Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) Questions and Answers
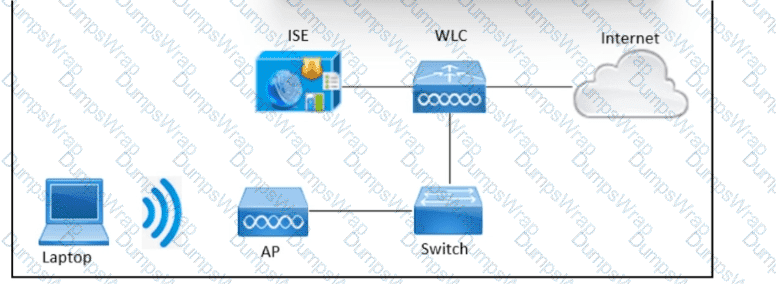
Refer to the exhibit. An engineer needs to configure central web authentication on the Cisco Wireless LAN Controller to use Cisco ISE for all guests connected to the wireless network. The components are configured already:
• Cisco Wireless LAN Controller is fully configured
• authorization profile on the Cisco ISE
• authentication policy on the Cisco ISE
Which component would be configured next on Cisco ISE?
An administrator is responsible for configuring network access for a temporary network printer. The administrator must only use the printer MAC address 50:89:65: 18:8: AB for authentication. Which authentication method will accomplish the task?
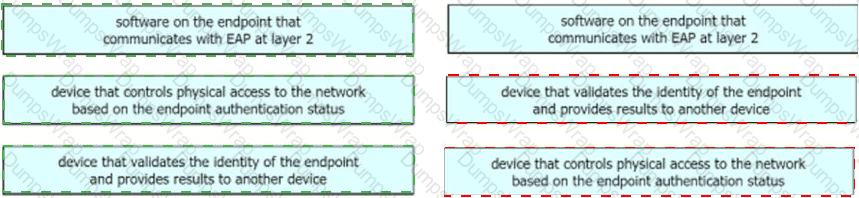
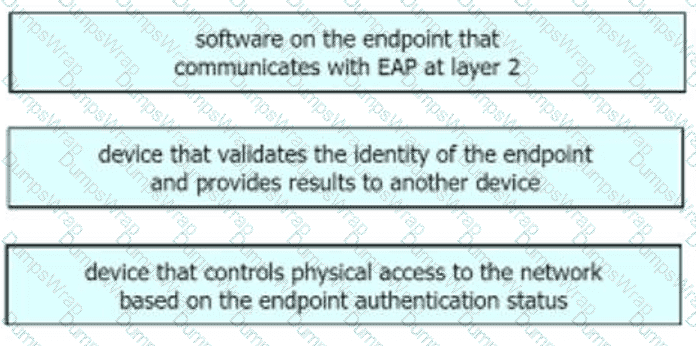
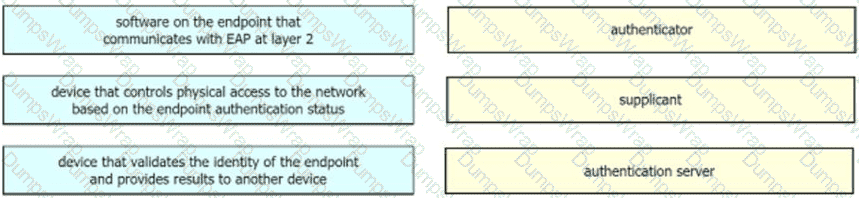
Drag the descriptions on the left onto the components of 802.1X on the right.
A network engineer must create a guest portal for wireless guests on Cisco ISE. The guest users must not be able to create accounts; however, the portal should require a username and password to connect. Which portal type must be created in Cisco ISE to meet the requirements?
What is the minimum certainty factor when creating a profiler policy?
What are two differences of TACACS+ compared to RADIUS? (Choose two.)
An engineer wants to use certificate authentication for endpoints that connect to a wired network integrated with Cisco ISE. The engineer needs to define the certificate field used as the principal username. Which component would be needed to complete the configuration?
Which two default endpoint identity groups does Cisco ISE create? (Choose two )
What is a function of client provisioning?
