Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Questions and Answers
What is indicated by an increase in IPv4 traffic carrying protocol 41 ?
Which option describes indicators of attack?
How does an attacker observe network traffic exchanged between two users?
An engineer is sharing folders and files with different departments and got this error: "No such file or directory". What must the engineer verify next?
STION NO: 102
Refer to the exhibit.
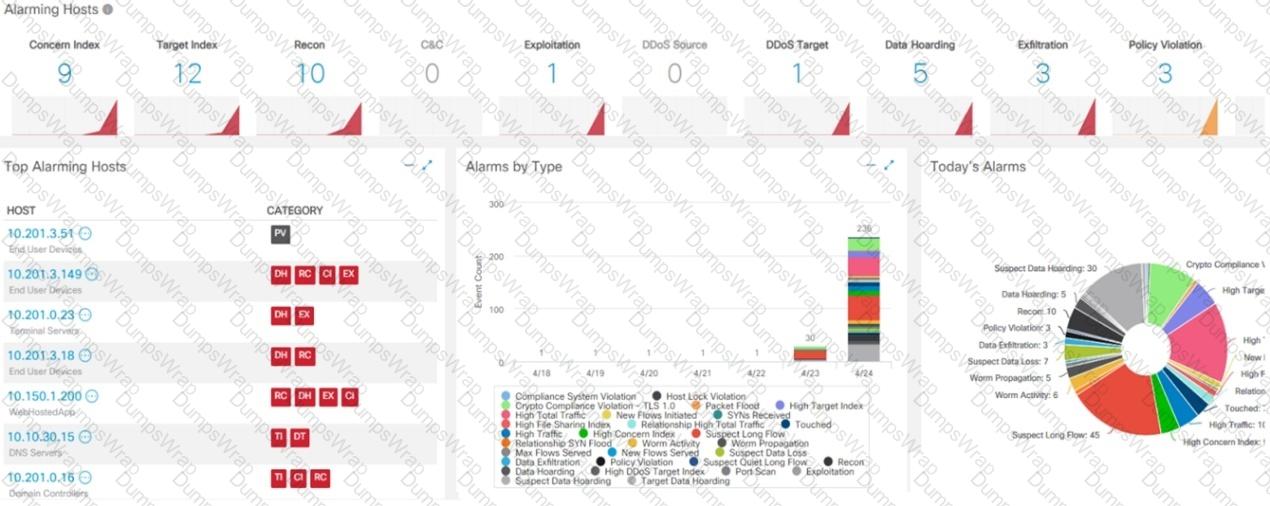
What is the potential threat identified in this Stealthwatch dashboard?
What is the impact of false positive alerts on business compared to true positive?
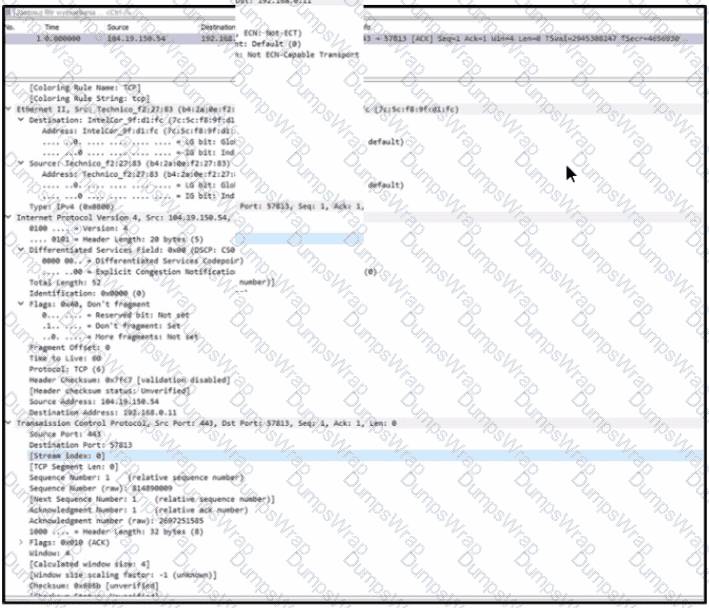
Refer to the exhibit. An engineer must use a 5-tuple approach to isolate a compromised host in a grouped set of logs.
Which data must the engineer use?
