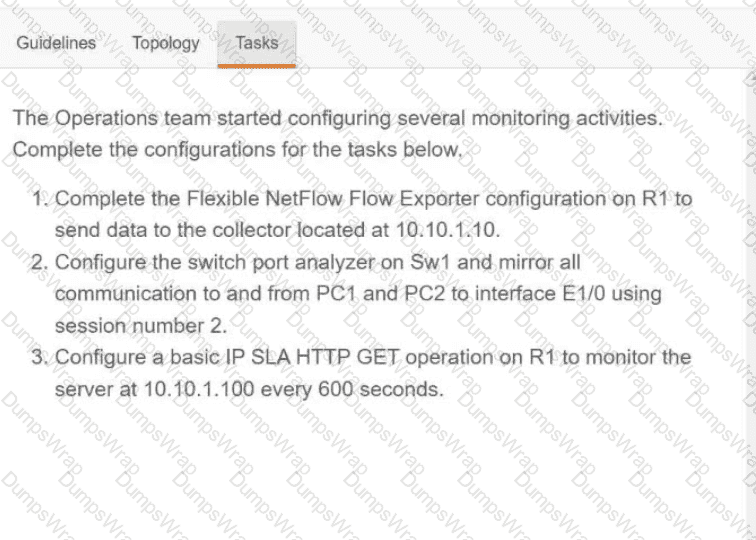
Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) Questions and Answers
What are two benefits of using Cisco TrustSec? (Choose two.)
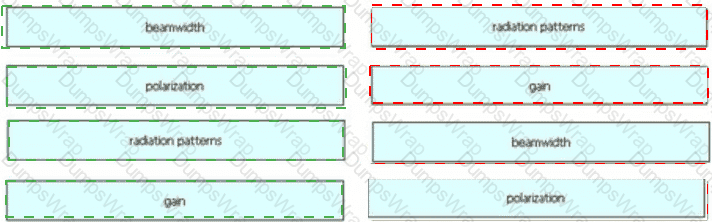
Drag and drop the wireless elements on the left to their definitions on the right.

What happens when a FlexConnect AP changes to standalone mode?
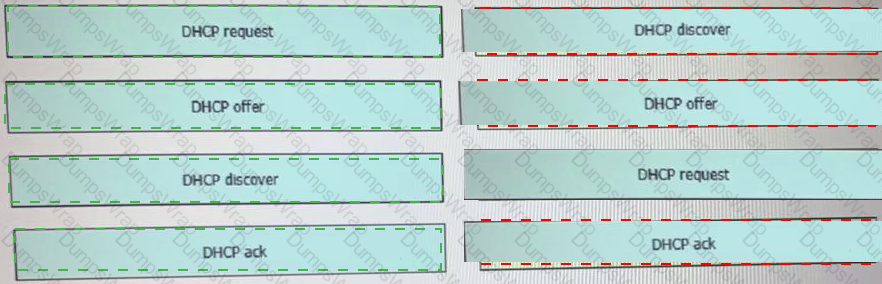
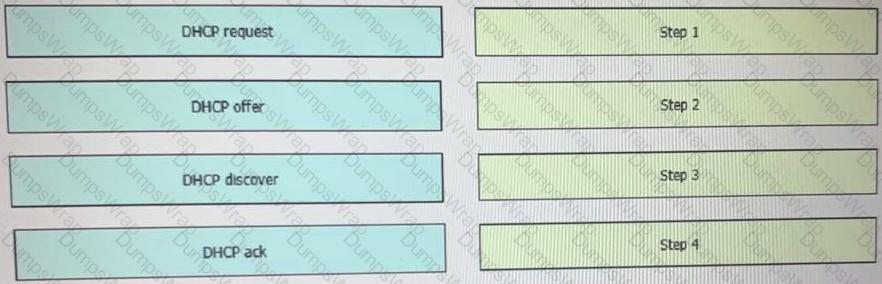
Drag and drop the DHCP messages that are exchanged between a client and an AP into the order they are exchanged on the right.
An engineer configures a WLAN with fast transition enabled Some legacy clients fail to connect to this WLAN Which feature allows the legacy clients to connect while still allowing other clients to use fast transition based on then OLTIs?
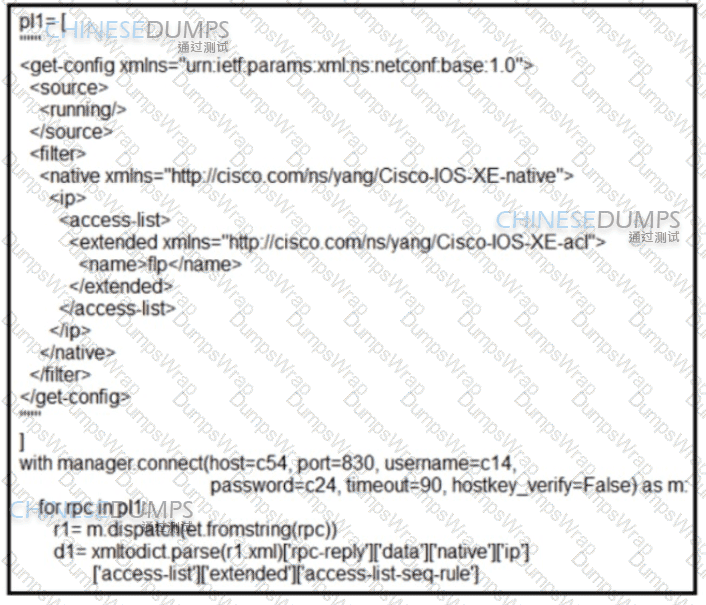
Refer to the exhibit. What is achieved by this Python script?
When does a Cisco StackWise primary switch lose its role?
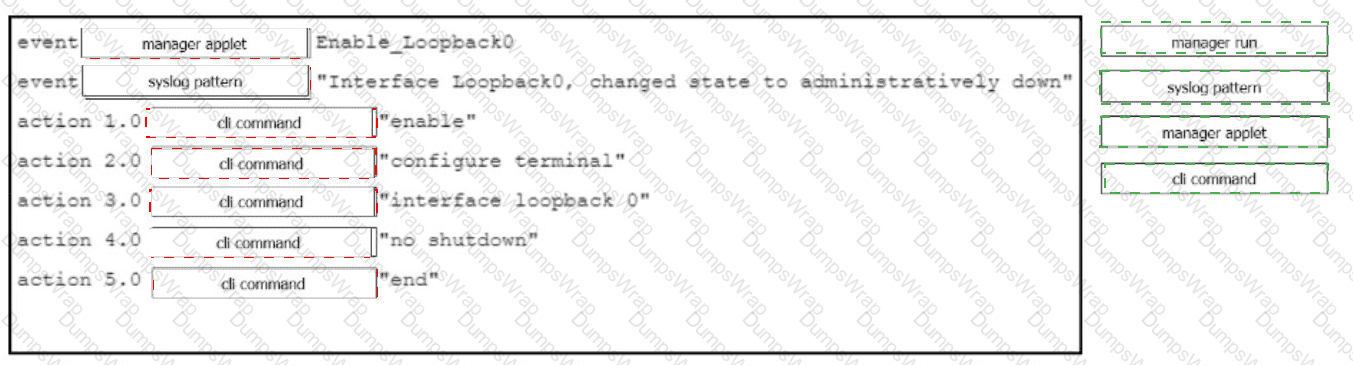
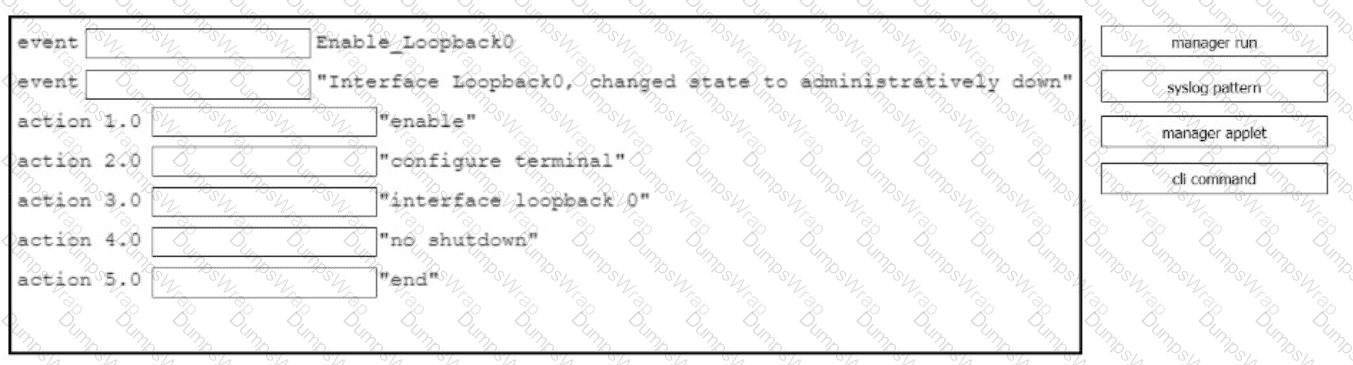
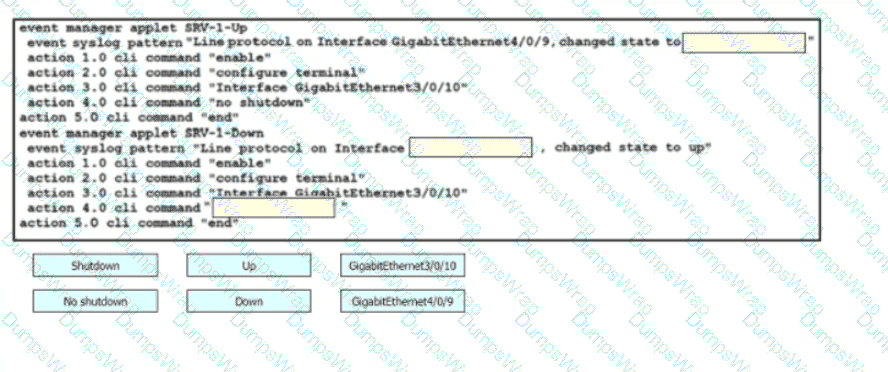
Drag and drop the command snippets from the right onto the boxes to create an EEM applet that will enable interface LoopbackO when the logging message 'Interface LoopbackO. changed state to administratively down" is received. Not all commands are used and some commands are used more than once.
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
•LocationA -72dBm
• Location B:-75 dBm
• Location C; -65 dBm
• Location D -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two.)
Which architectural component enables a zero-trust security model?
Which method is used by an AP to join HA controllers and is configured in NVRAM?
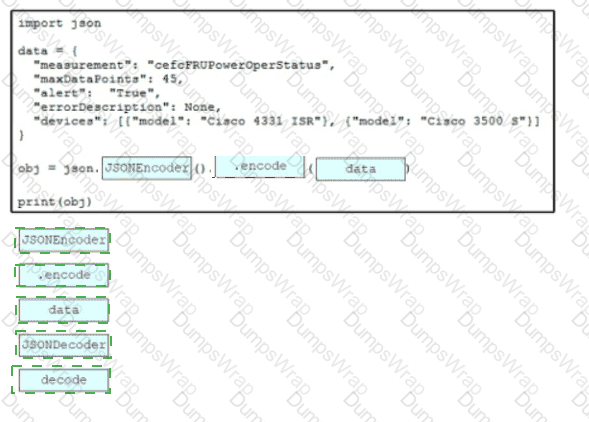
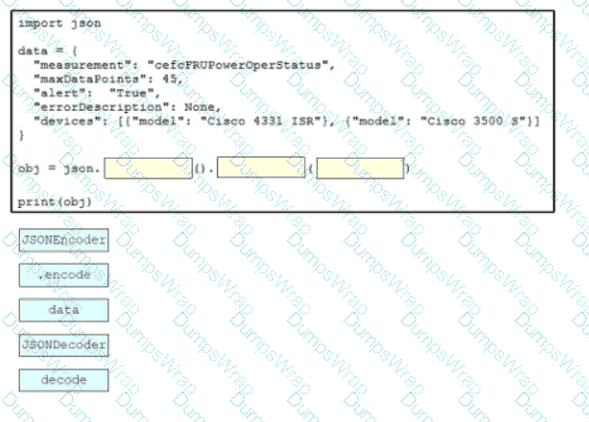
Drag and drop the code snippets from the bottom onto the blanks in the script to convert a Python object into a JSON string. Not all options are used
A wireless network engineer must configure a WPA2+WPA3 policy with the Personal security type. Which action meets this requirement?
Which protocol does Cisco Catalyst Center (formerly DNA Center) SDK use to discover the topology of non-Cisco devices in a network?
What is one advantage of using a data modeling language to develop an API client application?
What is the measure of the difference between the received signal and the noise floor in a wireless environment?
Which nodes require VXLAN encapsulation support In a Cisco SD-Access deployment?
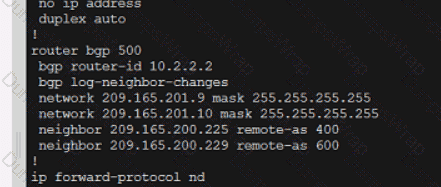
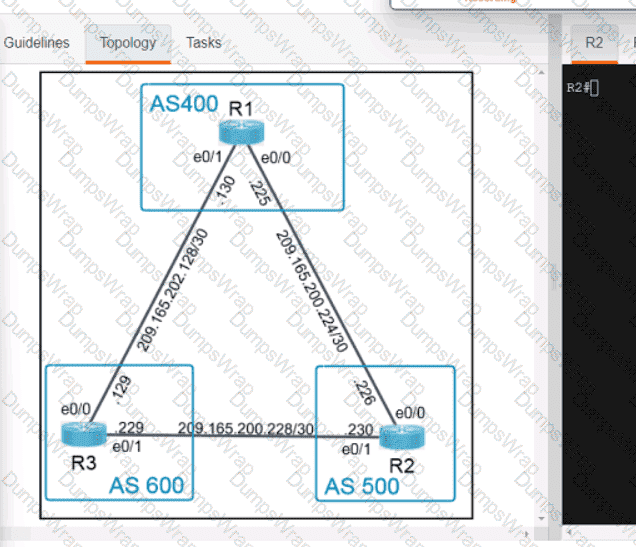
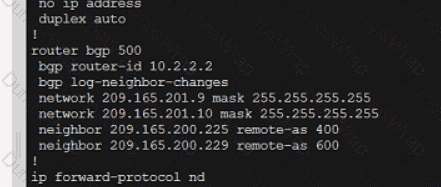
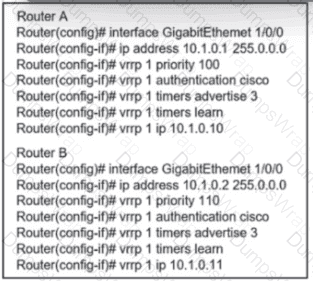
Refer to the exhibit. An engineer must adjust the configuration so that Router A becomes the active router. Which commands should be applied to router A? (Choose two)
Which device is responsible for finding EID-to-RLOC mappings when traffic is sent to a LISP-capable site?
What is a TLOC in a Cisco SD-WAN deployment?
What is one primary REST security design principle?
A network administrator is preparing a Python script to configure a Cisco IOS XE-based device on the network. The administrator is worried that colleagues will make changes to the device while the script is running. Which operation of the NC client manager prevents colleagues from making changes to the devices while the script is running?