What are two requirements of generating a single signing in Cisco ISE by using a certificate provisioning portal, without generating a certificate request? (Choose two )
What must be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
A network engineer is configuring a Cisco Wireless LAN Controller in order to find out more information about the devices that are connecting. This information must be sent to Cisco ISE to be used in authorization policies. Which profiling mechanism must be configured in the Cisco Wireless LAN Controller to accomplish this task?
An adminístrator is migrating device administration access to Cisco ISE from the legacy TACACS+ solution that used only privilege 1 and 15 access levels. The organization requires more granular controls of the privileges and wants to customize access levels 2-5 to correspond with different roles and access needs. Besides defining a new shell profile in Cisco ISE. what must be done to accomplish this configuration?
A network engineer is configuring Cisco TrustSec and needs to ensure that the Security Group Tag is being transmitted between two devices Where in the Layer 2 frame should this be verified?
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability. Which probe must be used to accomplish this task?
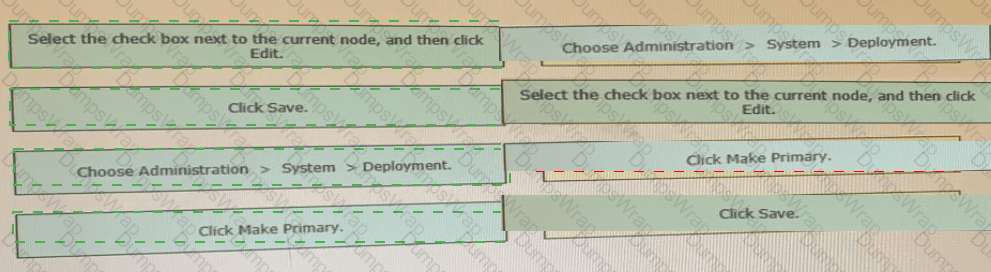
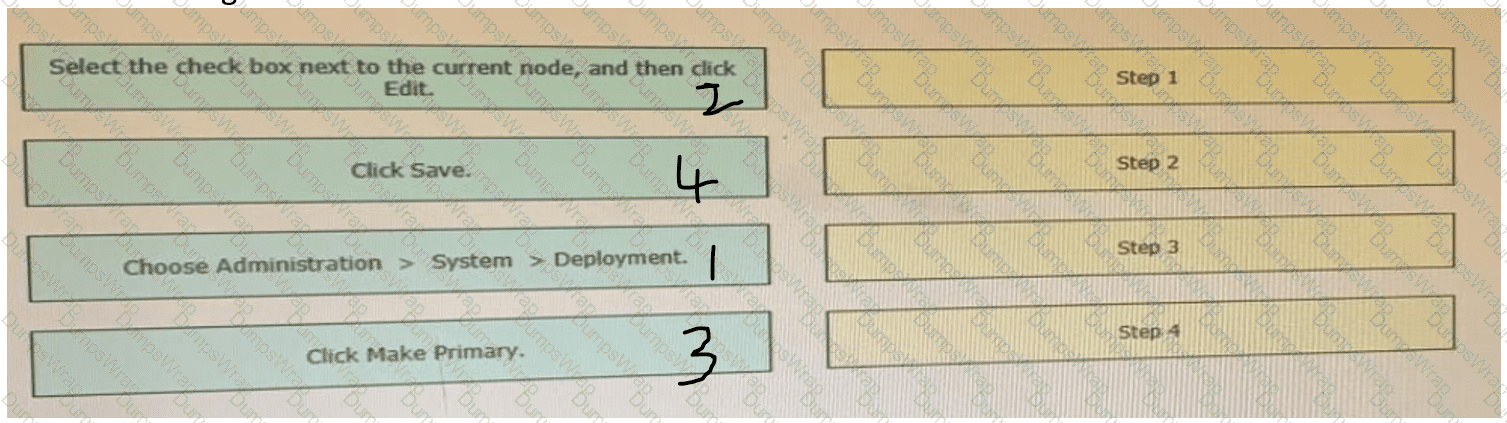
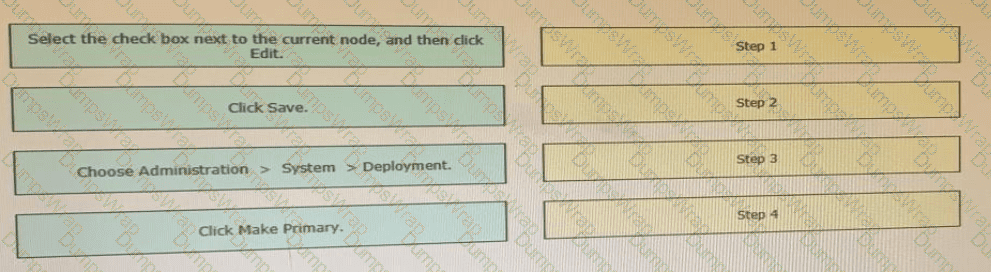
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the night.
