DevNet Associate (DEVASC) Questions and Answers
A developer plans to deploy a new application that will use an API to implement automated data collection from Webex with these requirements:
The application was created by using the request library.
Requires HTTP basic authentication.
Provides data in JSON or XML formats.
Which Cisco DevNet resource helps the developer with how to use the API?
A developer attempts to refactor and improve the application code. It is noticed that the code contains several pieces of key information that could be a security threat if this code is accessible by those who are not
authorized to this data. Which approach addresses the security concerns noticed by the developer?
What is a feature of a MAC address?
A developer must test the performance and reliability of an application. After functional and load tests are run, the application crashes due to traffic spikes from users. Which type of API constraint must be implemented to maintain reliability?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
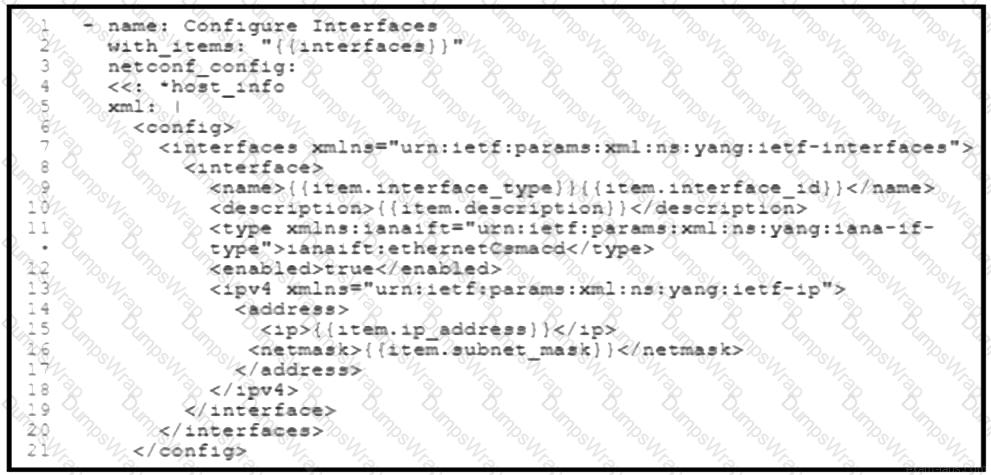
Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module?
Why would a developer compare a current version of code to a previous version?
Which IP service synchronizes the time across devices?
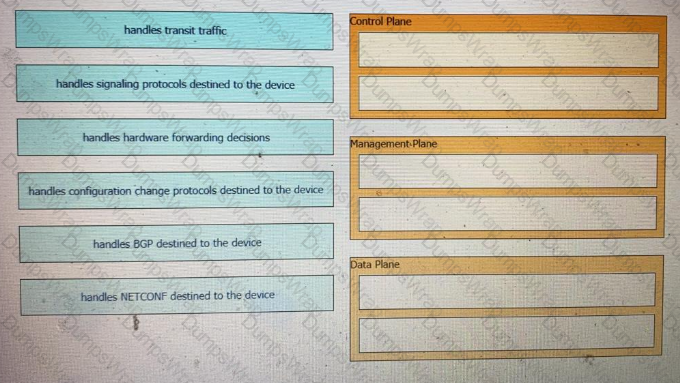
Which two protocols are associated with the control plane on a network device? (Choose two.)
An engineer must run tests on several Cisco controllers. Due to the nature of the task, the infrastructure must be running at all times and have access to APIs. Which Cisco DevNet source must the engineer use?

Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the ..call?
A)

B)

C)

D)

What is a capability of model-driven programmability for infrastructure automation?
A customer's cloud services must:
Migrate services to another data center on demand.
Save the operational state of the machine on demand.
Support Windows and Linux GUIs.
Maximize hardware utilization.
Which type of deployment meets these requirements?
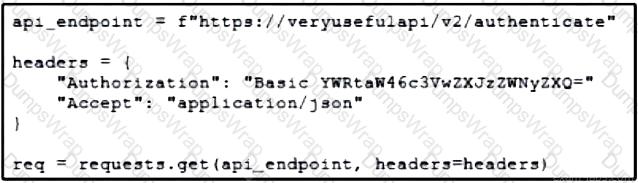
Refer to the exhibit. A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer's account?
Which protocol is used for clock synchronization between network devices?
What is a procedural component of CI/CD pipelines?
What is the purpose of Infrastructure as Code?
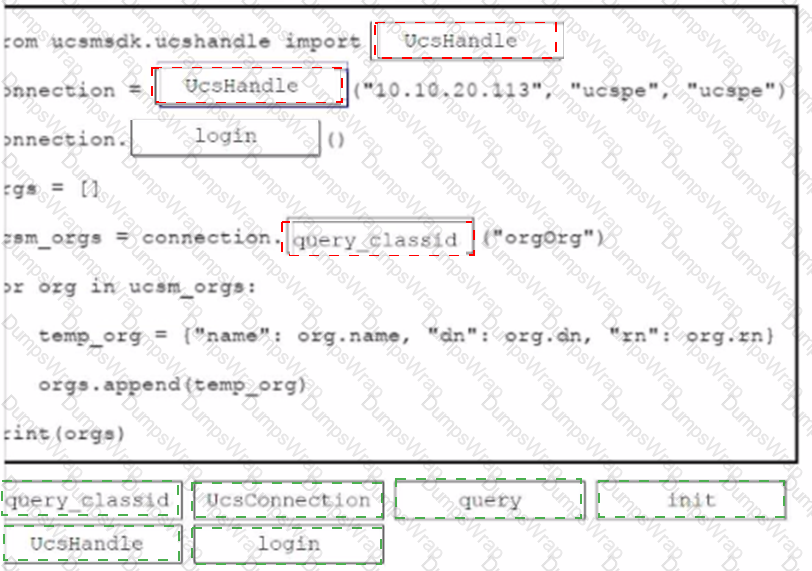
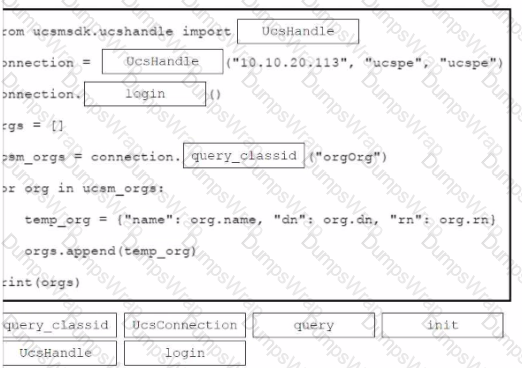
Refer to the exhibit.
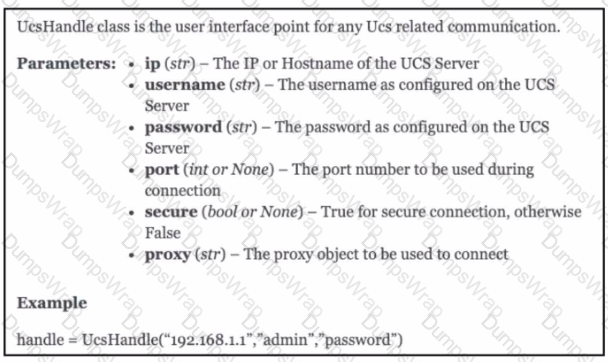
An engineer needs to retrieve all the organizations in a Cisco UCS Manager deployment. Drag and drop the code snippets from the bottom onto the blanks in.. Python script to print the information to standard output. Some options may be used more than once. Not all options are used.
A lead engineer is managing the development of a web application with a team of remote developers using Git as the version control system. What is the advantage of a version Control system that allows developers to pick code from any part of the project and perform updates on it?
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements?
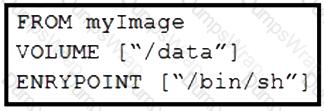
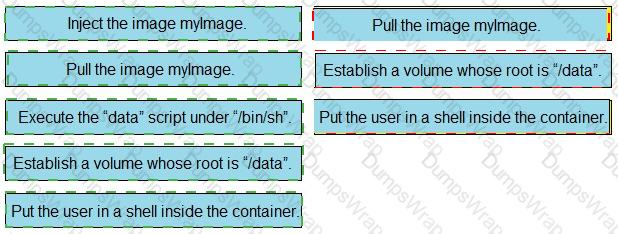
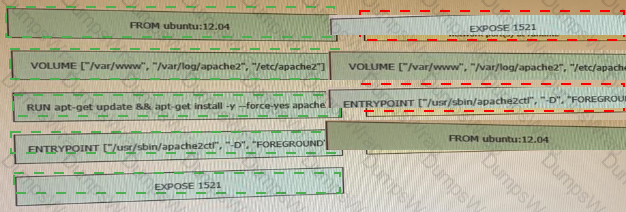
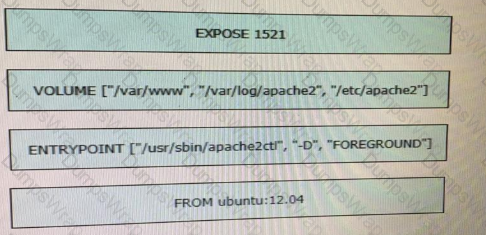
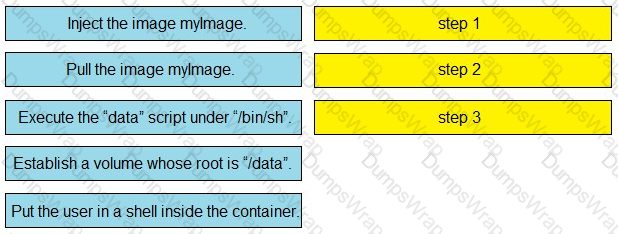
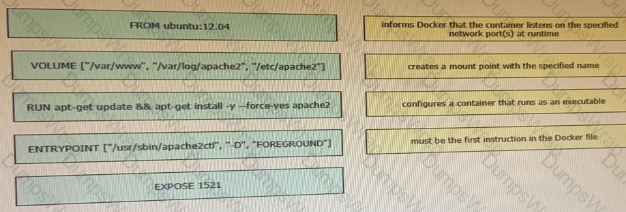
Refer to the exhibit. Drag and drop the actions from the left that the contents of this Dockerfile accomplish onto the right. Not all options are used.
What is a characteristic of RPC APIs compared to REST APIs?
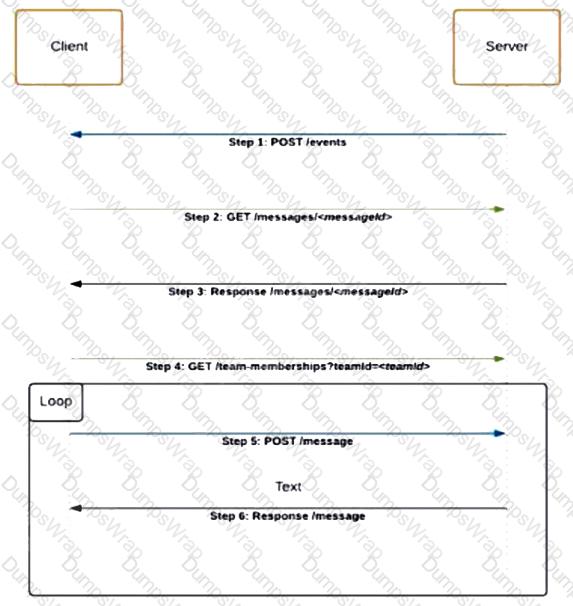
Refer to the exhibit. Which code snippet represents the sequence.
What is a benefit of a distributed version control system?
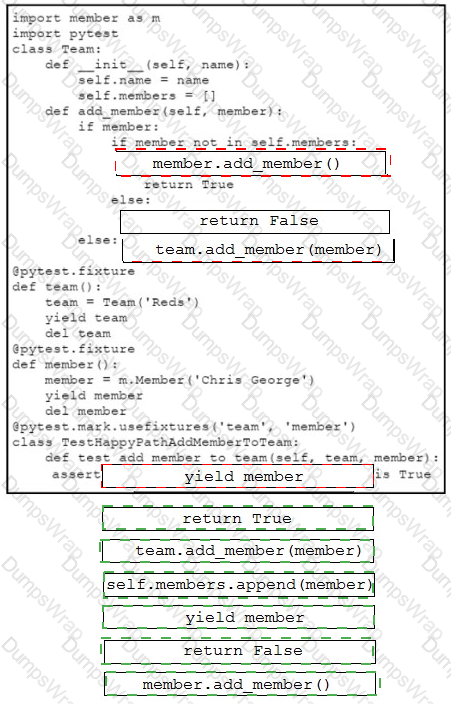
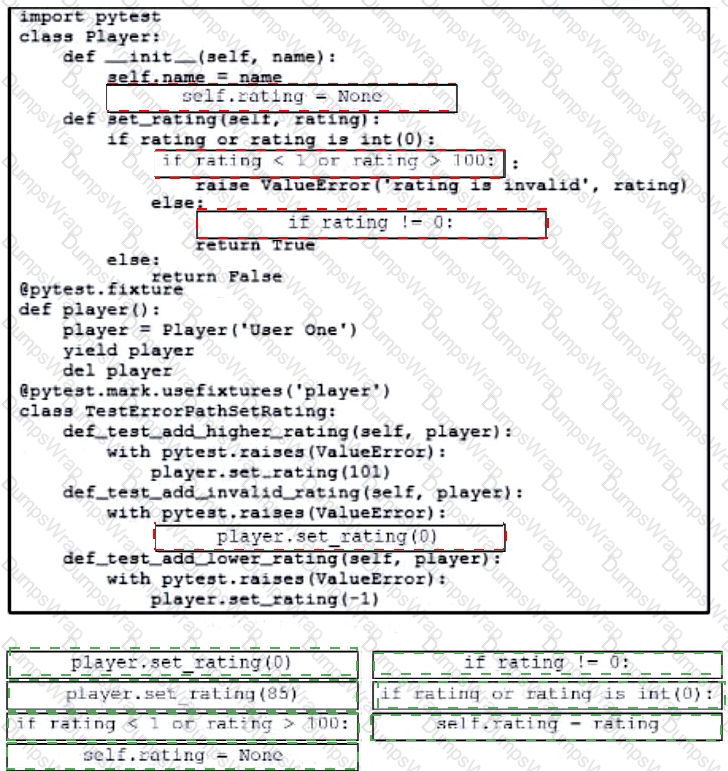
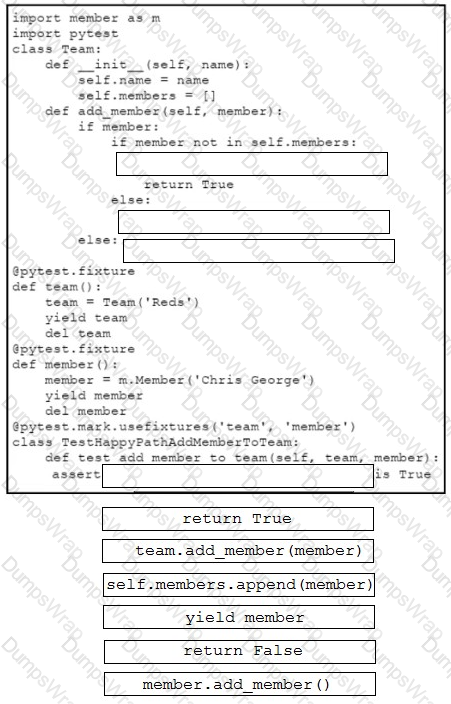
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the happy path scenario. Not all options are used.
Which protocol runs over TCP port 830?
Which network device plane is responsible for handling QoS?
What is a function of the default gateway in a network?
Which TCP port is used to connect to a network device by using Telnet?
Refer to the exhibit.
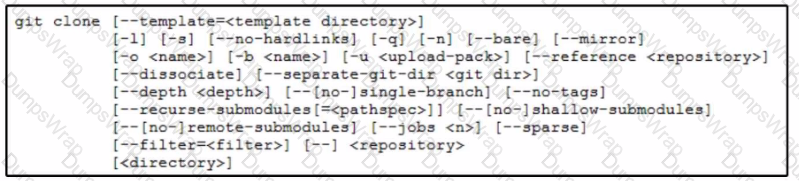
A network engineer must improve the fabric discovery process in a data center. The engineer wants to check current ACI scripts in the myproject repository and clone them to a folder named aci. The engineer will optimize the scripts from the new folder. Which command performs this task on the Git repository?
A)