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
Which piece of information is part of the chain of custody during investigation?
How does certificate authority impact a security system?
What is the impact of encryption?
What is the dataflow set in the NetFlow flow-record format?
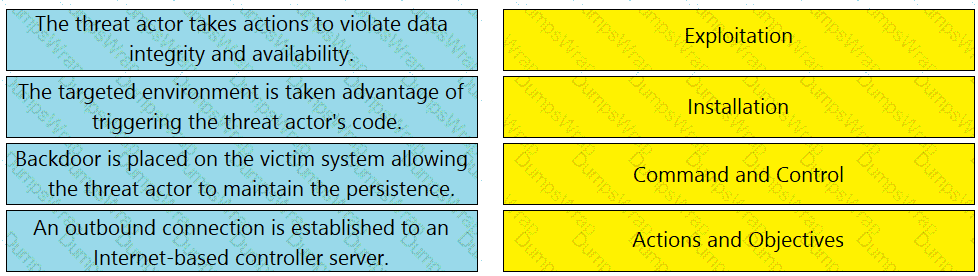
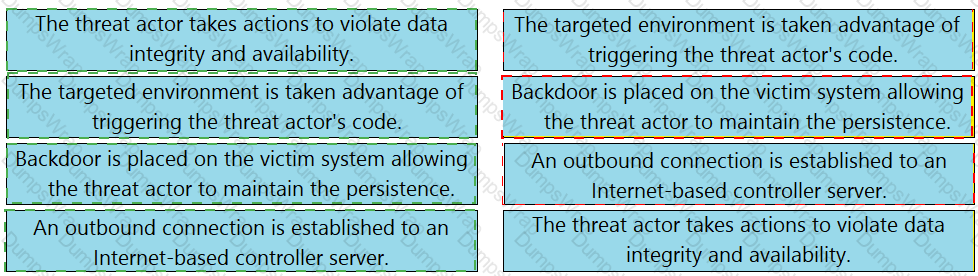
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
What describes the vulnerability management process?
Which incidence response step includes identifying all hosts affected by an attack?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?

Refer to the exhibit. Where is the executable file?
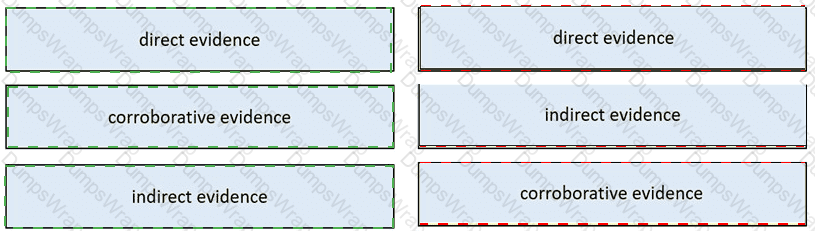
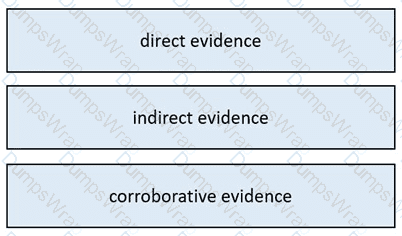
Drag and drop the type of evidence from the left onto the description of that evidence on the right.

Developers must implement tasks on remote Windows environments. They decided to use scripts for enterprise applications through PowerShell. Why does the functionality not work?
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
Which event is a vishing attack?
What is a disadvantage of the asymmetric encryption system?
A security analyst received a ticket about suspicious traffic from one of the workstations. During the investigation, the analyst discovered that the workstation was communicating with an external IP. The analyst could not investigate further and escalated the case to a T2 security analyst. What are the two data visibility challenges that the security analyst should identify? (Choose two.)
An analyst must choose one source of information for further troubleshooting. A key requirement is to use low storage space over the next 12 months while being able to quickly determine the source and scope of an attack to effectively mitigate it. Which source of information should the analyst choose?
What is session data used for in network security?
Which category relates to improper use or disclosure of PII data?
Refer to the exhibit.
