Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) Questions and Answers
Refer to the exhibit.
What is the effect of this configuration?
What is the role of NFVI?
Why do packet loops occur during the configuration of BlDlR-PIM?
What are two factors to consider when implementing NSR High Availability on an MPLS PE router? (Choose two.)
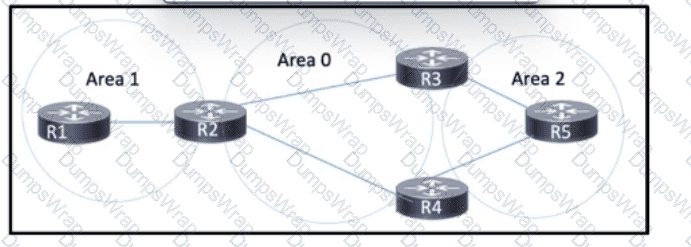
Refer to the exhibit. OSPF is running in the network, which is segmented into three areas. MPLS is enabled on all routers to support Layer 3 VPN. The network architect is concerned about potential packet loss when new OSPF adjacencies form. Which two tasks should the architect perform to implement MPLS LDP synchronization? (Choose two.)
What is the purpose of RSVP tear messages?
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
While implementing TTL security, an engineer issues the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command. After issuing this command, which BGP packets does the PE accept?

Refer to the exhibit. An engineer working for a private telecommunication company with an employee id: 3414:81:713 is implementing this network, in which:
Routers R1A and R1B are eBGP neighbors.
iBGP is configured within AS 65515 and AS 65516.
Network 192.168.2.0/24 is shared with AS 65516.
Router R3A has an iBGP relationship with router R2A only.
Router R2A has an iBGP relationship with routers R1A and R3A.
Which additional task must the engineer perform to complete the configuration?
Refer to the exhibit.

Which type of DDoS attack will be mitigated by this configuration?

Refer to the exhibit. Company A's network architect is implementing the capabilities that are described in RFC 4379 to provide new options for troubleshooting the company's MPLS network. MPLS LSPs are signaled via the BGP routing protocol with IPv4 unicast prefix FECs. Due to company security policies, access is controlled on the control plane and management plane. Which two tasks must the architect perform to achieve the goal? (Choose two.)
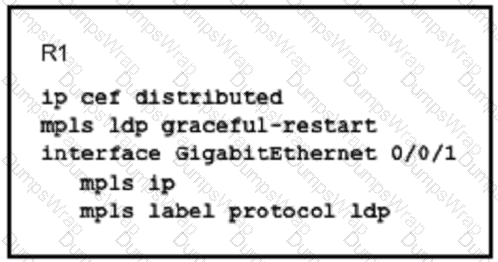
Which configuration mode do you use to apply the mpls Idp graceful-restart command in IOS XE Software? MPLS

Refer to the exhibit. A network engineer must configure XR-PE1 for uninterruptible failover from active RP to the standby RP Neither peer devices CGW1 nor the network of ASN 64512 support restart extensions Which configuration must the engineer apply to XR PEI to complete tasks?
A)

B)
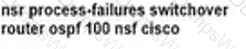
C)

D)

Refer to the exhibit:

An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network. Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
Refer to the exhibit.
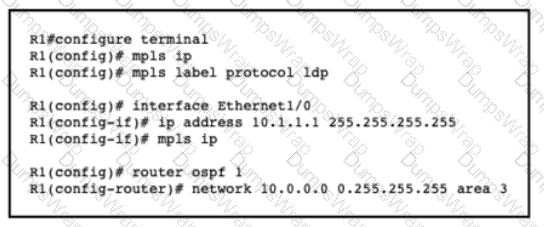
A network engineer is configuring MPLS LDP synchronization on router R1. Which additional configuration must an engineer apply to R1 so that it will synchronize to OSPF process 1?

What is a characteristic of the YANG model?
Which additional configuration is required for NetFlow to provide traceback information?
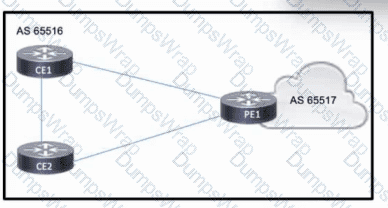
Refer to the exhibit. CE1 and CE2 reside in AS 65516 and access the internet through PE1, which resides in AS 65517. The PE-CE routing protocol is BGP, and CE1 and CE2 have an established iBGP peering. A network engineer must implement a route map on CE1 so that it becomes the preferred entry point for traffic from PE1.
Which action must the engineer take to meet the requirement?
Refer to the exhibit.
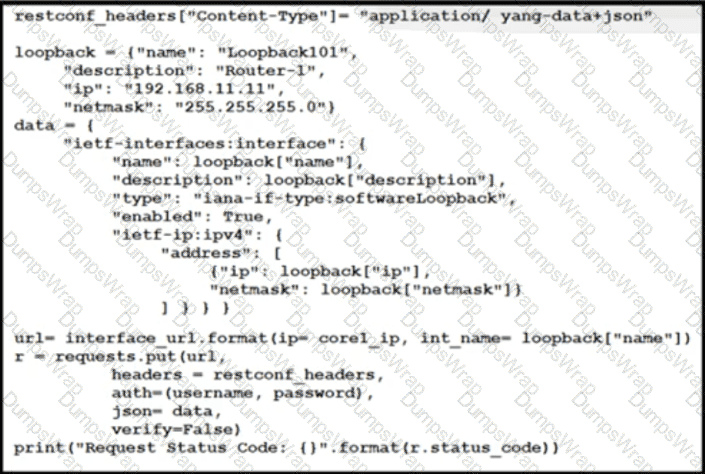
An engineer at a new ISP must configure many Cisco devices in the data center. To make the process more efficient, the engineer decides to automate the task with a REST API. Which action does this JSON script automate?
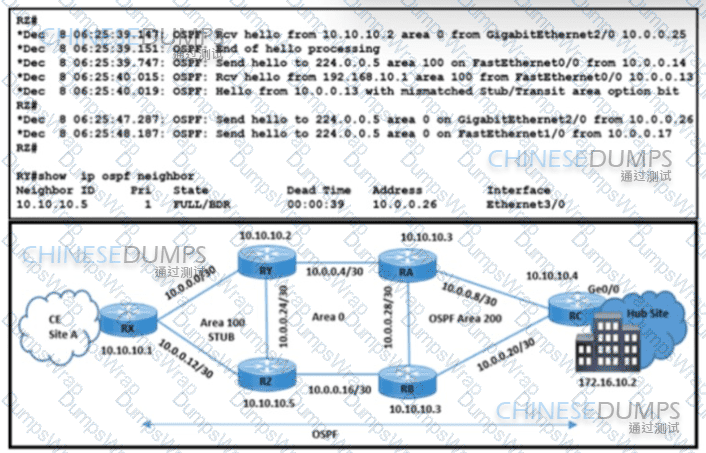
Refer to the exhibit. A network engineer received a complaint about these problems in OSPF stub area 100:
The Ethernet link is down between routers RX and RY because the fiber was cut.
CE site A traffic to the hub site is being dropped.
Which action resolves these issues?
Which BGP attribute is used first when determining the best path?
A network engineer is deploying VRF on ASBR router R1. The interface must have connectivity over an MPLS VPN inter-AS Option AB network. Which configuration must the engineer apply on the router to accomplish this task?
A)
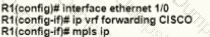
B)