B)

C)

D)

Drag and drop the code from the bottom onto the box where the code is missing to complete the error path scenario. Not all options are used.
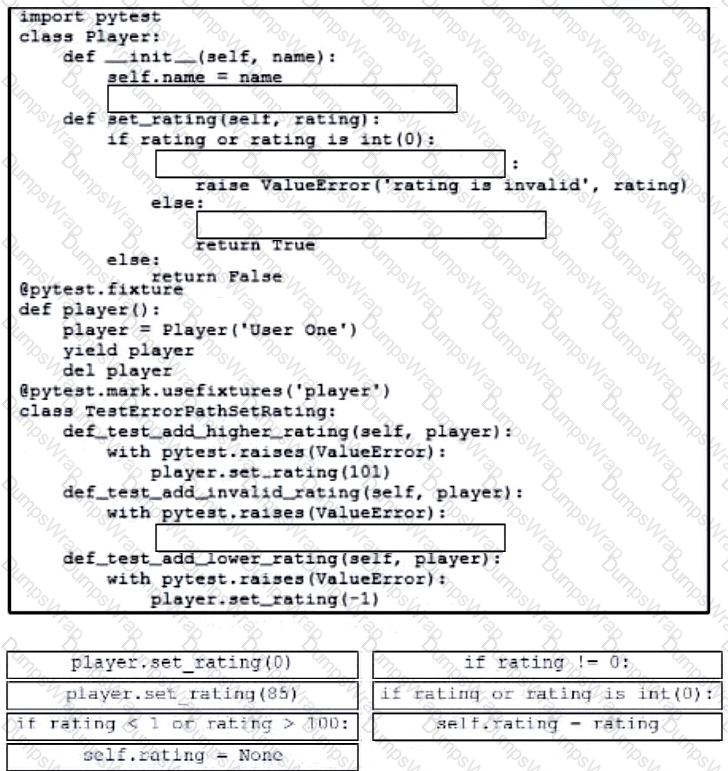
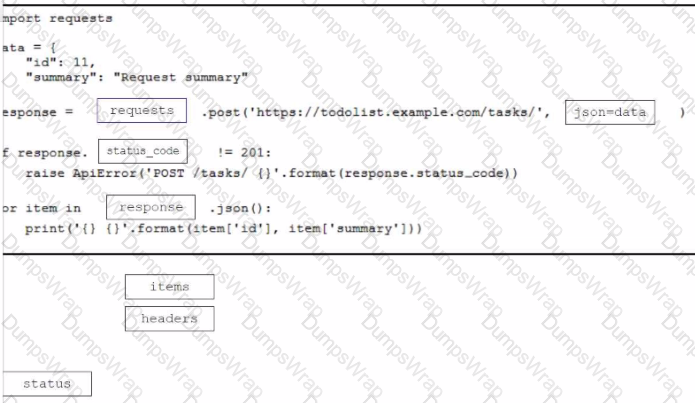
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
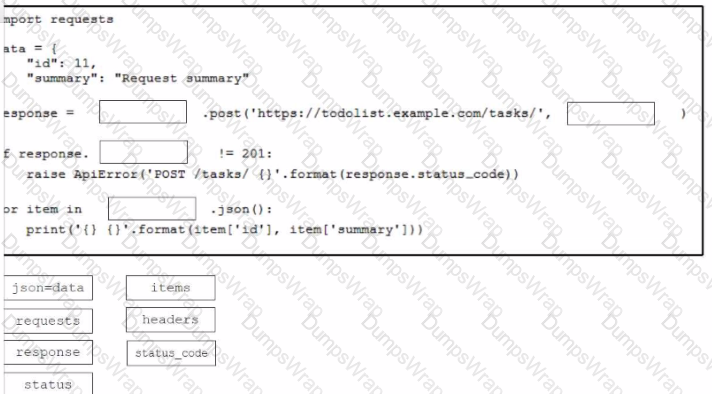
What is a capability of the AXL API?
What is a capability of Ansible playbooks?
A developer has experienced security issues with a previously developed application. The API offered by that application is open and without any constraints. During a recent attack, the application was overloaded with API requests. To address this issue, an API constraint is implemented to protect the application from future attacks or any sudden throttling. Which API constraint must the application developer implement in this situation?
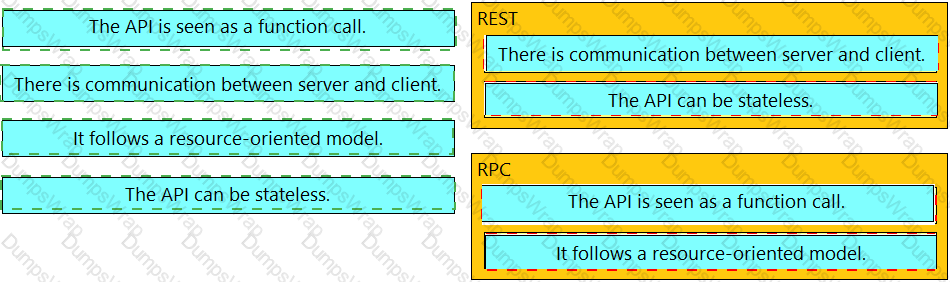
Drag and drop the API characteristics from the left onto the categories on the right.
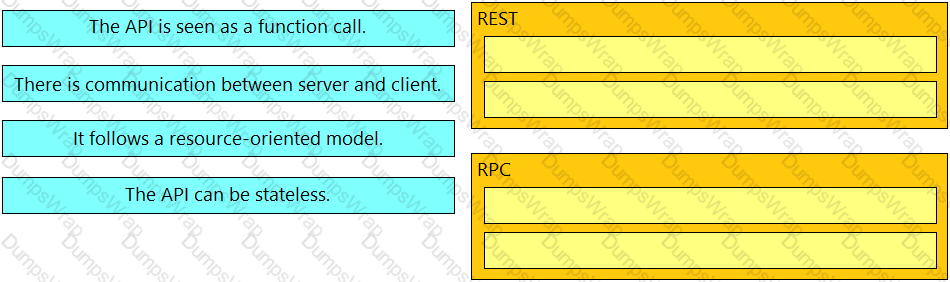
A developer pushes an application to production. The application receives a webhook over HTTPS without a secret. The webhook information contains credentials to service in cleartext. When the information is received, it is stored in the database with an SHA-256 hash. Credentials to the database are accessed at runtime through the use of a vault service. While troubleshooting, the developer sets the logging to debug to view the message from the webhook. What is the security issue in this scenario?
To which stage of development do Infrastructure as Code principles relate?