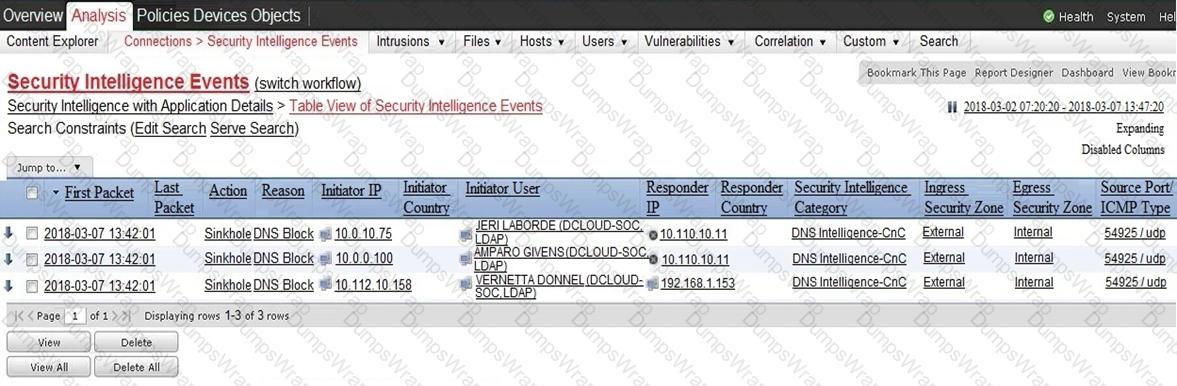
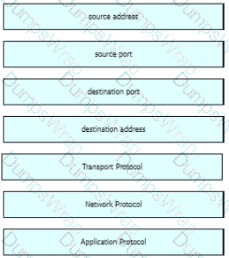
Which two elements in the table are parts of the 5-tuple? (Choose two.)
A security engineer must determine why a new core application does not work as desired The client can send requests toward the application server but receives no response One of the requirements is to gather all packets Data needs to be reliable without any delay or packet drops Which solution best meets this need?
A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
What is a scareware attack?
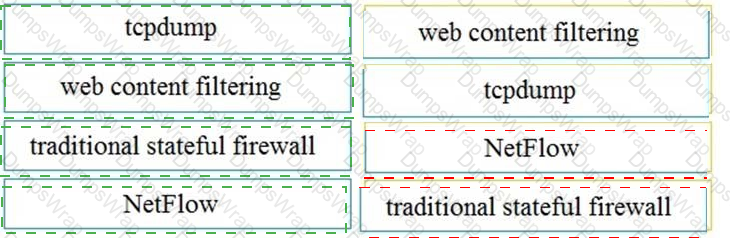
What are two differences of deep packet inspection compared to stateful firewall inspection? (Choose two.)
Which utility blocks a host portscan?
Refer to the exhibit.
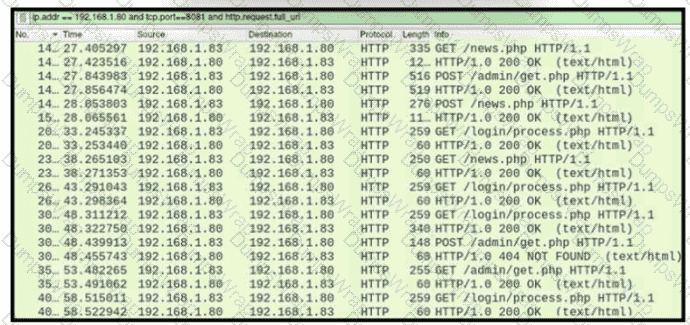
A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted What is occurring?
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmatware2022-12-22.pcaps file.The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
Refer to the exhibit.
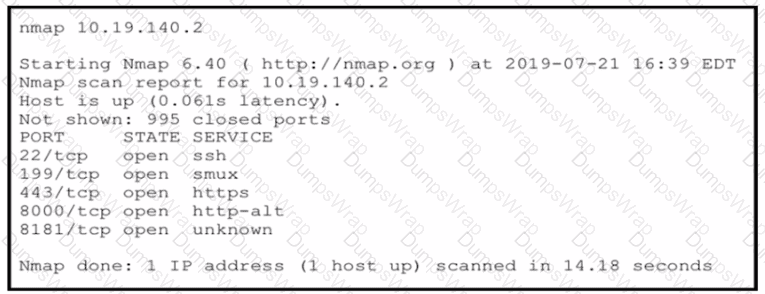
An attacker gained initial access to the company s network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data Which two elements can an attacker identify from the scan? (Choose two.)