C)

D)

How does Cisco MPLS TE use OSPF extensions to allow for optimized transit between a headend router and a destination router?
An engineering team must implement Unified MPLS to scale an MPLS network. Devices in the core layer use different IGPs, so the team decided to split the network into different areas. The team plans to keep the MPLS services as they are and introduce greater scalability. Which additional action must the engineers take to implement the Unified MPLS?
Refer to the exhibit:

What does this value mean when it is received in XML?
How do PE routers operate with the MDT in a multicast VPN?
Company A must increase throughput between two non-IEEE 802.3ad switches located in the access and distribution layers. A network engineer must create a link group with the same speed and duplex. The STP protocol must not block any of the group ports. Which action completes the implementation?
What is the primary role of a BR router in a 6rd environment?
Refer to the exhibit.
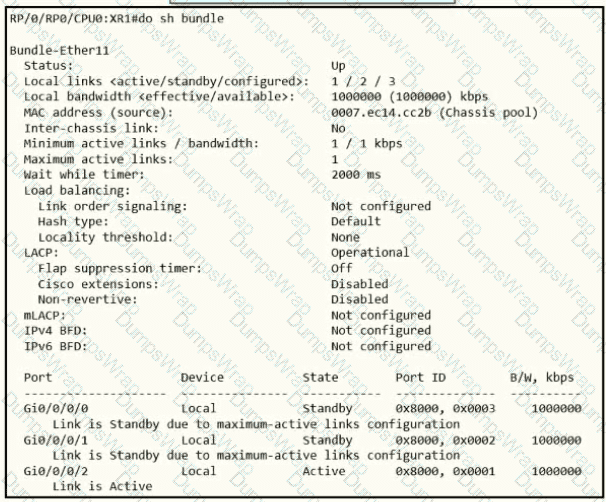
A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
Refer to the exhibit:

Based on the show/ command output, which result m true after BGP session is established?
Refer to the exhibit.

AN engineer is configuring segment routing on an ISP to simplify traffic engineering and management across network domains. What should the engineer do to complete the implementation of segment routing?
Refer to the exhibit.

A network administrator is implementing IGMP to enable multicast feed transmission to the receiver. Which configuration must the administrator deploy on GW1 to permit IGMP Joins only to the assigned (S, G) feed?
A)
B)

C)

D)

Refer to me exhibit.
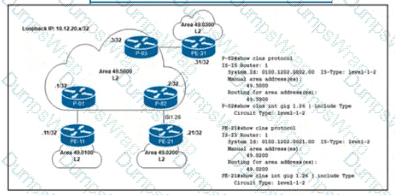
Refer to the exhibit. A network engineer notices PE-21 convergence degradation due to the growing LSDB size of Level 2 areas in the network. The engineer decides to migrate router PE-21 from an inter-area design to an intra-area implementation. Inter-area routing must be accomplished via an ATT-bit set by the Level 1/Level 2 router. Which configuration must the engineer implement on PE-21 to complete the migration?

Refer to the exhibit. A network engineer with an employee ID: 5086:72:817 is configuring a connection to manage CE1 from the OAM server on VLAN 100. PE1 must push S-VLAN tag 10 toward PE2 while forwarding traffic from CE1 to the OAM server. PE1 must push S-VLAN tag 20 toward PE2 while forwarding traffic from CE2 to the data traffic gateway. Which configuration must the engineer implement on PE2?
What do Chef and Puppet have in common?
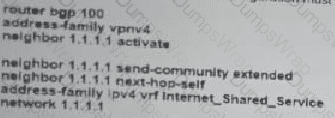
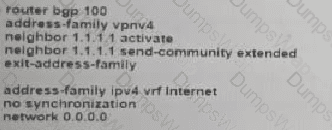
Refer to the exhibit. Which additional configuration must an engineer to the adge router to inject a default router into the MP-BGP address family for the internet_Shared_Services dedicated VRF?
A)
B)

C)
D)

