Securing Networks with Cisco Firepower (300-710 SNCF) Questions and Answers
An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside interfaces to the outside interfaces. They are unable to gather information about neighbouring Cisco devices or use multicast in their environment. What must be done to resolve this issue?
Refer to the exhibit.
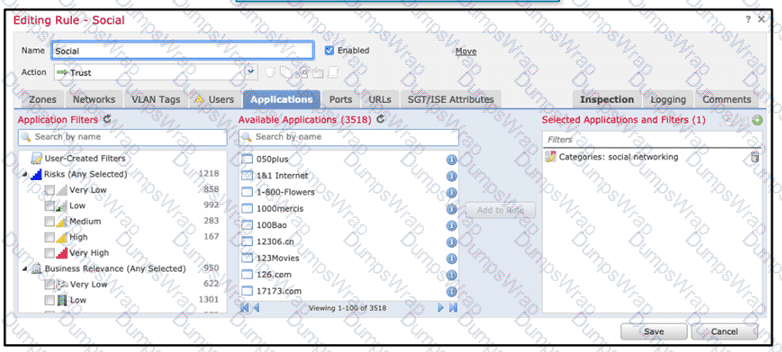
An organization has an access control rule with the intention of sending all social media traffic for inspection After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed What must be done to address this issue?
An engineer is troubleshooting HTTP traffic to a web server using the packet capture tool on Cisco FMC. When reviewing the captures, the engineer notices that there are a lot of packets that are not sourced from or destined to the web server being captured. How can the engineer reduce the strain of capturing packets for irrelevant traffic on the Cisco FTD device?
A network engineer must provide redundancy between two Cisco FTD devices. The redundancy configuration must include automatic configuration, translation, and connection updates. After the initial configuration of the two appliances, which two steps must be taken to proceed with the redundancy configuration? (Choose two.)
What is a result of enabling Cisco FTD clustering?
Which process should be checked when troubleshooting registration issues between Cisco FMC and managed devices to verify that secure communication is occurring?
Refer to the exhibit.
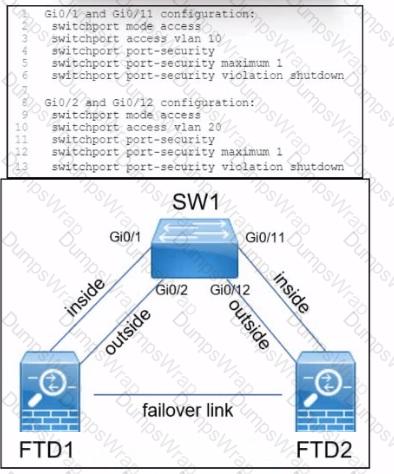
A company is deploying a pair of Cisco Secure Firewall Threat defence devices named FTD1 and FTD2. FTD1 and FTD2 have been configured as an active/standby pair with a failover link but without a stateful link. What must be implemented next to ensure that users on the internal network still communicate with outside devices if FTD1 fails?
A company wants a solution to aggregate the capacity of two Cisco FTD devices to make the best use of resources such as bandwidth and connections per second. Which order of steps must be taken across the Cisco FTDs with Cisco FMC to meet this requirement?
Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain environment?
Which Cisco Rapid Threat Containment mitigation action is enabled by integrating pxGrid Adaptive Network Control with Cisco ISE and Cisco Secure Firewall Management Center?
While configuring FTD, a network engineer wants to ensure that traffic passing through the appliance does not require routing or Vlan rewriting. Which interface mode should the engineer implement to accomplish this task?
After deploying a network-monitoring tool to manage and monitor networking devices in your organization, you realize that you need to manually upload an MIB for the Cisco FMC. In which folder should you upload the MIB file?