An engineer is working on a ticket for an incident from the incident management team A week ago. an external web application was targeted by a DDoS attack Server resources were exhausted and after two hours it crashed. An engineer was able to identify the attacker and technique used Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team According to NIST SP800-61, at which phase of the incident response did the engineer finish work?
Which regex matches only on all lowercase letters?
How low does rule-based detection differ from behavioral detection?
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
What are indicators of attack?
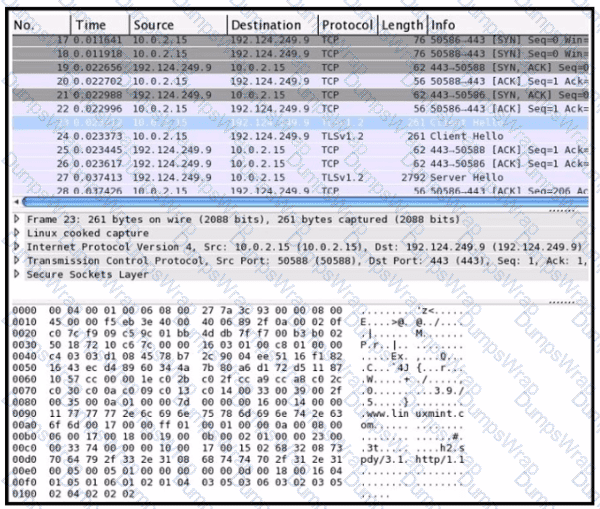
Refer to the exhibit Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.
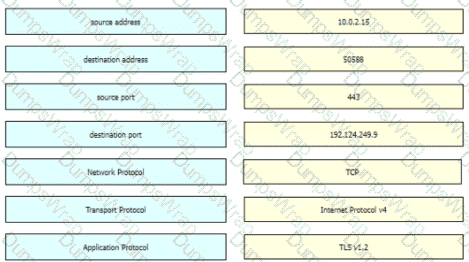
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
What is used to maintain persistent control of an exploited device?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
An engineer must compare NIST vs ISO frameworks The engineer deeded to compare as readable documentation and also to watch a comparison video review. Using Windows 10 OS. the engineer started a browser and searched for a NIST document and then opened a new tab in the same browser and searched for an ISO document for comparison
The engineer tried to watch the video, but there 'was an audio problem with OS so the engineer had to troubleshoot it At first the engineer started CMD and looked fee a driver path then locked for a corresponding registry in the registry editor The engineer enabled "Audiosrv" in task manager and put it on auto start and the problem was solved Which two components of the OS did the engineer touch? (Choose two)
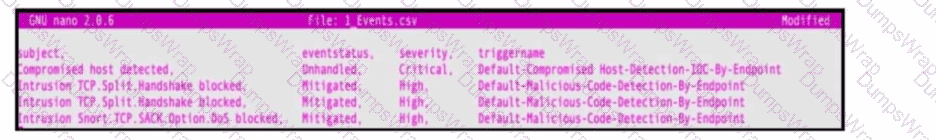
Refer to the exhibit. An engineer must map these events to the source technology that generated the event logs. To which technology do the generated logs belong?
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
Which security principle requires more than one person is required to perform a critical task?
Which technology on a host is used to isolate a running application from other applications?
In a SOC environment, what is a vulnerability management metric?

Refer to the exhibit. A SOC team member receives a case from his colleague with notes attached. The artifacts and alerts associated with the case must be analyzed and a conclusion must be provided. What is the cause of the alert?
Refer to the exhibit.