Company A is implementing VoIP services across the company. The network architect designed a QoS policy to allow only specific IP subnets and mark the signaling flow with DSCP 36. The solution should be as secure as possible. Phones receive their IP addresses from the 172.184.12.0/24 pool and are assigned by the RADIUS server to VLAN 1021. Skinny Client Control Protocol is used as a signaling protocol in the network. For security reasons, switchport port-security maximum 1 vlan voice has been preconfigured on the switch side. Which two tasks must an engineer perform on SW_1 to achieve this goal? (Choose two.)
While an engineer deploys a new Cisco device to redistribute routes from OSPF to BGP, they notice that not all OSPF routes are getting advertised into BGP. Which action must the engineer perform so that the device allows O, OIA, OE1, and OE2 OSPF routes into other protocols?
Refer to the exhibit.
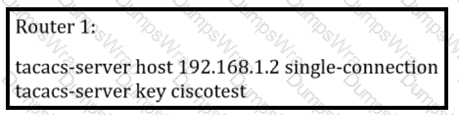
What is the result of this configuration?
Refer to the exhibit.
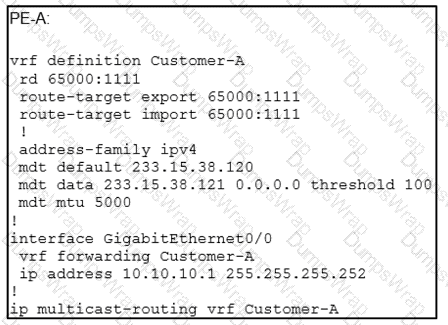
An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?
Which type of attack is an application attack?
BGP has been implemented on a IOS XR router. Which configuration sends BGP IPv4 labels to build inter-domain LSPs?
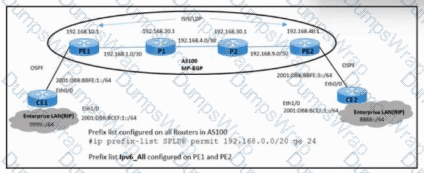
Refer to the exhibit. An engineer must update the configuration of the network with these requirements:
PE routers must define labels for IS-IS learned routes in AS100.
P routers must not receive LDP bindings for the external network in the IPv6 address family.
Which configuration must the engineer implement to meet these requirements?
A network administrator is planning a new network with a segment-routing architecture using a distributed control plane. How is routing information distributed on such a network?
Refer to the exhibit:
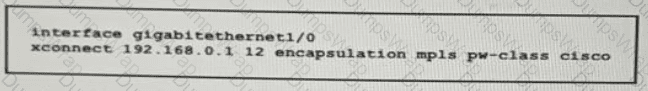
Which effect of this configuration is true?
Refer to the exhibit.
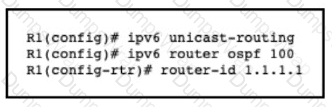
An engineer is configuring router R1 for OSPFv3 as shown. Which additional configuration must be performed so that the three active interfaces on the router will advertise routes and participate in OSPF IPv6 processes?
A)

B)

C)
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services For which reason do you make this decision?
A network engineer is configuring a newly installed PE router at the regional gateway location. The new PE router must use MPLS core routing protocols with the existing P router, and LDP sessions between the two routers must be protected to provide faster MPLS convergence. Which configuration must the engineer perform on the network so that LDP sessions are established?
An organization with big data requirements is implementing NETCONF as part of its migration to a new cloud-based environment. The organization has multiple offices across widespread geography. A network engineer is configuring NETCONF on one of the border routers. Which configuration must the engineer apply to save the running configuration?
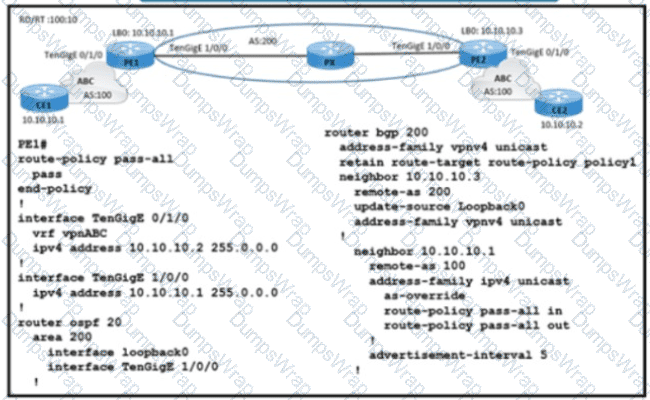
Refer to the exhibit. A service provider engineer Is configuring the connection between CE1 and CE2. AS 200 of the service provider and AS 100 of enterprise ABC should connect using BGP. The engineer already completed the configuration of VRF RT 100:10 of enterprise ABC. Which configuration must the engineer apply on PE1 to meet the requirement?
Which function does RSVP perform in a Cisco MPLS TE environment?
Refer to the exhibit:

Which statement describes this configuration?
Guidelines -
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology:
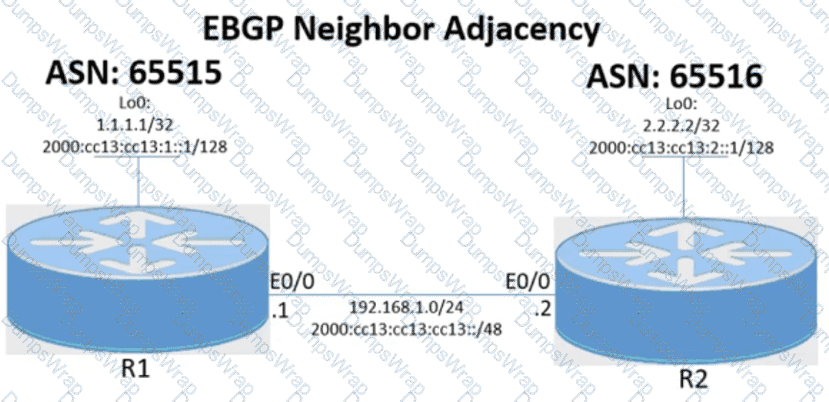
Tasks -
Configure the BGP routing protocol for R1 and R2 according to the topology to achieve these goals:
1. Configure EBGP neighbor adjacency for the IPv4 and IPv6 address family between R1 and R2 using Loopback0 IPv4 and IPv6 addresses. All BGP updates must come from the Loopback0 interface as the source. Do not use IGP routing protocols to complete this task.
2. Configure MD5 Authentication for the EBGP adjacency between R1 and R2. The password is clear text C1sc0!.
Refer to the exhibit.