Refer to the exhibit. Which HTTP code is returned after the RESTCONF query is executed?
Refer to the exhibit.
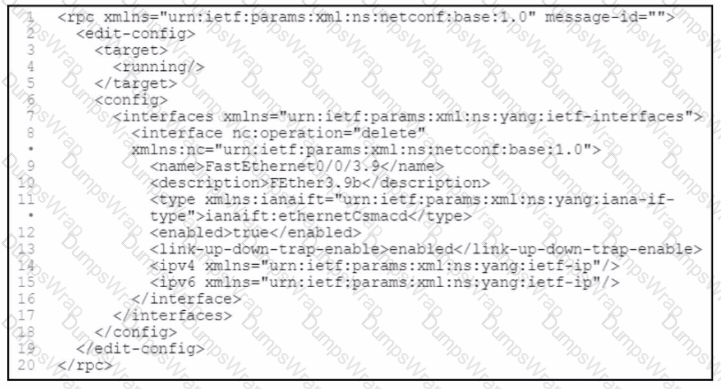
A developer writes an application that refines data in temporary secure file storage hosted on the public cloud. Data will be deleted after processing and does not contain any private information. What is the advantage that a public cloud deployment provides to the developer?
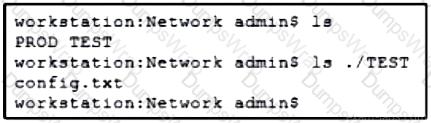
Refer to the exhibit. A network engineer must copy the “config.txt” file from directory TEST to directory PROD. The copied file must also be renamed into “current.txt”. Which command must be used to accomplish these tasks?
Which HTTP error code series relates to redirection?
An engineer deploys a Cisco CSR 1000 V instance to a virtual machine. The engineer must output the device configuration in JSON format. Which protocol is used for this task?
A developer checks the performance of a web application. The application is in the local data center and uses a REST-based API. Based on the API logs, it is discovered that many its abandon API requests. Also, the response is taking too long to get back. What is the reason for this issue?
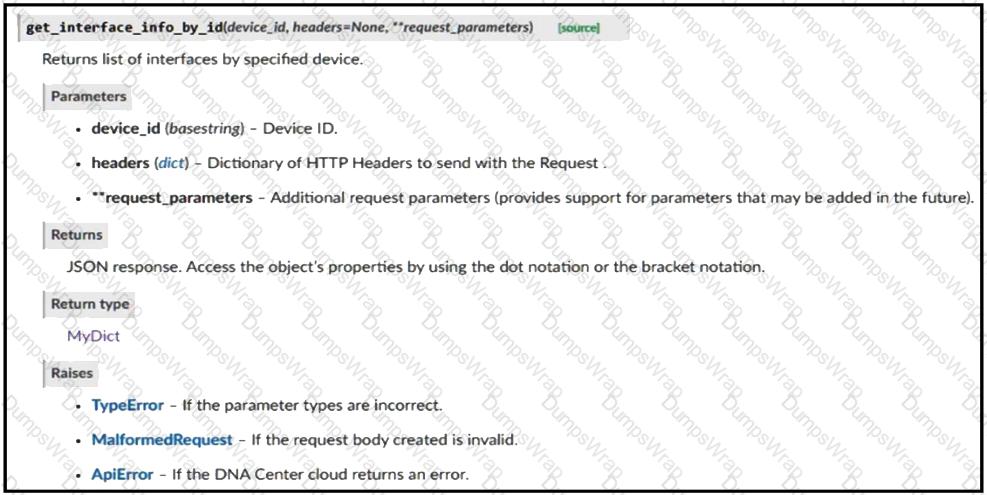
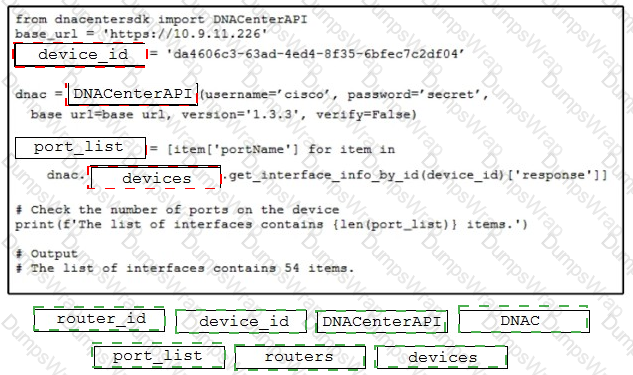
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to return the number of interfaces on a network device by using the Cisco DNA Center SDK. Not all options are used.
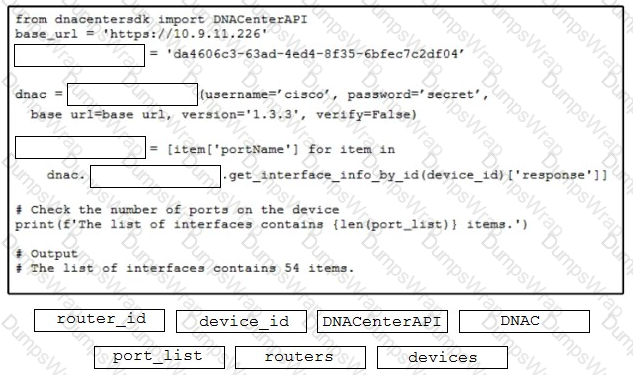

