Implementing Cisco Application Centric Infrastructure (300-620 DCACI) Questions and Answers
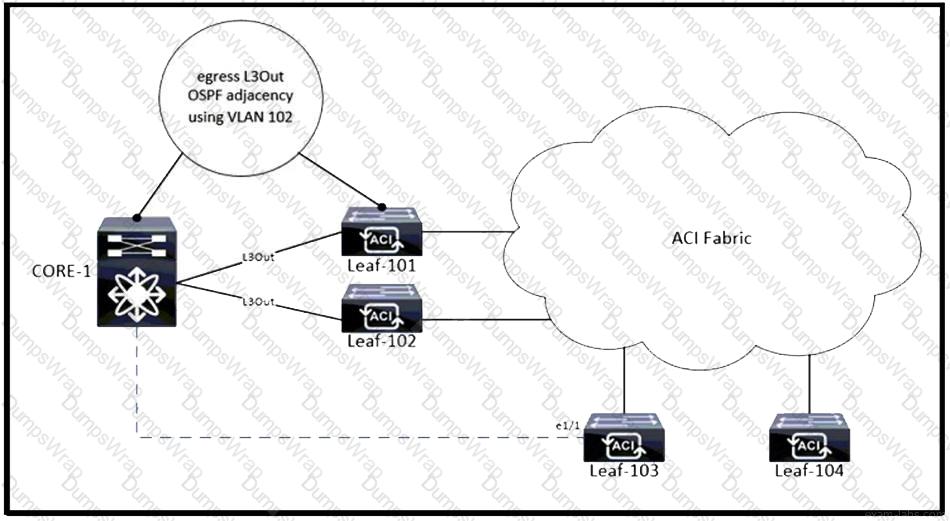
Refer to the exhibit. The Cisco ACI fabric has an egress L3Out from Leaf-101 and Leaf-102 to CORE-1. VLAN 102 is used to form the OSPF adjacency. The workloads must be migrated into EPG-101, and the static port binding is configured to Leaf-103 e1/1 with encap VLAN 101. An engineer completes the port binding and receives an MCP fault. Which action clears the fault?
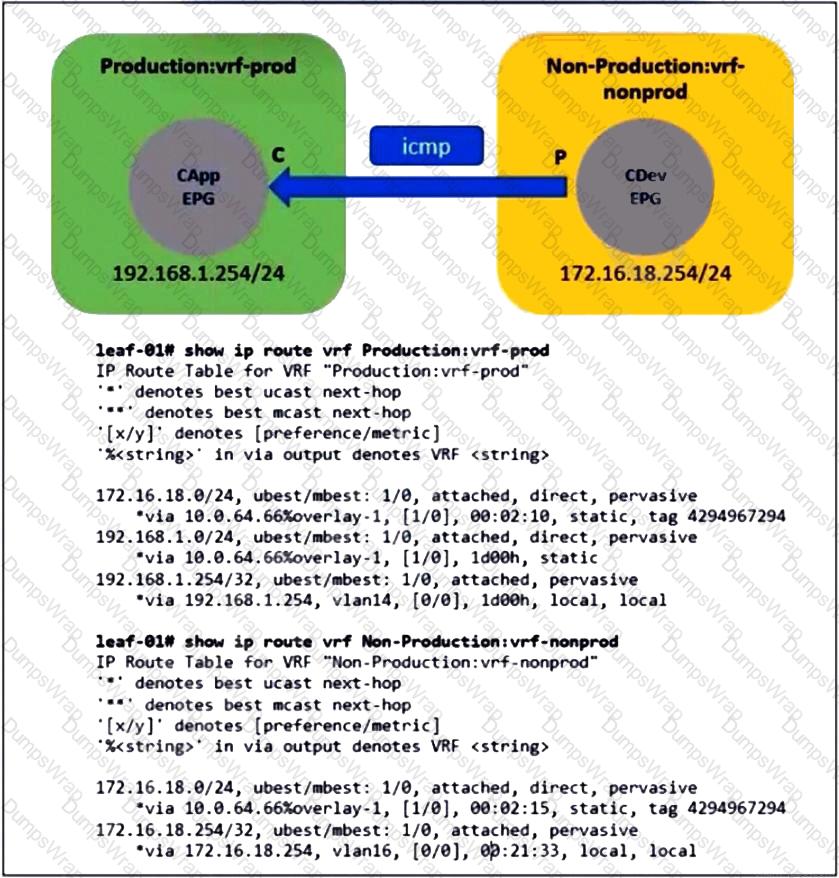
Refer to the exhibit. An administrator configures inter-VRF route leaking between Production:vrf-prod and Non-Production:vrf-nonprod. However, the route in the Non-Production:vrf-nonprod VRF to the production tenant is missing. Which action resolves the VRF route leaking issue?
Which new construct must a user create when configuring in-band management?