An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
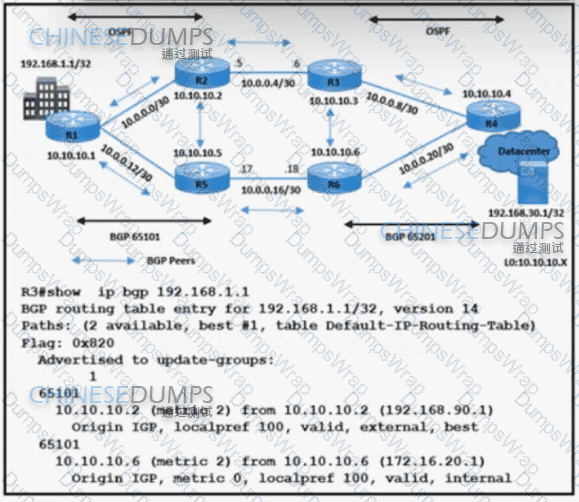
Refer to the exhibit. A network engineer is implementing BGP in AS 65101 and AS 65201. R3 sends data traffic to 192.168.1.1 /32 via the path R3-R2-R1. The traffic must travel via alternate path R6-R5 for prefix 192.168.1.1/32. Which action must be taken to meet the requirement?
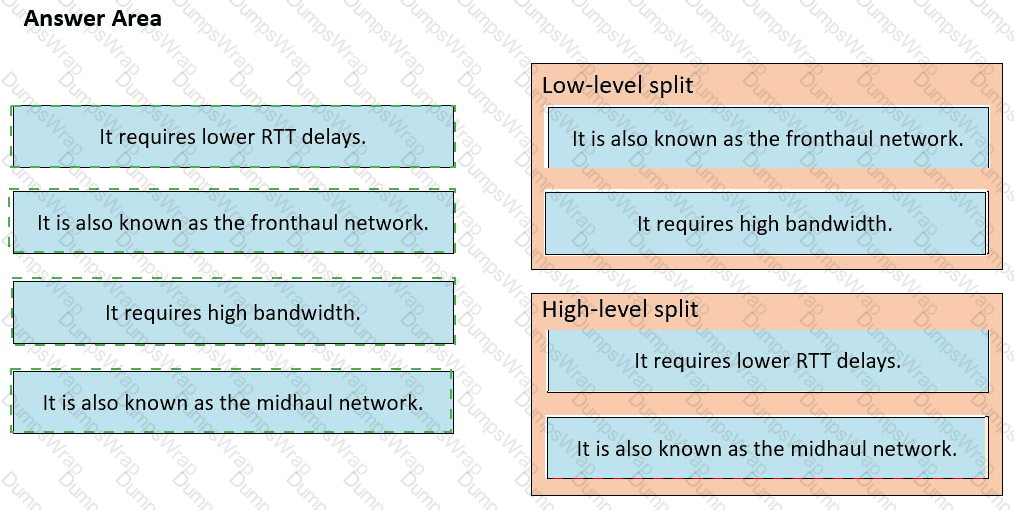
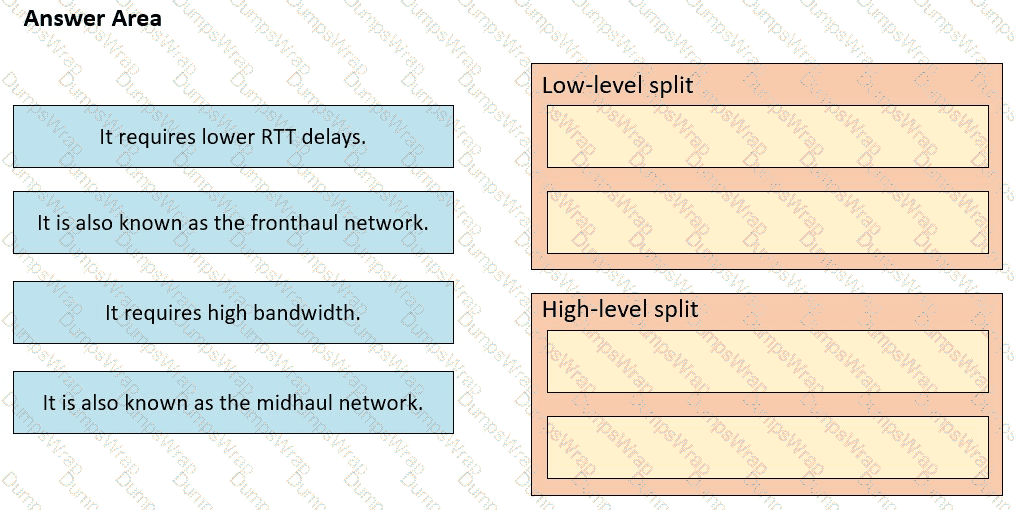
Drag and drop the characteristics from the left onto the corresponding radio splitting approaches on the right

Refer to the exhibit. A large enterprise streams training videos from a server connected to R4 to hosts connected to R5. PIM-SM is configured in the network using IGMPv2, with R2 serving as the RP. OSPF is configured in the network to support IGP routing, and the network uses BGP to access the internet through R3. The network engineering team must migrate the network to SSM.
Which action must the team take to begin the migration?

Refer to the exhibit an engineer working for a private telecommunication company with an employee Id: 4065:96:080 upgrades the WAN link between routers ASBR-101 and ASBR-201 to 1Gb by Installing a new physical connection between the Gi3 Interfaces. Which BGP attribute must the engineer configure on ASBR-201 so that the existing WAN link on Gi2 Is maintained as a backup?


In MPLS traffic engineering, which FRR operation swaps the label and pushes the backup label?
What is the purpose of DS-Lite technology?
Refer to the exhibit. All edge routers are fully meshed via the IBGP and IS-IS routing protocols, and LDP is used for label distribution. The network engineer must protect the TE tunnels and MPLS network from interface flaps and retain label information in the LIB cache for 10 minutes. Which action completes the implementation?
When configuring traffic engineering tunnels in Cisco MPLS core network, you see the traffic is not taking the expected path in the core.
Which command do you use to quickly check path of a TE tunnel?
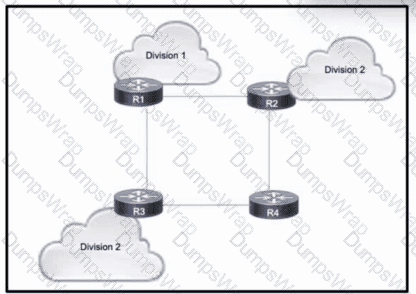
Refer to the exhibit. A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?
Refer to the exhibit:
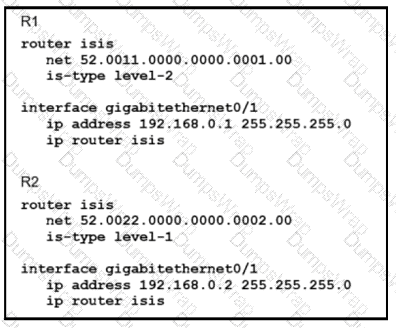
Which statement about the status of the neighbor relationship between R1 and R2 is true?
Egress PE NAT is being used via a single centralized router to provide Internet access to L3VPN customers.
Which description of the NAT operation is true?
Refer to the exhibit.