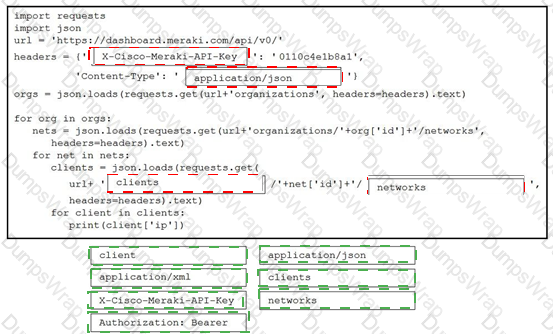
Refer to the exhibit. A developer creates a Python script by using the Cisco Meraki API. The solution must:
• Obtain a list of HTTP servers for a network named "netl".
• Print the response body if the HTTP status code is 200.
• Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
A)
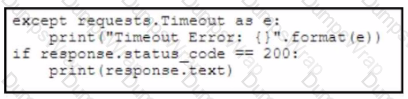
B)
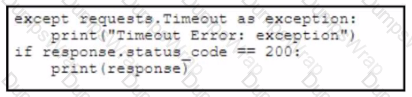
Which response status code is used by a RESTful interface to indicate successful execution of a request?
Which two types of NAT are used in a network? (Choose two.)
Refer to the exhibit.
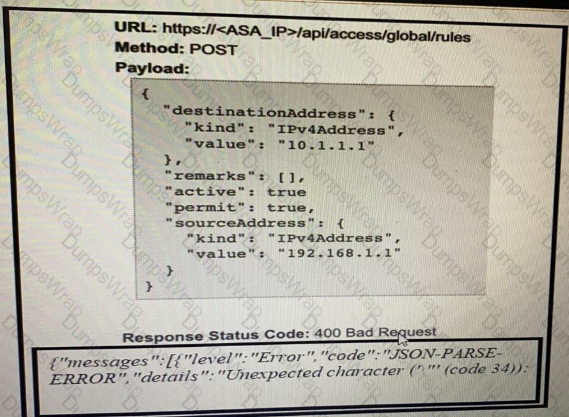
What caused the error in this API request?
Refer to the exhibit.
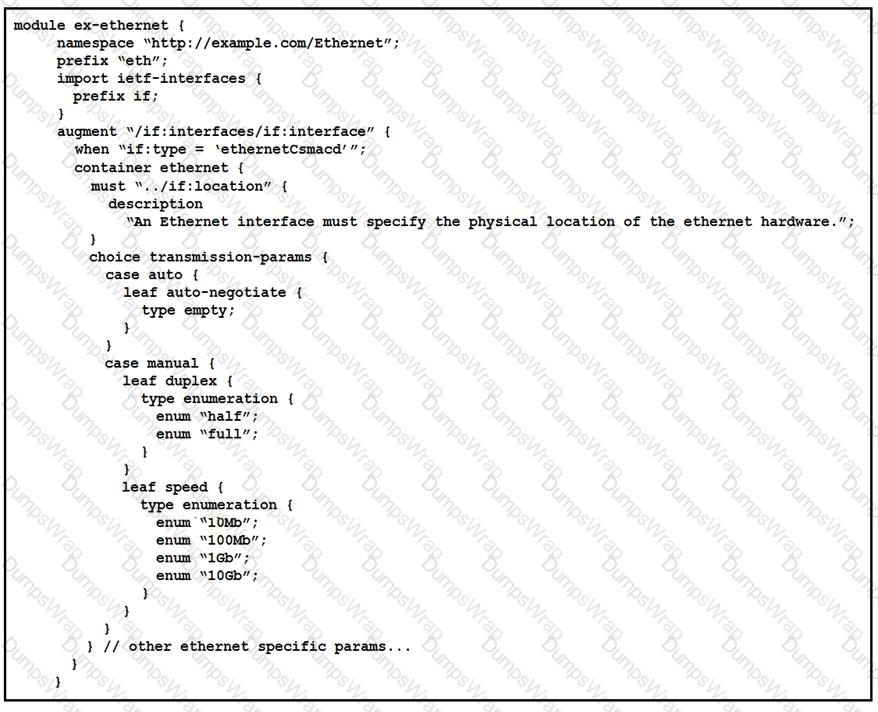
What is represented in this YANG module?
What are the two purposes for using a VLAN in a network? (Choose two)
Which two protocols are used to apply a configuration change on a Cisco IOS XE device? (Choose two)
Which way should be used to safely the API keys?
Which device is used to transport traffic from one broadcast domain to another broadcast domain?
Which task is performed because the test-driven development approach is being used?
Which statement about authentication a RESTCONF API session with a router that runs Cisco IOS XE software is true?
What is a tenet of test-driven development?
Which two query types does a client make to a DNS server? (Choose Two)
Which model-driven programmability protocol does Cisco IOS XE Software support?
What are two advantages of the Model-view-controller software design pattern? (Choose two.)
What is the purpose of a firewall in application deployment?
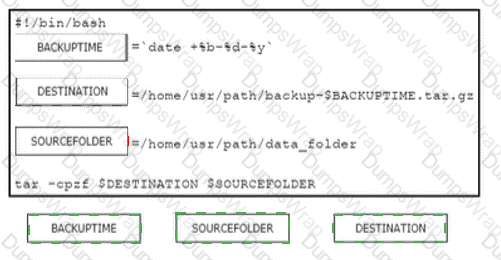
Refer to the exhibit.
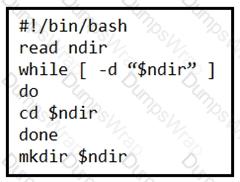
What is the action of the Bash script that is shown?
What is used in Layer 2 switches to direct packet transmission to the intended recipient?
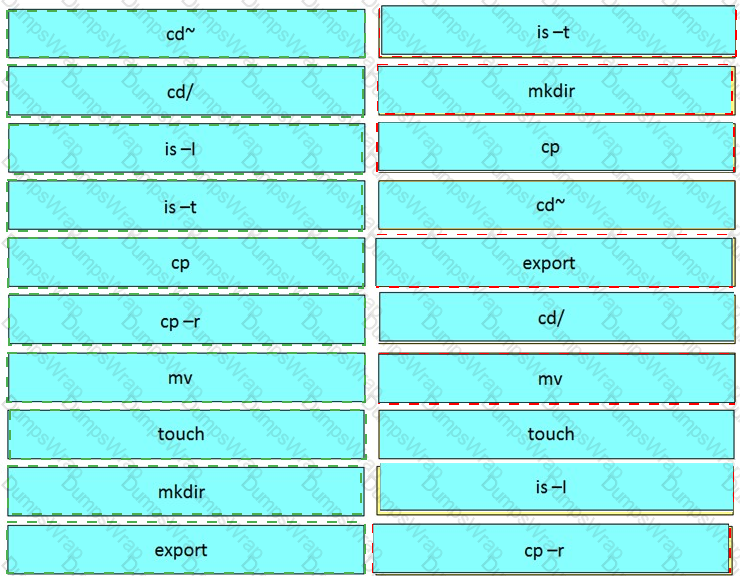
Drag and Drop the Bash commands from the left onto the correct actions on the right.
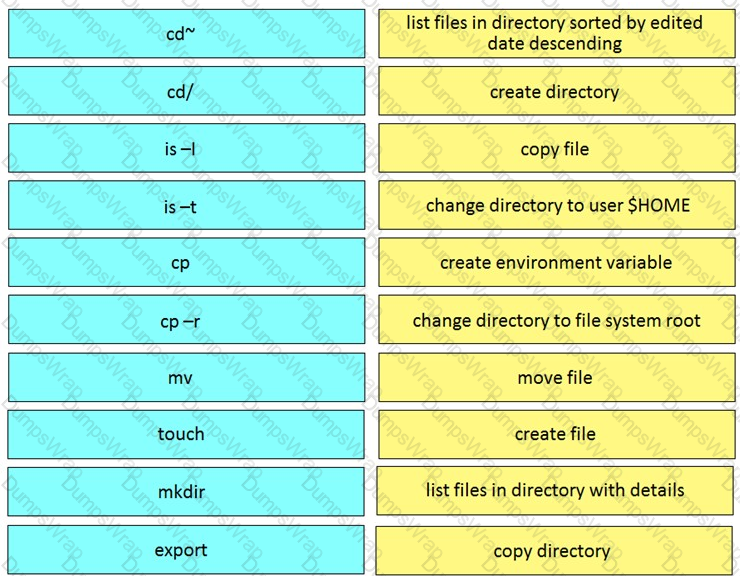
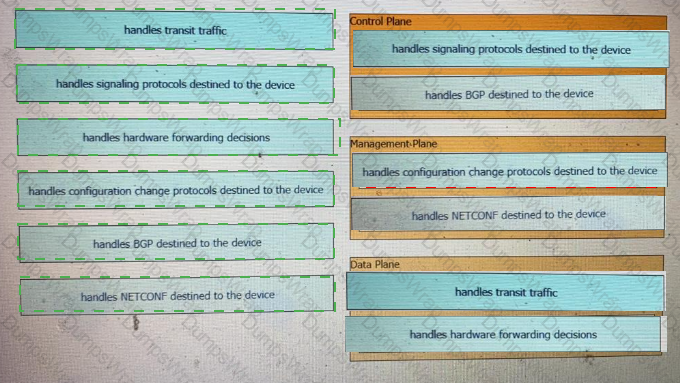
Drag and drop the function on the left onto the type of plane that handles the function on the right.
Refer to the exhibit.
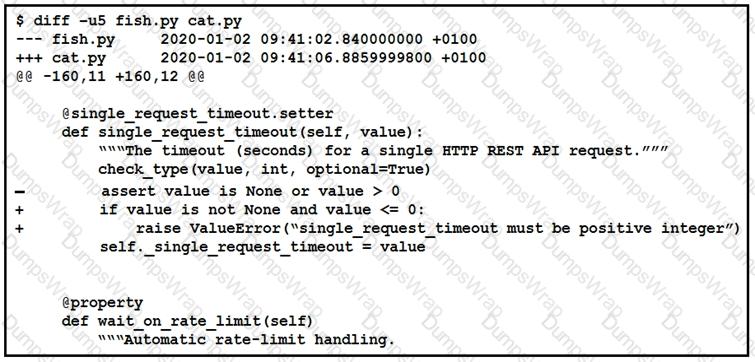
The output of a unified diff when comparing two versions of a python script is shown. Which two “single_request _timeout ()”

How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
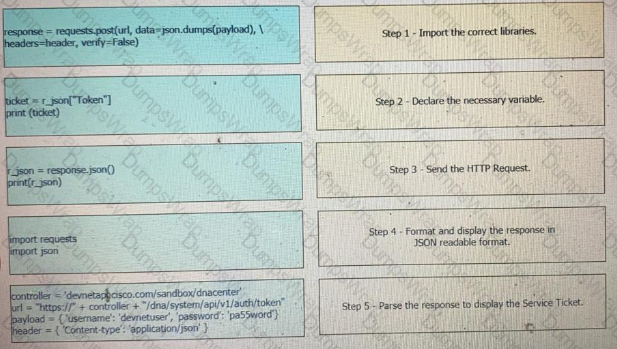
Drag and drop the Python code from the left onto the correct step on the right to call a REST API.
What is the purpose of the Cisco VIRL software tool?
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco DNA center API.
Which two statement describe the role of an artifact repository in a CI/CD pipeline? (Choose two.)
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
Refer to the exhibit.
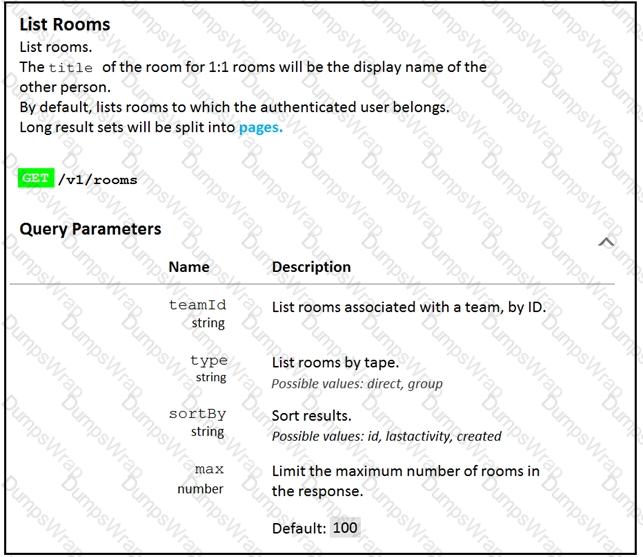
Fill in the blank to complete the query parameter and value so that the result set is returned in reverse chronological order (most recent first) based on when message were entered.