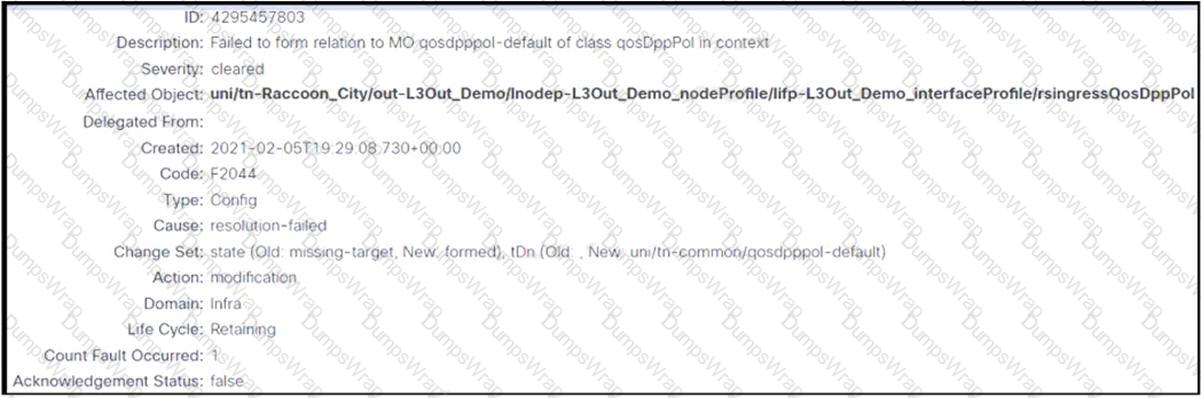
Refer to the exhibit. An engineer configures an L3Out but receives the error presented. Which action clears the fault?
Refer to the exhibit.
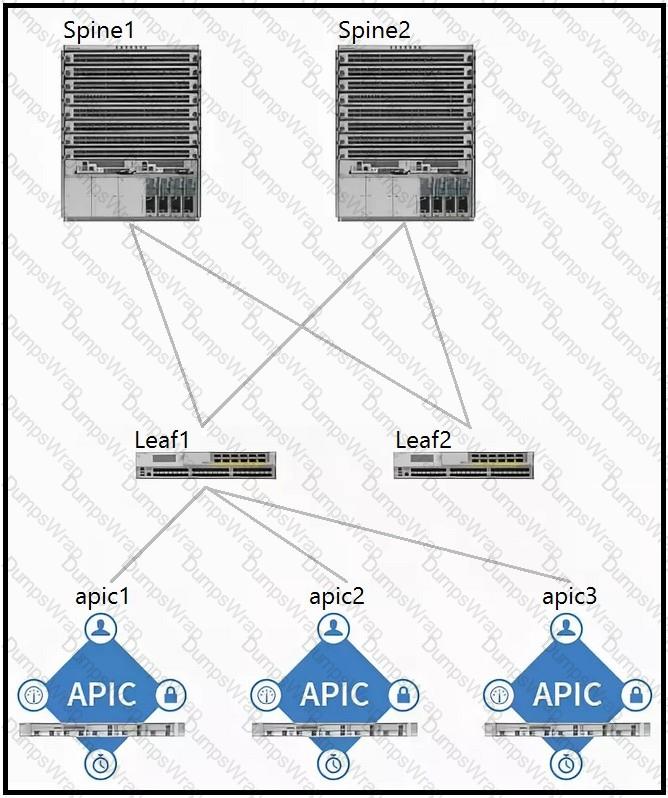
Which two components should be configured as route reflectors in the ACI fabric? (Choose two.)
Which components must be configured for the BGP Route Reflector policy to take effect?
Refer to the exhibit.
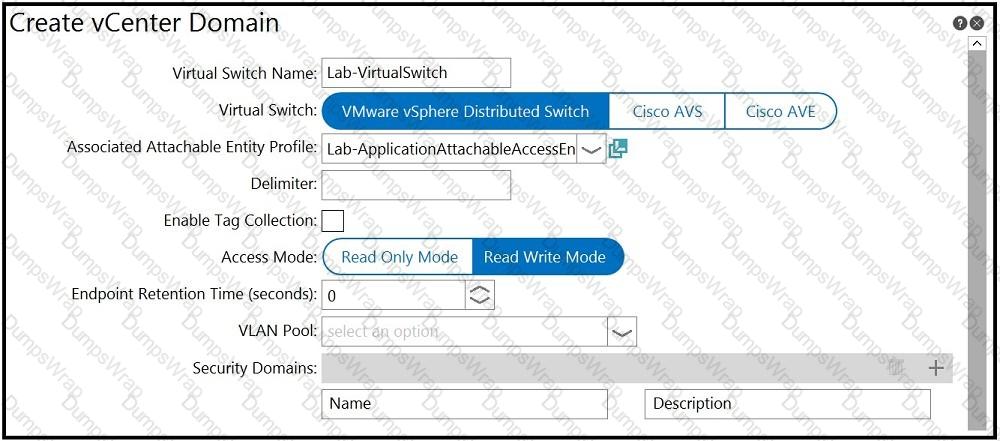
An engineer is integrating a VMware vCenter with Cisco ACI VMM domain configuration. ACI creates port-group names with the format of “Tenant | Application | EPG”. Which configuration option is used to generate port groups with names formatted as “Tenant=Application=EPG”?