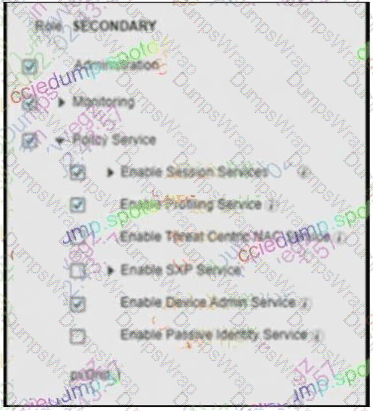
Which two roles are taken on by the administration person within a Cisco ISE distributed environment? (Choose two.)
Which use case validates a change of authorization?
An administrator enables the profiling service for Cisco ISE to use for authorization policies while in closed mode. When the endpoints connect, they receive limited access so that the profiling probes can gather information and Cisco ISE can assign the correct profiles. They are using the default values within Cisco ISE. but the devices do not change their access due to the new profile. What is the problem'?
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
Refer to the exhibit.
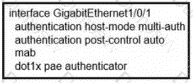
Which switch configuration change will allow only one voice and one data endpoint on each port?
What is a difference between TACACS+ and RADIUS in regards to encryption?
An engineer is using Cisco ISE and configuring guest services to allow wireless devices to access the network. Which action should accomplish this task?
A network administrator is configuring client provisioning resource policies for client machines and must ensure that an agent pop-up is presented to the client when attempting to connect to the network Which configuration item needs to be added to allow for this'?
A network administrator must configure Cisco SE Personas in the company to share session information via syslog. Which Cisco ISE personas must be added to syslog receivers to accomplish this goal?
MacOS users are complaining about having to read through wordy instructions when remediating their workstations to gam access to the network Which alternate method should be used to tell users how to remediate?
An engineer is configuring Central Web Authentication in Cisco ISE to provide guest access. When an authentication rule is configured in the Default Policy Set for the Wired_MAB or Wireless_MAB conditions, what must be selected for the "if user not found" setting?
What are two benefits of TACACS+ versus RADIUS for device administration? (Choose two )
Which two VMware features are supported on a Cisco ISE virtual appliance? (Choose two.)
A network administrator changed a Cisco ISE deployment from pilot to production and noticed that the JVM memory utilization increased significantly. The administrator suspects this is due to replication between the nodes What must be configured to minimize performance degradation?
Which two actions occur when a Cisco ISE server device administrator logs in to a device? (Choose two)
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two )
Which nodes are supported in a distributed Cisco ISE deployment?
What sends the redirect ACL that is configured in the authorization profile back to the Cisco WLC?
An engineer is configuring web authentication and needs to allow specific protocols to permit DNS traffic. Which type of access list should be used for this configuration?
A network administrator must configura endpoints using an 802 1X authentication method with EAP identity certificates that are provided by the Cisco ISE When the endpoint presents the identity certificate to Cisco ISE to validate the certificate, endpoints must be authorized to connect to the network Which EAP type must be configured by the network administrator to complete this task?
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
An administrator is editing a csv list of endpoints and wants to reprofile some of the devices indefinitely before importing the list into Cisco ISE. Which field and Boolean value must be changed for the devices before the list is reimported?
