Securing Email with Cisco Email Security Appliance (300-720 SESA) Questions and Answers
A network engineer must tighten up the SPAM control policy of an organization due to a recent SPAM attack. In which scenario does enabling regional scanning improve security for this organization?
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
A content dictionary was created for use with Forged Email Detection. Proper data that pertains to the CEO Example CEO:
Which attack is mitigated by using Bounce Verification?
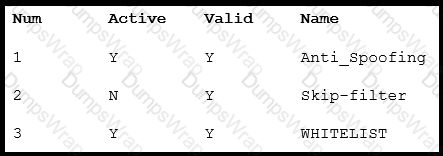
Refer to the exhibit. What is the correct order of commands to set filter 2 to active?
What is the default HTTPS port when configuring spam quarantine on Cisco ESA?
The CEO sent an email indicating that all emails containing a string of 123ABCDEFGHJ cannot be delivered and must be sent into quarantine for further inspection. Given the requirement, which regular expression should be used to match on that criteria?
What are two primary components of content filters? (Choose two.)
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
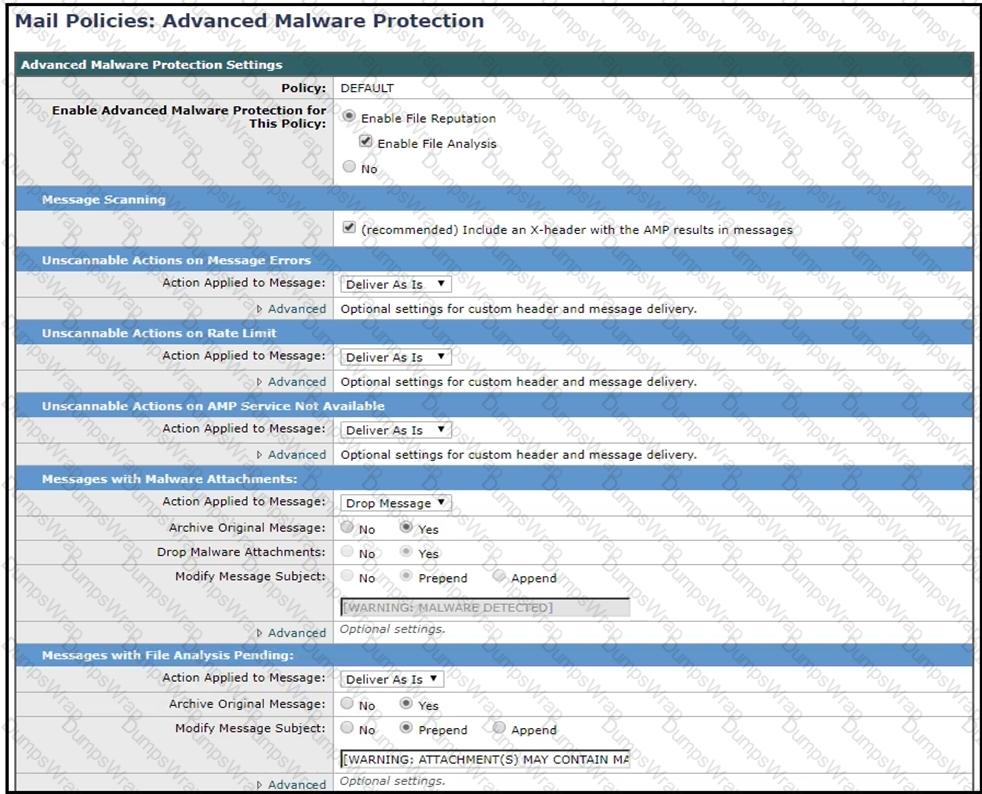
Refer to the exhibit. How should this configuration be modified to stop delivering Zero Day malware attacks?
Spreadsheets containing credit card numbers are being allowed to bypass the Cisco ESA.
Which outgoing mail policy feature should be configured to catch this content before it leaves the network?