Which two NETCONF operations cover the RESTCONF GET operation? (Choose two.)
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device mut be at fault?
Which description of a default gateway if true?
Refer to the exhibit.
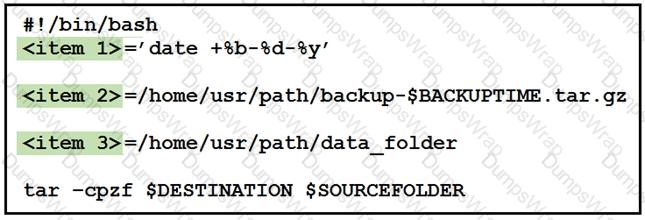
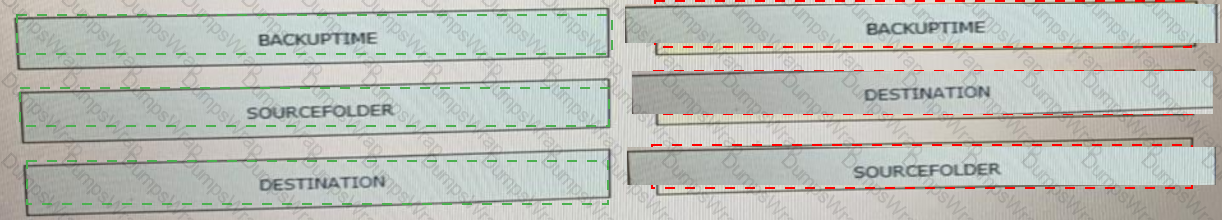
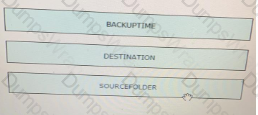
Drag and drop the variables from the left onto the item numbers on the right that match the missing assignments in the exhibit.
Which service provides a directory lookup for IP addresses and host names?
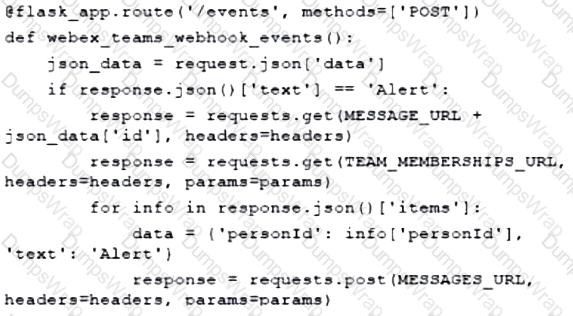
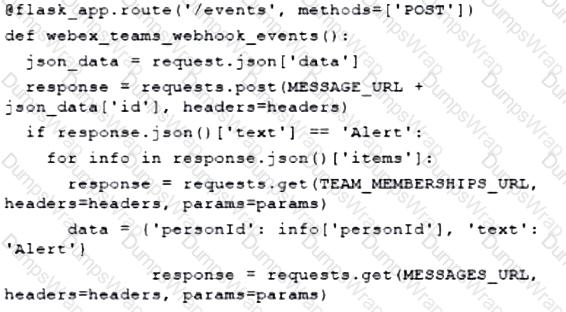
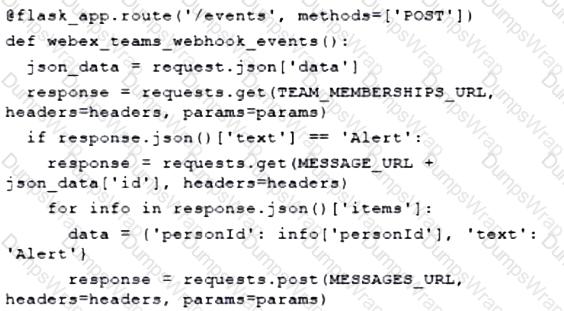
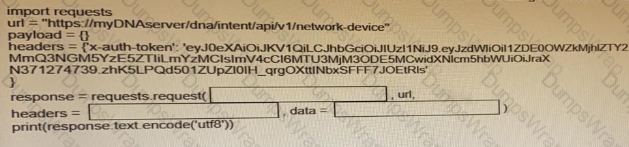
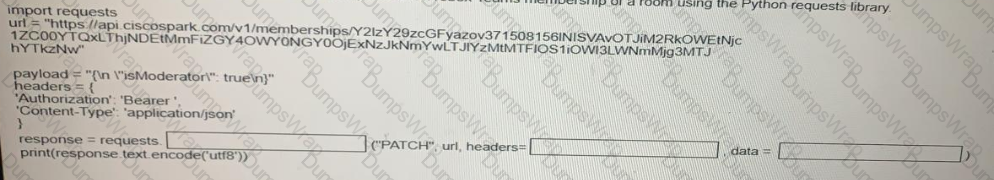
Fill in the blanks to complete the Python script to update the Webex Teams membership of a room using the Python requests library import requests
Which network device monitors incoming and outgoing traffic and decides whether to allow or block specific traffic based on a defined set of rules?
Refer to the exhibit.
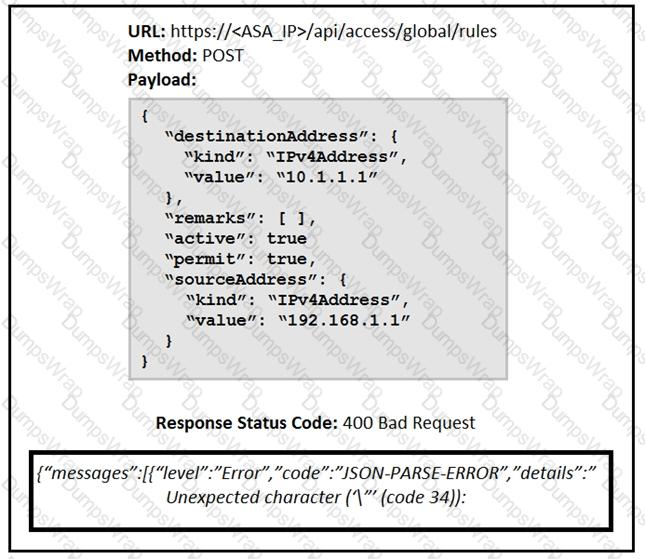
What caused the error in this API request?
Which principle is a value from the manifesto for Agile software development?
Fill in the blanks to complete the statement.
Given a username of “devnet” And a password “Cisco123”, applications must create a base64 encoding of the string” ____________ ” when sanding HTTP requests to an API that uses _______________ authentication.
A developer is writing an application that a REST API and the application requires a valid from the API which element of the response is used in the conditional check?
Which two statements describe the advantages of using a version control system? (Choose two.)
Refer to the exhibit.
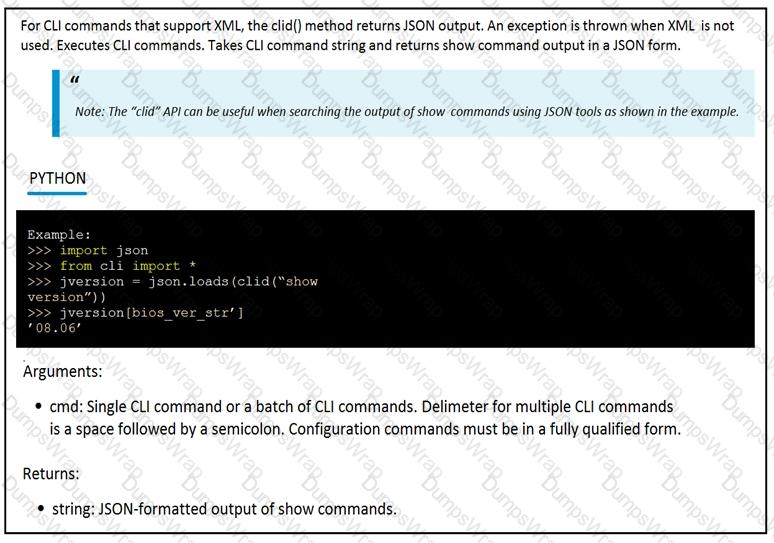
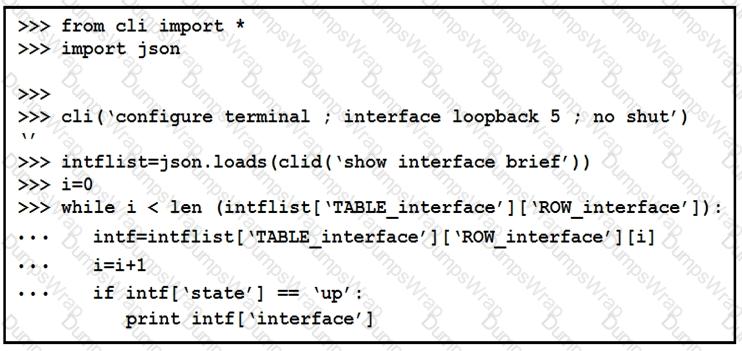
The python interpreter and the Cisco python SDK are available by default in the Cisco NX-OS software. The SDK documentation shows how the cild() API can be used when working with working with JSON and XML. What are two effect of running the script? (Choose two.)
Drag and drop the Docker file instructions from the onto correct descriptions on the right. Not all options are used.
Users cannot access a webserver and after the traffic is captured, the capture too* shows an ICMP packet that reports "communication administratively prohibited" What Is the cause of this webserver access Issue?
What is the Git command to delete a local branch named “experiment” without a warning?
Which two statements are true about Cisco UCS manager, Cisco Intersight APIs? (Choose two.)
Which detail is included in a routing table?
Refer to the exhibit.
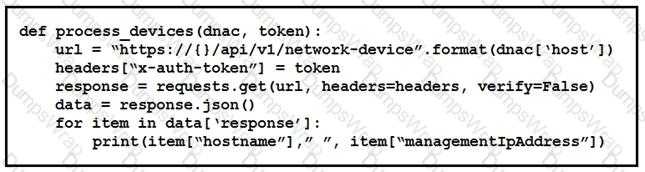
What is the function of the python script?
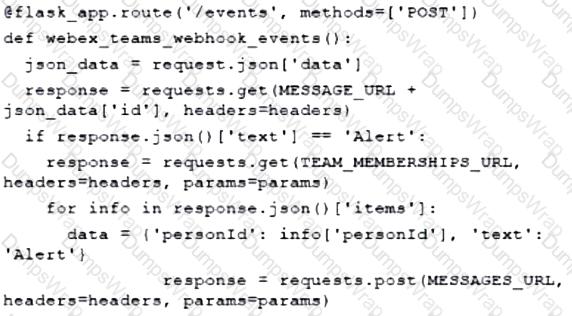
Which two descriptions can be given to an application that is interacting with a webhook? (Choose two.)
In test-driven development, what are two of the green bar patterns? (Choose two.)
What does a load balancer distribute in a network environment?
Which HTTP code group is issued when a request is received successfully, understood, and processed?
How does a synchronous API request differ from an asynchronous API request?
Why is refactoring done during test-driven development?
Refer to the exhibit.