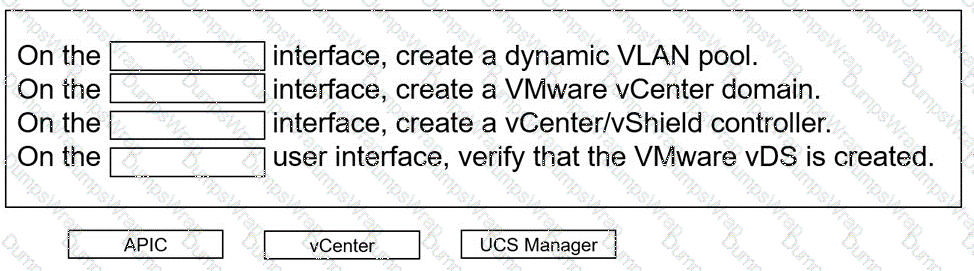
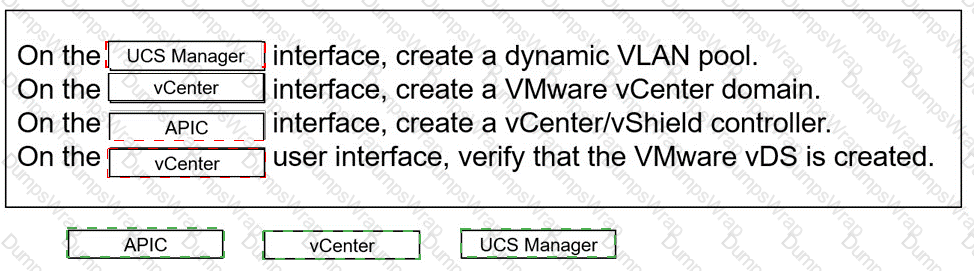
An engineer must configure VMM domain integration on a Cisco UCS B-Series server that is connected to a Cisco ACI fabric. Drag and drop the products used to create VMM domain from the bottom into the sequence in which they should be implemented at the top. Products are used more than once.
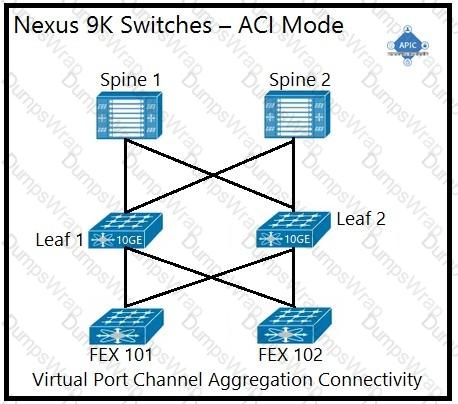
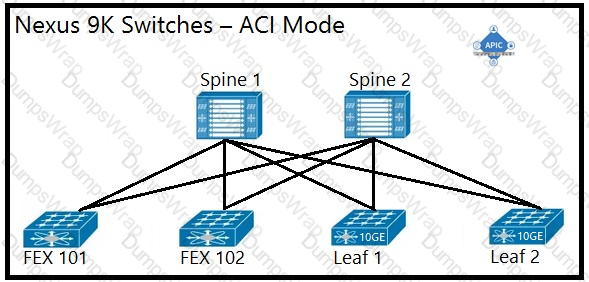
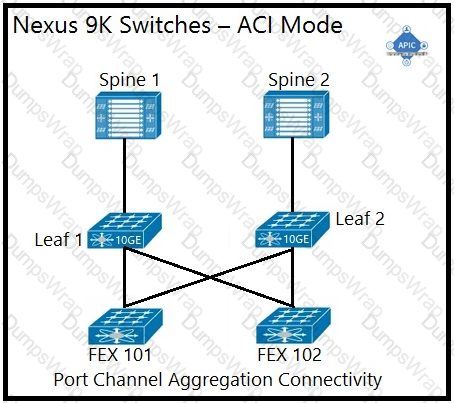
An engineer is implementing a Cisco ACI data center network that includes Cisco Nexus 2000 Series 10G fabric extenders. Which physical topology is supported?
A)
B)
C)
D)
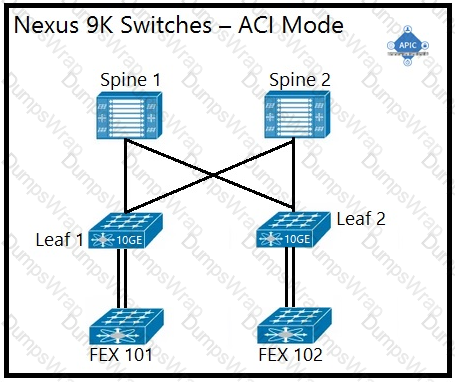
Which method does the Cisco ACI fabric use to load-balance multidestination traffic?
A situation causes a fault to be raised on the APIC. The ACI administrator does not want that fault to be raised because it is not directly relevant to the environment. Which action should the administrator take to prevent the fault from appearing?
An engineer must connect Cisco ACI fabric using Layer 2 with external third-party switches. The third-party
switches are configured using 802.1s protocol. Which two constructs are required to complete the task?
(Choose two.)
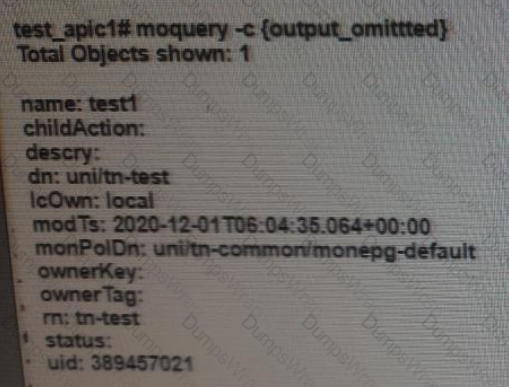
Which class of ACI object is presented in this output?