An engineer configured multicast routing on client's network. What is the effect of this multicast implementation?
Which service is a VNF role?
Refer to the exhibit.

What does this REST API script configure?
Refer to the exhibit:
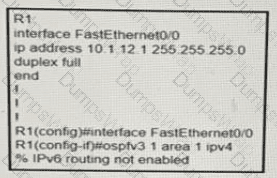
A network engineer is implementing an OSPF configuration Based on the output, which statement is true?
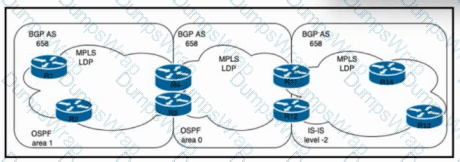
Refer to the exhibit. ISP_A is a Tier-1 ISP that provides private Layer 2 and Layer 3 VPN services across the globe using an MPLS-enabled backbone network. Routers R1, R2, R13, and R14 are PE devices. ASRs R3 and R4 and ASBRs R11 and R12 are acting as route reflectors with preconfigured next-hop-self for all BGP neighbors. After the network experienced IGP RIB overflow with multiple routes, a network engineer is working on a more scalable network design to minimize the impact on local RIBs. The solution should be based on RFC 3107 and maintain existing QoS capabilities.
Which task must the engineer perform to achieve the goal?
What is a characteristics of the Pipe model for MPLS QoS?
Refer to the exhibit.
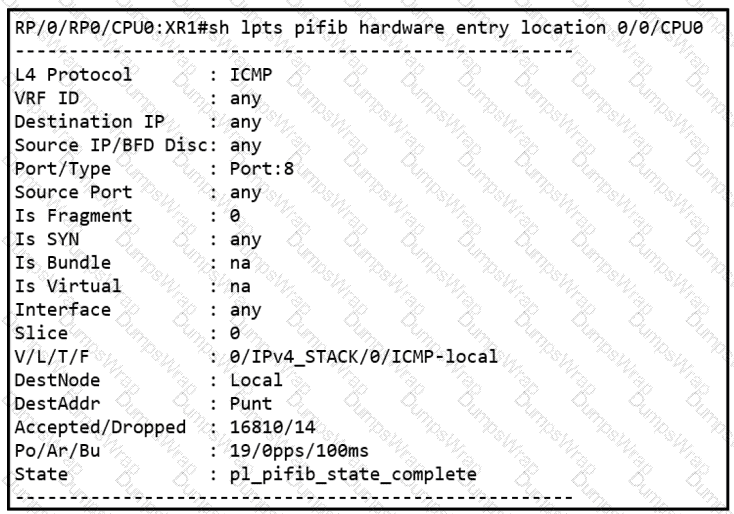
While troubleshooting the network, a network operator with an employee id: 3812:12:993 is trying to ping XR1. Which result should the operator expect when trying to ping to an XR1 local address?
Refer to the exhibit.
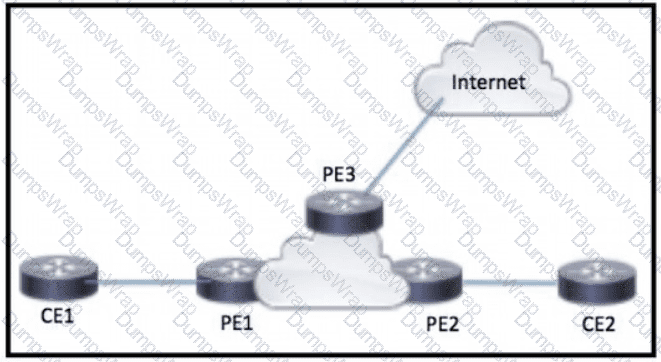
CE1 and CE2 require connectivity to the internet through the ISP connected to PE3 What should an engineer configure to complete this task?
Refer to the exhibit.

An engineer with an employee 10:4350:47:853 is implementing IS-IS as the new routing protocol in the network. All routers in the network operate as Level 2 routers in the same private autonomous system, and the three branches are connected via dark fibre. The engineer has already implemented IS-IS on router R1 with NET address 49.0133.532b.ca14.6915.21311.F40F.1B3a.ba10.00. Which IS-IS NET address configuration must be implemented on R3 to establish IS-IS connectivity?
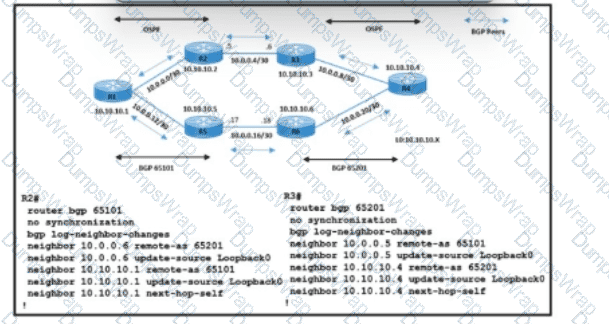
Refer to the exhibit. A network operations team is implementing eBGP on the service provider network. Data traffic between routers R1 and R4 must use the R2-R3 link, which connects AS 65101 and AS65201. iBGP sessions with adjacent routers are up on 10.10.10.1 and 10.10.10.4. The team is now updating the configuration for eBGP peers on routers R2 and R3. Which action must be taken to meet the requirements?
A company uses PIM-SM multicast with IGMPv2 to stream training videos from a server in one network to hosts in a different network. As the company has grown, the networking team decided to implement SSM to improve efficiency for multicast within Layer 2. Which action must the team take to begin the process?
Refer to the exhibit.