An engineer must provide differentiated email filtering to executives within the organization Which two actions must be taken to accomplish this task? (Choose two)
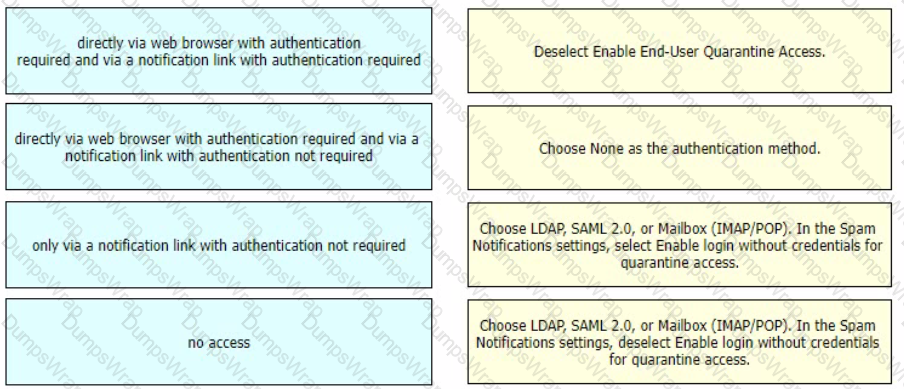
Drag and drop authentication options for End-User Quarantine Access from the left onto the corresponding configuration steps on the right.
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
Refer to the exhibit.
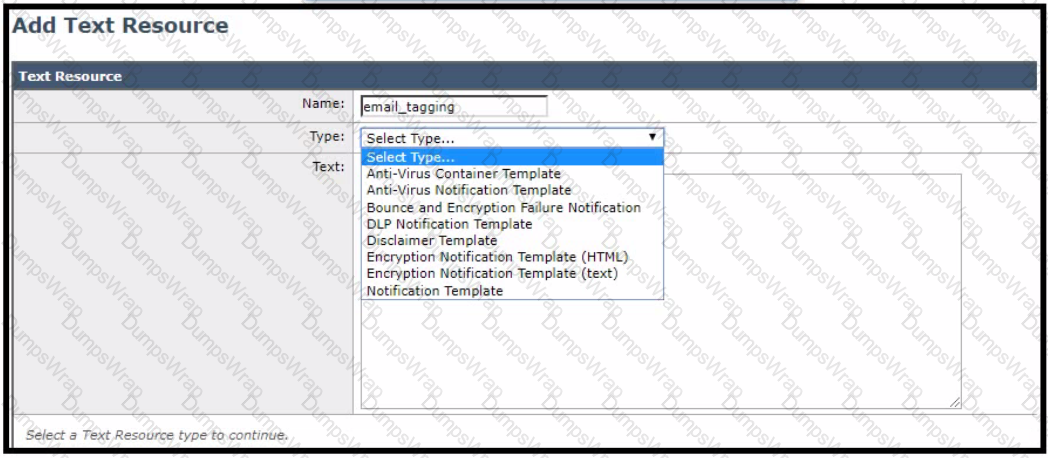
For improved security, an administrator wants to warn users about opening any links or attachments within an email How must the administrator configure an HTML-coded message at the top of an email body to create this warning?
Which feature utilizes sensor information obtained from Talos intelligence to filter email servers connecting into the Cisco ESA?
Which setting affects the aggressiveness of spam detection?
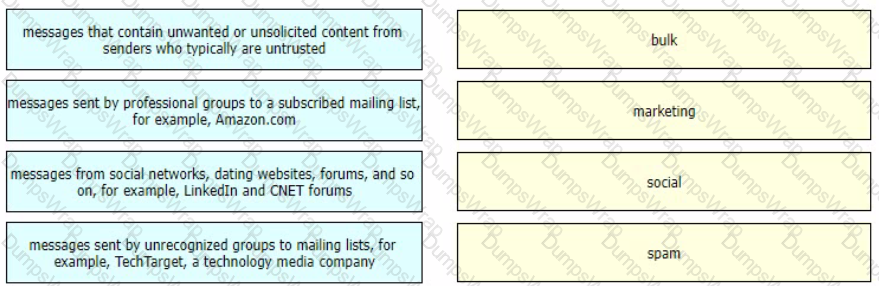
Which two components form the graymail management solution in Cisco ESA? (Choose two.)
The company security policy requires that the finance department have an easy way to apply encryption to their outbound messages that contain sensitive data Users must be able to flag the messages that require encryption versus a Cisco Secure Email Gateway appliance scanning all messages and automatically encrypting via detection Which action enables this capability?
Refer to the exhibit.
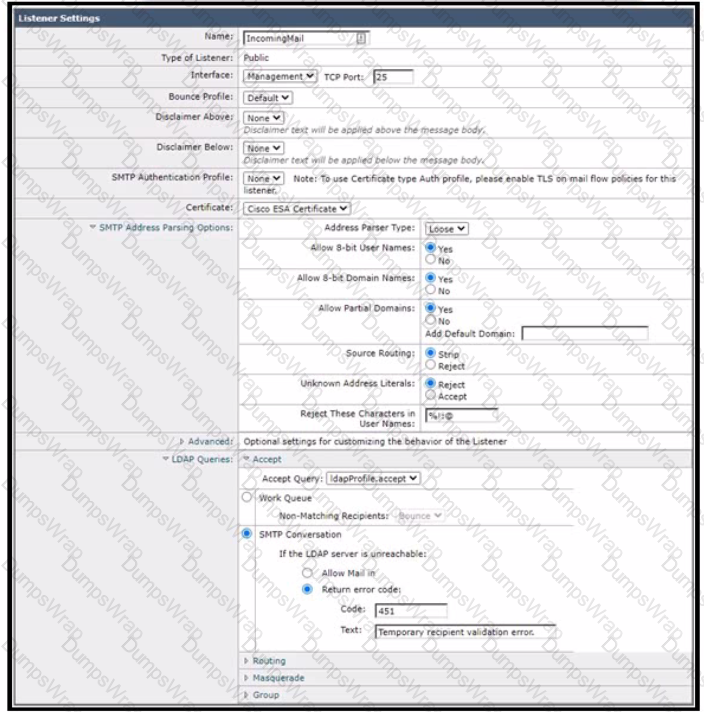
Which additional configuration action must be taken to protect against Directory Harvest Attacks?
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
Which feature utilizes sensor information obtained from Talos intelligence to filter email servers connecting into the Cisco ESA?
Which Cisco ESA security service is configured only through an outgoing mail policy?
What is the default port to deliver emails from the Cisco ESA to the Cisco SMA using the centralized Spam Quarantine?
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
A Cisco Secure Email Gateway administrator is creating a Mail Flow Policy to receive outbound email from Microsoft Exchange. Which Connection Behavior must be selected to properly process the messages?
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
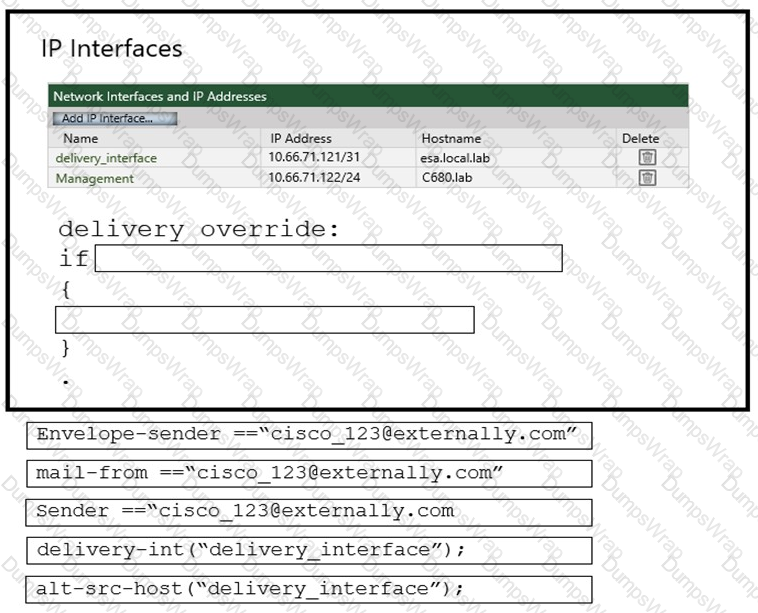
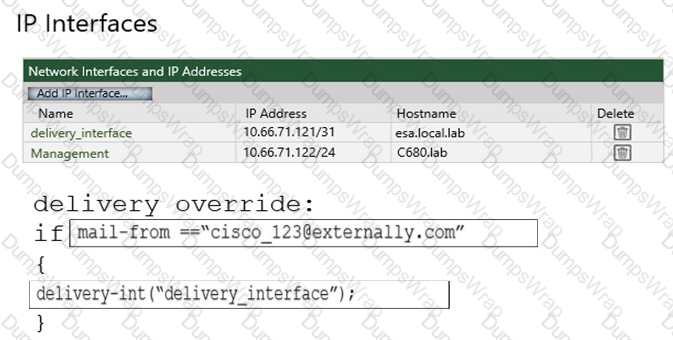
An administrator must ensure that emails sent from cisco_123@externally.com are routed through an alternate virtual gateway. Drag and drop the snippet from the bottom onto the blank in the graphic to finish the message filter syntax. Not all snippets are used.
Which type of attack is prevented by configuring file reputation filtering and file analysis features?
How does the graymail safe unsubscribe feature function?
An engineer wants to utilize a digital signature in outgoing emails to validate to others that the email they are receiving was indeed sent and authorized by the owner of that domain Which two components should be configured on the Cisco Secure Email Gateway appliance to achieve this? (Choose two.)
An email containing a URL passes through the Cisco ESA that has content filtering disabled for all mail policies. The sender is sampleuser@test1.com, the recipients are testuser1@test2.com, testuser2@test2.com, testuser3@test2.com, and mailer1@test2.com. The subject of the email is Test Document395898847. An administrator wants to add a policy to ensure that the Cisco ESA evaluates the web reputation score before permitting this email.
Which two criteria must be used by the administrator to achieve this? (Choose two.)
What is the default behavior of any listener for TLS communication?
Which setting affects the aggressiveness of spam detection?
Which two steps configure Forged Email Detection? (Choose two.)
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
An engineer deploys a Cisco Secure Email Gateway appliance with default settings in an organization that permits only standard H feature does not work. Which additional action resolves the issue?
Which two certificate authority lists are available in Cisco ESA? (Choose two.)
Refer to the exhibit.
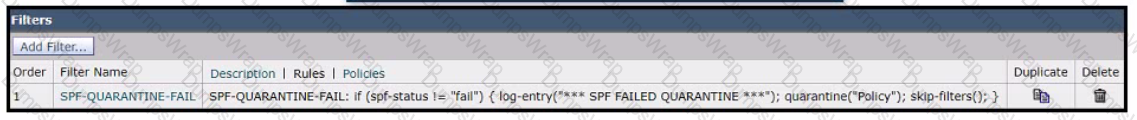
A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
An Encryption Profile has been set up on the Cisco ESA.
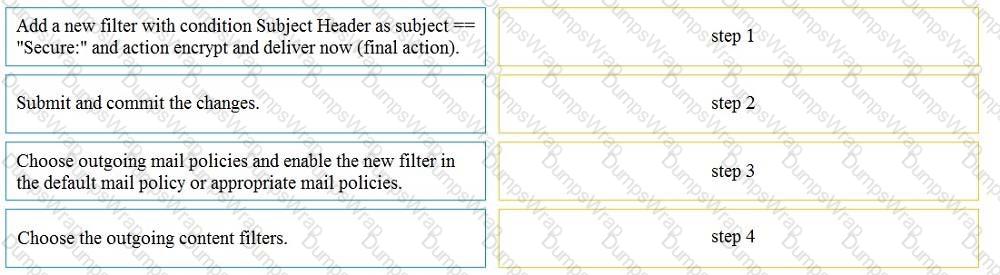
Drag and drop the steps from the left for creating an outgoing content filter to encrypt emails that contains the subject "Secure:" into the correct order on the right.
When DKIM signing is configured, which DNS record must be updated to load the DKIM public signing key?
Drag and drop the graymail descriptions from the left onto the verdict categories they belong to on the right.
Which method enables an engineer to deliver a flagged message to a specific virtual gateway address in the most flexible way?
When the spam quarantine is configured on the Cisco Secure Email Gateway, which type of query is used to validate non administrative user access to the end-user quarantine via LDAP?



 Table
Description automatically generated
Table
Description automatically generated