A customer migrates a legacy environment to Cisco ACI. A Layer 2 trunk is configured to interconnect the two
environments. The customer also builds ACI fabric in an application-centric mode. Which feature should be
enabled in the bridge domain to reduce instability during the migration?
Which feature dynamically assigns or modifies the EPG association of virtual machines based on their attributes?
New ESXi hosts are procured in a data center compute expansion project. An engineer must update the
configuration on the Cisco APIC controllers to support the addition of the new servers to the existing VMM
domain. Which action should be taken to support this change?
A customer creates Layer 3 connectivity to the outside network. However, only border leaf switches start receiving destination updates to other networks from the newly created L3Out. The updates must also be propagated to other Cisco ACI leaf switches. The L3Out is linked with the EPGs via a contract. Which action must be taken in the pod policy group to accomplish this goal?
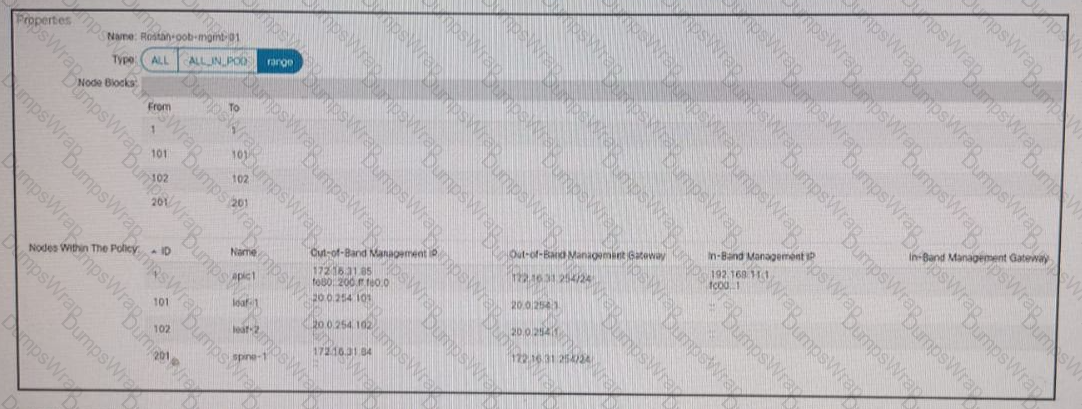
Refer to the exhibit A Cisco ACI fabric is using out-of-band management connectivity The APIC must access a routable host with an IP address of 192 168 11 2 Which action accomplishes this goal?
Refer to the exhibit.
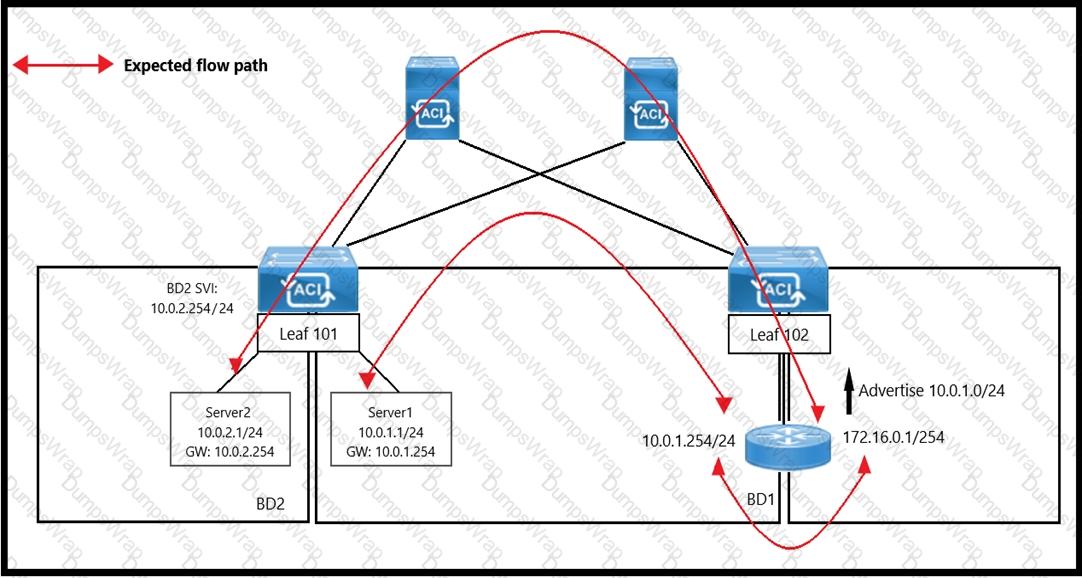
An engineer wants to initiate an ICMP ping from Server1 to Server2. The requirement is for the BD1 to enforce ICMP replies that follow the expected path. The packets must be prevented fromtaking the direct path from Leaf1 to Server1. Which action must be taken on BD1 to meet these requirements?