A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
Refer to the exhibit.
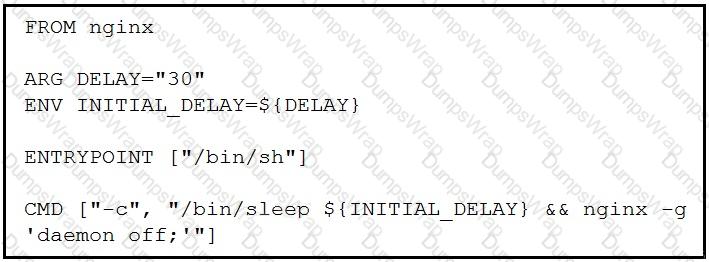
Which command, including arguments, is executed when the container starts?
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code,
which resource must be used to verify that the code works correctly?
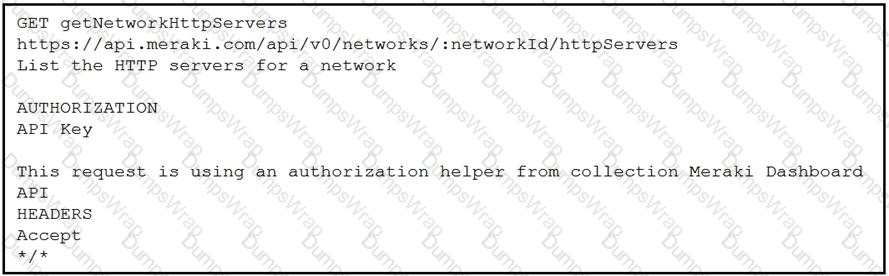
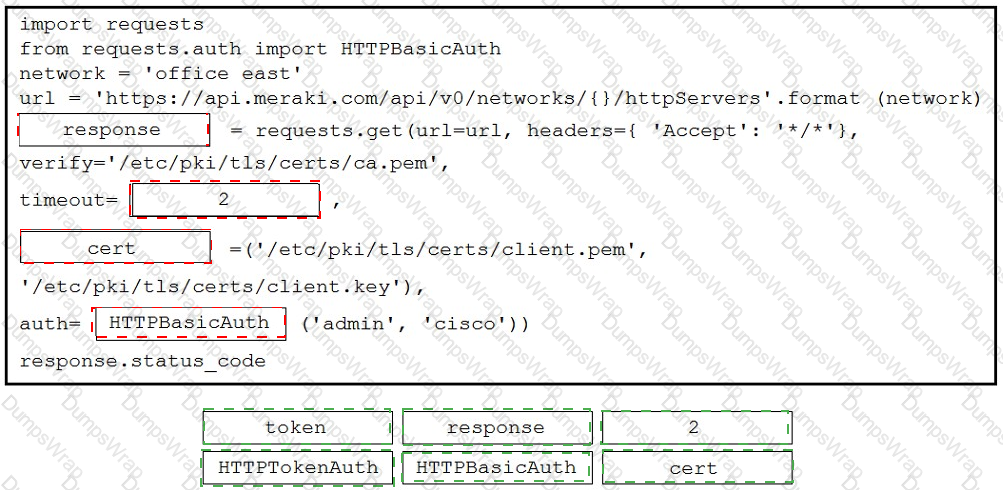
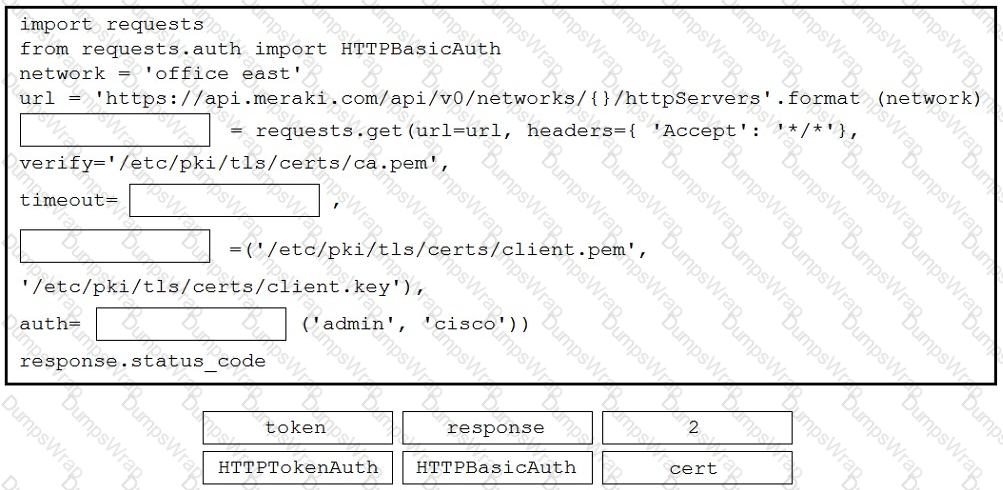
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements:
• Must time out if the response is not received within 2 seconds.
• Must utilize client certificates and SSL certificate verification.
• Must utilize basic authentication that uses a username of admin and a password of cisco.
• Must save the response to an object named response.
Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
Refer to the exhibit.
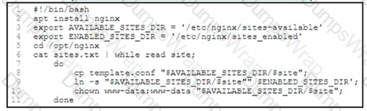
An engineer must configure a load balancer server. The engineer prepares a script to automate workflow by using Bash. The script install the nginx package, moves to the /optAtginx directory, and reads the sites M We (or further processing Based on the script workflow, which process is being automated within the loop by using the information mi sites txt?
What is the function of IP address in networking?
What are two considerations when selecting the "best route" for a network device to reach its destination? (Choose two.)
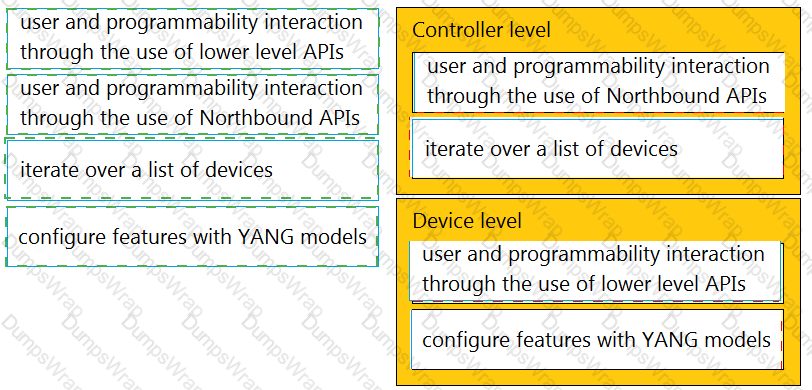
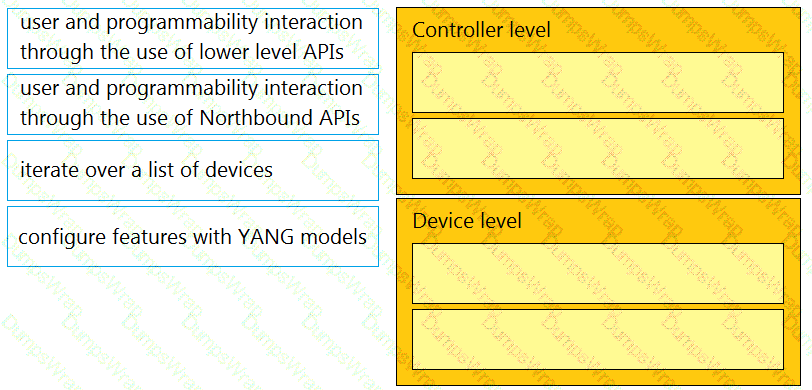
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
What is the difference between YAML and JSON data structure?
Refer to the exhibit.
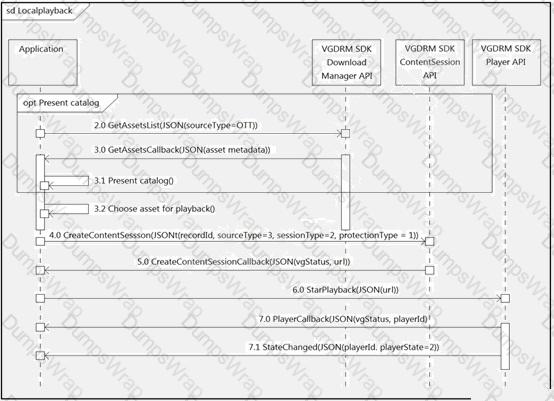
What do all the calls shown in the sequence diagram have in common?
What is a capability of the NETCONF protocol?
Refer to the exhibit.
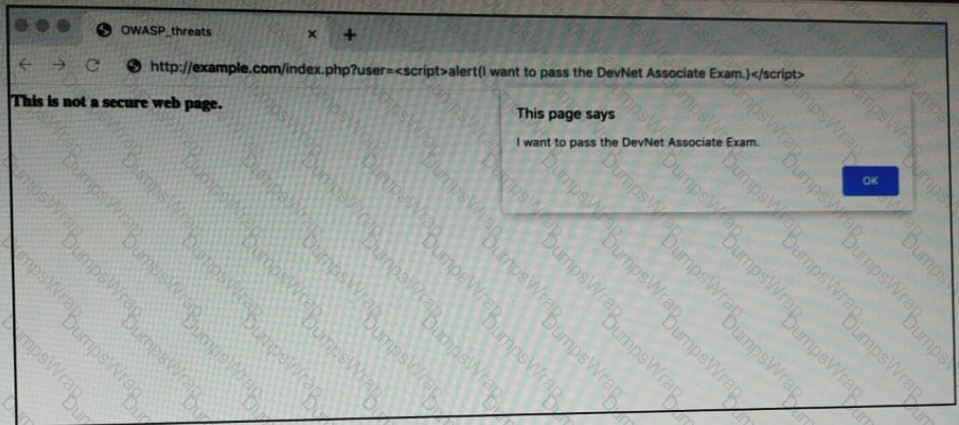
OWASP threat does this example demonstrate?
Refer to the exhibit.
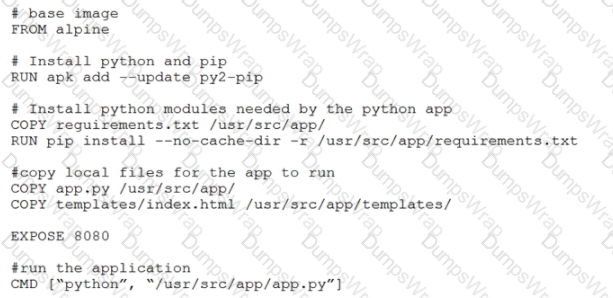
Which function does the EXPOSE line perform when building an image from this Dockerfile?
Refer to the exhibit.
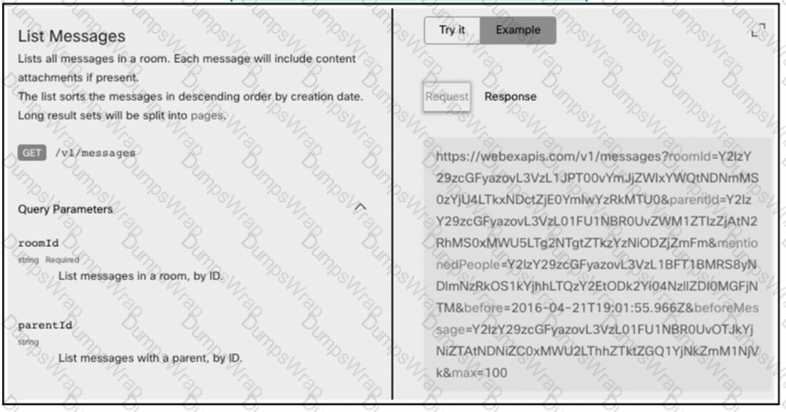
A developer needs to automatically retrieve all of the messages of a Webex room with the roomld of
HY2l2Y292cGFyazovL3Vz397748444YjU5NjAtNTk0ZJ0xMWVhLTk0Mj". Using the Webex API documentation shown, drag and drop the code snippets from below onto the code to complete the Python script to list all of the messages in the room. Not all options are used.