How is policy services node redundancy achieved in a deployment?
What is a valid guest portal type?
An engineer must configure Cisco ISE to provide internet access for guests in which guests are required to enter a code to gain network access. Which action accomplishes the goal?
An administrator plans to use Cisco ISE to deploy posture policies to assess Microsoft Windows endpoints that run Cisco Secure Client. The administrator wants to minimize the occurrence of messages related to unknown posture profiles if Cisco ISE fails to determine the posture of the endpoint. Secure Client is deployed to all the endpoints. and all the required Cisco ISE authentication, authorization, and posture policy configurations were performed. Which action must be taken next to complete the configuration?
TION NO: 33
Which portal is used to customize the settings for a user to log in and download the compliance module?
NO: 184
An engineer builds a five-node distributed Cisco ISE deployment The first two deployed nodes are responsible for the primary and secondary administration and monitoring personas Which persona configuration is necessary to have the remaining three Cisco ISE nodes serve as dedicated nodes in the Cisco ISE cube that is responsible only for handling the RADIUS and TACACS+ authentication requests, identity lookups, and policy evaluation?
A)
B)
C)
D)
When planning for the deployment of Cisco ISE, an organization's security policy dictates that they must use network access authentication via RADIUS. It also states that the deployment provide an adequate amount of security and visibility for the hosts on the network. Why should the engineer configure MAB in this situation?
An engineer is designing a new distributed deployment for Cisco ISE in the network and is considering failover options for the admin nodes. There is a need to ensure that an admin node is available for configuration of policies at all times. What is the requirement to enable this feature?
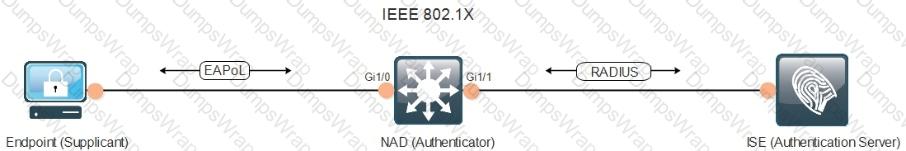
Refer to the exhibit.
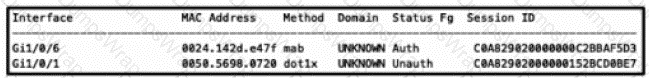
An engineer is configuring a client but cannot authenticate to Cisco ISE During troubleshooting, the show authentication sessions command was issued to display the authentication status of each port Which command gives additional information to help identify the problem with the authentication?
Users in an organization report issues about having to remember multiple usernames and passwords. The network administrator wants the existing Cisco ISE deployment to utilize an external identity source to alleviate this issue. Which two requirements must be met to implement this change? (Choose two.)
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
When setting up profiling in an environment using Cisco ISE for network access control, an organization must use non-proprietary protocols for collecting the information at layer 2. Which two probes will provide this information without forwarding SPAN packets to Cisco ISE? {Choose two.)
An administrator must provide network access to legacy Windows endpoints with a specific device type and operating system version using Cisco ISE profiler services. The ISE profiler services and access switches must be configured to identify endpoints using the dhcp-class-identifier and parameters-request-list attributes from the DHCP traffic. These configurations were performed:
enabled the DHCP probe in Cisco ISE
configured the Cisco ISE PSN interface to receive DHCP packets
configured the attributes in custom profiling conditions
configured a custom profiling policy
configured an authorization rule with permit access
Which action completes the configuration?
An organization is adding nodes to their Cisco ISE deployment and has two nodes designated as primary and secondary PAN and MnT nodes. The organization also has four PSNs An administrator is adding two more PSNs to this deployment but is having problems adding one of them What is the problem?
What is the Microsoft security policy recommendation (or fast user switching in Cisco ISE?
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
TION NO: 69
Refer to the exhibit.

A network engineers configuring the switch to accept downloadable ACLs from a Cisco ISC server Which two commands should be run to complete the configuration? (Choose two)
The IT manager wants to provide different levels of access to network devices when users authenticate using TACACS+. The company needs specific commands to be allowed based on the Active Directory group membership of the different roles within the IT department. The solution must minimize the number of objects created in Cisco ISE. What must be created to accomplish this task?