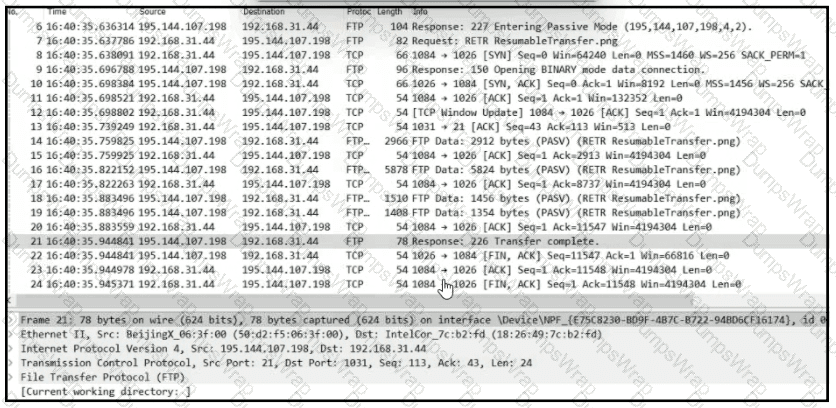
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
Which items is an end-point application greylist used?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
What are the two differences between stateful and deep packet inspection? (Choose two )
A company recently encountered a breach. Critical services went through a disturbance and the integrity of the data was altered. An engineer is investigating the issue and searching through the logs in the SIEM. Which phase of the incident response is an engineer working on?
Which attack represents the evasion technique of resource exhaustion?
Which SOC metric represents the time to stop the incident from causing further damage to systems or data?
What is the communication channel established from a compromised machine back to the attacker?
A user reports that a mobile application is working very slowly. A DDoS detection tool reports high-volume traffic. During which phase does the CSIRT ensure that the incident does not continue and confirm that the organization has taken the required actions?
A forensic investigator is analyzing a recent breach case. An external USB drive was discovered to be connected and transmitting the data outside of the organization, and the owner of the USB drive could not be identified. Video surveillance shows six people during a two-month period had close contact with the affected asset. How must this type of evidence be categorized?
Refer to the exhibit.
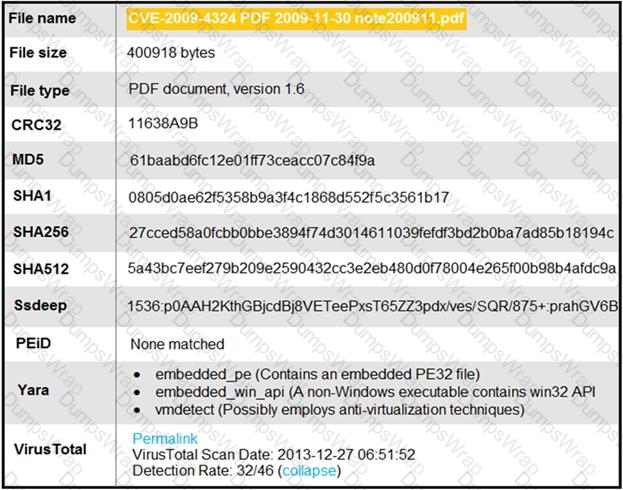
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
According to CVSS, what is a description of the attack vector score?
What is the difference between tampered and untampered disk images?
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Which type of data consists of connection level, application-specific records generated from network traffic?
What is the difference between statistical detection and rule-based detection models?
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
Refer to the exhibit.
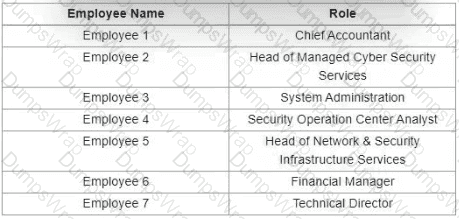
Which stakeholders must be involved when a company workstation is compromised?
At which layer is deep packet inspection investigated on a firewall?
Which action matches the weaponization step of the Cyber Kill Chain model?
Refer to the exhibit.

In which Linux log file is this output found?
Drag and drop the technology on the left onto the data type the technology provides on the right.
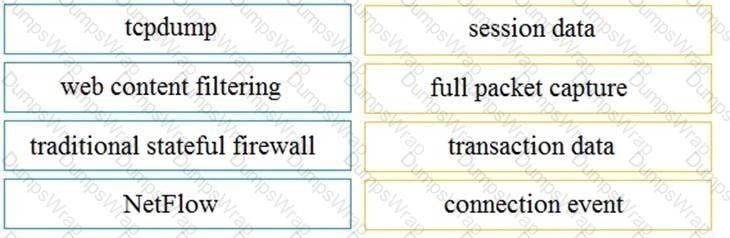
Refer to the exhibit.