What are two benefits of using VLANs? (Choose two.)
How are load balancers used in modern application deployment?
How do XML and JSON compare regarding functionality?
Refer to the exhibit.

Which JSON snippet configures a new interface according to YANG model?
A)
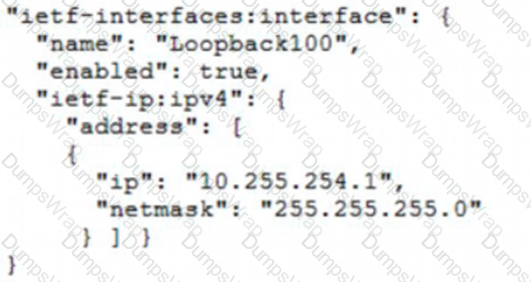
B)
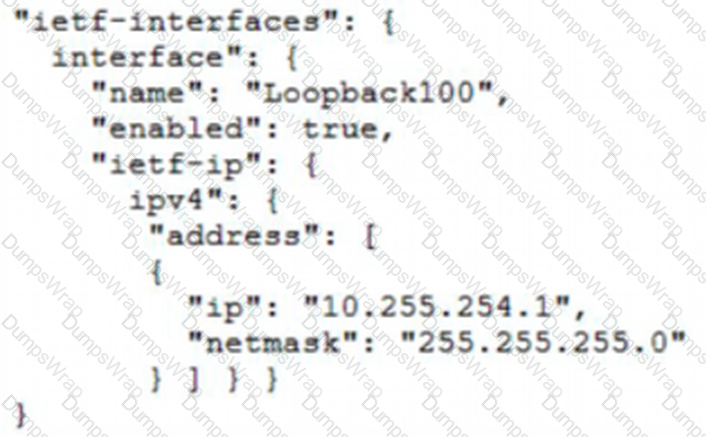
C)
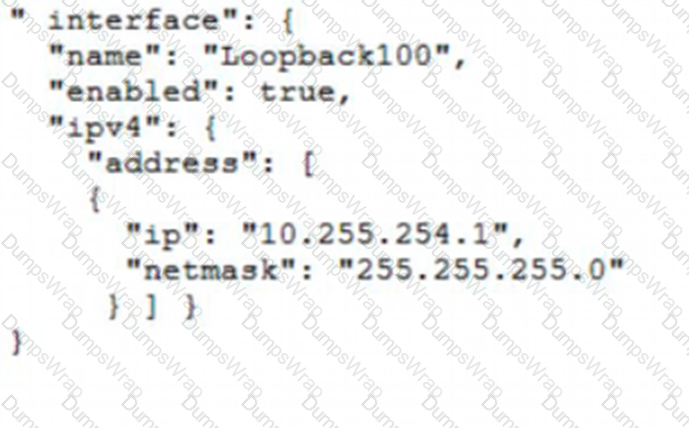
D)
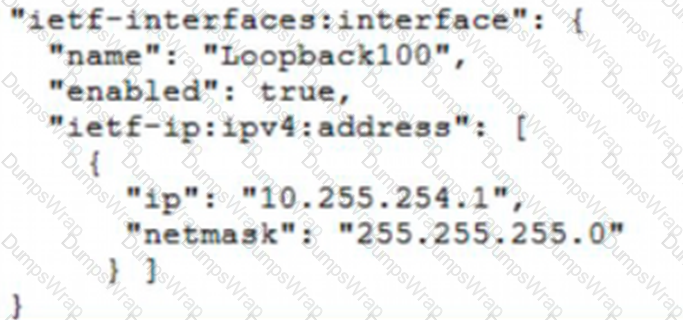
Which protocol runs over TCP port 23?
A new application is being developed with specific platform requirements. The platform and application deployment and the ongoing platform management must be fully automated. The application includes a large database component that has significant disk I/O requirements. Which application deployment type meets the requirements?
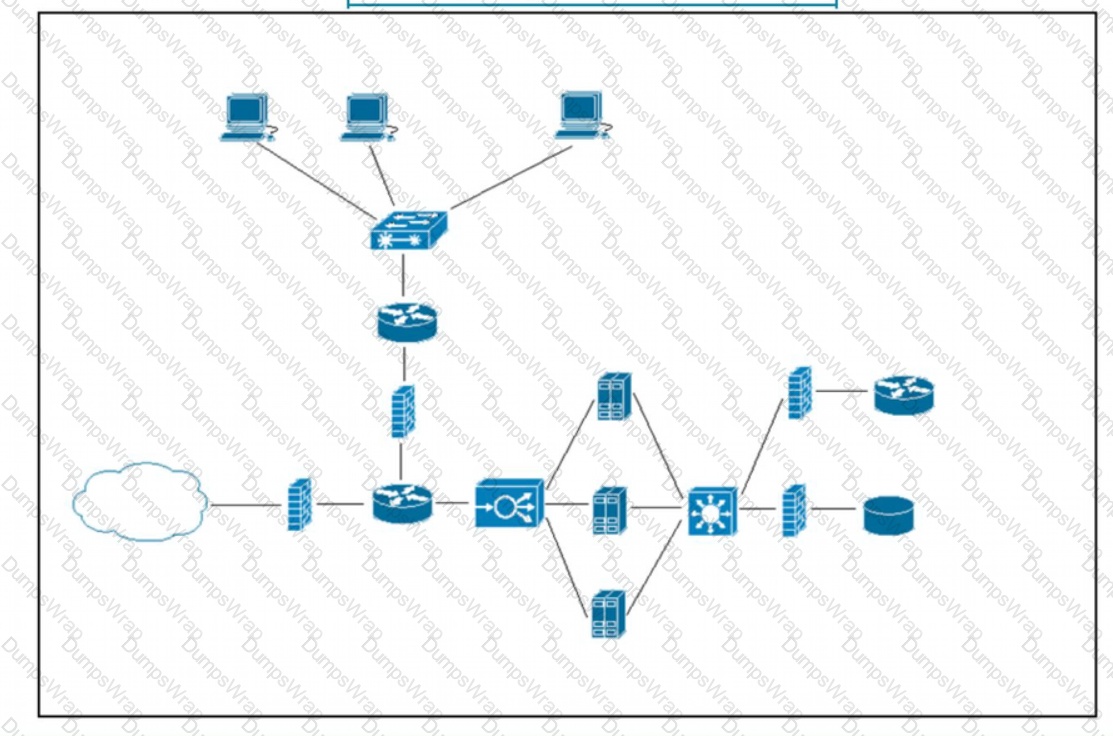
Refer to the exhibit. What does the load balancer enable in the network topology?
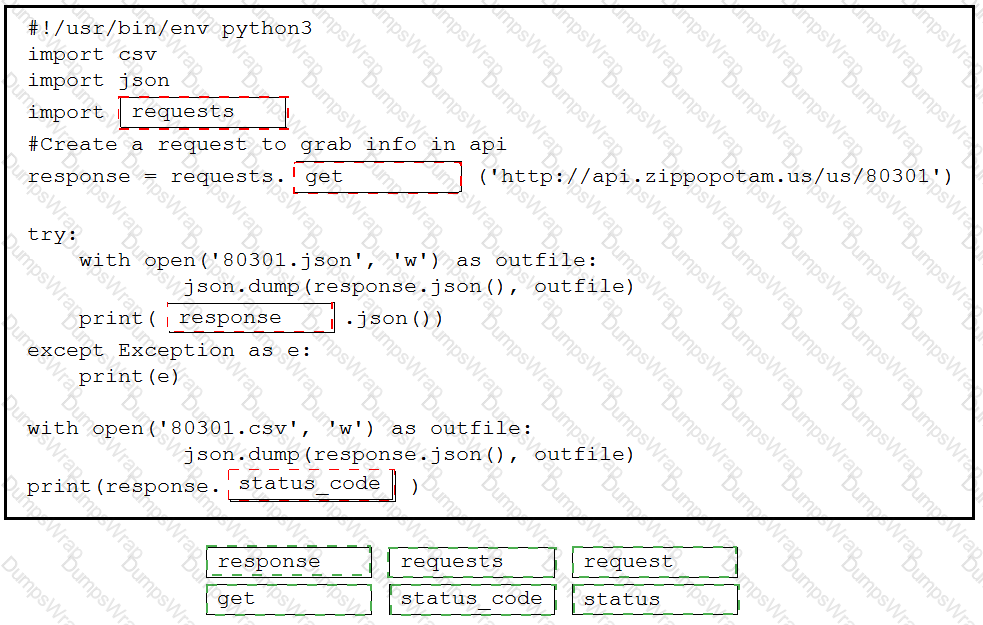
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
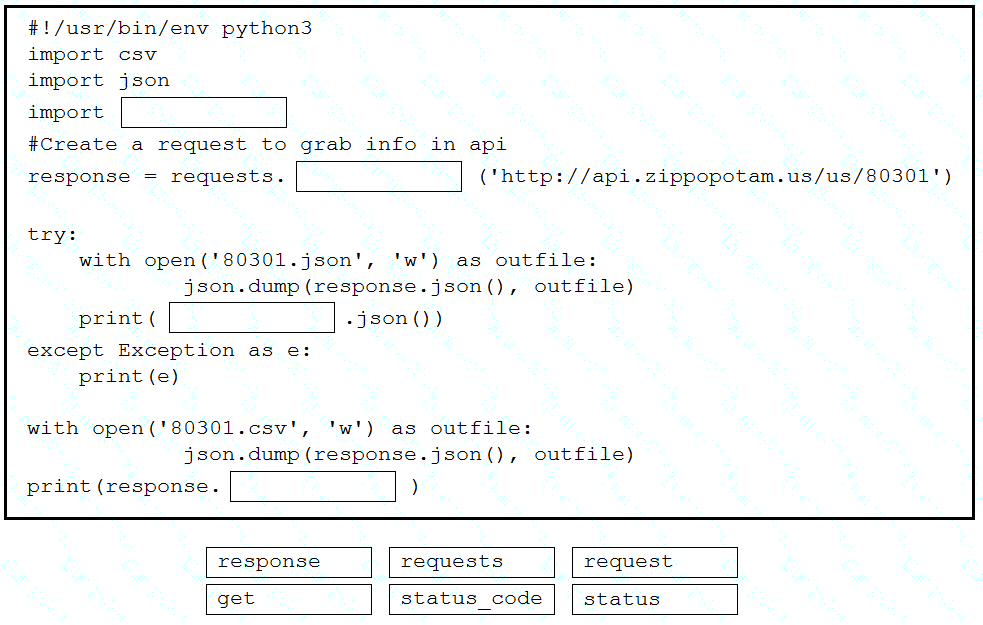
Refer to the exhibit.
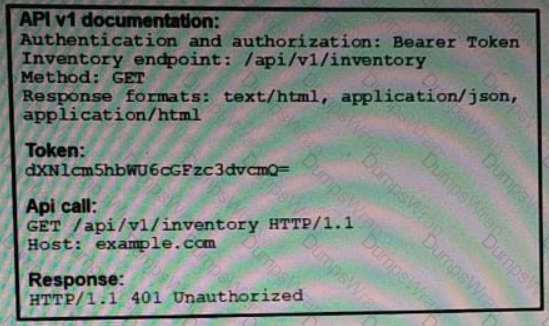
An API call is constructed to retrieve the inventory in XML format by using the API. The response to the call is 401 Unauthorized. Which two headers must be added to the API call? (Choose two.)
Which configuration management tool has an agentless capability?
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit?
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to complete a function to return all the clients on a network by using the Cisco Meraki Dashboard API. Not all options are used.
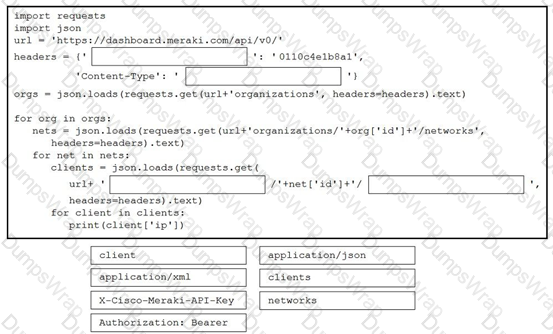
Drag and drop the code from the bottom onto the box where the code is missing in the Bash script to complete the missing assignment.
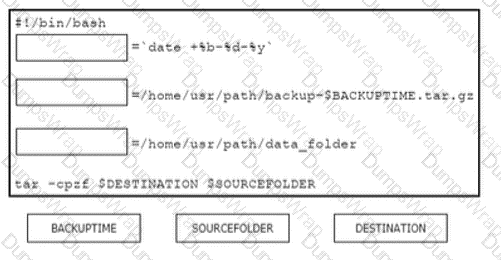
What is a benefit of a model-driven approach for infrastructure automation?