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
An organization wants to split their Cisco ISE deployment to separate the device administration functionalities from the mam deployment. For this to work, the administrator must deregister any nodes that will become a part of the new deployment, but the button for this option is grayed out Which configuration is causing this behavior?
A network administrator is configuring a secondary cisco ISE node from the backup configuration of the primary cisco ISE node to create a high availability pair The Cisco ISE CA certificates and keys must be manually backed up from the primary Cisco ISE and copied into the secondary Cisco ISE Which command most be issued for this to work?
Which two authentication protocols are supported by RADIUS but not by TACACS+? (Choose two.)
An engineer is using the low-impact mode for a phased deployment of Cisco ISE and is trying to connect to the network prior to authentication. Which access will be denied in this?
An engineer is deploying a new Cisco ISE environment for a company. The company wants the deployment to use TACACS+. The engineer verifies that Cisco ISE has a Device Administration license. What must be configured to enable TACACS+ operations?
A user changes the status of a device to stolen in the My Devices Portal of Cisco ISE. The device was originally onboarded in the BYOD wireless Portal without a certificate. The device is found later, but the user cannot re-onboard the device because Cisco ISE assigned the device to the Blocklist endpoint identity group. What must the user do in the My Devices Portal to resolve this issue?
Which RADIUS attribute is used to dynamically assign the inactivity active timer for MAB users from the Cisco ISE node'?
Which two external identity stores support EAP-TLS and PEAP-TLS? (Choose two.)
An employee must access the internet through the corporate network from a new mobile device that does not support native supplicant provisioning provided by Cisco ISE. Which portal must the employee use to provision to the device?
An administrator is configuring new probes to use with Cisco ISE and wants to use metadata to help profile the endpoints. The metadata must contain traffic information relating to the endpoints instead of industry-standard protocol information Which probe should be enabled to meet these requirements?
Refer to the exhibit Which component must be configured to apply the SGACL?
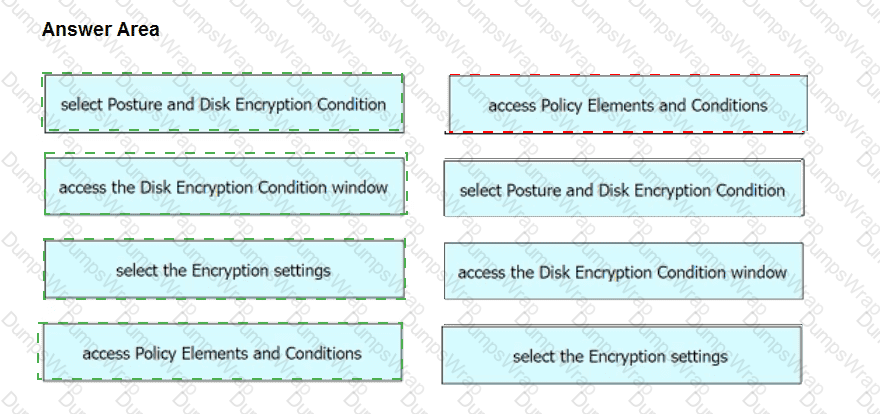
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
What is an advantage of using EAP-TLS over EAP-MS-CHAPv2 for client authentication?
NO: 188
During a 802 1X deployment, an engineer must identify failed authentications without causing problems for the connected endpoint. Which command will successfully achieve this''
An engineer is configuring sponsored guest access and needs to limit each sponsored guest to a maximum of two devices. There are other guest services in production that rely on the default guest types. How should this configuration change be made without disrupting the other guest services currently offering three or more guest devices per user?
Refer to the exhibit.