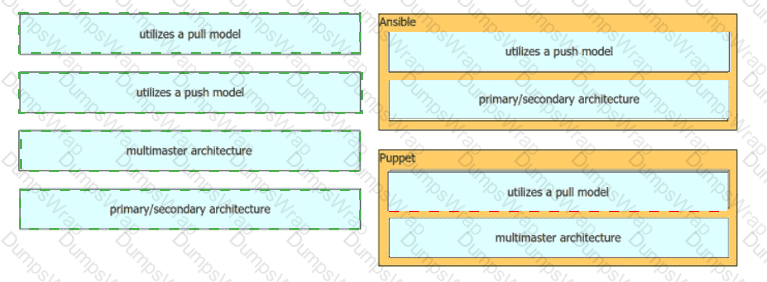
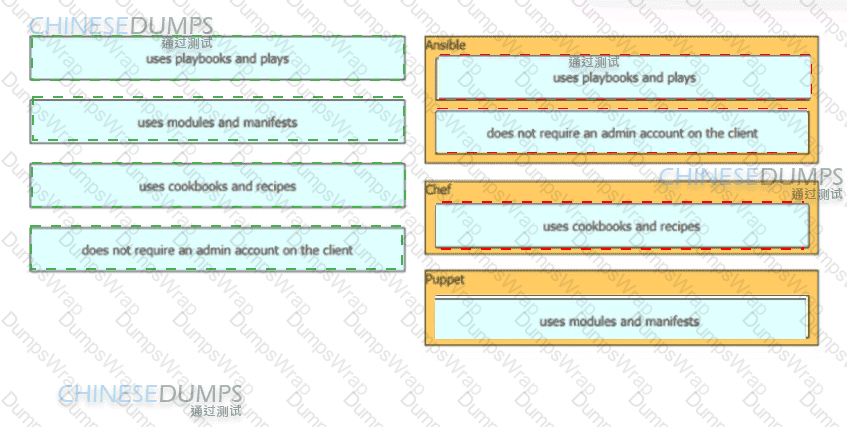
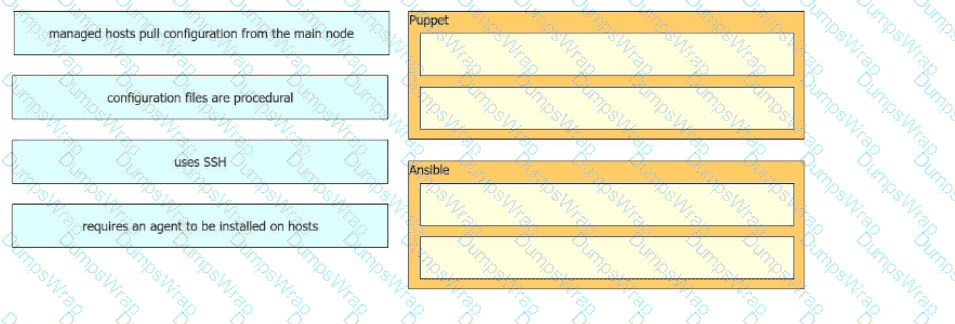
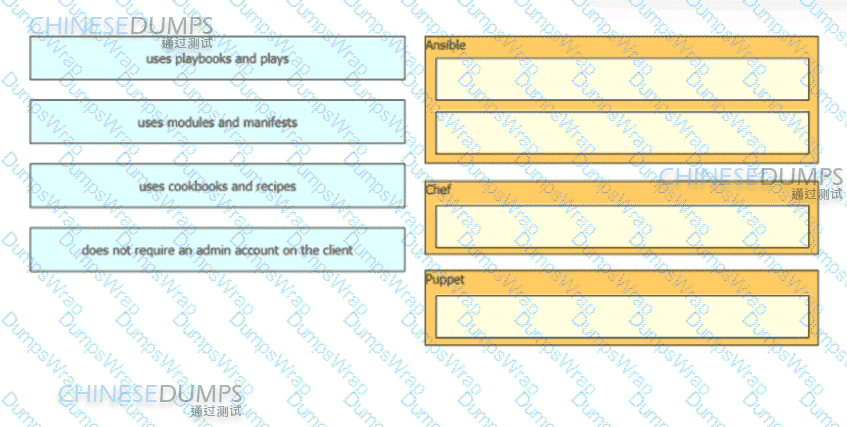
Drag and drop the characteristics from the left onto the corresponding orchestration tool on the right.

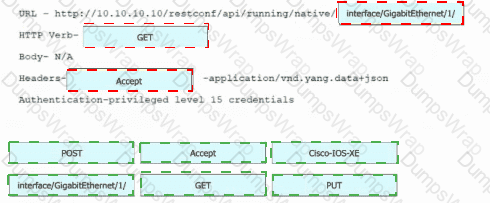
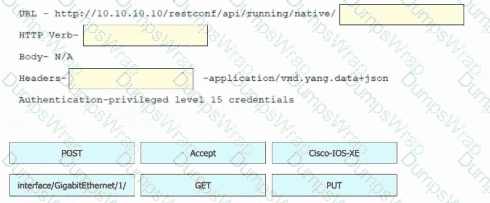
Refer to the exhibit. Drag and drop the snippets into the RESTCONF request to form the request that returns this response. Not all options are used.
A customer wants to use a single SSID to authenticate loT devices using different passwords. Which Layer 2 security type must be configured in conjunction with Cisco ISE to achieve this requirement?
What is required for a VXLAN tunnel endpoint to operate?
Which action reduces sticky clients in dense RF environments?
What is the recommended minimum SNR for data applications on wireless networks?
Which tag defines the properties to be applied to each specific WLAN?
What is an advantage of utilizing data models in a multivendor environment?
Which A record type should be configured for access points to resolve the IP address of a wireless LAN controller using DNS?