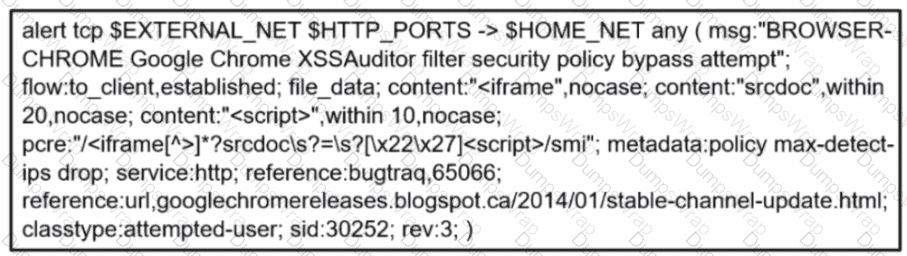
A company's user HTTP connection to a malicious site was blocked according to configured policy What is the source technology used for this measure'?
Which regular expression matches loopback IP address (127.0.0.1)?
Which information must an organization use to understand the threats currently targeting the organization?
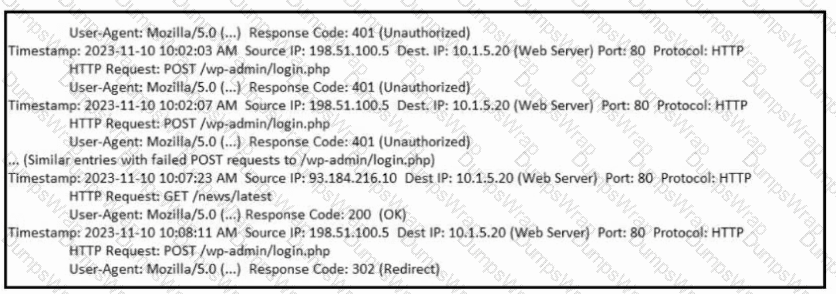
Refer to the exhibit. What is occurring?
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
What describes the usage of a rootkit in endpoint based attacks?
Refer to the exhibit.

Which type of log is displayed?
Refer to the exhibit.
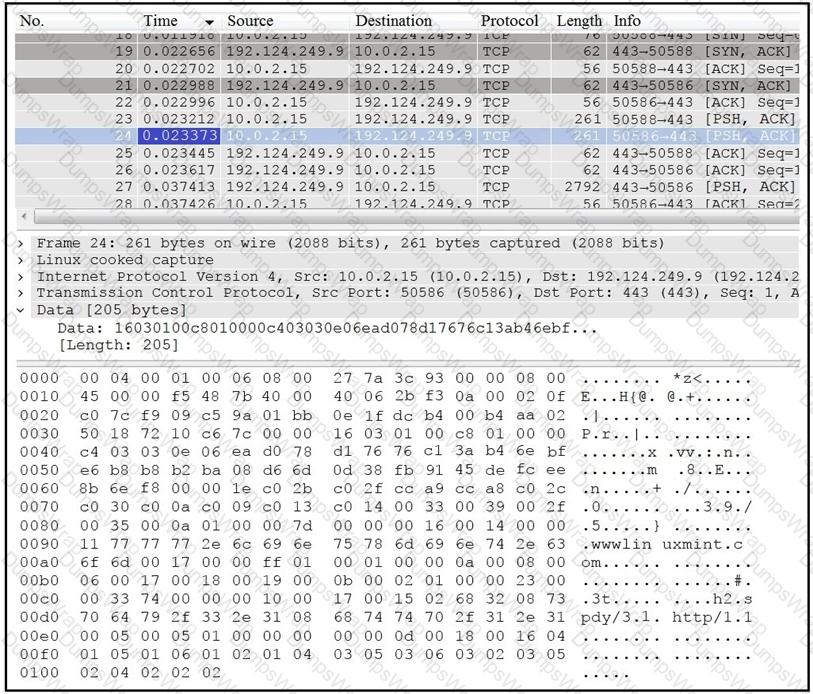
Which application protocol is in this PCAP file?
The SOC team detected an ongoing port scan. After investigation, the team concluded that the scan was targeting the company servers. According to the Cyber Kill Chain model, which step must be assigned to this type of event?
What are two categories of DDoS attacks? (Choose two.)