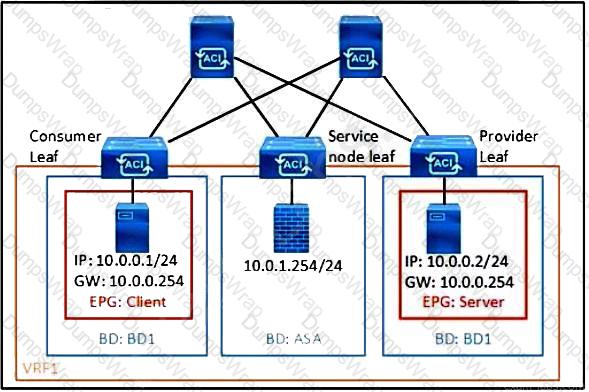
Refer to the exhibit. What must be configured in the service graph to redirect HTTP traffic between the EPG client and EPG server to go through the Cisco ASA firewall?
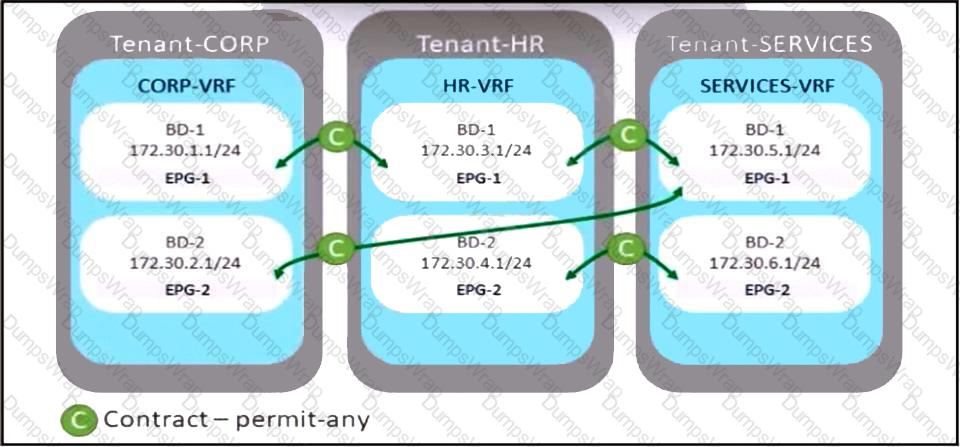
Refer to the exhibit. A company merges three of its departments: CORP, HR, and SERVICES, Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking. Which configuration meets these criteria?
Refer to the exhibit.
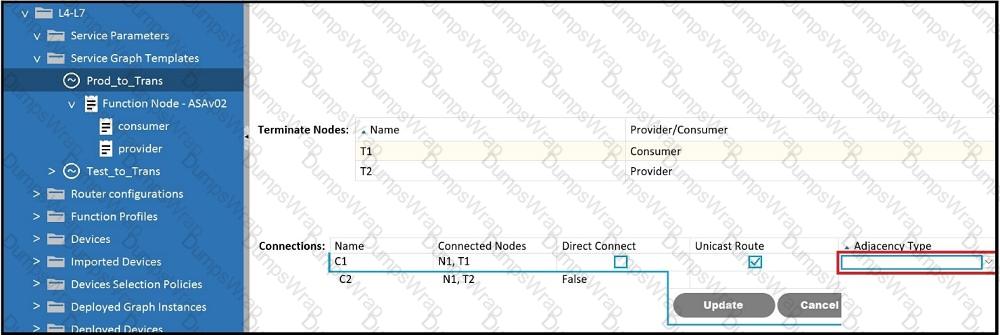
Which Adjacency Type value should be set when the client endpoint and the service node
interface are in a different subnet?
A Solutions Architect is asked to design two data centers based on Cisco ACI technology that can extend L2/ L3, VXLAN, and network policy across locations. ACI Multi-Pod has been selected. Which two requirements must be considered in this design? (Choose two.)
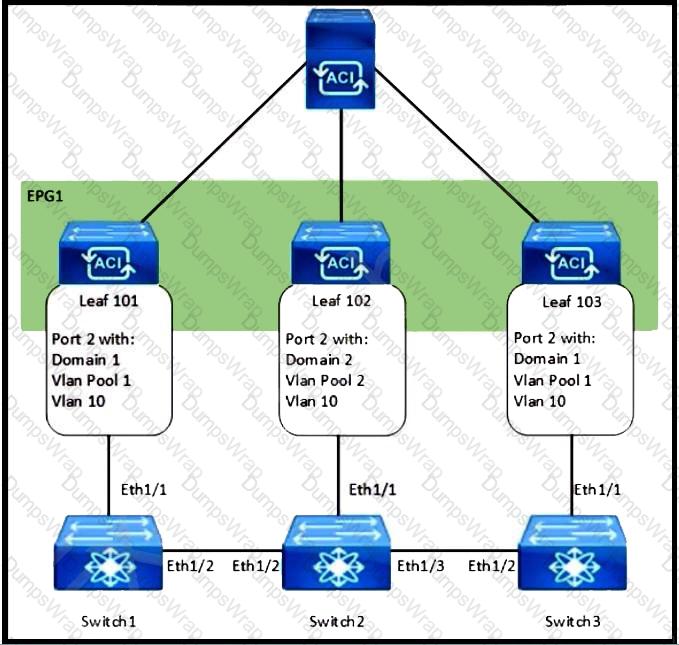
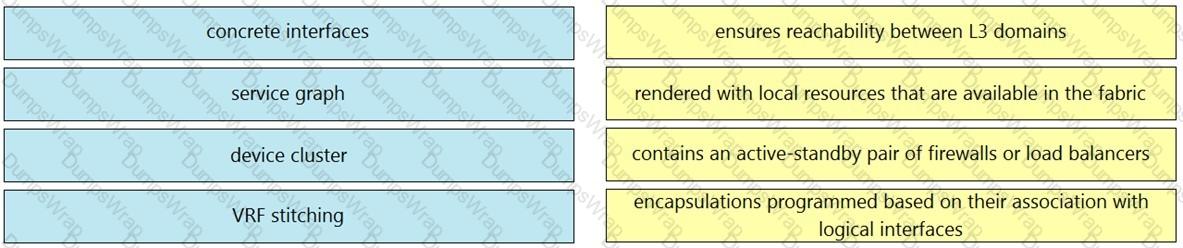
Refer to the exhibit. How are the STP BPDUs forwarded over Cisco ACI fabric?
Refer to the exhibit. VM1 and VM2 are in Cisco ACI POD1 and communication takes place. Which event is triggered when VM2 is live migrated from POD1 to POD2?
What is the advantage of implementing an active-active firewall cluster that is stretched across separate pods when anycast services are configured?
Refer to the exhibit.
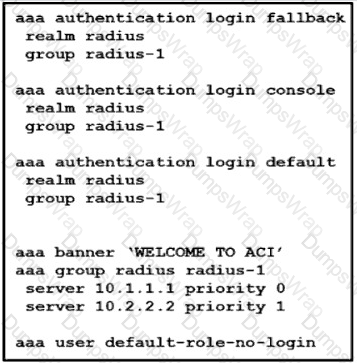
Which action should be taken to ensure authentication if the RADIUS servers are unavailable?
What must be configured to allow SNMP traffic on the APIC controller?
Which type of policy configures the suppression of faults that are generated from a port being down?
A network engineer must configure a new SNMP configuration and syslog servers. The requirement is for all faults and events related to endpoint groups, bridge domains, and VRFs to be sent to it. Which action must be taken to meet the requirements?
A network engineer configures the Cisco ACI fabric to connect to vCenter with these requirements:
Port groups must be automatically created on the distributed virtual switch.
Port groups must use the VLAN allocation in the range between 20-30.
The deployment must optimize the CAM space on the leaf switches.
Which set of actions meets these criteria?
When the subnet is configured on a bridge domain, on which physical devices is the gateway IP address configured?
An ACI administrator notices a change in the behavior of the fabric. Which action must be taken to determine if a human intervention introduced the change?
An organization has encountered many STP-related issues in the past due to failed hardware components. They are in the process of long-term migration to a newly deployed ACI fabric. Senior engineers are worried that spanning-tree loops in the existing network may be extended to the ACI fabric. Which feature must be enabled on the ACI leaf ports to protect the fabric from spanning-tree loops?
When a pre-provision immediacy is used, when is the policy downloaded to the Cisco ACI leaf switch?
Which two protocols support accessing backup files on a remote location from the APIC? (Choose two.)
What does a bridge domain represent?
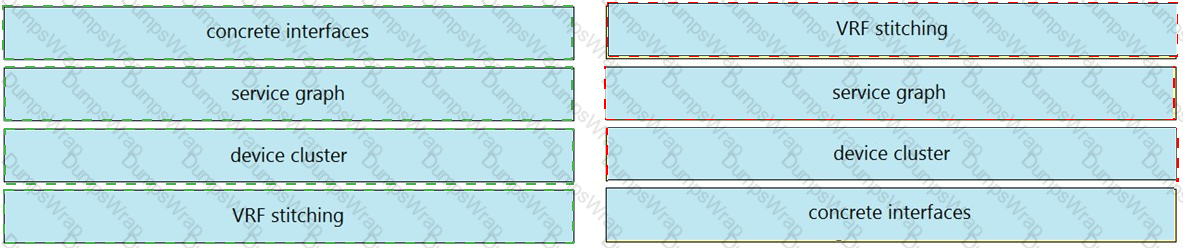
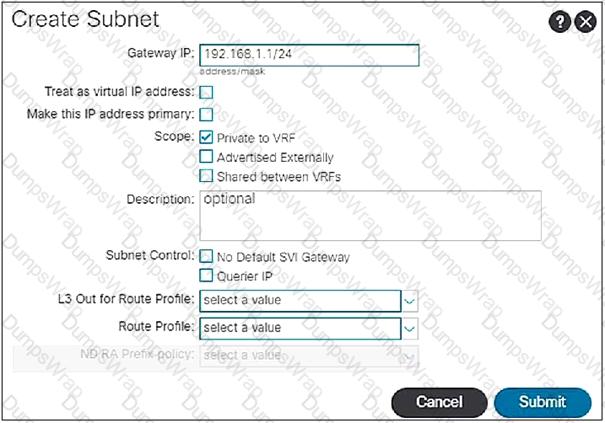
Drag and drop the Cisco ACI Layer 4 to Layer 7 service insertion terms on the left to the correct descriptions on the right.
A packet is routed between two endpoints on different Cisco ACI leaf switches. Which VXLAN VNID is applied to the packet?
An engineer must create a backup of the Cisco ACI fabric for disaster recovery purposes. The backup must be transferred over a secure and encrypted transport. The backup file must contain all user and password related information. The engineer also wants to process and confirm the backup file validity by using a Python script. This requires the data structure to have a format similar to a Python dictionary. Which configuration set must be used to meet these requirements?
A bridge domain for a new endpoint group in the Cisco ACI fabric must meet these requirements:
The bridge domain must function as the default gateway for the subnet so that routing remains within the Cisco ACI fabric.
ARP requests must be managed via Layer 3 unicast packets or be dropped to reduce excessive broadcast traffic.
The impact of misconfigured virtual machines must be kept to a minimum by preventing IP addresses outside of the configured subnet from being routed.
Which set of actions must be taken?
An engineer wants to filter the System Faults page and view only the active faults that are present in the Cisco
ACI fabric. Which two lifecycle stages must be selected for filtering? (Choose two.)
All workloads in VLAN 1001 have been migrated into EPG-1001. The requirement is to move the gateway address for VLAN 1001 from the core outside the Cisco ACI fabric into the Cisco ACI fabric. The endpoints in EPG-1001 must route traffic to endpoints in other EPGs and minimize flooded traffic in the fabric. Which configuration set is needed on the bridge domain to meet these requirements?
Which routing protocol is supported between Cisco ACI spines and IPNs in a Cisco ACI Multi-Pod environment?
Refer to the exhibit, An engineer is deploying a Cisco ACI environment but experiences a STP loop between switch1 and switch2. Which configuration step is needed to break the STP loop?
Which type of port is used for in-band management within ACI fabric?
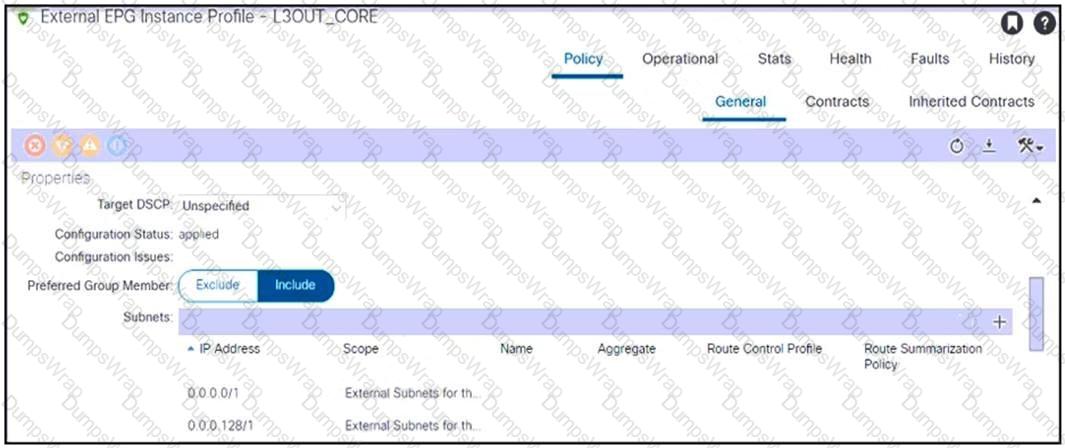
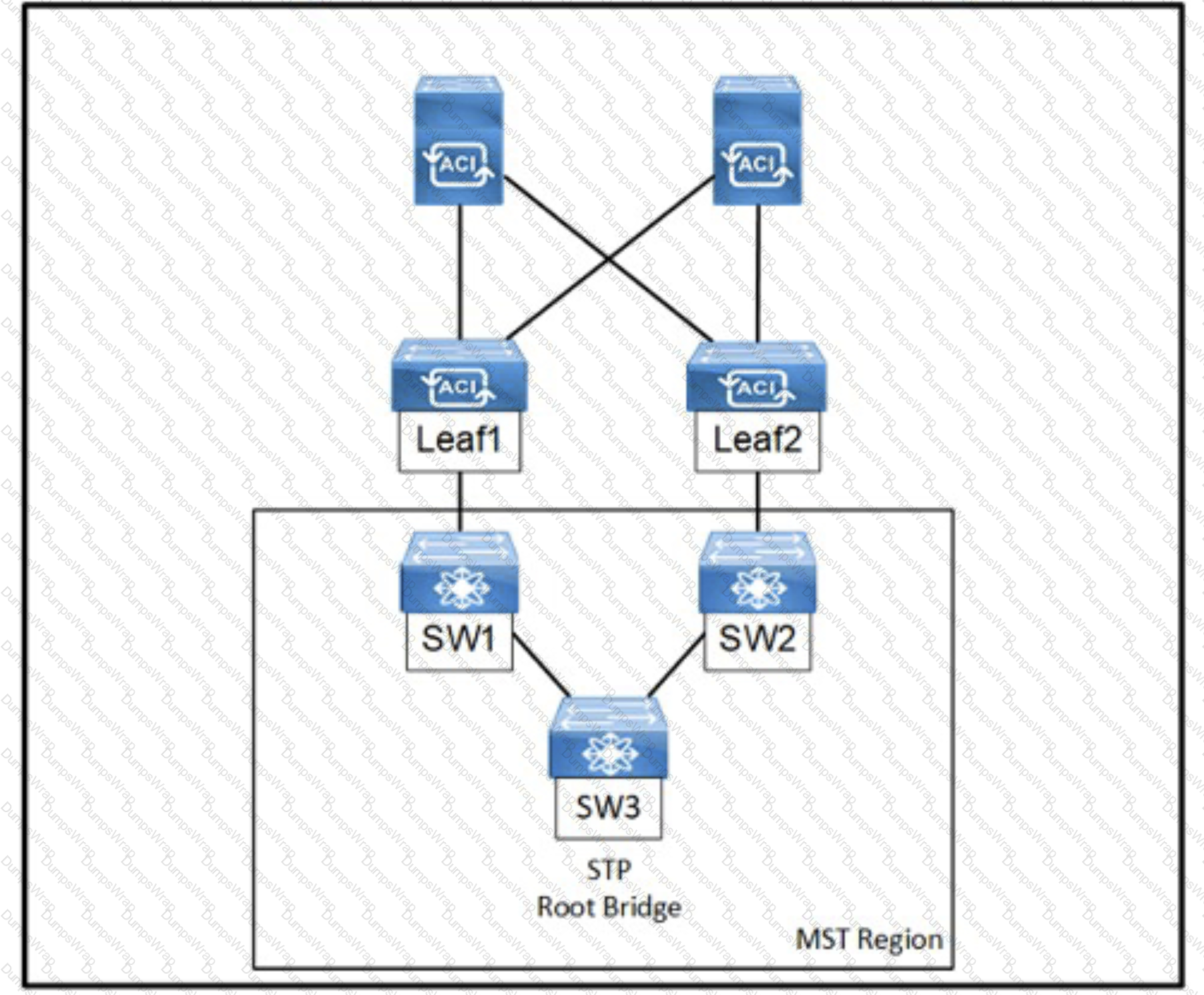
Refer to the exhibit. An engineer configured subnets on the external EPG called L3OUT_CORE. The external endpoints in the 10.1.0.0/24 subnet can reach internal endpoints, but the external endpoints in the 172.16.1.0/24 subnet are unreachable. Which set of actions enables the connectivity?
As part of a migration, legacy non-ACI switches must be connected to the Cisco ACI fabric. All non-ACI switches run per-VLAN RSTP. After the non-ACI switches are connected to Cisco ACI, the STP convergence caused a microloop and significant CPU spike on all switches. Which configuration on the interfaces of the external switches that face the Cisco ACI fabric resolves the problem?
A bridge domain for an EPC called “Web Servers” must be created in the Cisco APIC. The configuration must meet these requirements:
Only traffic to known Mac addresses must be allowed to reduce noice.
The multicast traffic must be limited to the ports that are participating in multicast routing.
The endpoints within the bridge domain must be kept in the endpoint table for 20 minultes without any updates.
Which set of steps configures the bridge domain that satisfies the requirements?
An engineer configures a one-armed policy-based redirect service Insertion for an unmanaged firewall. The engineer configures these Cisco ACI objects:
a contract named All_Traffic_Allowed
a Layer 4 to Layer 7 device named FW-Device
a policy-based redirect policy named FW-1Arm-Policy-Based RedirectPolicy
Which configuration set redirects the traffic to the firewall?
Which two actions extend a Layer 2 domain beyond the ACI fabric? (Choose two.)
A network engineer mustconfigurea Cisco ACI system to detect network loops for untagged and tagged traffic The loop must be detected and slopped by disabling an interface within 4 seconds Which configuration must be used?

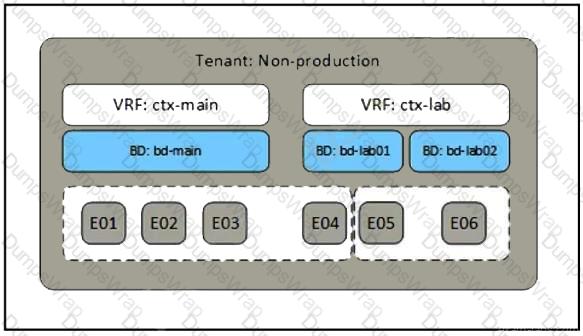
Refer to the exhibit. A network engineer must complete the Cisco ACI implementation based on the logical system design created by the systems architect. Which Cisco ACI object is required where the dotted line indicates to complete the task?
When configuring Cisco ACI VMM domain integration with VMware vCenter, which object is created in vCenter?
An engineer is creating a configuration import policy that must terminate if the imported configuration is incompatible with the existing system. Which import mode achieves this result?
Which two IP address types are available for transport over the ISN when they are configured from Cisco ACI Multi-Site Orchestrator? (Choose two.)
What are two PBR characteristics of the Cisco ACI Active-Active Across Pods deployment mode in Cisco ACI Multi-Pod design? (Choose two.)

 C:\Users\User\AppData\Local\Temp\SNAGHTML5a772e.PNG
C:\Users\User\AppData\Local\Temp\SNAGHTML5a772e.PNG