In a Cisco SD-Access network architecture, which access layer cabling design is optimal for the underlay network?
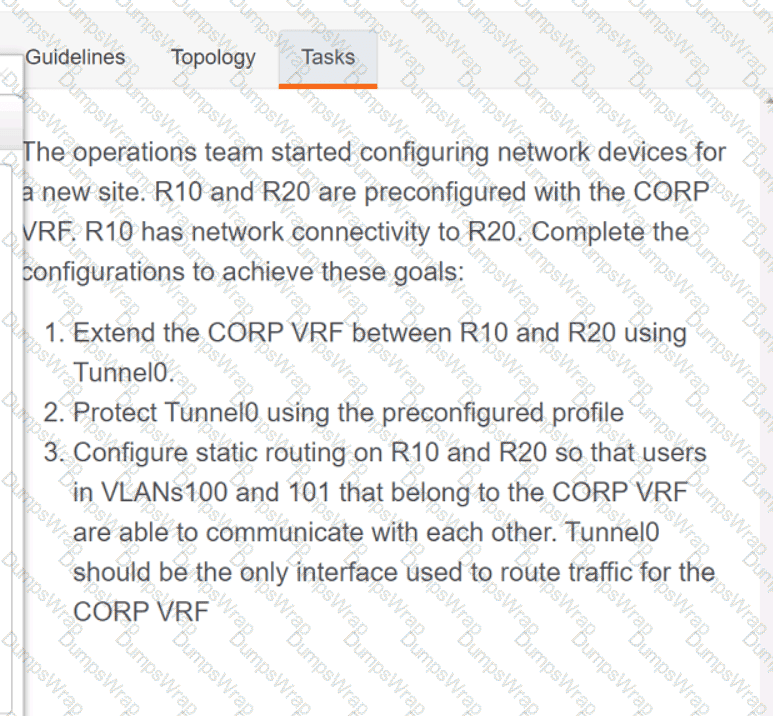
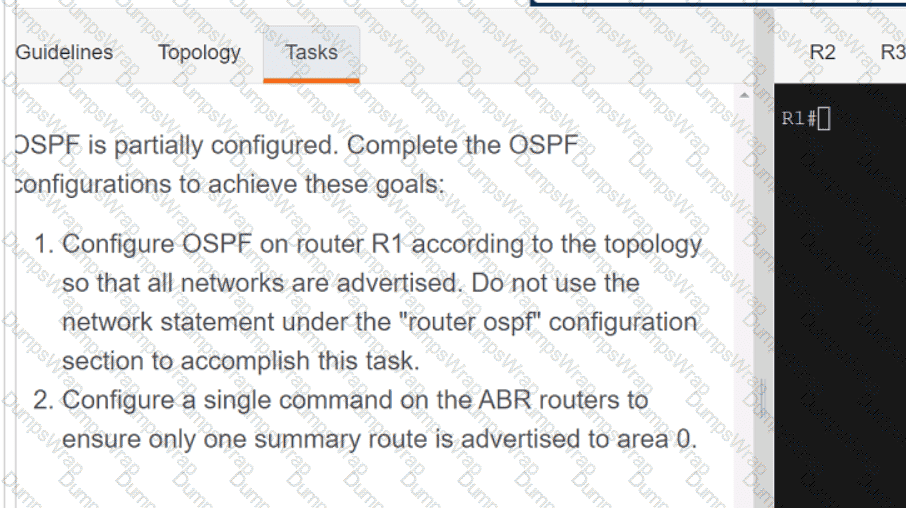
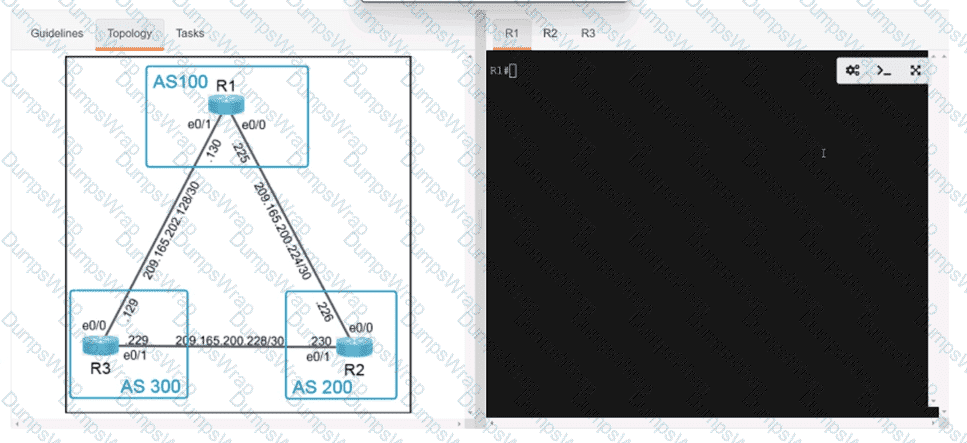
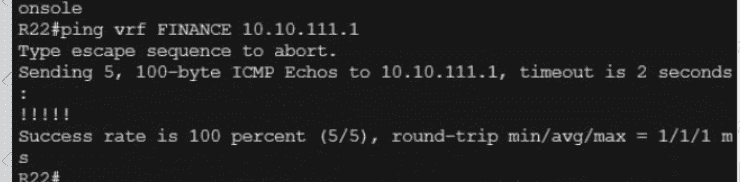
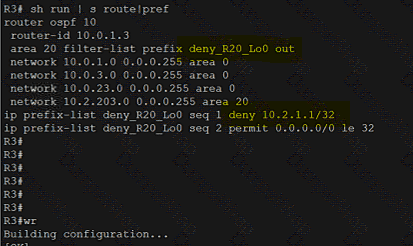
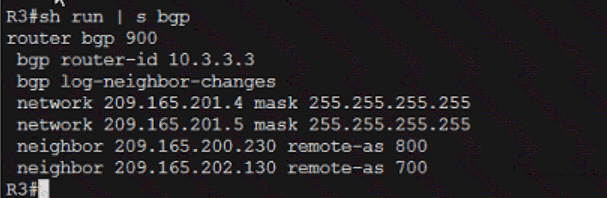
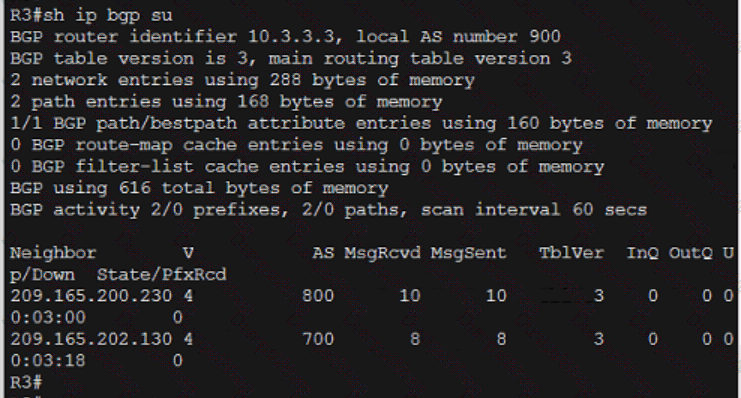
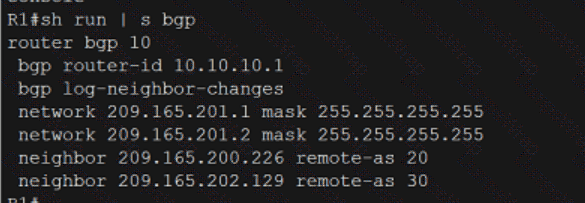
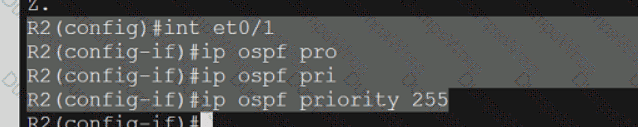
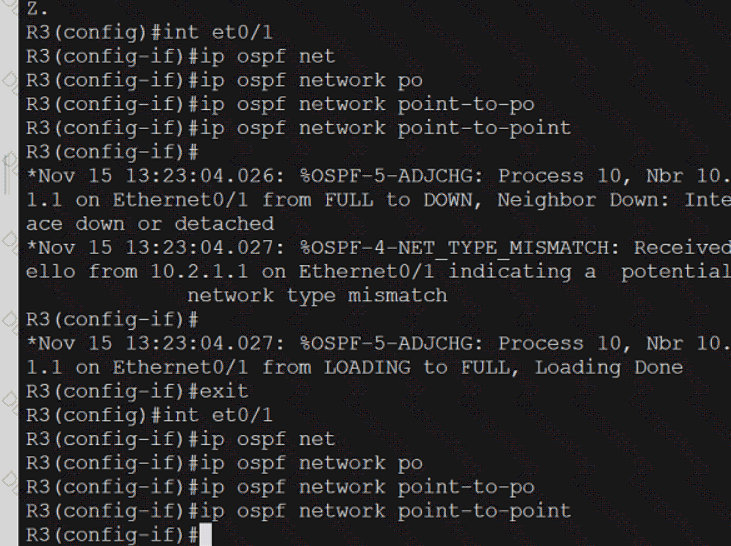
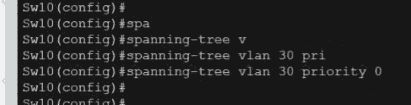
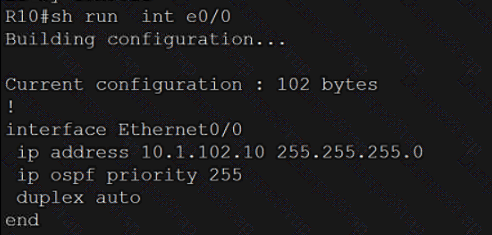
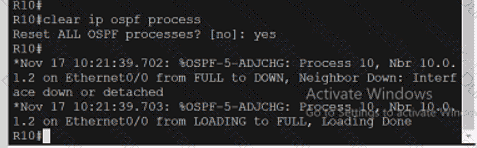
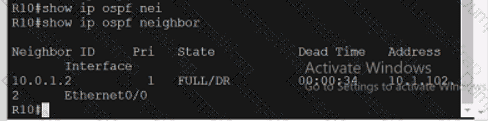
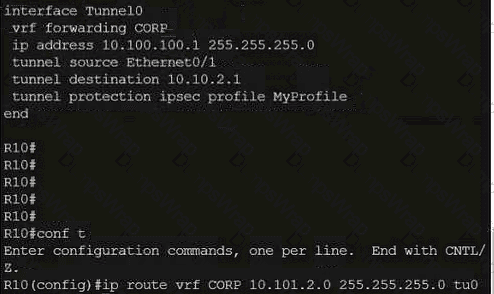
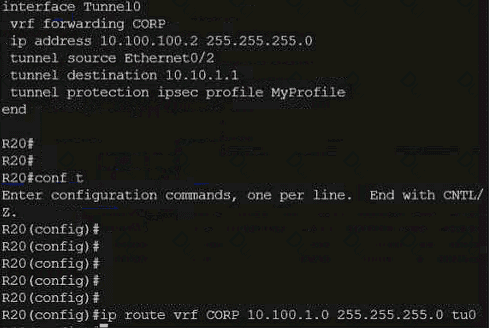
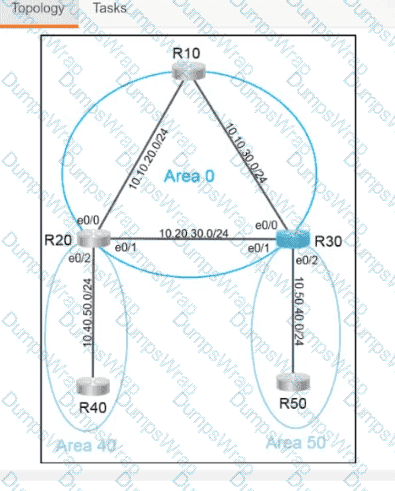
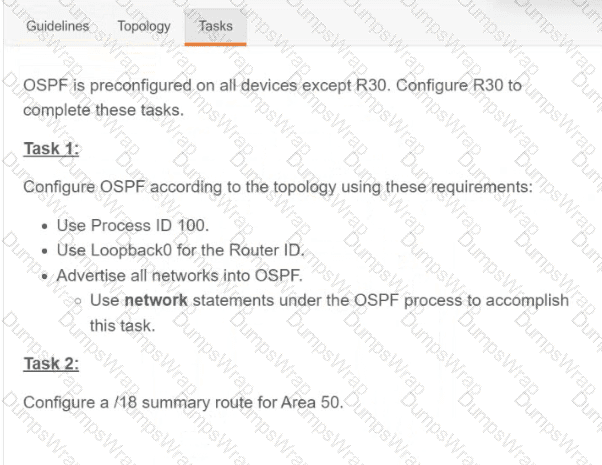
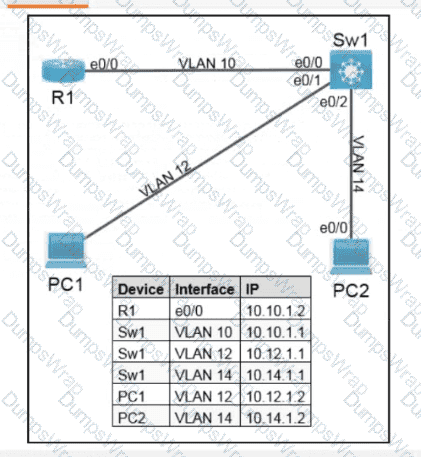
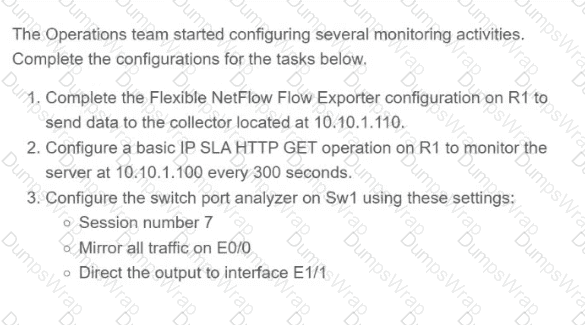
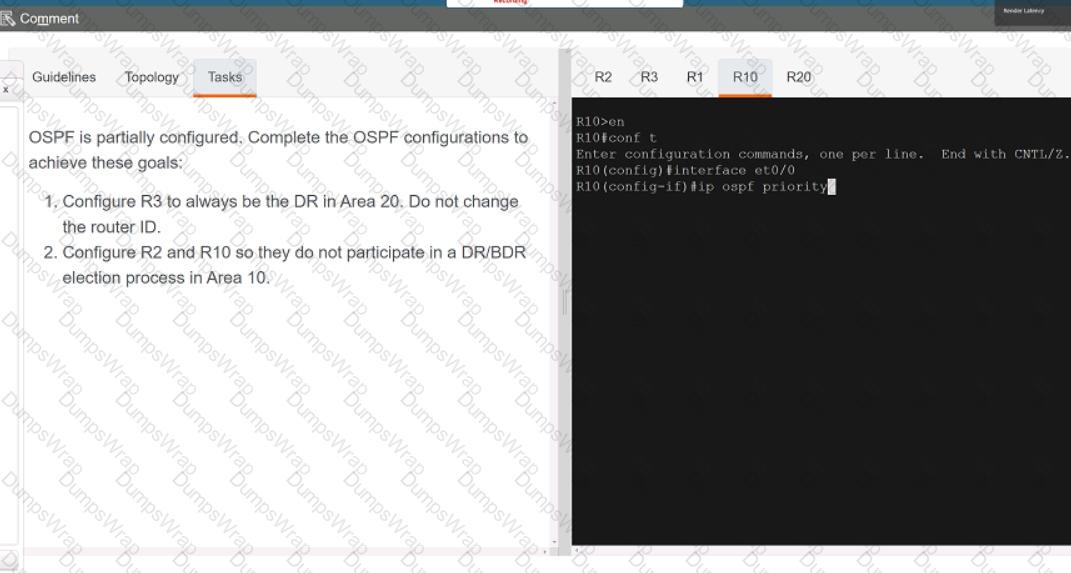
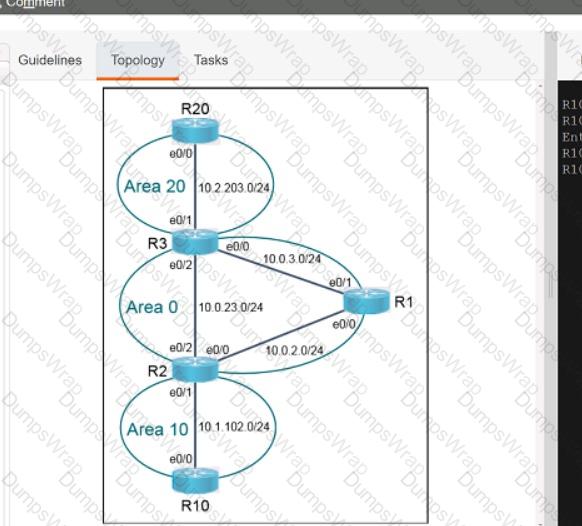
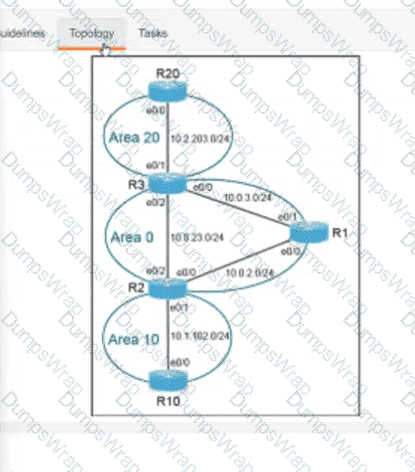
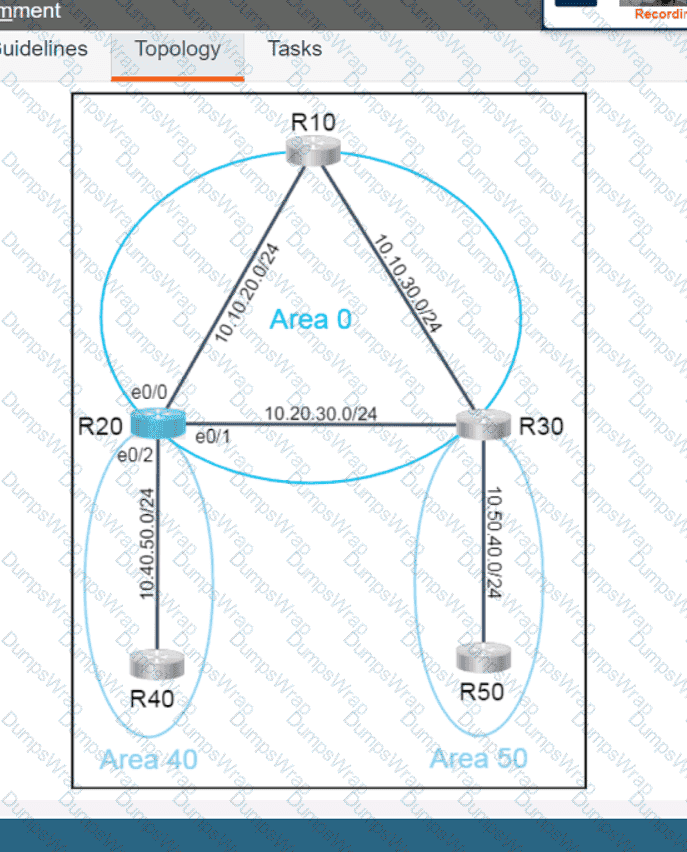
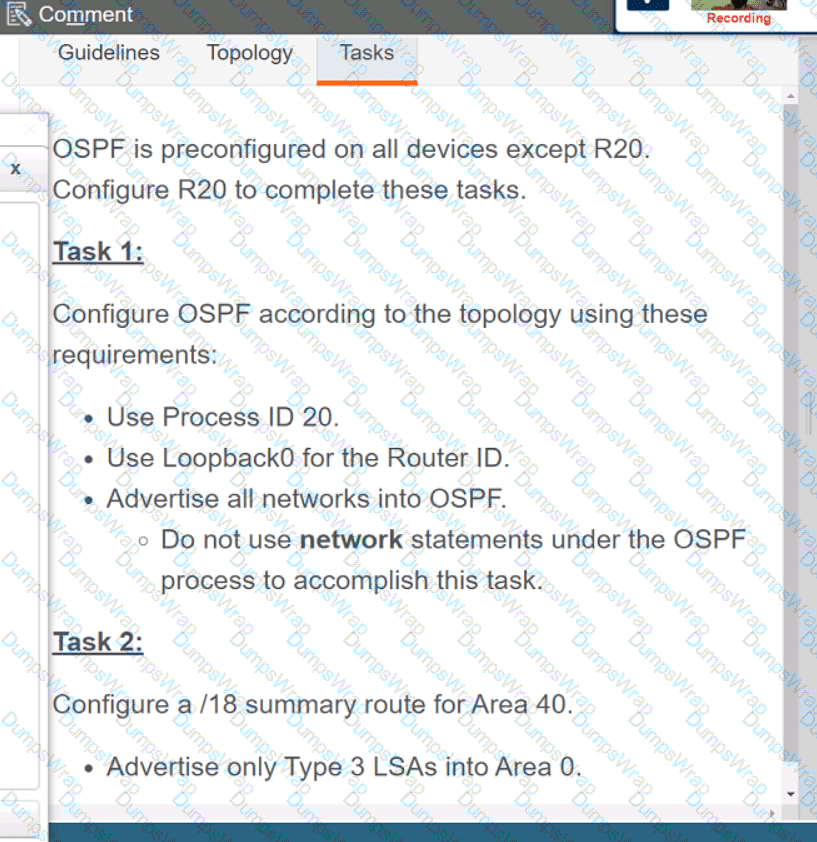
Refer to the exhibit.

Which EEM script generates a critical-level syslog message and saves a copy of the running configuration to the bootflash when an administrator saves the running configuration to the startup configuration?

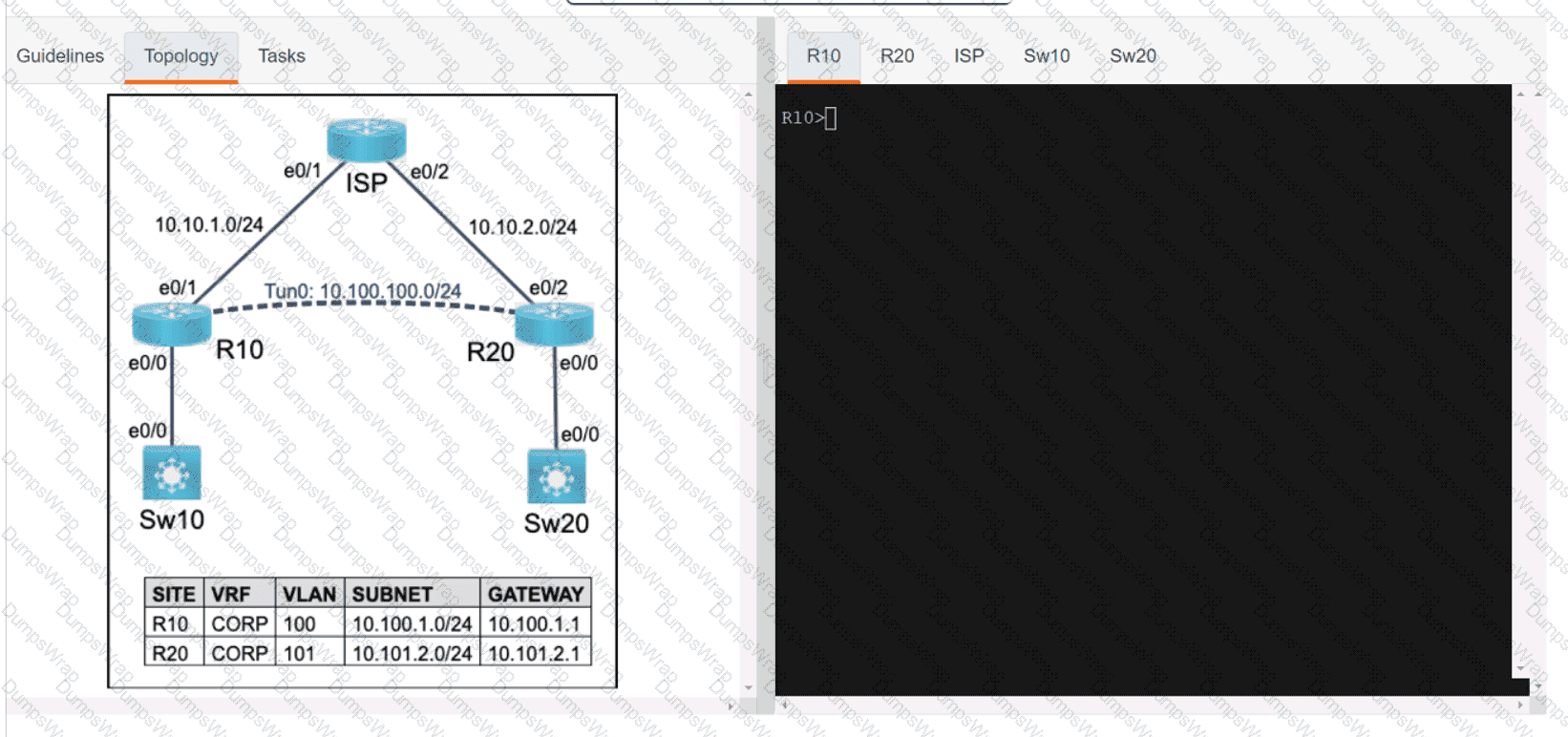
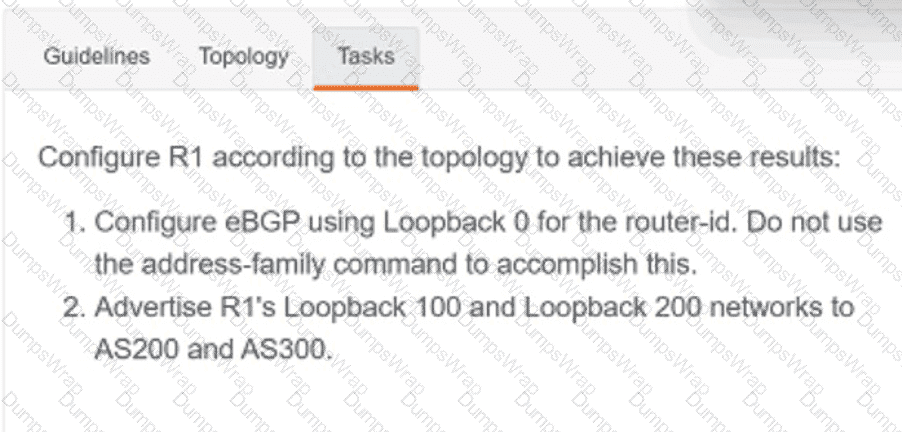
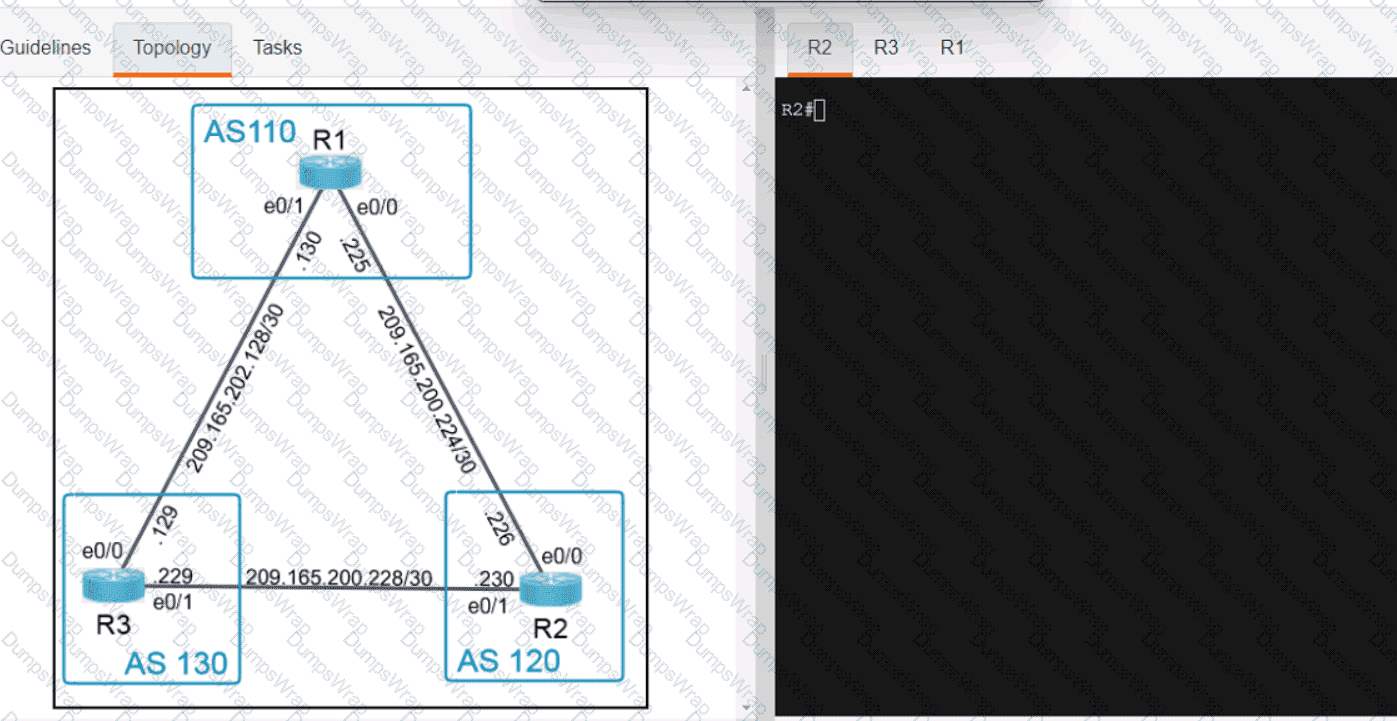
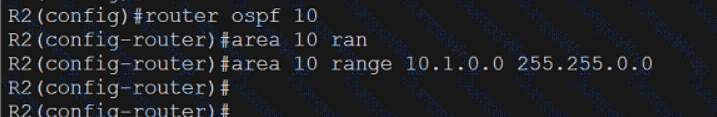
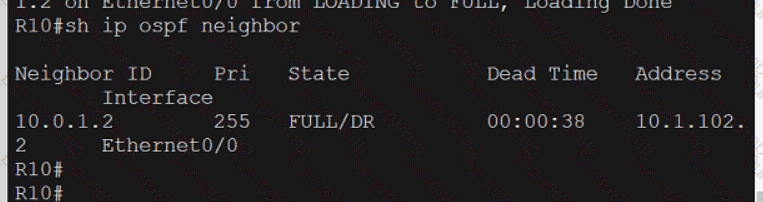
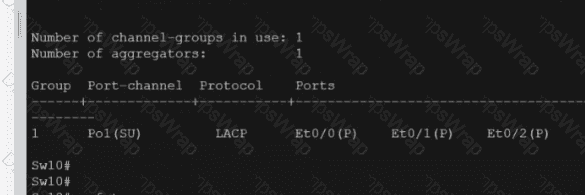
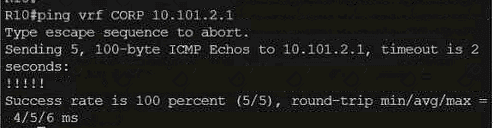
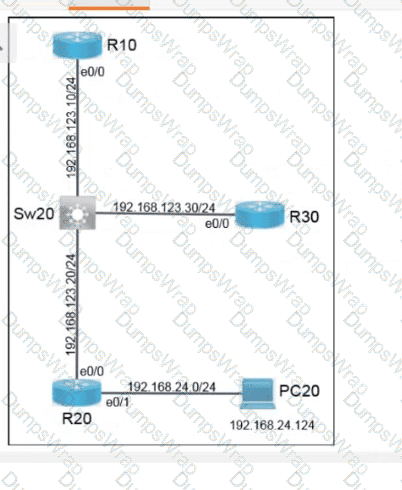
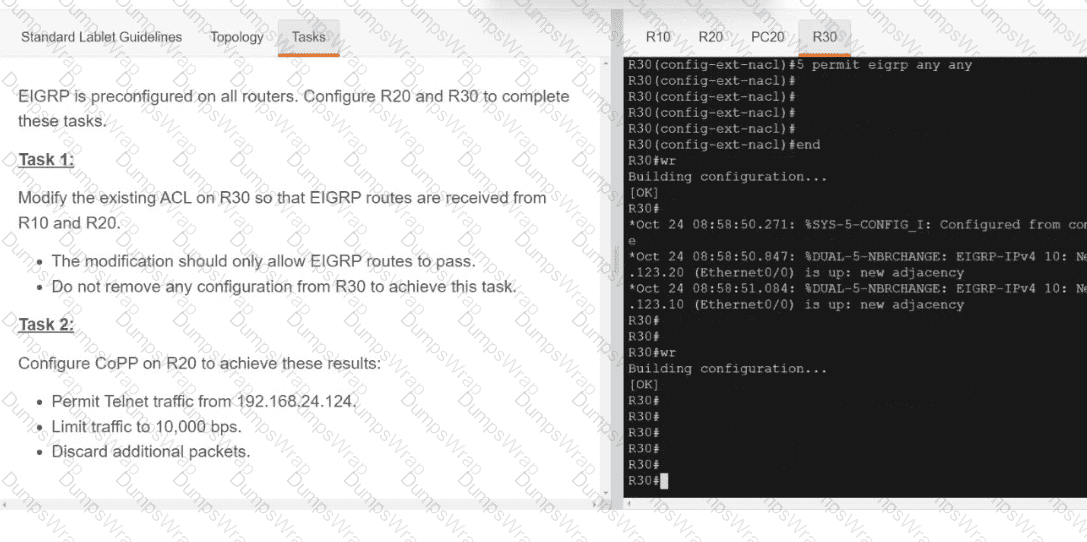
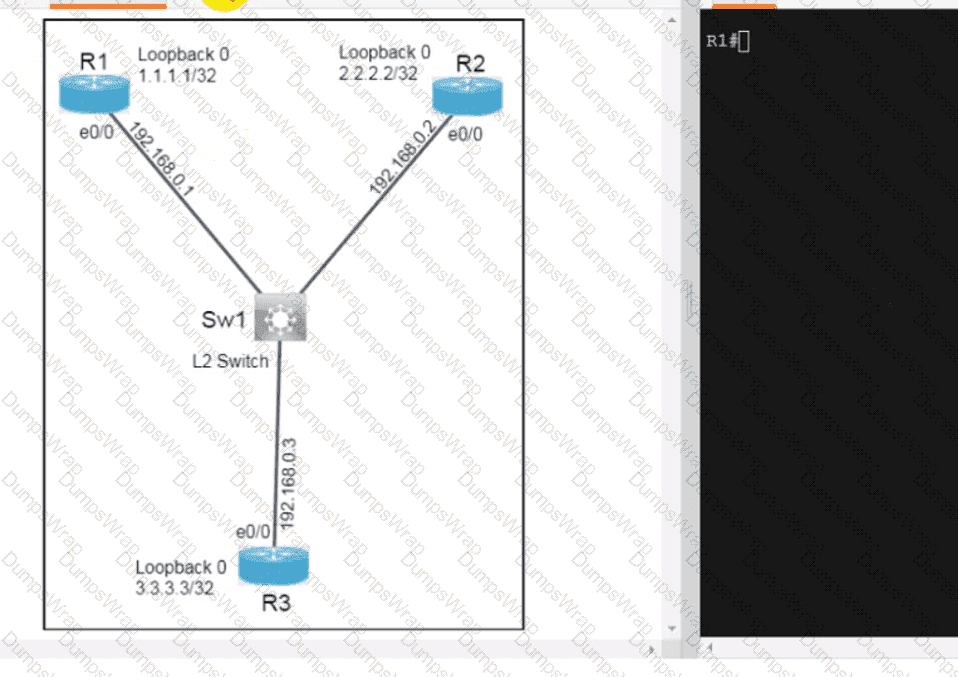
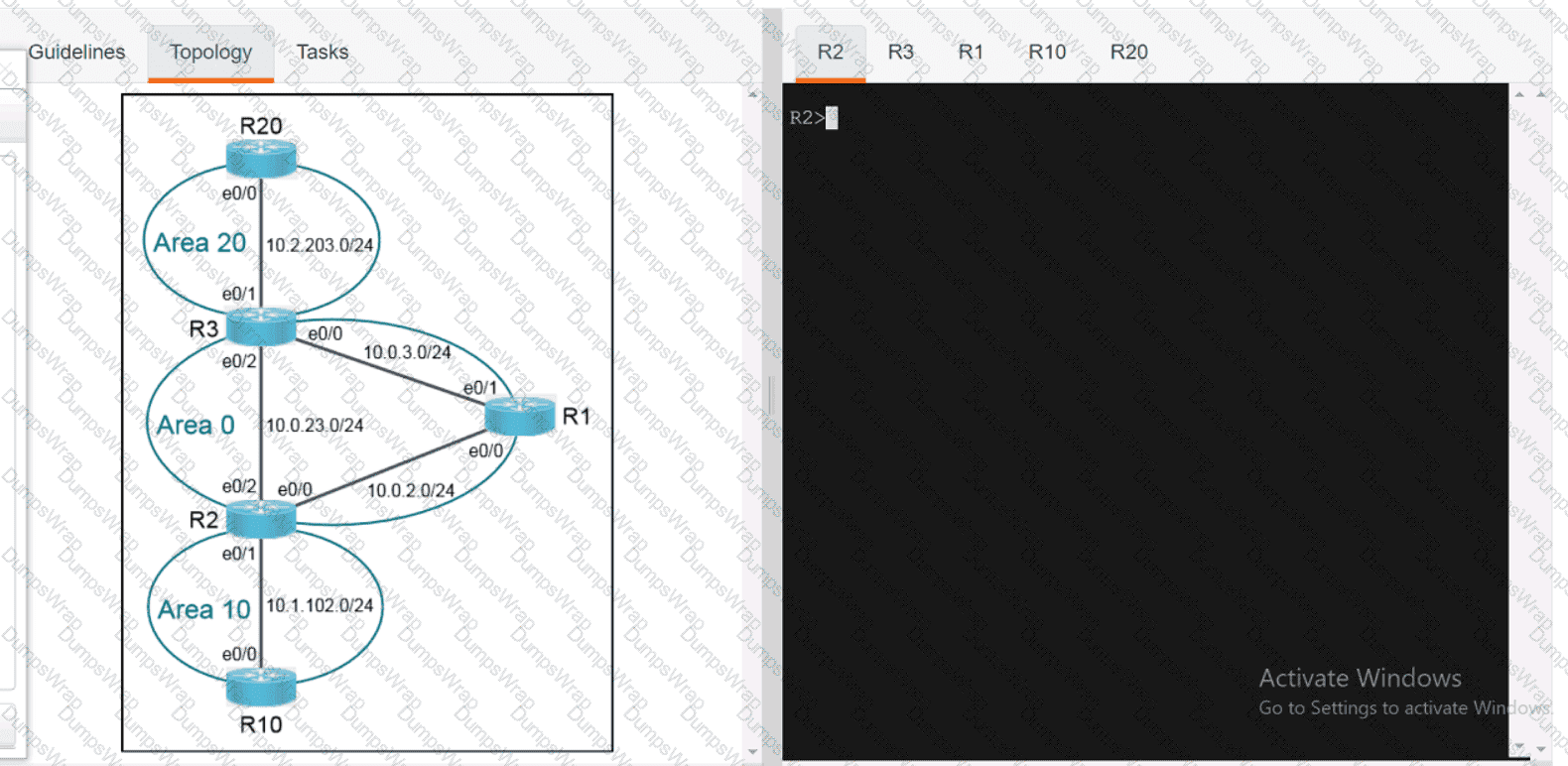
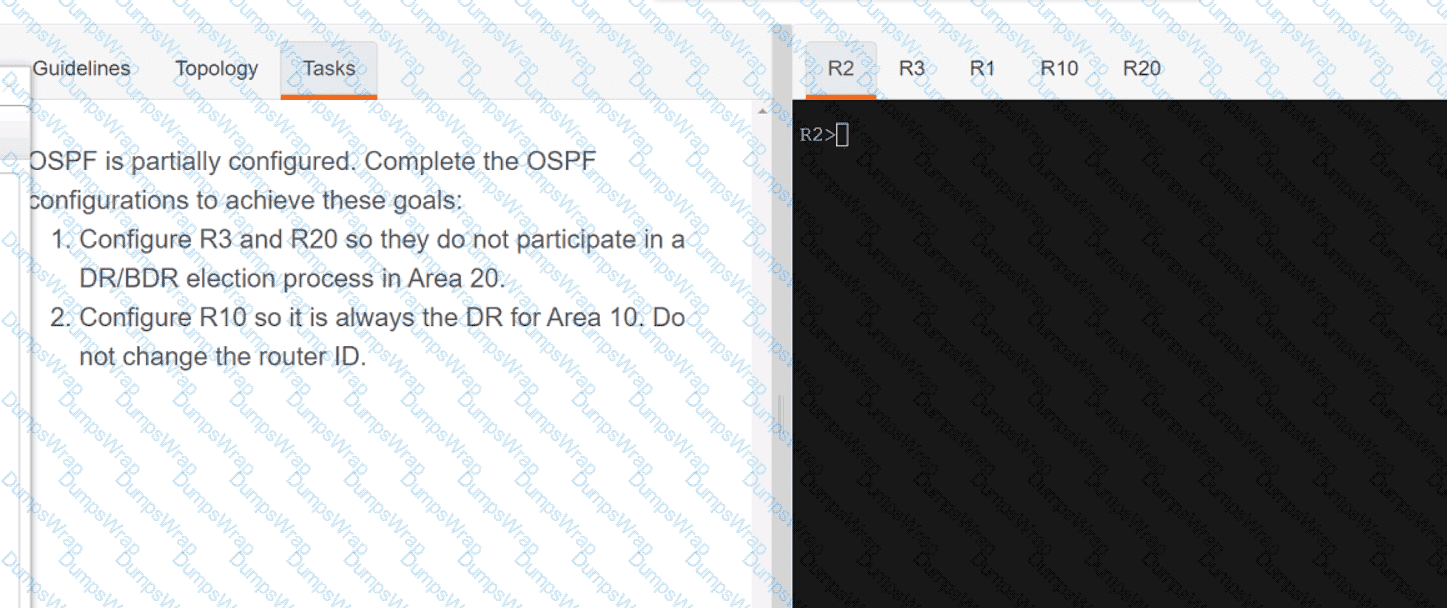
Refer to the exhibit.

Which JSON syntax is derived from this data?

Which mobility role is assigned to a client in the client table of the new controller after a Layer 3 roam?
Which two mechanisms are used with OAuth 2.0 for enhanced validation? (Choose two.)
What are two best practices when designing a campus Layer 3 infrastructure? (Choose two.)
Which feature provides data-plane security for Cisco Catalyst SD-WAN networks'?
Which solution should be used in a high-density wireless environment to increase bandwidth for each user?
Which definition describes JWT in regard to REST API security?
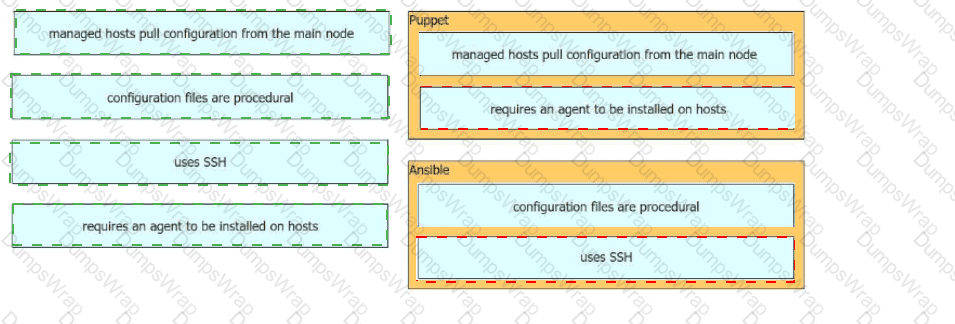
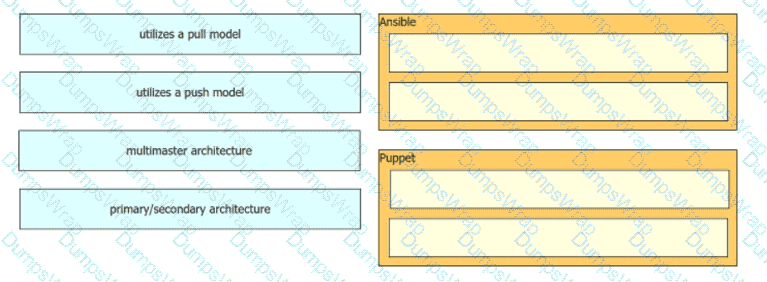
Drag and drop the characteristics from the left onto the orchestration tools they describe on the right.
What does a YANG model provide?
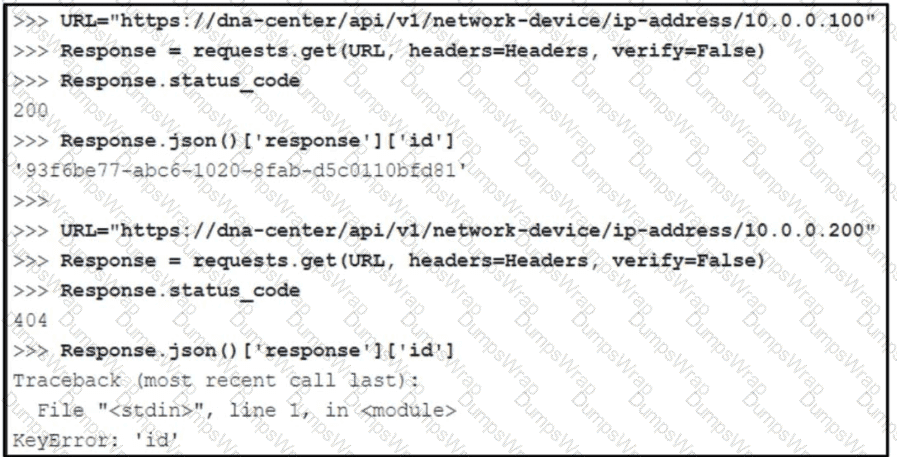
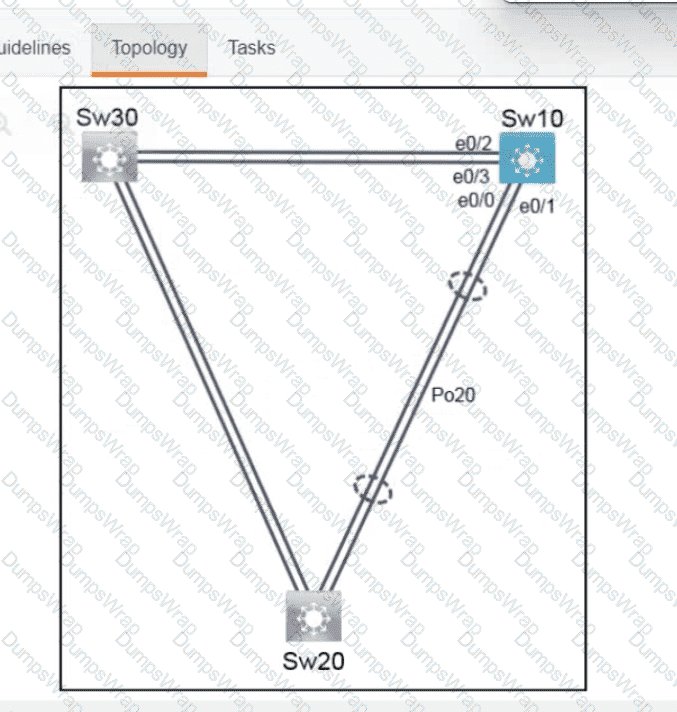
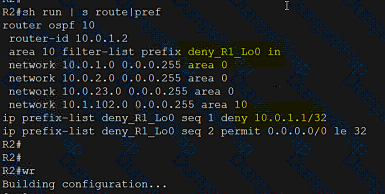
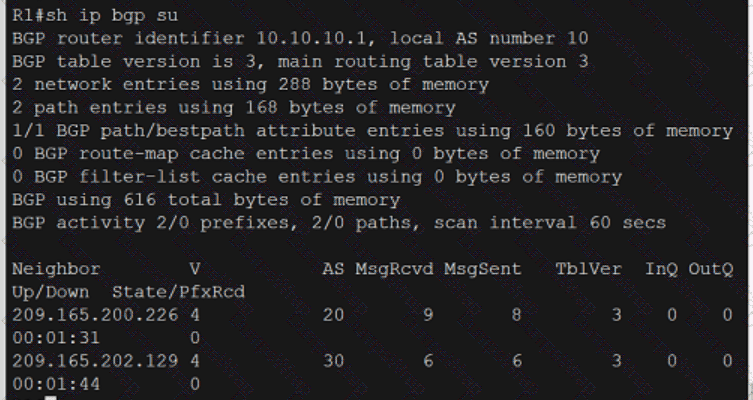
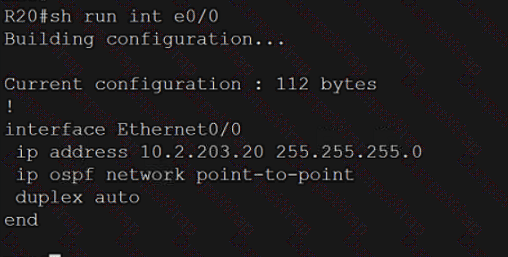
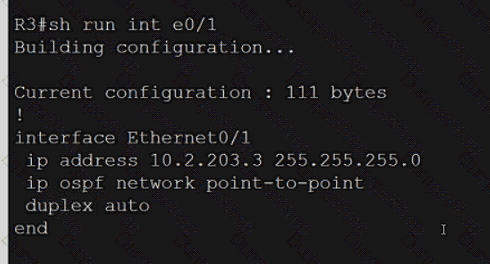
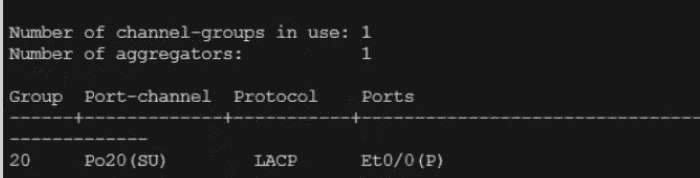
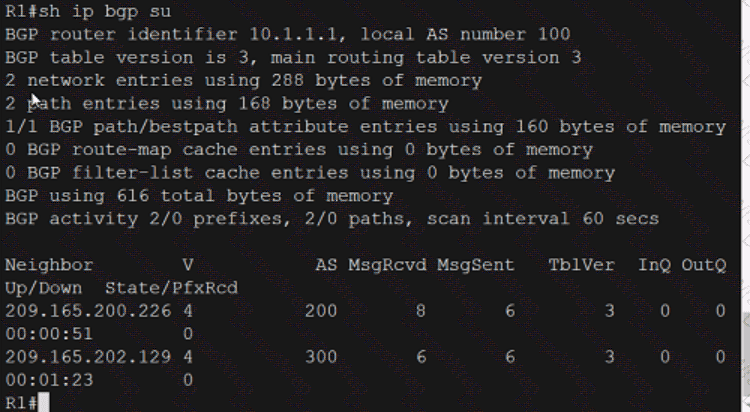
Refer to the exhibit. What is determined from the output?
What is the structure of a JSON web token?

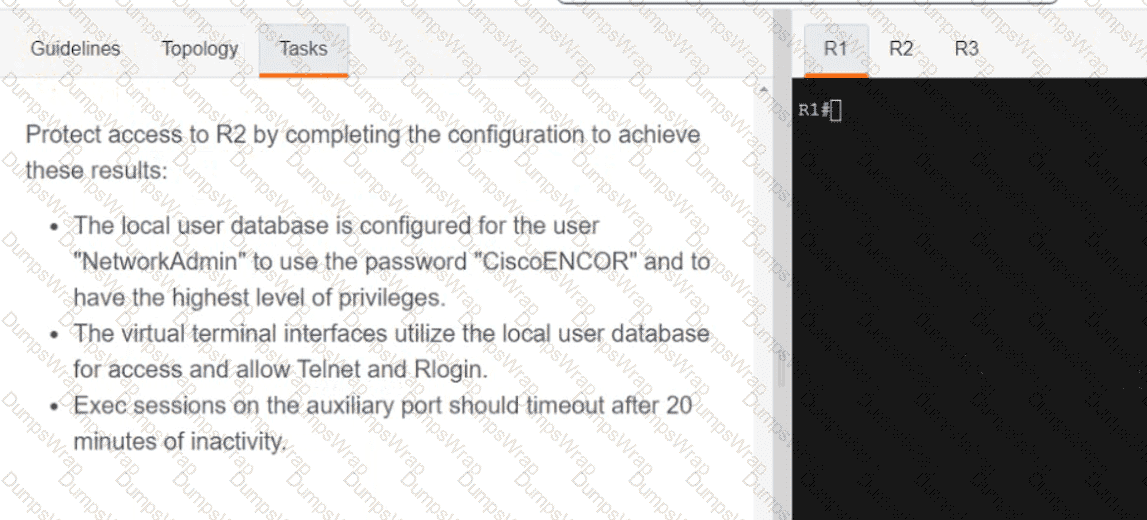
Refer to the exhibit. The existing configuration must be updated to terminate all EXEC sessions after 120 minutes. Which command set should be applied?
Drag and drop the automation characteristics from the left to the corresponding tools on the right.
Which framework is used for third-party authorization?
In a Cisco SD-Access wireless architecture, which device manages endpoint ID to edge node bindings?
Which type of API enables Cisco Catalyst Center (formerly DNA Center) to focus on outcome instead of the individual steps that are required to achieve the outcome?
What is the calculation that is used to measure the radiated power of a signal after it has gone through the radio, antenna cable, and antenna?
Drag and drop the snippets onto the blanks within the code to construct a script that brings up the failover Ethernet port if the primary port goes down and also shuts down the failover port when the primary returns to service. Not all options are used.
Which tag defines the roaming domain and properties of an AP deployment?
An engineer must configure a new WLAN that supports 802.11r and requires users to enter a passphrase. What must be configured to support this requirement?
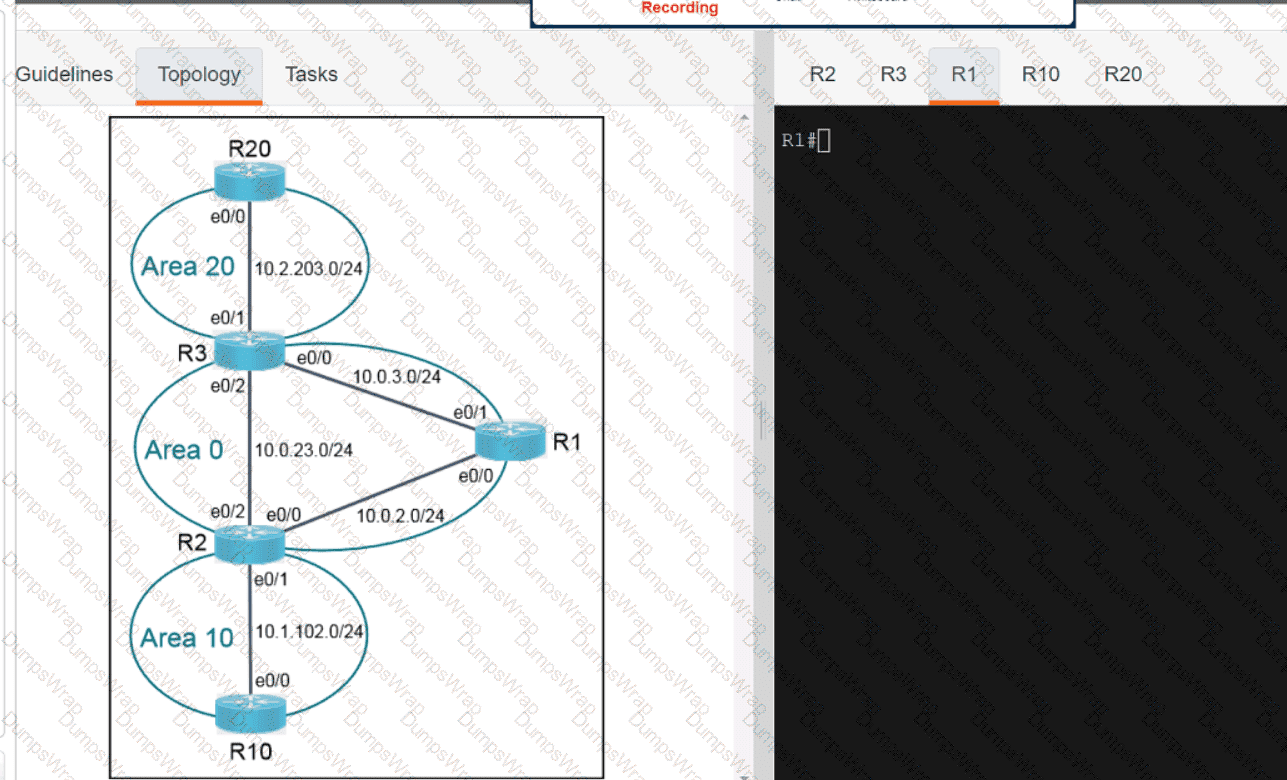
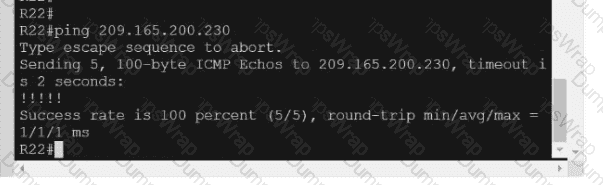
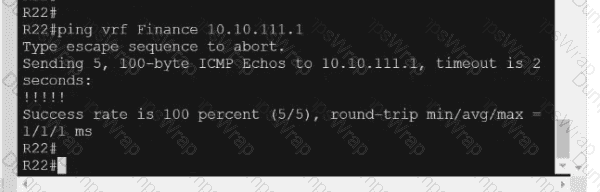
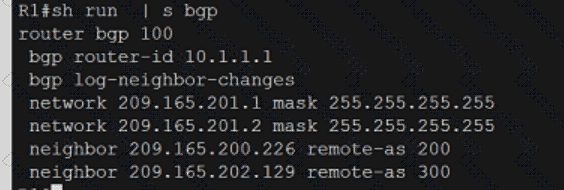
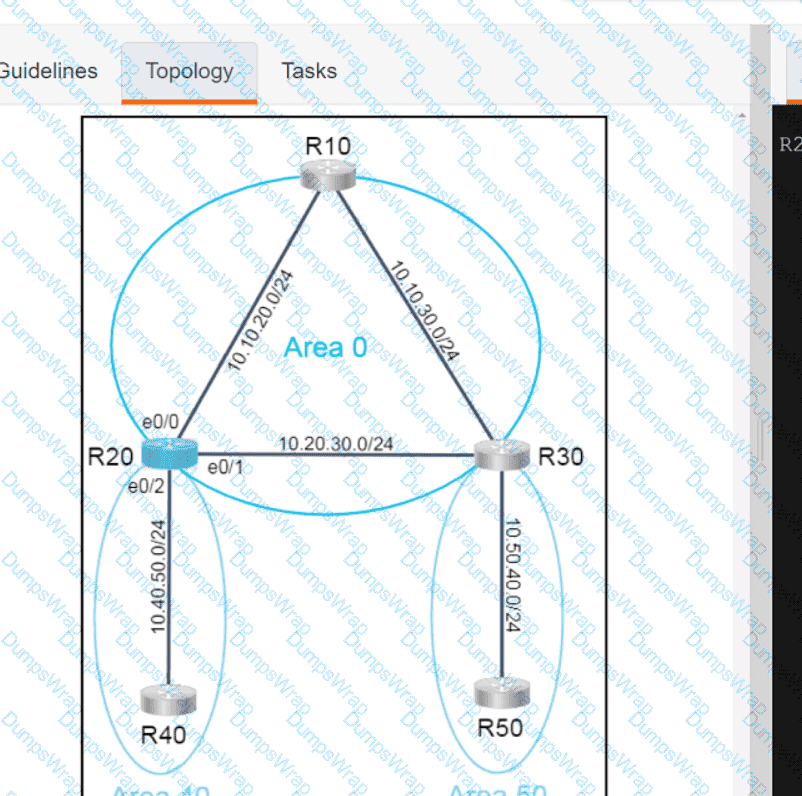
Refer to the exhibit.
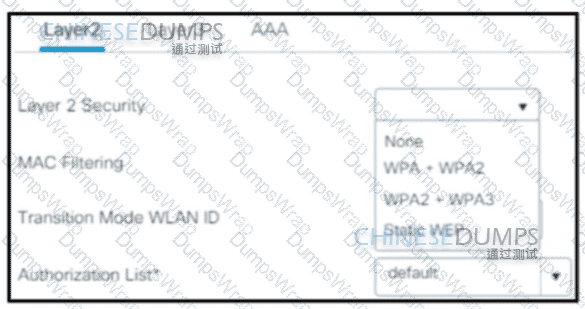
A client requests a new SSID that will use web-based authentication and external RADIUS servers. Which Layer 2 security mode must be selected?
Which technology collects location information through data packets received by the APs instead of using mobile device probes?
An engineer is implementing a new SSID on a Cisco Catalyst 9800 Series WLC that must be broadcast on 6 GHz radios. Users will be required to use EAP-TLS to authenticate. Which wireless Layer 2 security method is required?
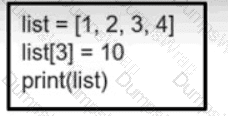
Refer to the exhibit. What is the value of the variable list after the code is run?
What are two benefits of virtualizing the server with the use of VMs in a data center environment? (Choose two.)
Which DNS record type is needed to allow a Cisco AP to discover a WLC when using IPv4?
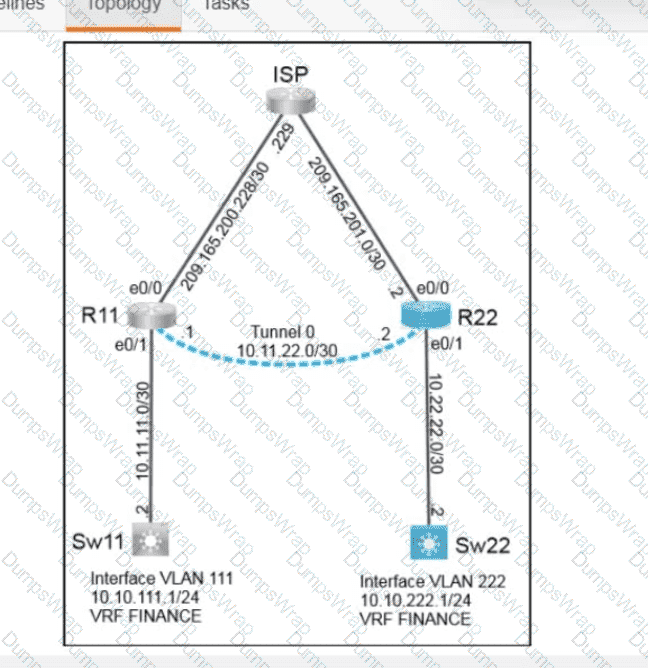
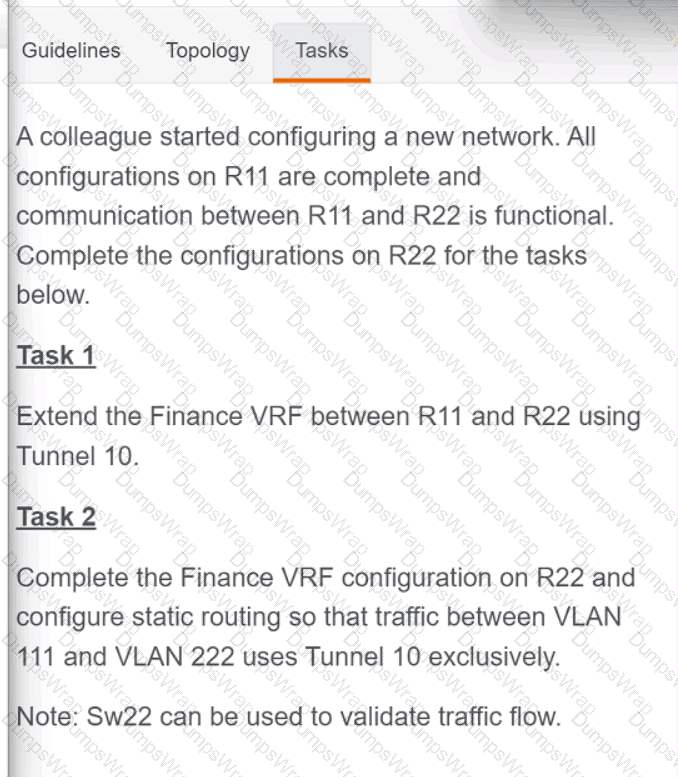
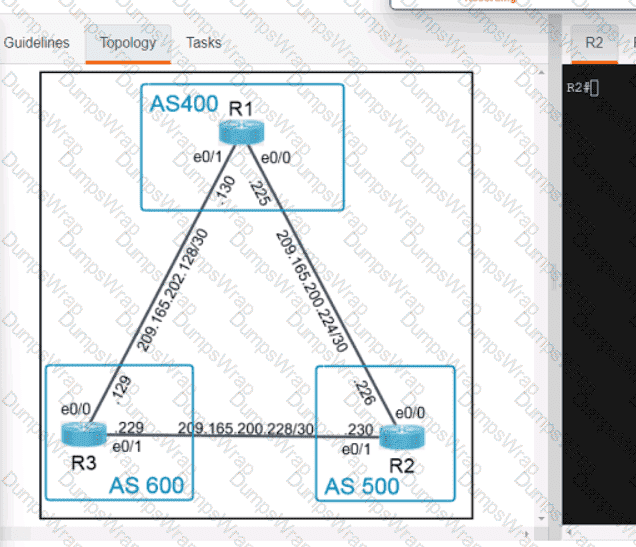
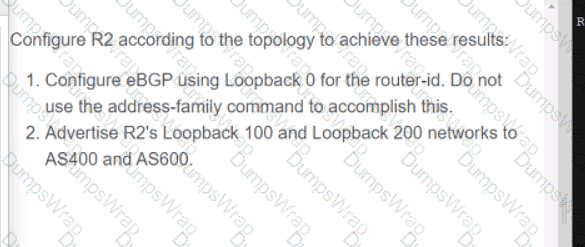
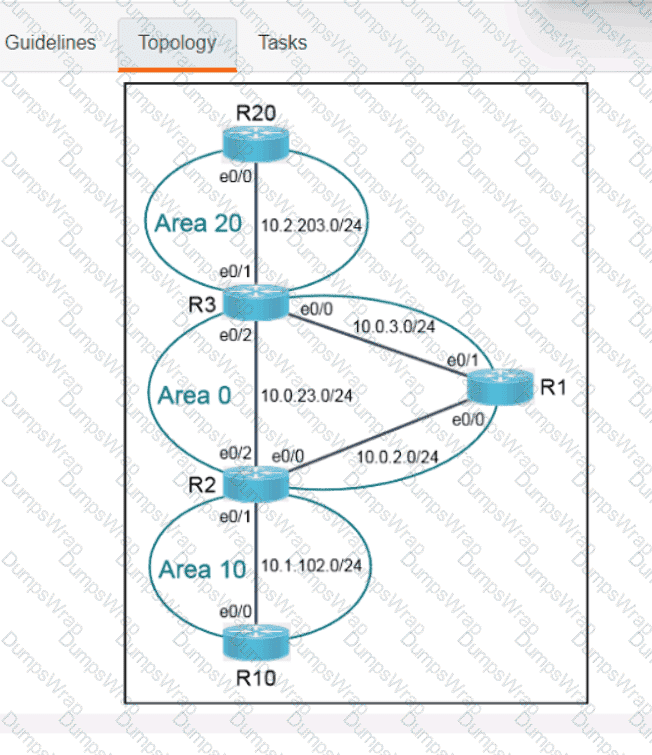

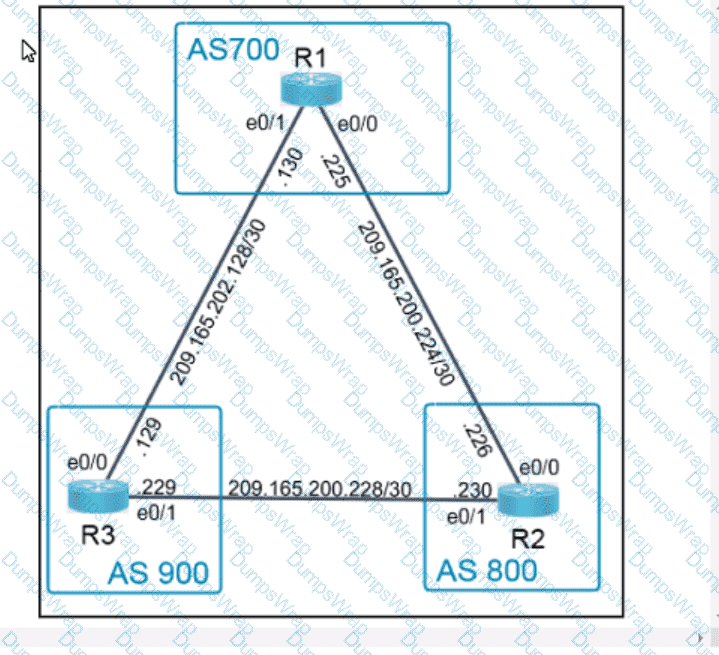
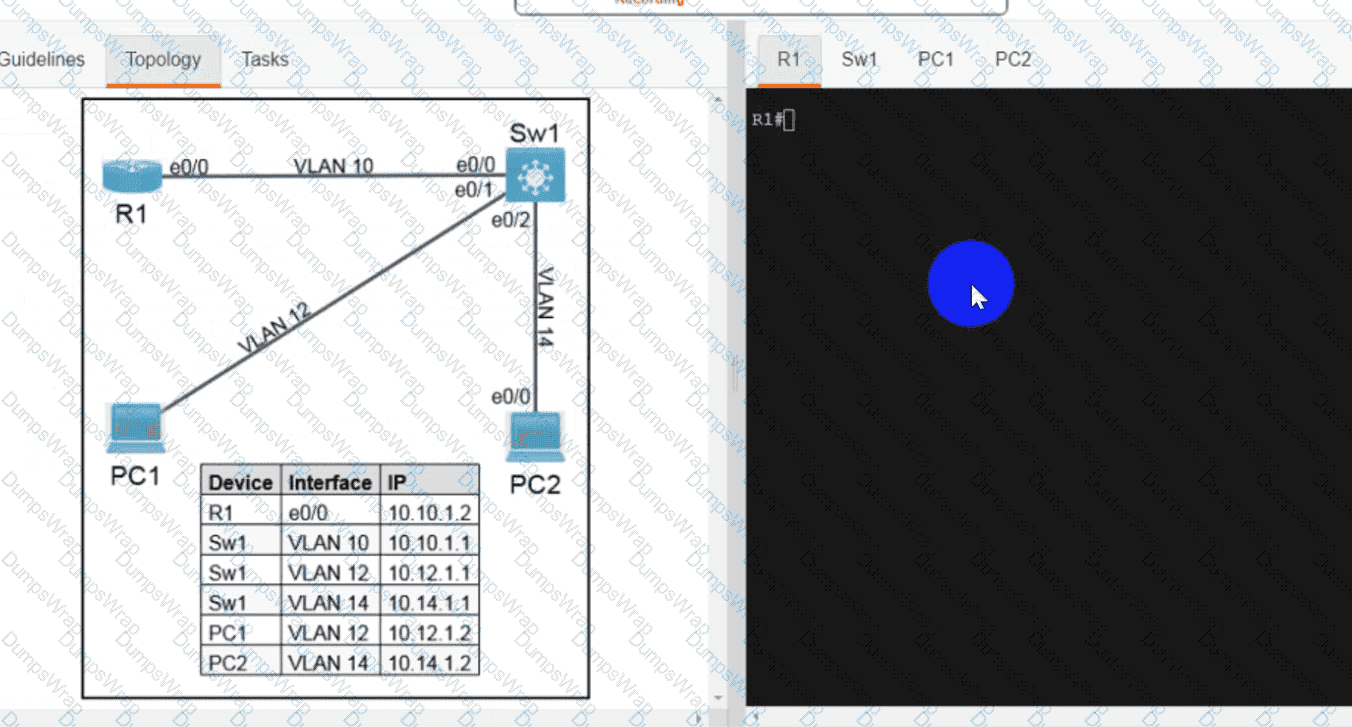
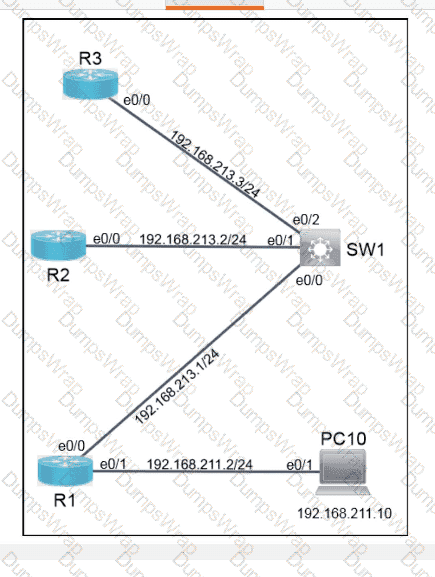
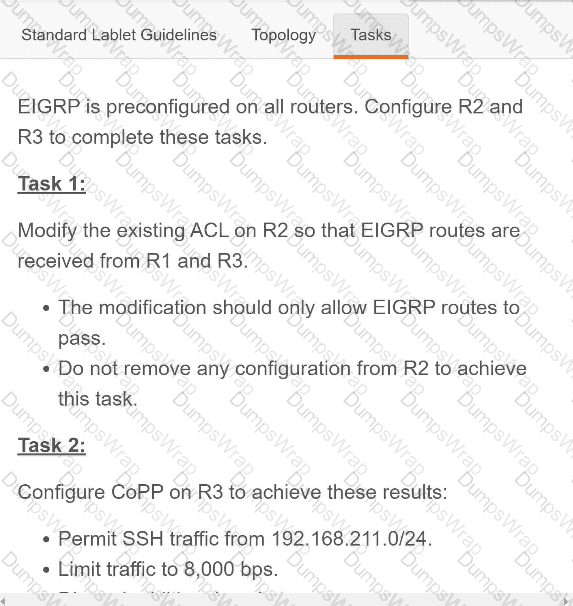
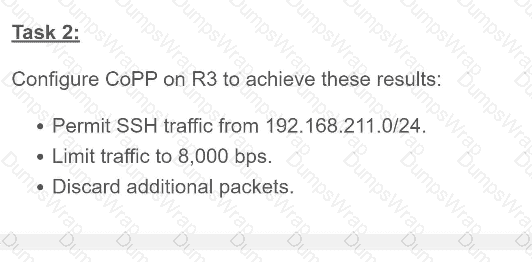
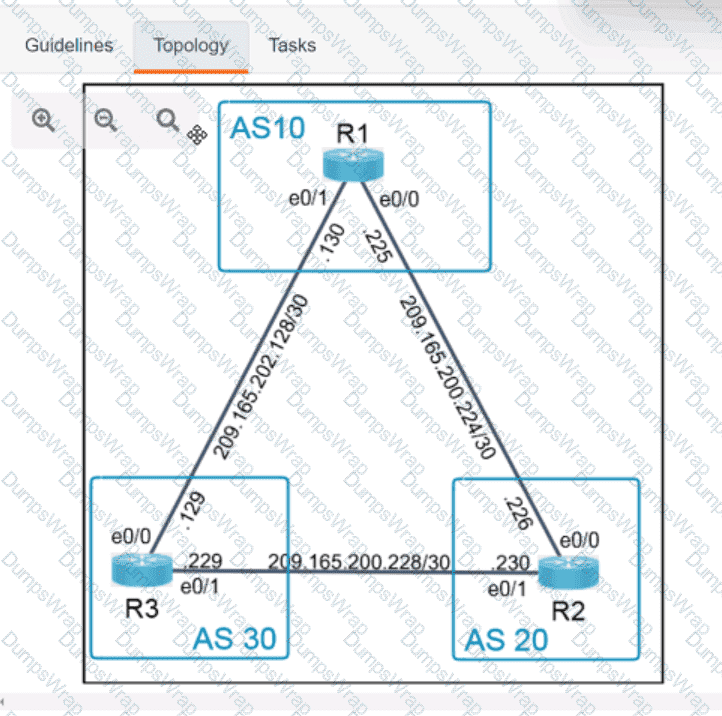
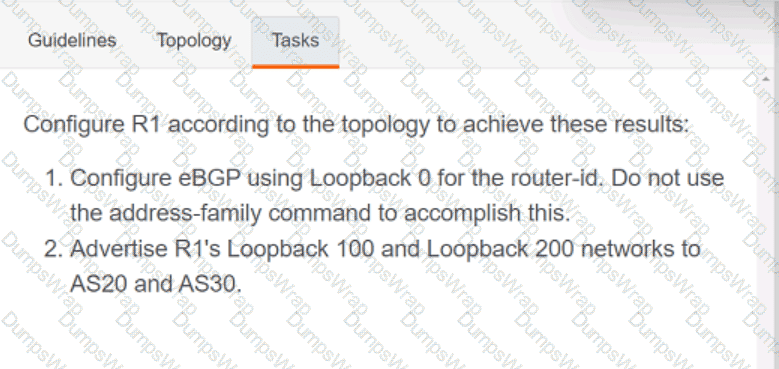
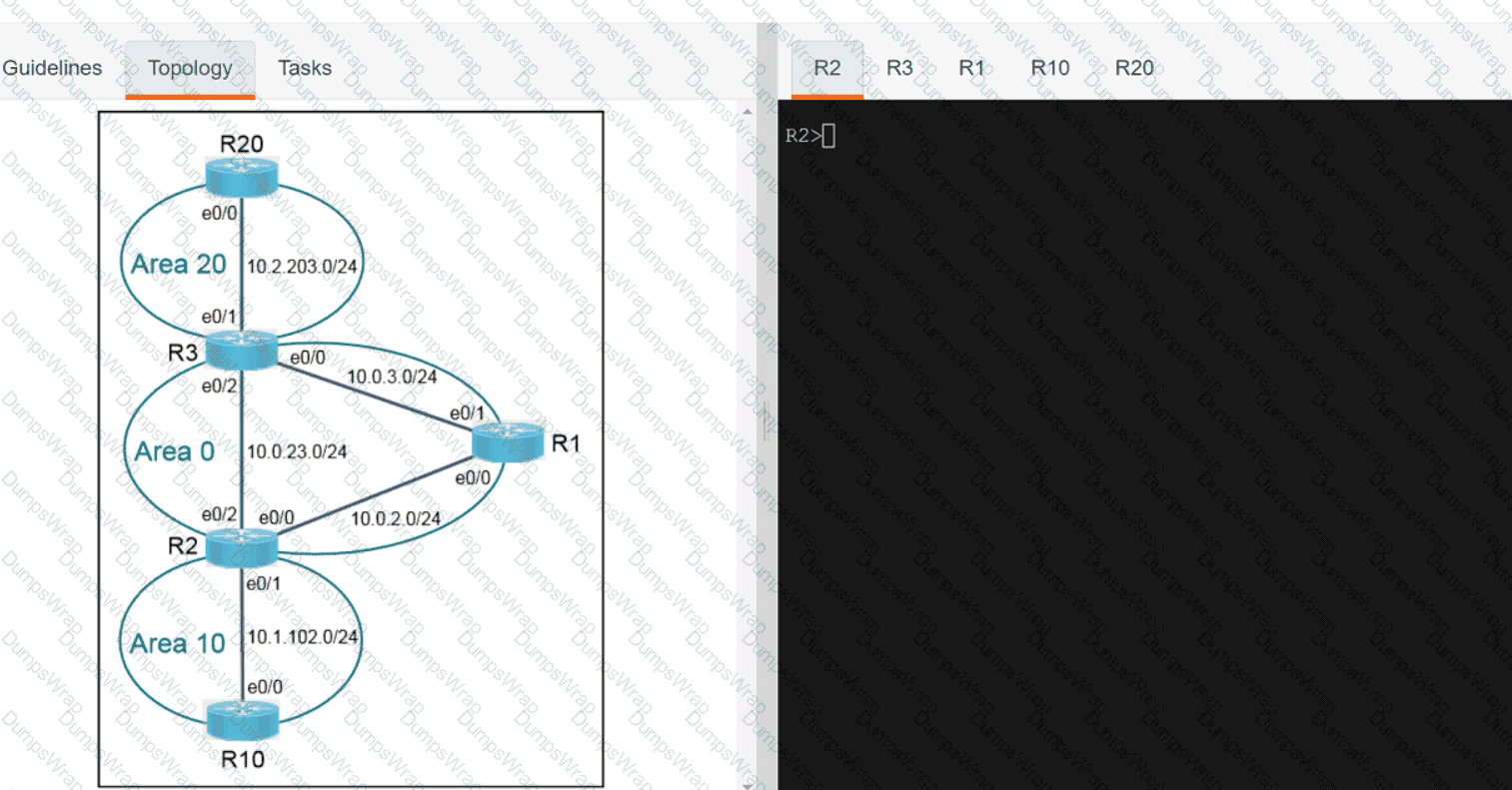
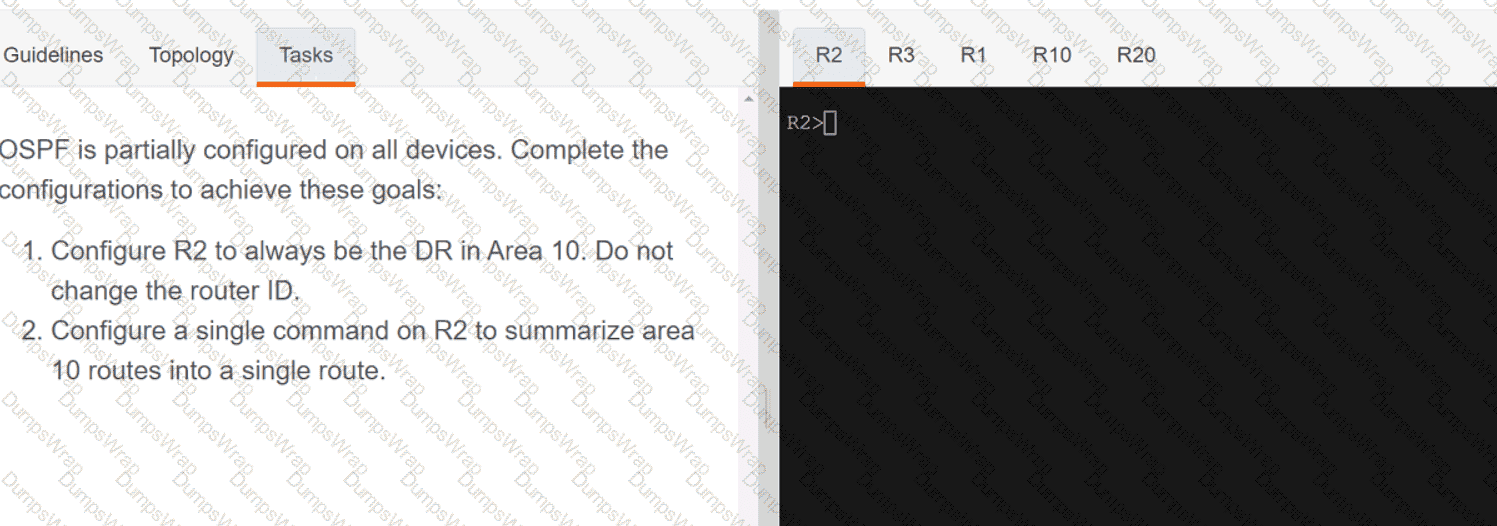
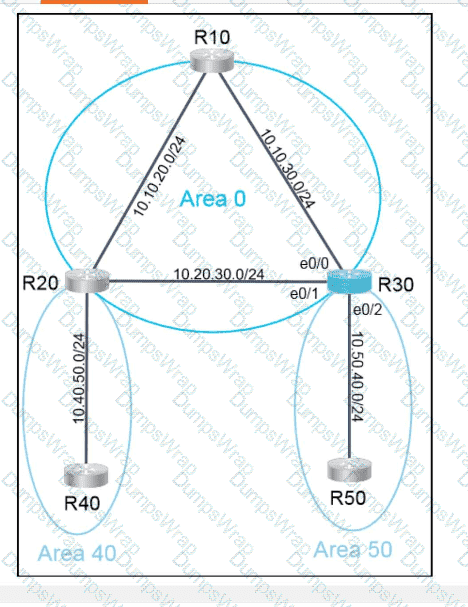
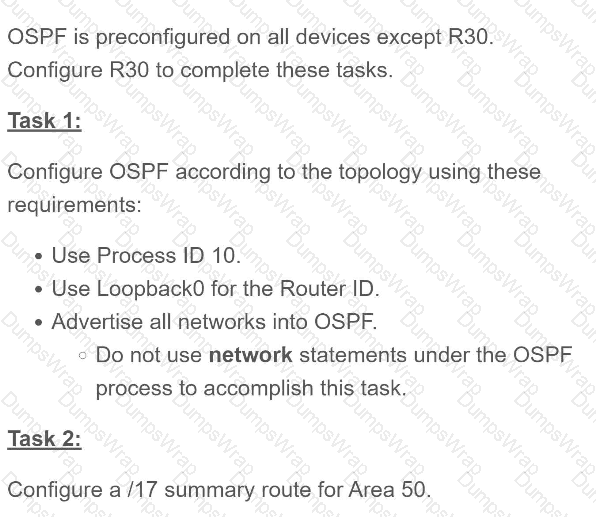
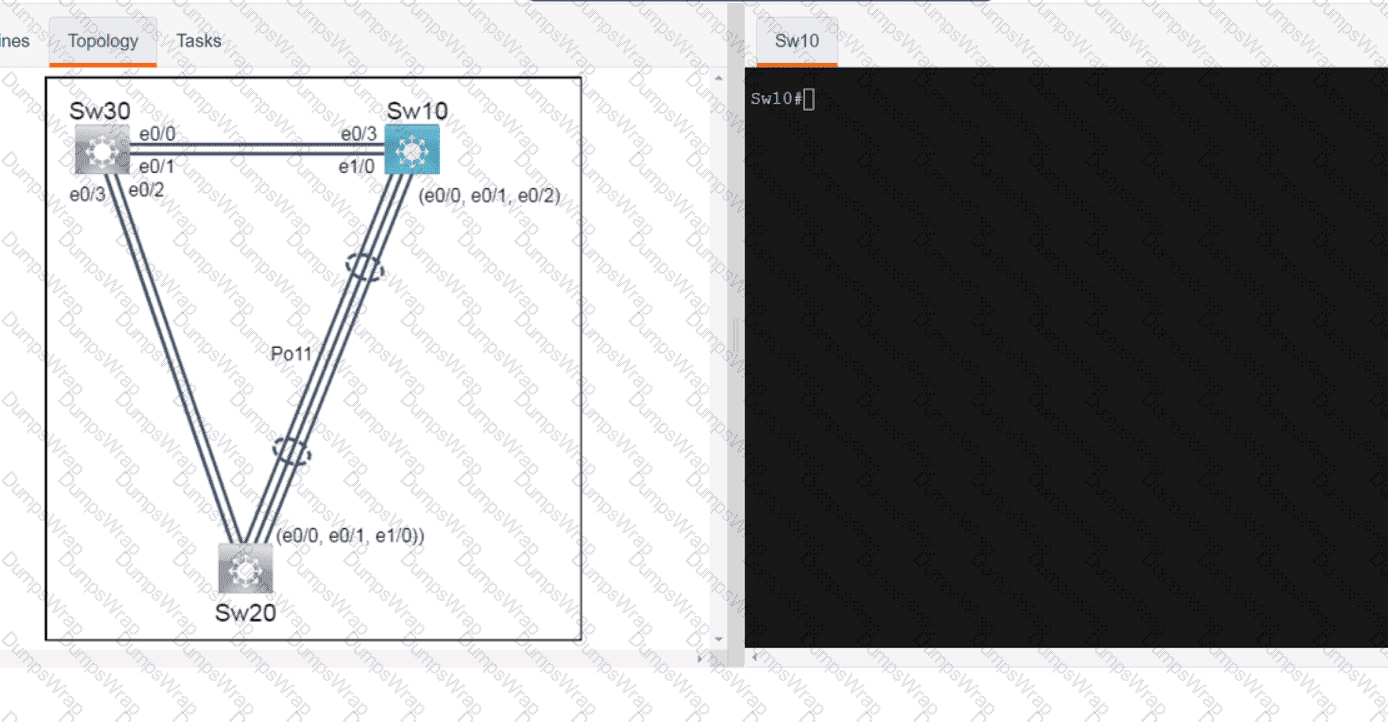
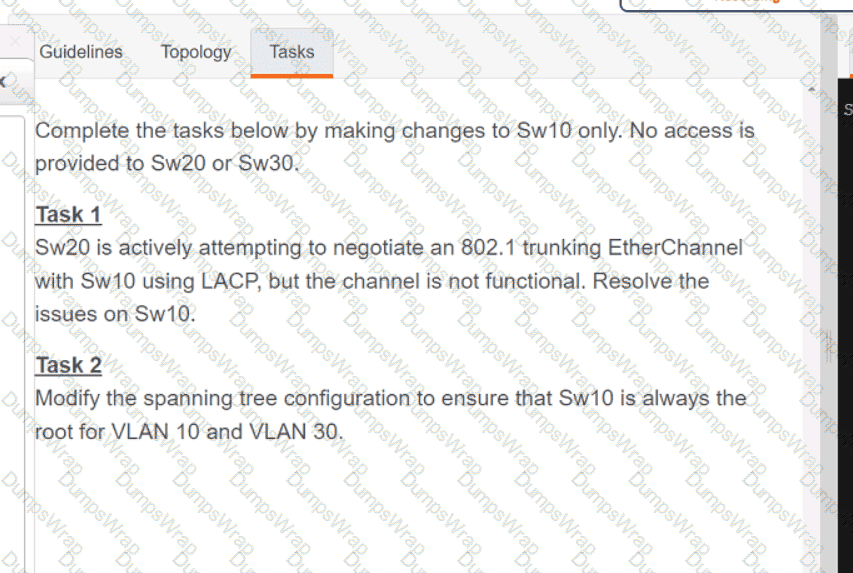
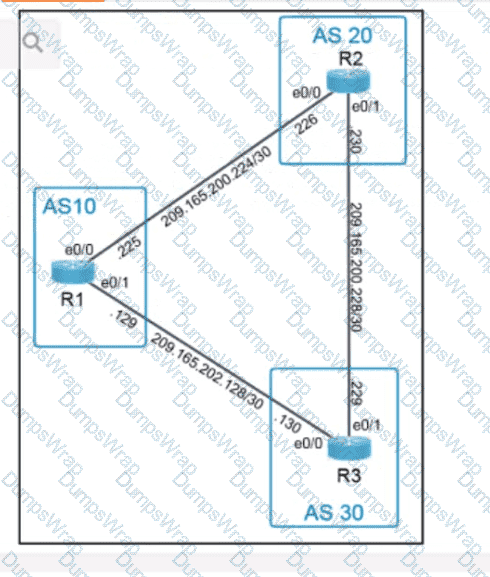
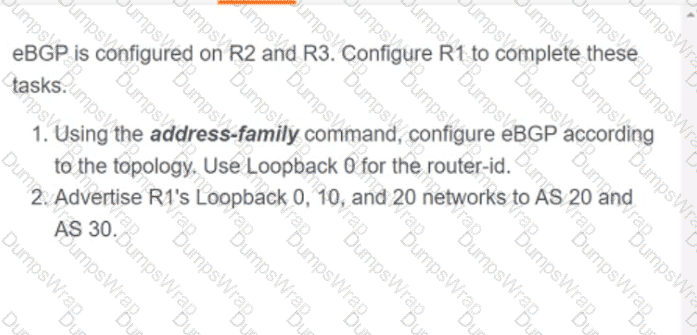
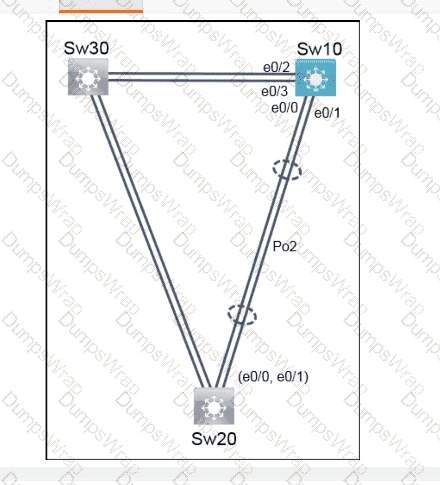
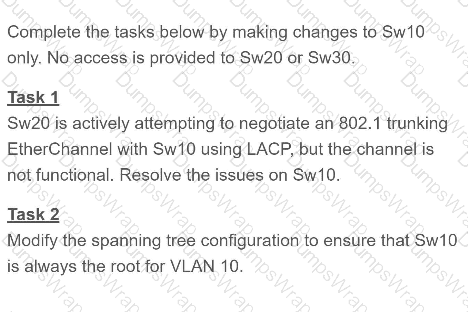
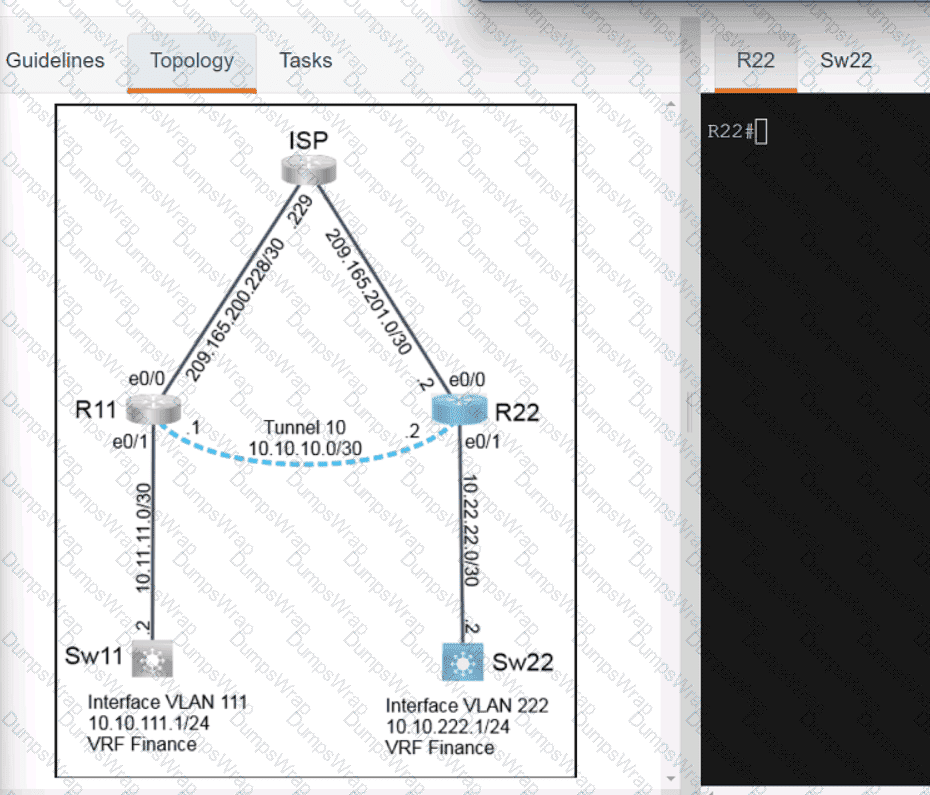
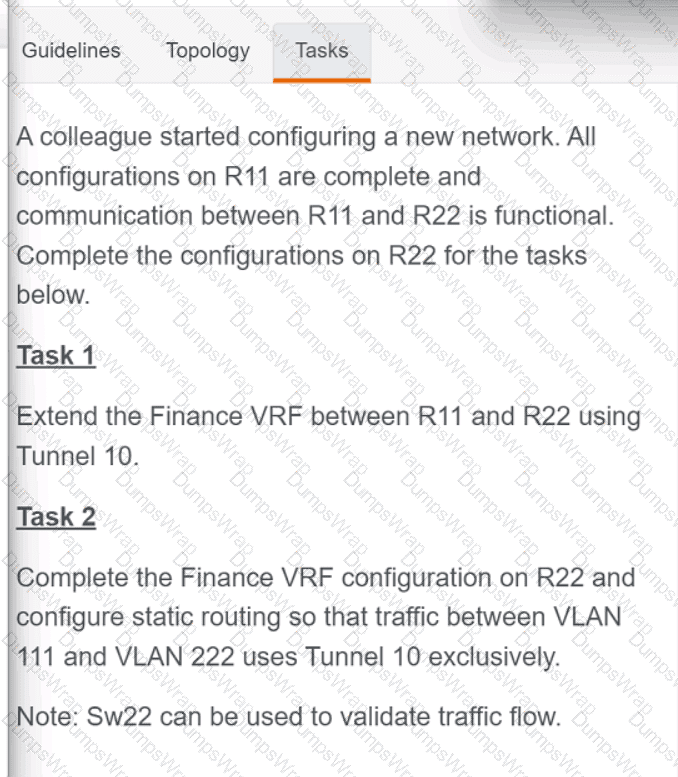
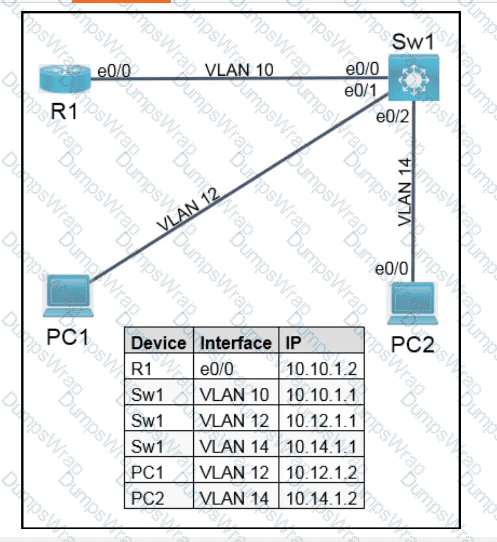

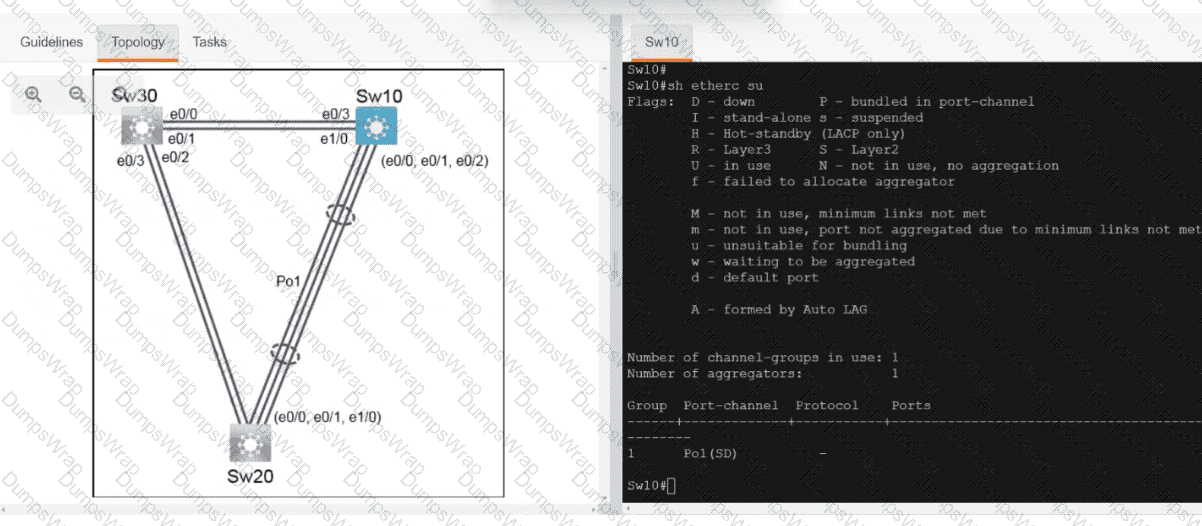
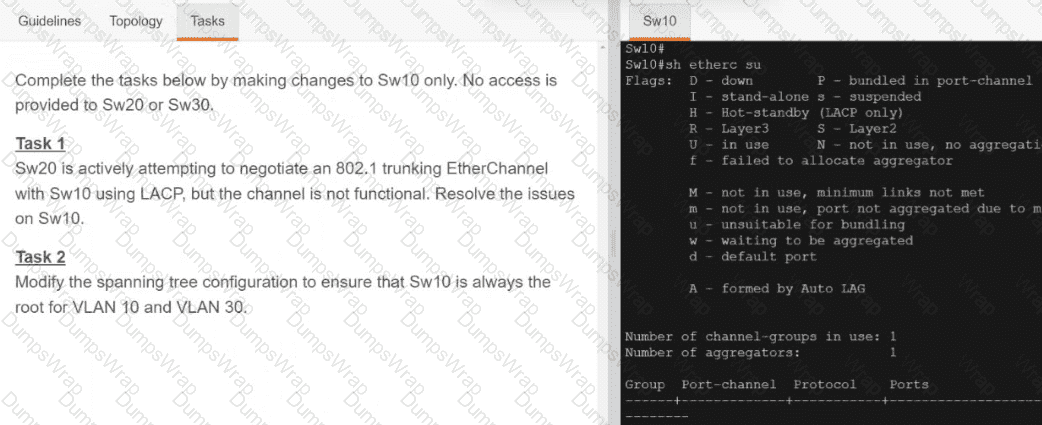

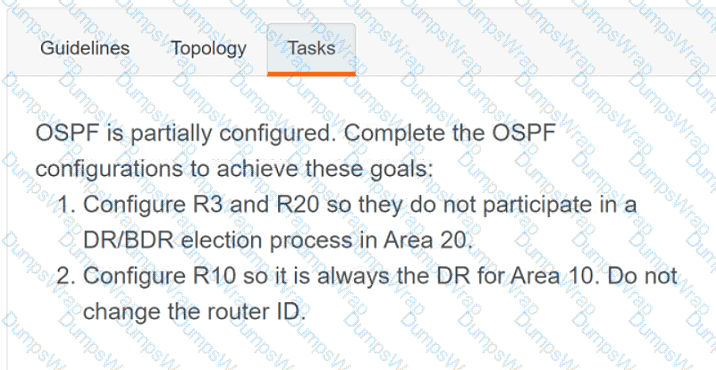
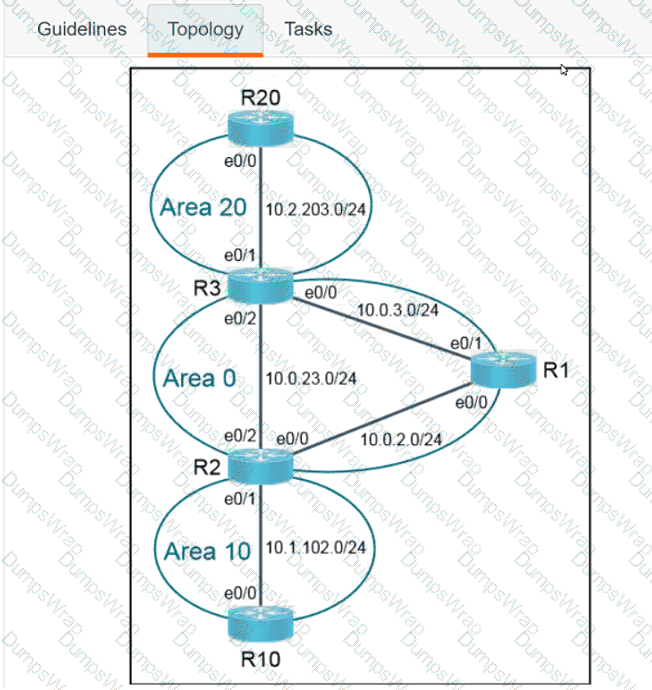
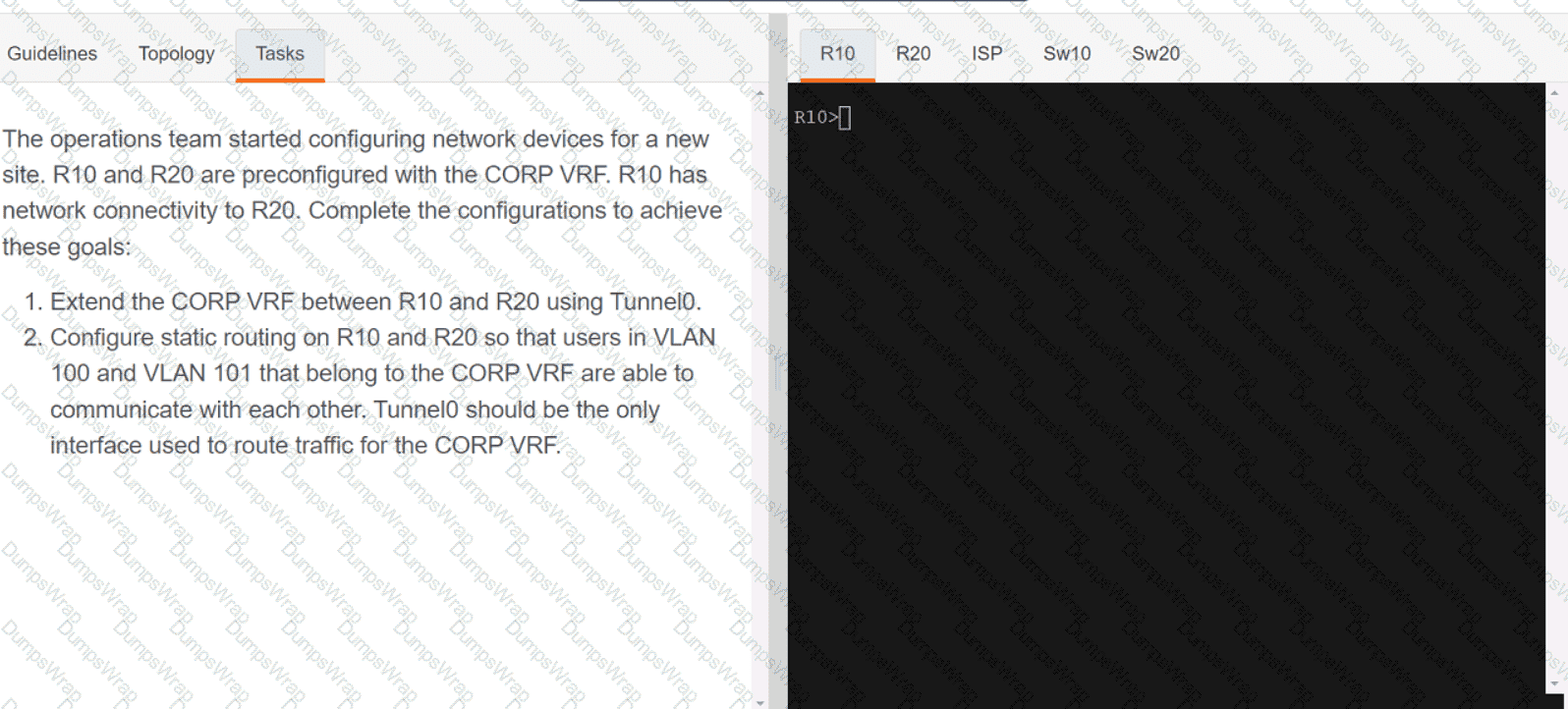
OR