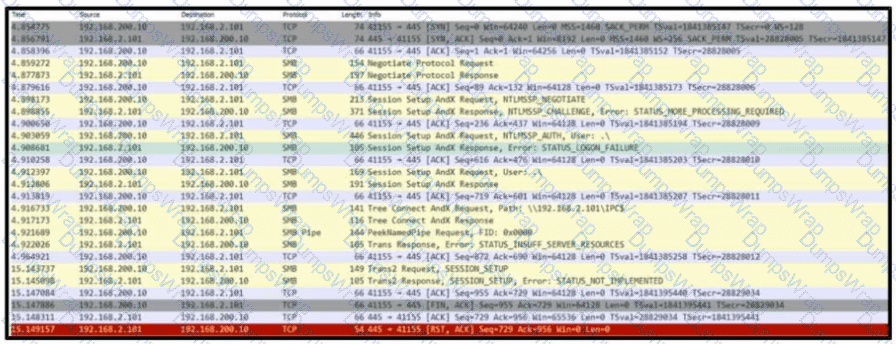
Refer to the exhibit. Based on the .pcap file, which protocol's vulnerability has been exploited to establish a session?
A security engineer must protect the company from known issues that trigger adware. Recently new incident has been raised that could harm the system. Which security concepts are present in this scenario?
Which step in the incident response process researches an attacking host through logs in a SIEM?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Which type of data collection requires the largest amount of storage space?
Refer to the exhibit.
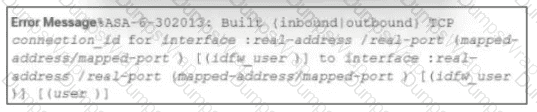
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
Which two components reduce the attack surface on an endpoint? (Choose two.)
What is vulnerability management?
What is the principle of defense-in-depth?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
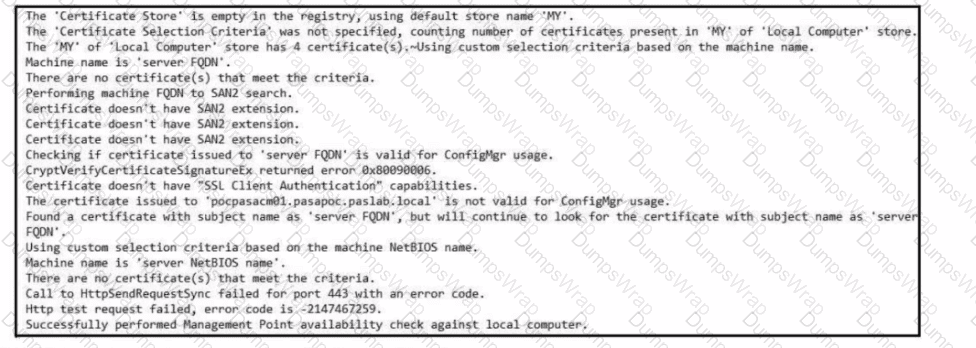
Refer to the exhibit. Which set of actions must an engineer perform to identify and fix this issue?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
Refer to the exhibit.

An engineer received a ticket about a slowed-down web application. The engineer runs the #netstat -an command. How must the engineer interpret the results?
What is a difference between tampered and untampered disk images?
What is a difference between SOAR and SIEM?
Which type of evidence supports a theory or an assumption that results from initial evidence?
Refer to the exhibit.
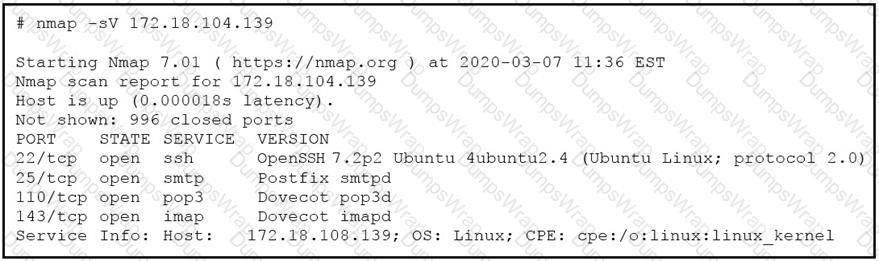
What does the output indicate about the server with the IP address 172.18.104.139?
Which process represents the application-level allow list?
What is corroborating evidence?