Refer to the exhibit. An ISP provides shared VoIP Extranet services to a customer in VRF-100 with these settings:
The VoIP services are hosted in the 198.19.100.0/24 space.
The customer has been assigned the 198.18.1.0/29 IP address block.
VRF-100 is assigned import and export route target 65010:100.
Which configuration must the engineer apply to PE-1 to provision VRF-100 and provide access to the shared services?
In an MPLS network, which protocol can be used to distribute a Segment Prefix?
Which capability does RSVP provide in an MPLS network?
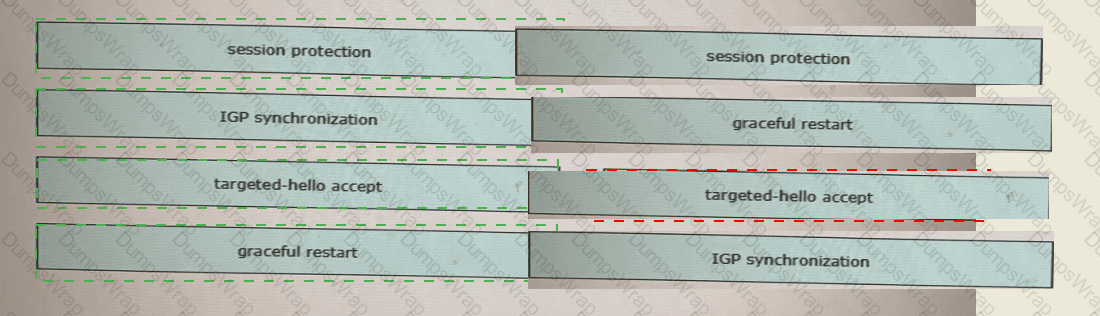
Drag and drop the LDP features from the left onto the correct usages on the right.

Refer to the exhibit:

R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?
In an EVPN operation, how does the PE determine and advertise Ethernet segment reachability?
A regional company is planning to bolster the security of their LAN infrastructure by implementing advanced encryption techniques between their core switch and their distribution switch. The solution must leverage hardware-accelerated encryption capabilities to transparently encrypt all traffic between the two switches at the data-link layer to safeguard against unauthorized access. However, it is important for the solution to have minimal impact on network performance and latency.
Which action must the engineer take to meet the requirements?
What is the primary purpose of routed optical networks?

Refer to the exhibit. AS 65517 is running OSPF within the core. BGP is running between all four autonomous systems, interconnecting several ISPs that provide intranet and extranet services. All of the PE routers are connected, and eBGP peering relationships have been established. A network engineer also configured an iBGP peering between PE3 and P1, and the peering is up. However, P1 cannot reach routes outside of AS 65517. Which action must the engineer take so that P1 reaches external routes?)

Refer to the exhibit. The network team must implement MPLS LDP session protection with two requirements:
Session protection is provided for core loopback IP addresses only.
The LDP session must remain operational for one hour when the WAN link on PE-XR1 fails.
Which configuration must the team implement on PE-XR1?
A network engineer is testing an automation platform that interacts with Cisco networking devices via NETCONF over SSH. In accordance with internal security requirements:
NETCONF sessions are permitted only from trusted sources in the 172.16.20.0/24 subnet.
CLI SSH access is permitted from any source.
Which configuration must the engineer apply on R1?
Refer to the exhibit.
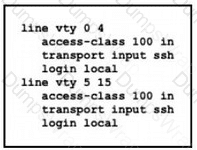
An engineer has started to configure a router for secure remote access as shown. All users who require network access need to be authenticated by the SSH Protocol.Which two actions must the engineer implement to complete the SSH configuration? (Choose two.)

Refer to the exhibit. The operations team for a service provider network is implementing a route map policy. OSPF area 0 should originate the default route with a type 2 metric of 2 when the application server on the connected interface (192.168.1.1) is up. Routers RL and RM have set up OSPF peering with other adjacent routers. Which action meets this requirement?
What causes multicast traffic to permanently stay on the shared tree and not switch to the source tree?
An engineer working for a private service provider with employee id: 3994 37 650 is configuring a Cisco device to redistribute OSPF into BGP. Which task enables the device to filter routes?
A customer of an ISP requests support to setup a BGP routing policy. Which BGP attribute should be configured to choose specific BGP speakers as preferred exit
points for the customer AS?
How does TI-LFA reduce packet loss in Segment routing?

Refer to the exhibit. R1 has two upstream Tier 1 service providers. BGP is in use as the exterior routing protocol, and ISP_A and ISP_B are sending the full BGP table. A network engineer must assign local-preference 70 to all routes with multiple exit discriminator 30. Which configuration must the network engineer apply?

Simulation 5


Which protocol is used for communication between the PCE and PCC?
What is the primary purpose of containers in a service-provider virtualization environment?
Which two features will be used when defining SR-TE explicit path hops if the devices are using IP unnumbered interfaces? (Choose two.)
A network engineer must implement an ACL-based solution to mitigate availability issues on a web service that is hosted on a server at IP address 172.16.15.18/23. Access to the web server should be allowed over HTTP from RFC 1918 addresses only. The network architect has already enabled PMTUD in the network. Which ACL configuration must the engineer implement to complete the task?

Refer to the exhibit. Users in AS 65010 are connected with the application server in AS 65050 with these requirements:
AS 65010 users are experiencing latency and congestion to connect with application server 172.16.50.10.
AS 65030 must be restricted to become Transient Autonomous System for traffic flow.
Links connected to AS 65020 and AS 65040 are underutilized and must be used efficiently for traffic.
Which two configurations must be implemented to meet these requirements? (Choose two.)
Refer to the exhibit.