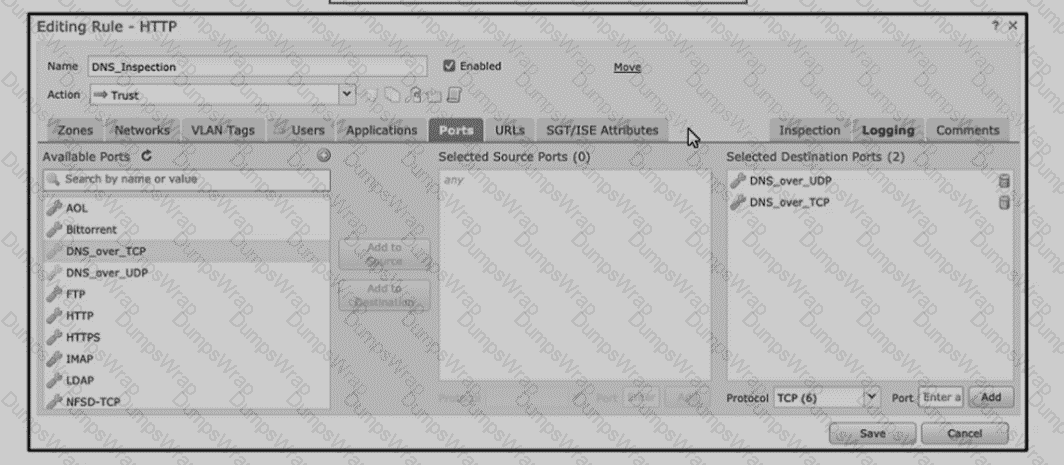
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?
A security engineer is configuring an Access Control Policy for multiple branch locations. These locations share a common rule set and utilize a network object called INSIDE_NET which contains the locally significant internal network subnets at each location. Which technique will retain the policy consistency at each location but allow only the locally significant network subnet within the applicable rules?
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
What is the role of realms in the Cisco ISE and Cisco FMC integration?
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
Which two solutions are used to access and view aggregated log data from the firewalls using Cisco Security Analytics and Logging? (Choose two.)
A security engineer found a suspicious file from an employee email address and is trying to upload it for analysis, however the upload is failing. The last registration status is still active. What is the cause for this issue?
An engineer integrates Cisco FMC and Cisco ISE using pxGrid. Which role is assigned for Cisco FMC?
In a multi-tennent deployment where multiple domains are in use. which update should be applied outside of the Global Domain?
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?
Which Cisco FMC report gives the analyst information about the ports and protocols that are related to the configured sensitive network for analysis?
What is the maximum SHA level of filtering that Threat Intelligence Director supports?
Which action must be taken on the Cisco FMC when a packet bypass is configured in case the Snort engine is down or a packet takes too long to process?
An administrator is optimizing the Cisco FTD rules to improve network performance, and wants to bypass inspection for certain traffic types to reduce the load on the Cisco FTD. Which policy must be configured to accomplish this goal?
An engineer is setting up a new Cisco Secure Firewall Threat Defense appliance to replace the current firewall. The company requests that inline sets be used and that when one interface in
an inline set goes down, the second interface in the inline set goes down. What must the engineer configure to meet the deployment requirements?
Which two conditions are necessary for high availability to function between two Cisco FTD devices? (Choose two.)
An engineer must configure a Cisco FMC dashboard in a child domain. Which action must be taken so that the dashboard is visible to the parent domain?
Which component simplifies incident investigation with Cisco Threat Response?
An engineer has been tasked with using Cisco FMC to determine if files being sent through the network are malware. Which two configuration tasks must be performed to achieve this file lookup? (Choose two).
An administrator is configuring a transparent Cisco FTD device to receive ERSPAN traffic from multiple switches on a passive port but the FTD is not processing the traffic What is the problem?
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation. How will this issue be addresses globally in the quickest way possible and with the least amount of impact?
An engineer is configuring URL filtering tor a Cisco Secure Firewall Threat Defense device in Cisco Secure Firewall Management Centre. Use's must receive a warning when they access
..wwww badaduitsito com with the option of continuing to the website if they choose to No other websites should he blocked. Which two actions must the engineer take to moot these requirements?
An engineer is restoring a Cisco FTD configuration from a remote backup using the command restore remote-manager-backup location 1.1.1.1 admin /volume/home/admin BACKUP_Cisc394602314.zip on a Cisco FMG. After connecting to the repository, an error occurred that prevents the FTD device from accepting the backup file. What is the problem?
An organization created a custom application that is being flagged by Cisco Secure Endpoint. The application must be exempt from being flagged. What is the process to meet the requirement?
What is the result of specifying of QoS rule that has a rate limit that is greater than the maximum throughput of an interface?
An organization wants to secure traffic from their branch office to the headquarter building using Cisco Firepower devices, They want to ensure that their Cisco Firepower devices are not wasting resources on inspecting the VPN traffic. What must be done to meet these requirements?
A VPN user is unable to conned lo web resources behind the Cisco FTD device terminating the connection. While troubleshooting, the network administrator determines that the DNS responses are not getting through the Cisco FTD What must be done to address this issue while still utilizing Snort IPS rules?
An engineer must change the mode of a Cisco Secure Firewall Threat Defense (FTD) firewall in the Cisco Secure Firewall Management Center (FMC) inventory. The engineer must take these actions:
• Register Secure FTD with Secure FMC.
• Change the firewall mode.
• Deregister the Secure FTD device from Secure FMC.
How must the engineer take FTD take the actions?
An engineer wants to perform a packet capture on the Cisco FTD to confirm that the host using IP address 192 168.100.100 has the MAC address of 0042 7734.103 to help troubleshoot aconnectivity issue What is the correct tcpdump command syntax to ensure that the MAC address appears in the packet capture output?
Which two actions can be used in an access control policy rule? (Choose two.)
A network administrator cannot select the link to be used for failover when configuring an active/passive HA Cisco FTD pair.
Which configuration must be changed before setting up the high availability pair?
Refer to the exhibit.

What is the effect of the existing Cisco FMC configuration?
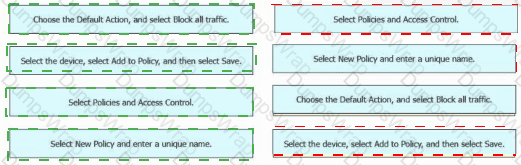
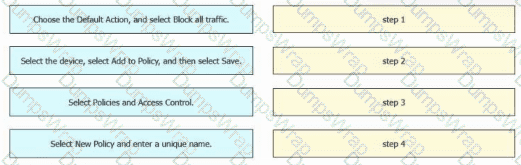
An engineer must create a basic access control policy in the Cisco Secure Firewall Management Center to block all traffic by default. Drag and drop the configuration actions from the left into sequence on the right.
A network administrator is reviewing a monthly advanced malware risk report and notices a host that Is listed as CnC Connected. Where must the administrator look within Cisco FMC to further determine if this host is infected with malware?
An engineer is implementing a new Cisco Secure Firewall. The firewall must filler traffic between the three subnets:
• LAN 192.168.101.0724
• DMZ 192.168 200.0/24
• WAN 10.0.0.0/30
Which firewall mode must the engineer implement?
An engineer is configuring Cisco Security Devices by using Cisco Secure Firewall Management Center. Which configuration command must be run to compare the CA certificate bundle on the local system to the latest CA bundle from the Cisco server?
When deploying a Cisco ASA Firepower module, an organization wants to evaluate the contents of the traffic without affecting the network. It is currently configured to have more than one instance of the same device on the physical appliance Which deployment mode meets the needs of the organization?
A network engineer must monitor threat events from the console of Cisco Secure Firewall Management Center. The engineer integrates the Cisco Secure Firewall Malware Defense in Secure Firewall Management Center. Which action must the engineer take next?
A connectivity issue is occurring between a client and a server which are communicating through a Cisco Firepower device While troubleshooting, a network administrator sees that traffic is reaching the server, but the client is not getting a response Which step must be taken to resolve this issue without initiating traffic from the client?
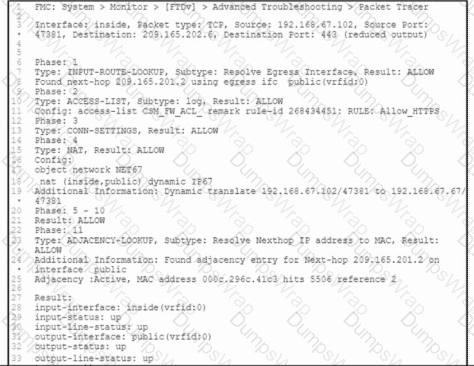
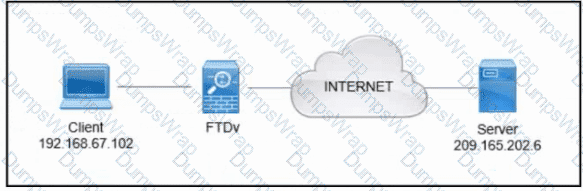
Refer to the exhibit. A client that has IP address 192.168.67.102 reports issues when connecting to a remote server. Based on the topology and output of packet tracer tool, which action resolves the connectivity issue?
An engineer is troubleshooting a file that is being blocked by a Cisco FTD device on the network.
The user is reporting that the file is not malicious.
Which action does the engineer take to identify the file and validate whether or not it is malicious?
Which Cisco Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two.)
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
When an engineer captures traffic on a Cisco FTD to troubleshoot a connectivity problem, they receive a large amount of output data in the GUI tool. The engineer found that viewing the Captures this way is time-consuming and difficult lo son and filter. Which file type must the engineer export the data in so that it can be reviewed using a tool built for this type of analysis?
Network users experience issues when accessing a server on a different network segment. An engineer investigates the issue by performing packet capture on Cisco Secure Firewall Threat Defense. The engineer expects more data and suspects that not all the traffic was collected during a 15-minute can’t captured session. Which action must the engineer take to resolve the issue?
An engineer is deploying a Cisco Secure Firewall Management Center appliance. The company must send data to Cisco Secure Network Analytics appliances. Which two actions must the engineer take? (Choose two.)
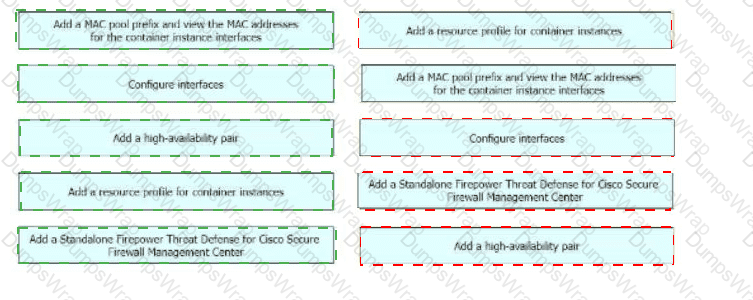
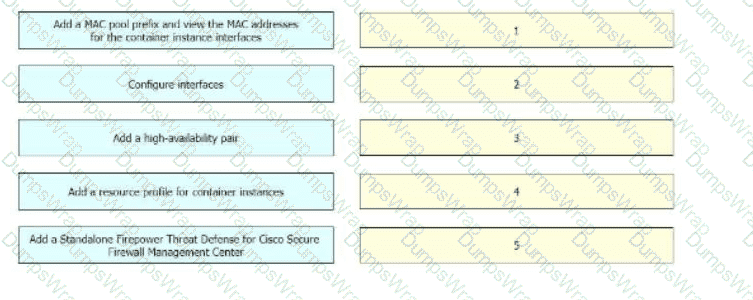
A network engineer is deploying a Cisco Firepower 4100 appliance and must configure a multi-instance environment for high availability. Drag and drop me actions from the left into sequence on the right far this configuration.
The CEO ask a network administrator to present to management a dashboard that shows custom analysis tables for the top DNS queries URL category statistics, and the URL reputation statistics.
Which action must the administrator take to quickly produce this information for management?
A network administrator is migrating from a Cisco ASA to a Cisco FTD.
EIGRP is configured on the Cisco ASA but it is not available in the Cisco FMC.
Which action must the administrator take to enable this feature on the Cisco FTD?
Which Firepower feature allows users to configure bridges in routed mode and enables devices to perform Layer 2 switching between interfaces?
An administrator configures a Cisco Secure Firewall Threat Defense device in transparent mode. To configure the BVI (Bridge Virtual Interface), the administrator must:
Add a bridge-group interface
Configure a bridge-group ID
Configure the bridge-group interface description
Add bridge-group member interfaces
How must the engineer perform these actions?
An administrator Is setting up a Cisco PMC and must provide expert mode access for a security engineer. The engineer Is permitted to use only a secured out-of-band network workstation with a static IP address to access the Cisco FMC. What must be configured to enable this access?
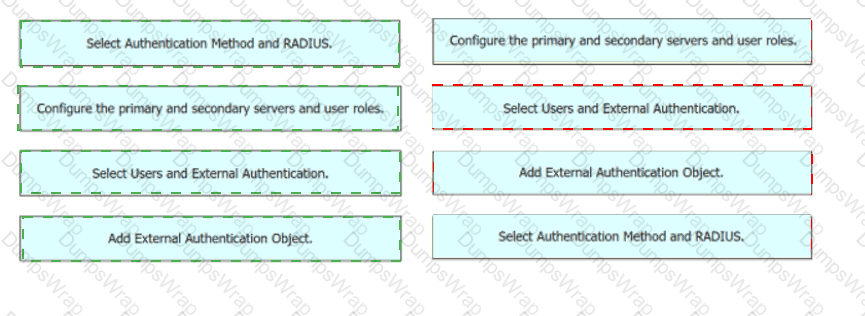
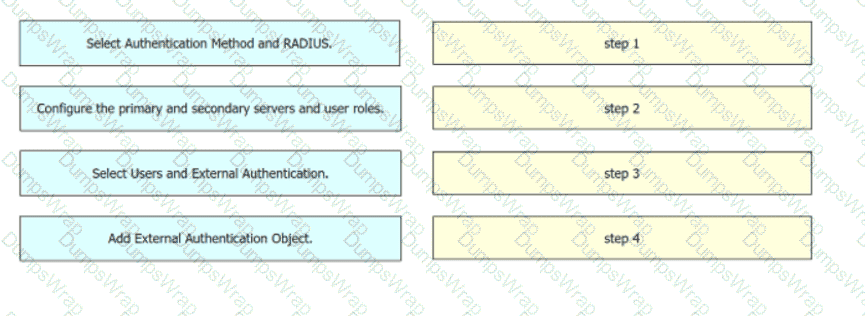
Drag and drop the configuration steps from the left into the sequence on the right to enable external authentication on Cisco FMC to a RADIUS server.
An organization has implemented Cisco Firepower without IPS capabilities and now wants to enable inspection for their traffic. They need to be able to detect protocol anomalies and utilize the Snort rule sets to detect malicious behaviour. How is this accomplished?
With Cisco FTD integrated routing and bridging, which interface does the bridge group use to communicate with a routed interface?
A network administrator is implementing an active/passive high availability Cisco FTD pair.
When adding the high availability pair, the administrator cannot select the secondary peer.
What is the cause?
Network users are experiencing Intermittent issues with internet access. An engineer ident med mat the issue Is being caused by NAT exhaustion. How must the engineer change the dynamic NAT configuration to provide internet access for more users without running out of resources?
An engineer must configure high availability for the Cisco Firepower devices. The current network topology does not allow for two devices to pass traffic concurrently. How must the devices be implemented in this environment?
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
An engineer is configuring a second Cisco FMC as a standby device but is unable to register with the active unit. What is causing this issue?
Which feature issupportedby IRB on Cisco FTD devices?
An engineer must replace a Cisco Secure Firewall high-availability device due to a failure. When the replacement device arrives, the engineer must separate the high-availability pair from Cisco Secure Firewall Management Center Which action must the engineer take first to restore high availability?
A network engineer wants to add a third-party threat feed into the Cisco FMC for enhanced threat detectionWhich action should be taken to accomplish this goal?
A network administrator reviews the file report for the last month and notices that all file types, except exe. show a disposition of unknown. What is the cause of this issue?
A mid-sized company is experiencing higher network bandwidth utilization due to a recent acquisition The network operations team is asked to scale up their one Cisco FTD appliance deployment to higher capacities due to the increased network bandwidth. Which design option should be used to accomplish this goal?
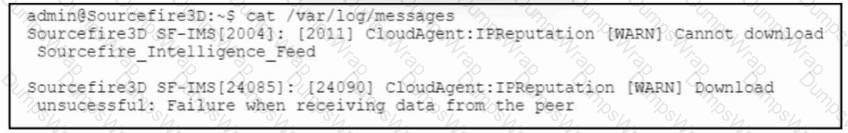
Refer to the exhibit. A Cisco Secure Firewall Management Center, 7.0 device fails to receive intelligence feed updates. The Cisco Secure Firewall Management Center is configured to use a proxy server that performs SSL inspection. Which action allows the Cisco Secure Firewall Management Center device to download the intelligence feed updates?
Which protocol establishes network redundancy in a switched Firepower device deployment?
What is the RTC workflow when the infected endpoint is identified?
Which two features of Cisco AMP for Endpoints allow for an uploaded file to be blocked? (Choose two.)
A security analyst must create a new report within Cisco FMC to show an overview of the daily attacks, vulnerabilities, and connections. The analyst wants to reuse specific dashboards from other reports to create this consolidated one. Which action accomplishes this task?
When a Cisco FTD device is configured in transparent firewall mode, on which two interface types can an IP address be configured? (Choose two.)
Which protocol is needed to exchange threat details in rapid threat containment on Cisco FMC?
When do you need the file-size command option during troubleshooting with packet capture?
An organization is setting up two new Cisco FTD devices to replace their current firewalls and cannot have any network downtime During the setup process, the synchronization between the two devices is failing What action is needed to resolve this issue?
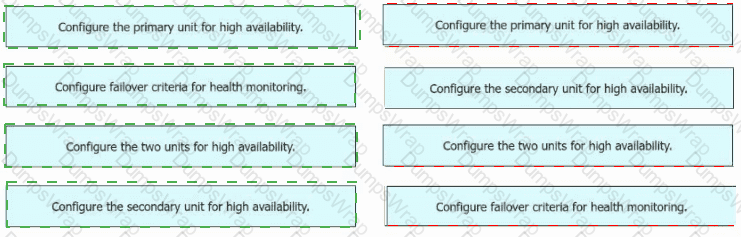
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances. Drag and drop the configuration steps from the left into the sequence on the right.
An engineer must integrate a third-party security intelligence feed with Cisco Secure Firewall Management Center. Secure Firewall Management Center is running Version 6.2.3 and has 8
GB of memory. Which two actions must be taken to implement Threat Intelligence Director? (Choose two.)
While integrating Cisco Umbrella with Cisco Threat Response, a network security engineer wants to automatically push blocking of domains from the Cisco Threat Response interface to Cisco Umbrella. Which API meets this requirement?
An engineer is troubleshooting connectivity to the DNS servers from hosts behind a new Cisco FTD device. The hosts cannot send DNS queries to servers in the DMZ. Which action should the engineer take to troubleshoot this issue using the real DNS packets?
Which default action setting in a Cisco FTD Access Control Policy allows all traffic from an undefined application to pass without Snort Inspection?
Refer to the exhibit.
A systems administrator conducts a connectivity test to their SCCM server from a host machine and gets no response from the server. Which action ensures that the ping packets reach the destination and that the host receives replies?
Upon detecting a flagrant threat on an endpoint, which two technologies instruct Cisco Identity Services Engine to contain the infected endpoint either manually or automatically? (Choose two.)
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic segmentation Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?
Which firewall design allows a firewall to forward traffic at layer 2 and layer 3 for the same subnet?
An engineer must export a packet capture from Cisco Secure Firewall Management Center to assist in troubleshooting an issue an a Secure Firewall Threat Defense device. When the engineer navigates to URL for Secure Firewall Management Center at:
..
An engineer receives a 403: Forbidden error instead of being provided with the PCAP file. Which action resolves the issue?
A network administrator needs to create a policy on Cisco Firepower to fast-path traffic to avoid Layer 7 inspection. The rate at which traffic is inspected must be optimized. What must be done to achieve this goal?
Refer to the exhibit.
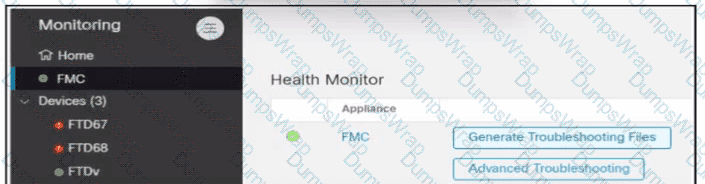
An engineer generates troubleshooting files in Cisco Secure Firewall Management Center (FMC). A successfully completed task Is removed before the files are downloaded. Which two actions must be taken to determine the filename and obtain the generated troubleshooting files without regenerating them? (Choose two.)
An engineer is configuring two new Cisco FTD devices to replace the existing high availability firewall pair in a highly secure environment. The information exchanged between the FTD devices over the failover link must be encrypted. Which protocol supports this on the Cisco FTD?
An engineer is reviewing an existing custom server fingerprint on a Cisco Secure Firewall because the current information is inaccurate. Which action must the engineer take to improve the accuracy of the network discovery rules?
An engineer must implement Cisco Secure Firewall transparent mode due to a new server recently being added that must communicate with an existing server that is currently separated by the firewall. Which implementation action must be taken next by the engineer to accomplish the goal?
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
Which command should be used on the Cisco FTD CLI to capture all the packets that hit an interface?
Which feature within the Cisco FMC web interface allows for detecting, analyzing and blocking malware in network traffic?
A network administrator is configuring a transparent Cisco Secure Firewall Threat Defense registered to a Cisco Secure Firewall Management Center. The administrator wants to configure the Secure Firewall Threat Defense to allow ARP traffic to pass between two interfaces of a bridge group. What must be configured?
An engineer is configuring Cisco Secure Firewall Threat Defense managed by a Secure Firewall Management Center appliance. The company wants remote access VPN users to be reachable from the inside network. What must the engineer configure to meet the requirements?
What is an advantage of adding multiple inline interface pairs to the same inline interface set when deploying an asynchronous routing configuration?
Which report template field format is available in Cisco FMC?
Which firewall mode is Cisco Secure Firewall Threat Defense in when two physical interfaces are assigned to a named BVI?
Which interface type allows packets to be dropped?
An engineer must integrate a thud-party security Intelligence teed with Cisco Secure Firewall Management Center. Secure Firewall Management Center is running Version 6.2 3 and has 8 GB of memory. Which two actions must be taken to implement Throat Intelligence Director? (Choose two.)
Which feature sets up multiple interfaces on a Cisco Secure Firewall Threat Defense to be on the same subnet?
A network engineer is planning on replacing an Active/Standby pair of physical Cisco Secure Firewall ASAs with a pair of Cisco Secure Firewall Threat Defense Virtual appliances. Which two virtual environments support the current High Availability configuration? (Choose two.)
What is a feature of Cisco AMP private cloud?