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
Which management concept best describes developing, operating, maintaining, upgrading, and disposing of all resources?
What is the advantage of agent-based protection compared to agentless protection?
A data privacy officer at a marketing firm has received a request from a former client to delete all personally sensitive information held by the company. The firm operates globally and follows international data protection standards. The only information retained about the client is a unique customer ID, "051473912", which is not directly tied to the name, address, or any other identifiable details. Which action should the data privacy officer take?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
What is a description of a social engineering attack?
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
What is an evasion technique?
Which of these describes volatile evidence?
What does cyber attribution identify in an investigation?
Which access control should a chief information security officer select to protect extremely sensitive data categorized at various levels of confidentiality?
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
Refer to the exhibit.

Which component is identifiable in this exhibit?
An employee received an email from a colleague’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender’s address. What does this incident describe?
Which HTTP header field is used in forensics to identify the type of browser used?
What are two differences and benefits of packet filtering, stateful firewalling, and deep packet inspections? (Choose two.)
Which principle reduces the risk of attackers gaining access to sensitive data by compromising a low-level user account?
Which action matches the weaponization step of the Cyber Kill Chain Model?
Why is encryption challenging to security monitoring?
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
What makes HTTPS traffic difficult to monitor?
Refer to the exhibit.
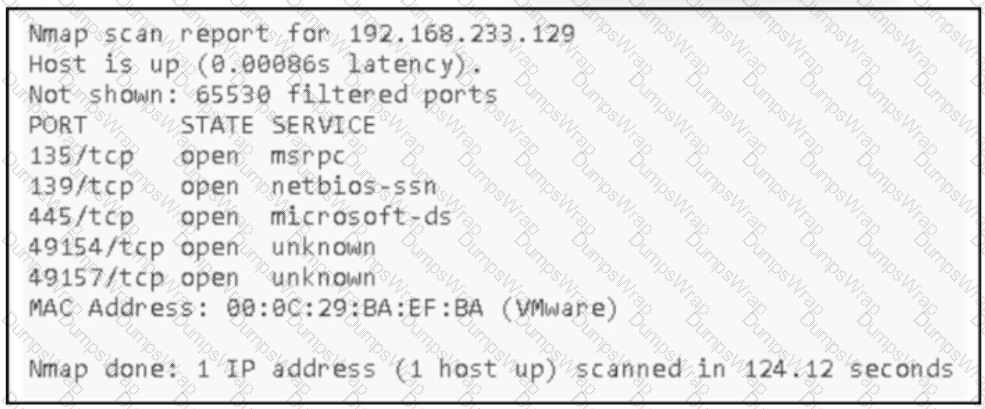
An attacker Infiltrated an organization's network and ran a scan to advance with the lateral movement technique. Which two elements from the scan assist the attacker? (Choose two.)
Refer to the exhibit.
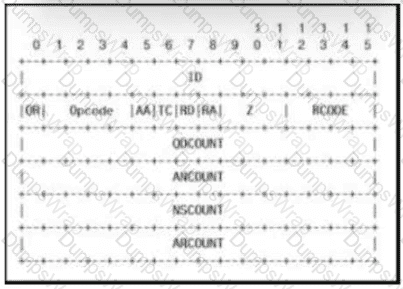
Which field contains DNS header information if the payload is a query or a response?
Which element is included in an incident response plan as stated m NIST SP800-617
Which statement describes patch management?
How does a certificate authority impact security?
What is an attack surface as compared to a vulnerability?
What is an incident response plan?
Which are two denial-of-service attacks? (Choose two.)
What describes the difference when comparing attack surface and vulnerability in practice?
Which evasion method involves performing actions slower than normal to prevent detection?
Which type of data must an engineer capture to analyze payload and header information?
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?

 Graphical user interface, application Description automatically generated
Graphical user interface, application Description automatically generated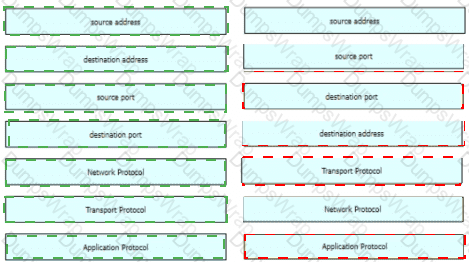
 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated