Implementing Secure Solutions with Virtual Private Networks (SVPN) Questions and Answers
Refer to the exhibit.

An SSL client is connecting to an ASA headend. The session fails with the message “Connection attempt has timed out. Please verify Internet connectivity.” Based on how the packet is processed, which phase is causing the failure?
Refer to the exhibit.
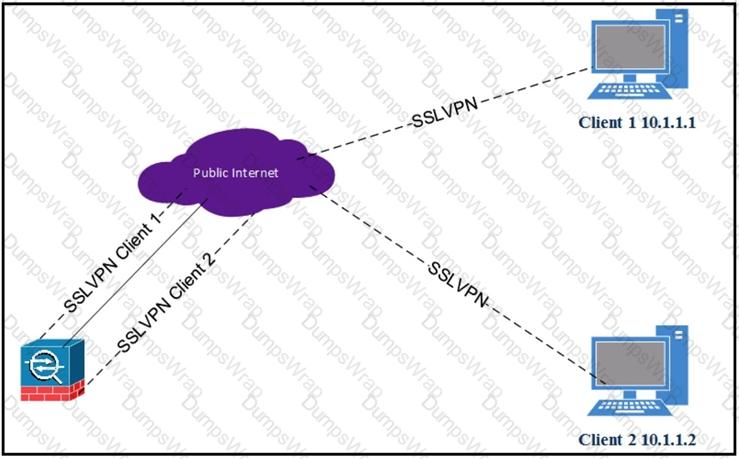
Client 1 cannot communicate with client 2. Both clients are using Cisco AnyConnect and have established a successful SSL VPN connection to the hub ASA. Which command on the ASA is missing?
Which command is used to troubleshoot an IPv6 FlexVPN spoke-to-hub connectivity failure?
Refer to the exhibit.
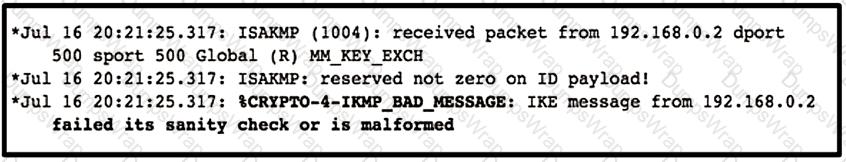
Which type of mismatch is causing the problem with the IPsec VPN tunnel?
Refer to the exhibit.
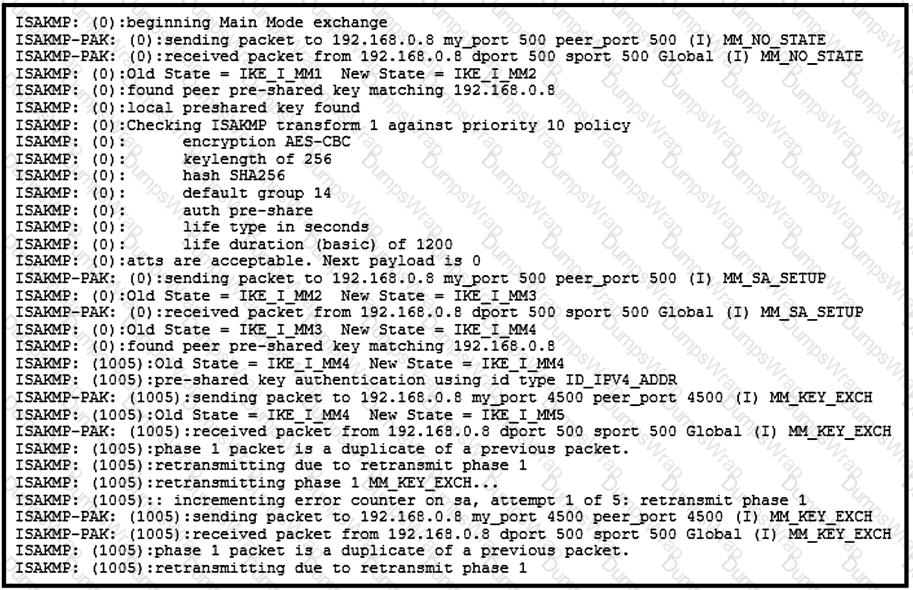
A site-to-site tunnel between two sites is not coming up. Based on the debugs, what is the cause of this issue?
Refer to the exhibit.
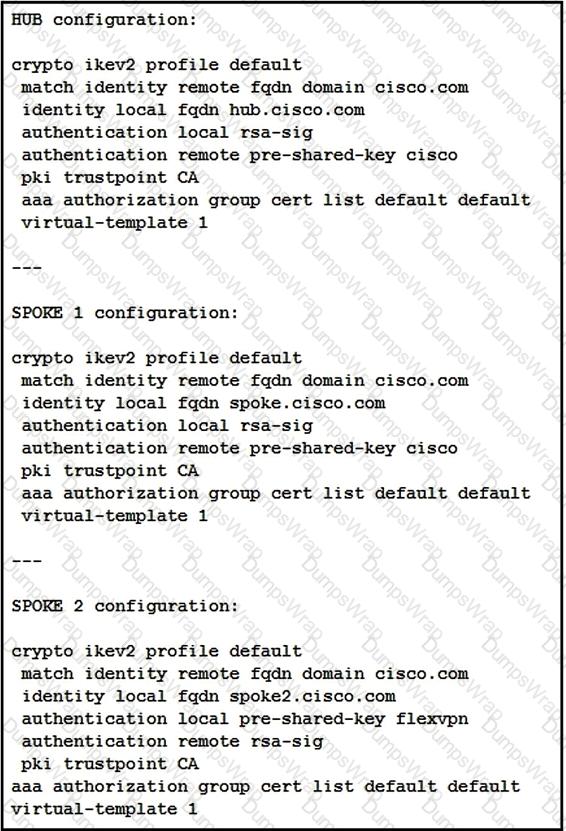
What is a result of this configuration?
Refer to the exhibit.
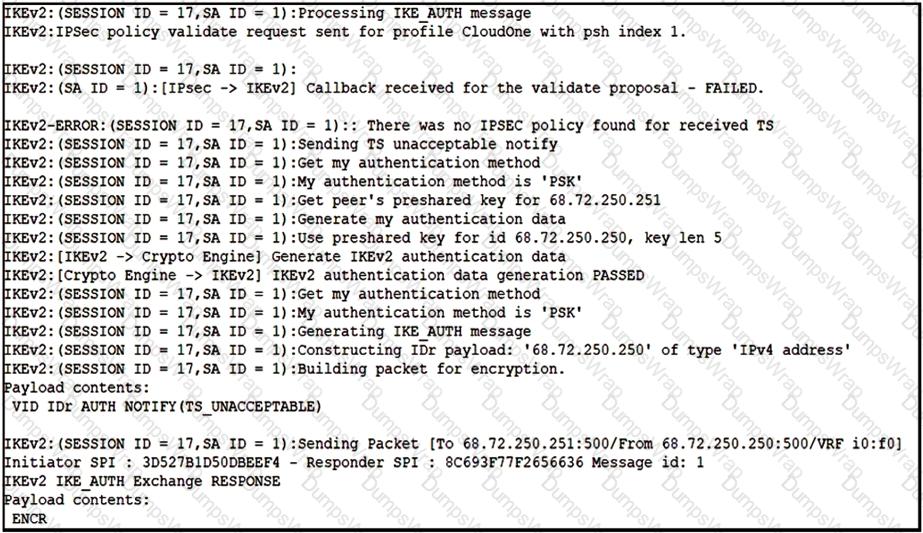
Based on the debug output, which type of mismatch is preventing the VPN from coming up?
An engineer is troubleshooting a new DMVPN setup on a Cisco IOS router. After the show crypto isakmp sa command is issued, a response is returned of "MM_NO_STATE." Why does this failure occur?
In a FlexVPN deployment, the spokes successfully connect to the hub, but spoke-to-spoke tunnels do not form. Which troubleshooting step solves the issue?
Refer to the exhibit.
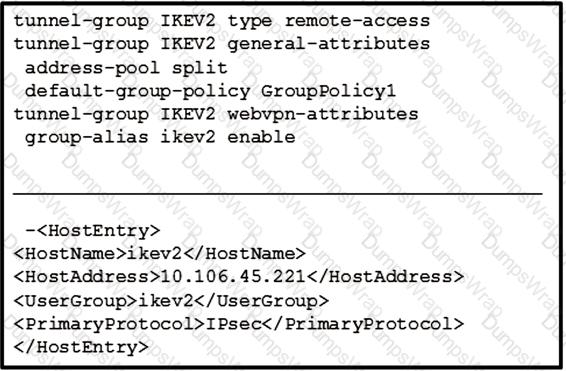
The customer can establish a Cisco AnyConnect connection without using an XML profile. When the host "ikev2" is selected in the AnyConnect drop down, the connection fails. What is the cause of this issue?
Refer to the exhibit.
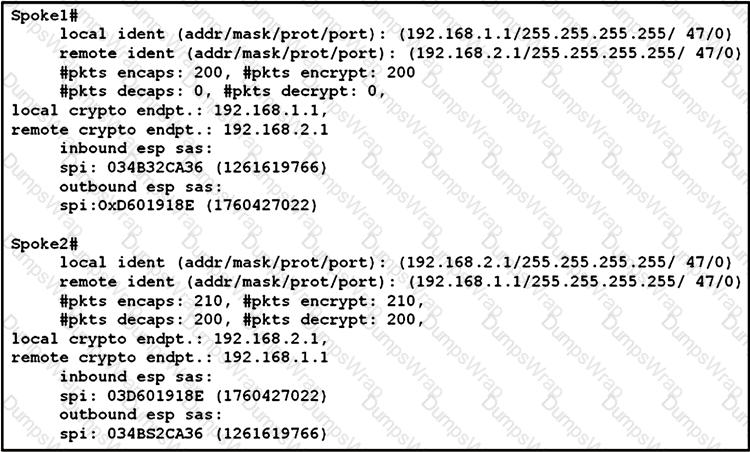
An engineer is troubleshooting a new GRE over IPsec tunnel. The tunnel is established but the engineer cannot ping from spoke 1 to spoke 2. Which type of traffic is being blocked?
Which IKE identity does an IOS/IOS-XE headend expect to receive if an IPsec Cisco AnyConnect client uses default settings?
Refer to the exhibit.
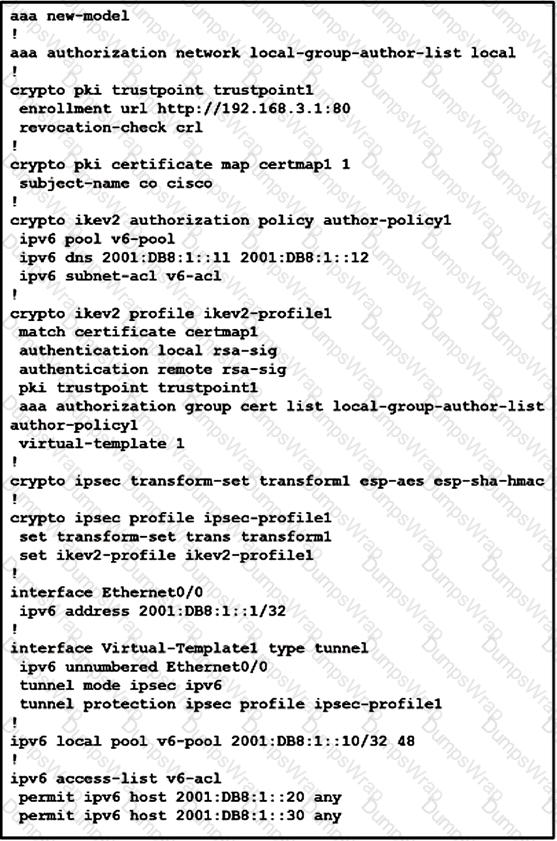
What is configured as a result of this command set?
Refer to the exhibit.
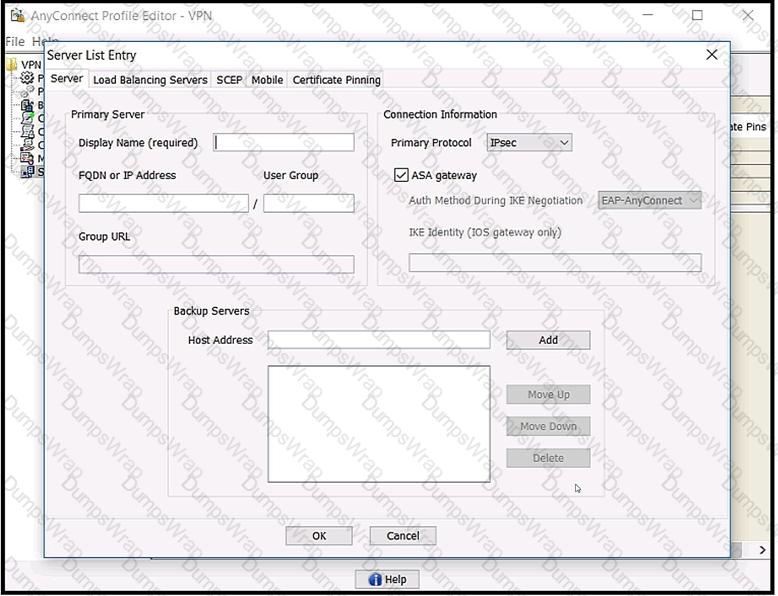
Which value must be configured in the User Group field when the Cisco AnyConnect Profile is created to connect to an ASA headend with IPsec as the primary protocol?
Which requirement is needed to use local authentication for Cisco AnyConnect Secure Mobility Clients that connect to a FlexVPN server?
Which command automatically initiates a smart tunnel when a user logs in to the WebVPN portal page?
Which configuration construct must be used in a FlexVPN tunnel?
Refer to the exhibit.
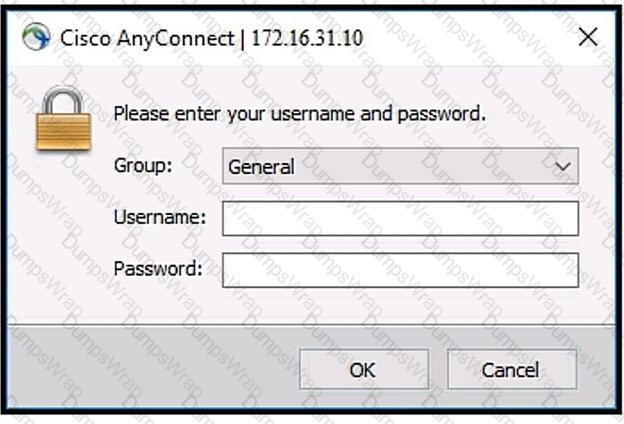
Which two commands under the tunnel-group webvpn-attributes result in a Cisco AnyConnect user receiving the AnyConnect prompt in the exhibit? (Choose two.)
Refer to the exhibit.
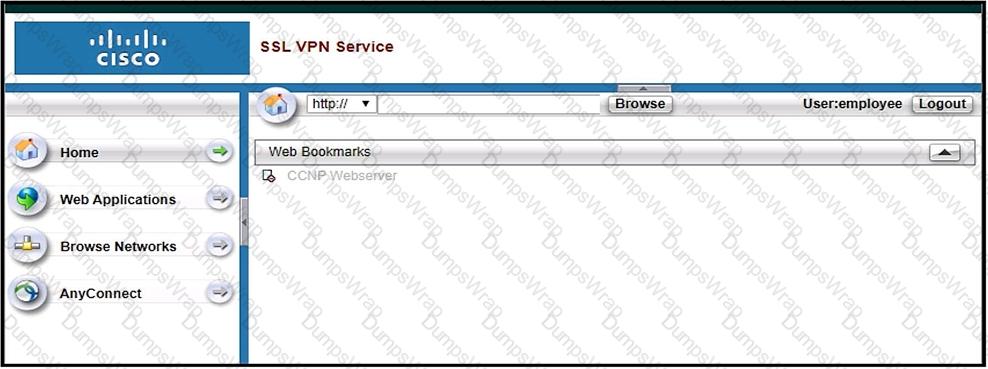
Based on the exhibit, why are users unable to access CCNP Webserver bookmark?
Under which section must a bookmark or URL list be configured on a Cisco ASA to be available for clientless SSLVPN users?
Which two features provide headend resiliency for Cisco AnyConnect clients? (Choose two.)
Cisco AnyConnect Secure Mobility Client has been configured to use IKEv2 for one group of users and SSL for another group. When the administrator configures a new AnyConnect release on the Cisco ASA, the IKEv2 users cannot download it automatically when they connect. What might be the problem?
What are two functions of ECDH and ECDSA? (Choose two.)
Which benefit of FlexVPN is a limitation of DMVPN using IKEv1?
What is a requirement for smart tunnels to function properly?
Which two commands help determine why the NHRP registration process is not being completed even after the IPsec tunnel is up? (Choose two.)
Which VPN does VPN load balancing on the ASA support?
Which two remote access VPN solutions support SSL? (Choose two.)
Refer to the exhibit.
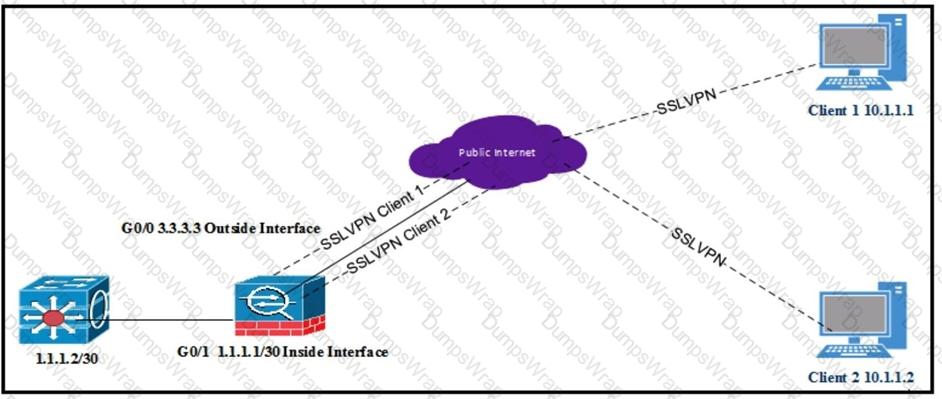
All internal clients behind the ASA are port address translated to the public outside interface that has an IP address of 3.3.3.3. Client 1 and client 2 have established successful SSL VPN connections to the ASA. What must be implemented so that "3.3.3.3" is returned from a browser search on the IP address?
Which technology works with IPsec stateful failover?
Which feature of GETVPN is a limitation of DMVPN and FlexVPN?
Which technology is used to send multicast traffic over a site-to-site VPN?
Where is split tunneling defined for IKEv2 remote access clients on a Cisco router?
A network engineer is implementing a FlexVPN tunnel between two Cisco IOS routers. The FlexVPN tunnels will terminate on encrypted traffic on an interface configured with an IP MTU of 1500, and the company has a security policy to drop fragmented traffic coming into or leaving the network. The tunnel will be used to transfer TFTP data between users and internal servers. When the TFTP traffic is not traversing a VPN, it can have a maximum IP packet size of 1500. Assuming the encrypted payload will add 90 bytes, which configuration allows TFTP traffic to traverse the FlexVPN tunnel without being dropped?
Which command shows the smart default configuration for an IPsec profile?
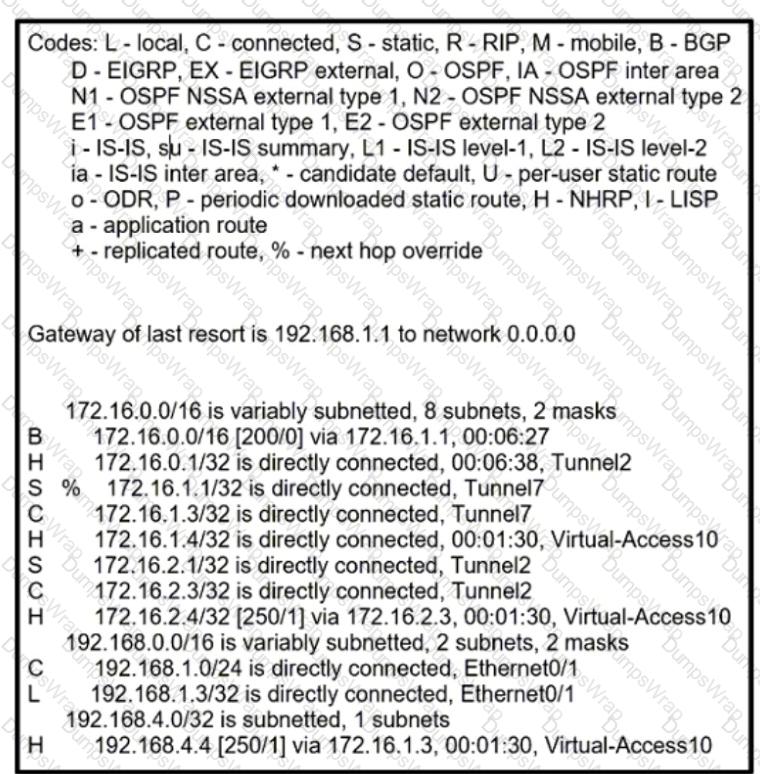
Given the output of the show ip route command, which remote access VPN technology is in use?
An engineer is using DMVPN to provide secure connectivity between a data center and remote sites. Which two routing protocols should be used between the routers? (Choose two.)
A company needs to ensure only corporate issued laptops and devices are allowed to connect with the Cisco AnyConnect client. The solution should be applicable to multiple operating systems, including Windows, MacOS, and Linux, and should allow for remote remediation if a corporate issued device is stolen. Which solution should be used to accomplish these goals?
An engineer is requesting an SSL certificate for a VPN load-balancing cluster in which two Cisco ASAs provide clientless SSLVPN access. The FQDN that users will enter to access the clientless VPN is asa.example.com, and users will be redirected to either asa1.example.com or asa2.example.com. The cluster FQDN and individual Cisco ASAs FQDNs resolve to IP addresses 192.168.0.1, 192.168.0.2, and 192.168.0.3 respectively. The issued certificate must be able to be used to validate the identity of either ASA in the cluster without returning any certificate validation errors. Which fields must be included in the certificate to meet these requirements?
Refer to the exhibit.

Users cannot connect via AnyConnect SSLVPN. Which action resolves this issue?
An engineer has integrated a new DMVPN to link remote offices across the internet using Cisco IOS routers. When connecting to remote sites, pings and voice data appear to flow properly, and all tunnel stats show that they are up. However, when trying to connect to a remote server using RDP, the connection fails. Which action resolves this issue?
While troubleshooting, an engineer finds that the show crypto isakmp sa command indicates that the last state of the tunnel is MM_KEY_EXCH. What is the next step that should be taken to resolve this issue?
Which VPN technology must be used to ensure that routers are able to dynamically form connections with each other rather than sending traffic through a hub and be able to advertise routes without the use of a dynamic routing protocol?
A network engineer must expand a company's Cisco AnyConnect solution. Currently, a Cisco ASA is set up in North America and another will be installed in Europe with a different IP address. Users should connect to the ASA that has the lowest Round Trip Time from their network location as measured by the AnyConnect client. Which solution must be implemented to meet this requirement?
Refer to the exhibit.
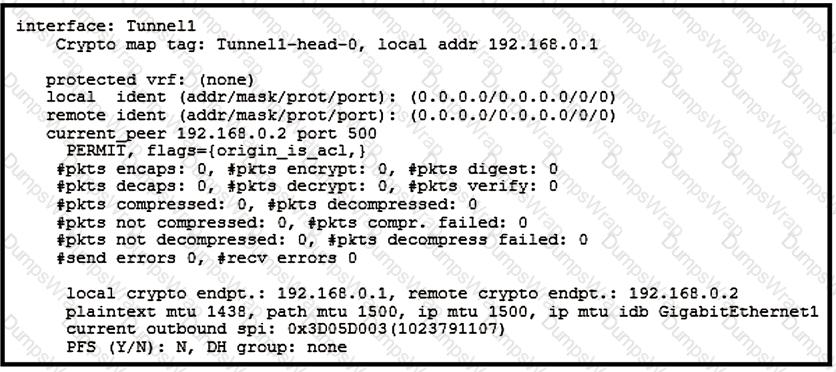
Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
Which two parameters help to map a VPN session to a tunnel group without using the tunnel-group list? (Choose two.)
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2 packet will contain details of the exchange?
Which statement about GETVPN is true?
Refer to the exhibit.

A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based on the syslog message, which action brings up the VPN tunnel?
Which method dynamically installs the network routes for remote tunnel endpoints?
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose two.)
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed, which command is needed for the hub to be able to terminate FlexVPN tunnels?