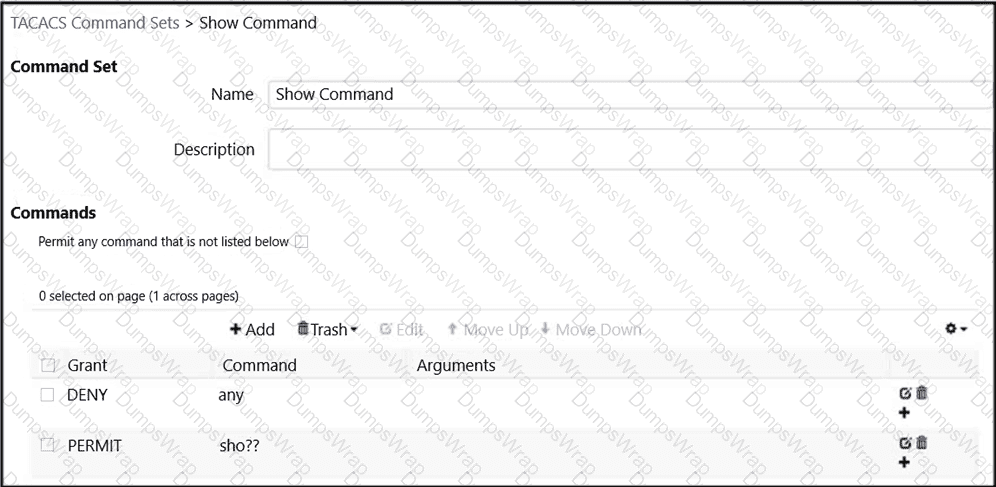
An engineer is creating a new TACACS* command set and cannot use any show commands after togging into the device with this command set authorization Which configuration is causing this issue?
An engineer wants to learn more about Cisco ISE and deployed a new lab with two nodes. Which two persona configurations allow the engineer to successfully test redundancy of a failed node? (Choose two.)
An engineer is configuring static SGT classification. Which configuration should be used when authentication is disabled and third-party switches are in use?
A Cisco ISE server sends a CoA to a NAD after a user logs in successfully using CWA Which action does the CoA perform?
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group. These configurations were performed:
Configured an identity group named allowlist
Configured the endpoints to use the MAC address of incompatible 802.1X devices
Added the endpoints to the allowlist identity group
Configured an authentication policy for MAB users
What must be configured?
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group. These configurations were performed:
• configured an identity group named allowlist
• configured the endpoints to use the MAC address of incompatible 802.1X devices
• added the endpoints to the allowlist identity group
• configured an authentication policy for MAB users
What must be configured?
During BYOD flow, from where does a Microsoft Windows PC download the Network Setup Assistant?
Which default "guest type" is included with Cisco ISE?
An administrator is configuring TACACS+ on a Cisco switch but cannot authenticate users with Cisco ISE. The configuration contains the correct key of Cisc039712287. but the switch is not receiving a response from the Cisco ISE instance What must be done to validate the AAA configuration and identify the problem with the TACACS+ servers?
An administrator is configuring a new profiling policy within Cisco ISE The organization has several endpoints that are the same device type and all have the same Block ID in their MAC address. The profiler does not currently have a profiling policy created to categorize these endpoints. therefore a custom profiling policy must be created Which condition must the administrator use in order to properly profile an ACME Al Connector endpoint for network access with MAC address
An administrator adds a new network device to the Cisco ISE configuration to authenticate endpoints to the network. The RADIUS test fails after the administrator configures all of the settings in Cisco ISE and adds the proper configurations to the switch. What is the issue"?
Which profiling probe collects the user-agent string?
An administrator needs to allow guest devices to connect to a private network without requiring usernames and passwords. Which two features must be configured to allow for this? (Choose two.)
An engineer is configuring a virtual Cisco ISE deployment and needs each persona to be on a different node. Which persona should be configured with the largest amount of storage in this environment?
Using the SAK Active Directory Federation Services server. The configurations were performed:
• created a new SAML Identity provider profile in Cisco ISE
• exported the service provider Information
• configured all the required Active Directory Federation Services configurations
• Imported the Active Directory Federation Services metadata
• configured groups in the new SAML identity
• added attributes to the new SAML identity provider profile
• configured Advanced Settings in the new SAML identity provider profile
Which two actions must be taken to complete the configuration? (Choose two.)
What is the default port used by Cisco ISE for NetFlow version 9 probe?