A network engineer Is implementing OSPF multiarea. Which command on interface G0/1 resolves adjacency Issues in the new area?
Which CLI mode must be used to configure the BGP keychain in Cisco IOS XR software?
Refer to the exhibit:
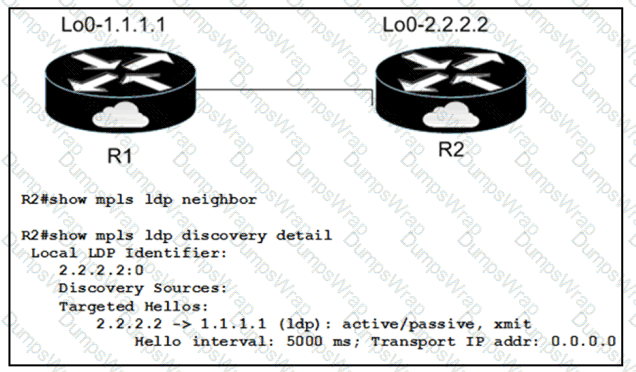
When implementing an LDP protocol, an engineer experienced an issue between two directly connected routers and noticed that no LDP neighbor exists for 1.1.1.1.
Which factor should be the reason for this situation?
What is the role of NSO?

Refer to the exhibit. A network engineer is configuring a new router for iBGP to improve the capacity of a growing network. The router must establish an iBGP peer relationship with its neighbor. The underlay network is already configured with the correct IP addresses. Which step should the engineer apply to complete this task?
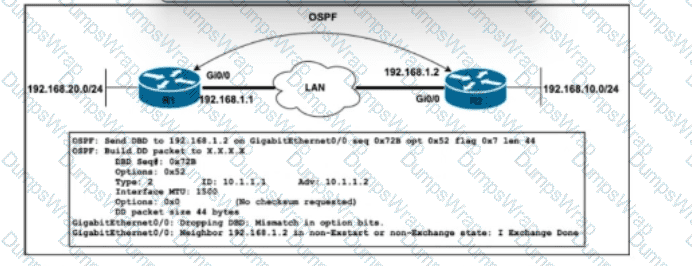
Refer to the exhibit. A network engineer just upgraded the Cisco IOS XE Software to the newest version on OSPF routers R1 and R2, added the point-to-point network type under Gi0/0 on R2, and configured ip route 192.168.10.0 255.255.255.0 192.168.1.2 on R1. After the engineer restarted the routers, R1 entered the Exstart state with its neighbor, but the adjacency has not been established. Which action must the engineer take to resolve the issue?
A network engineer must enable the helper router to terminate the OSPF graceful restart process if it detects any changes in the LSA. Which command enables this feature?
Which programmable API allows the service provider to plan and optimize the automation of network operations and achieve closed-loop operations?
Exhibit:
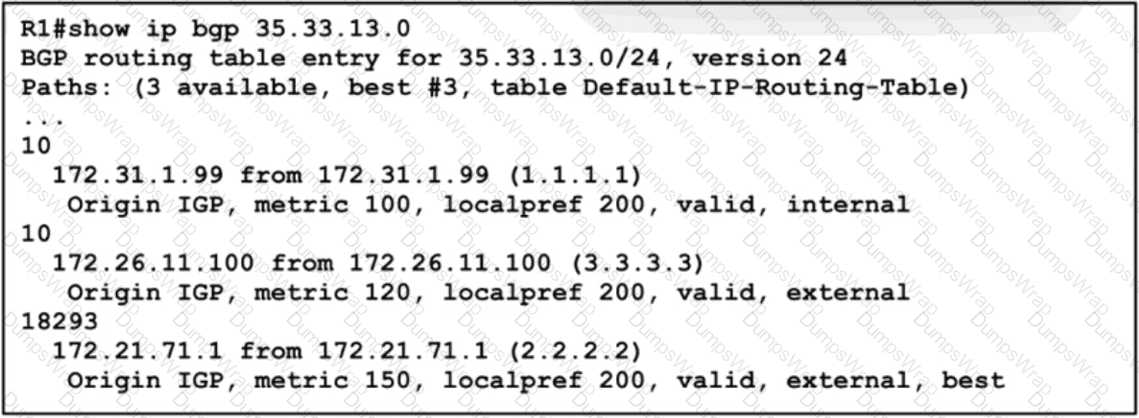
A network engineer must update the routing toward the web server with IP address 35.22.13.1. The primary path must be configured via the neighbor router with ID 1.1.1.1. However, local-preference configuration is not permitted on R1. Which task must the engineer perform on R1 to complete the implementation?

Refer to the exhibit. In the service provider network, routers PE1, PE2, and PE4 have access to the internet and provide access to customer networks. Router PE3 is used for access to other customer systems. In accordance with a new SLA, an engineer is updating settings on this network so that router CE1 accesses the internet via PE1 instead of PE2. Which two tasks must the engineer perform to complete the process? (Choose two.)
What is the function of the FEC field within the OTN signal structure?

Refer to the exhibit. The network is configured with OSPF. A networking team just connected a streaming multicast server to router R7, and they now must enable access for users throughout the network to stream video from the server.
Which action must the team take so that users can stream video without overloading the network?
After a possible security breach, the network administrator of an ISP must verify the times that several different users logged into the network. Which command must the administrator enter to display the login time of each user that activated a session?
A mid-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company's two sites across the service provider core. To meet service requirements, the service provider must extend the Layer 2 domain between the company's two locations.
Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?




Which function does orchestrated fulfillment perform under the Cisco Network Services Orchestrator model?
Refer to the exhibit.

Routers R2 and R3 are Level 1/Level 2 IS-IS routers that redistribute 198 18.x.x/24 prefixes to routers R5 and R6 In the Level 1 area R2 Is to be the preferred router for all redistributed prefixes in the Level 1 area. Which configuration sets this preference?