A developer has created a new image to use in a Docker build and has added a tag for the image by using the command:
$ docker tag 84fe411926287 local/app:0.4
Which command must be executed next to build the Docker image using the tag?
What are two key capabilities of Cisco Finesse? (Choose two.)
Which advantage does the agile process offer compared to waterfall software development?
What are two properties of private IP addresses? (Choose two.)
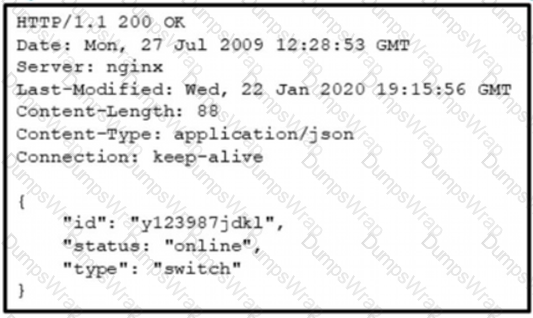
Which data is specified in the response header?
Refer to the exhibit.
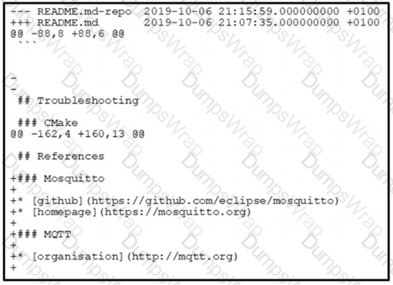
The output of the diff-u README.md-repo README.md command is shown. The original file was 165 lines long How many lines are in the edited copy of the file?
What are two use cause where webhooks are effective? (Choose two.)
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire?
Refer to the exhibit.
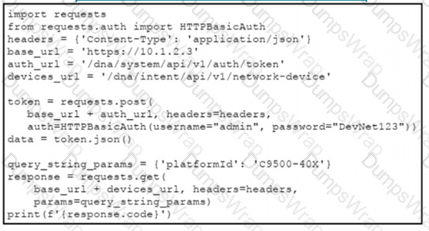
A network engineer must manage the network devices. The engineer prepares a Python scripts to authenticate to the Cisco to DNA Center API and request a device list. The device request fails and returns errors code 401. Which action solves the problem?
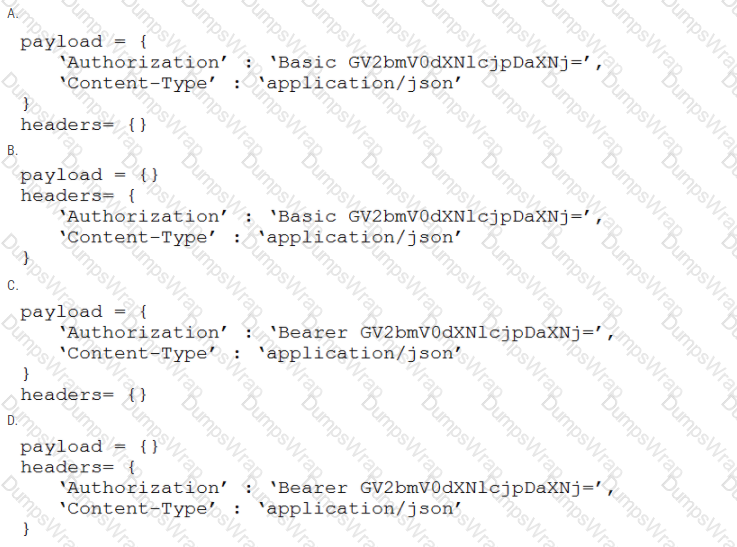
A developer is creating a script to interact with a REST API service which requires basic authentication. The credentials are "devnet:391665405" and the Base64 encoding of the credentials is "GV2bmV0dXNlcjpDaXNj=". Which payload and header combination must be used for authentication?
Refer to the exhibit.

The script returns an output of 401. To use the supplied URL. an HTTP GET request must Be sent with an Authorization header. The header value is a BaseG4 encoded concatenation of the username and password. Which action must be taken to return an output of 200?
Which Cisco product provides malware and content filtering through DNS?
What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software?