ is translated.