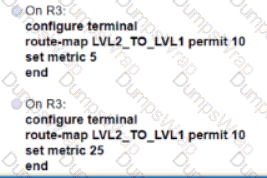
An engineer Is implementing NSR with OSPF on a large campus that requires high availability. Which task must an engineer perform to complete the process with minimal disruption to traffic?
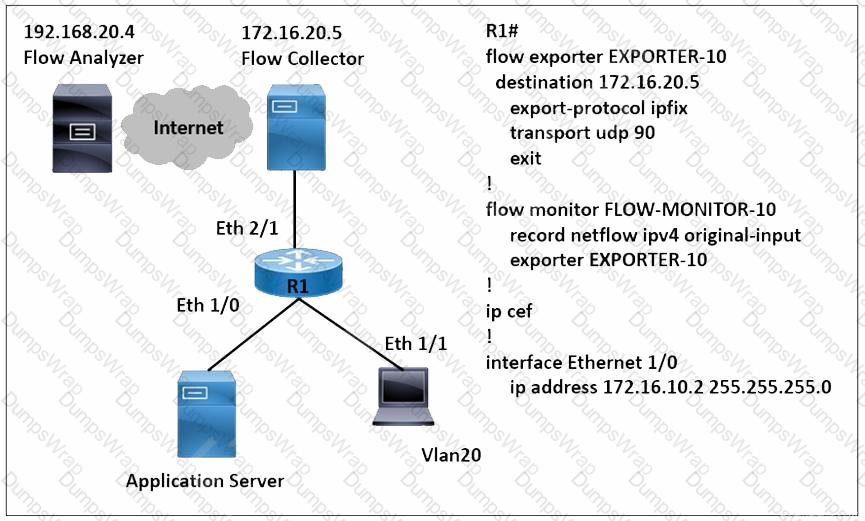
Refer to the exhibit. A network engineer wants to monitor traffic from the application server and send the output to the external monitoring device at 172.16.20.5. Application server traffic should pass through the R1 Eth2/1 interface for further analysis after it is monitored. Which configuration must be applied on the R1 router?
Refer to the exhibit.

A network engineer with an employee id: 3812:12:993 has started to configure router R1 for IS-IS as shown. Which additional configuration must be applied to configure the IS-IS instance to advertise only network prefixes associated to passive interfaces?

Refer to the exhibit.

An engineer ran this show telemetry command to view subscription SUB11 on RouterX. The engineer then decided that RouterY should provide the same output lor sensor group SGroup13 as RouterX. The engineer cannot access RouterX to copy its configuration No access lists on the router block user access Which configuration must the engineer apply on RouterY to provide the same output from the show telemetry command?
A)

B)

C)

D)


Refer to the exhibit. Router R13 is operating in Level 1 / Level 2 mode. A network engineer with an employee ID: 5209:82:636 must change the IS-IS cost of the route IP address 10.212.124.1 to 90. The metric update must be carried over in TLV 128. Which configuration must be implemented to complete the task?
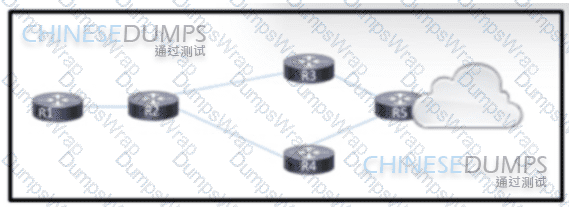
Refer to the exhibit. An engineer is scripting ACLs to handle traffic on the given network. The engineer must block users on the network between R1 and R2 from leaving the network through R5. but these users must still be able to access all resources within the administrative domain. How must the engineer implement the ACL configuration?
You are writing an RPL script to accept routes only from certain autonomous systems Consider this code.

If you apply this code to BGP filters, which effect does the code have on your router?
Refer to the exhibit:
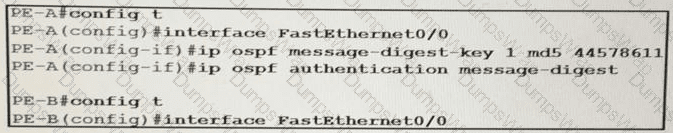
An engineer wants to authenticate the OSPF neighbor between PEA and PE-B using MD5.
Which command on PE-B successfully completes the configuration?
A)

B)

C)

D)

Refer to the exhibit.
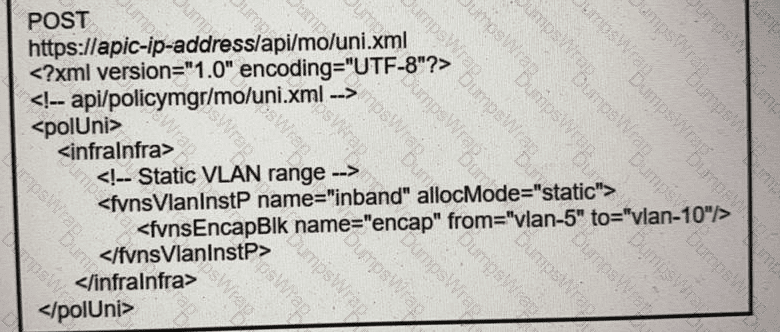
What does the script configure?
Which module refers to the network automation using Ansible?
Refer To the exhibit:

On R1, which output does the show isis neighbors command generate?
A)

B)

C)

D)
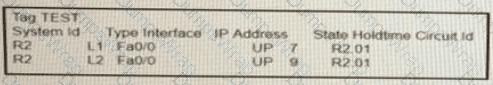
Which feature describes the weight parameter for BGP path selection?
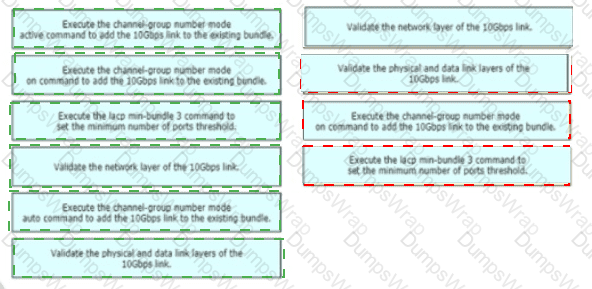
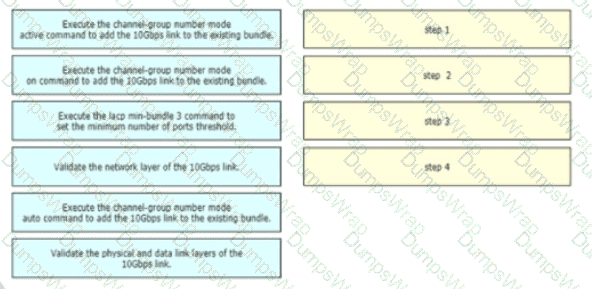
A network engineer is adding 10Gbps link to an existing 2X1Gbps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be take out of service if one of its member links does down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.
What is a characteristic of MVPN?
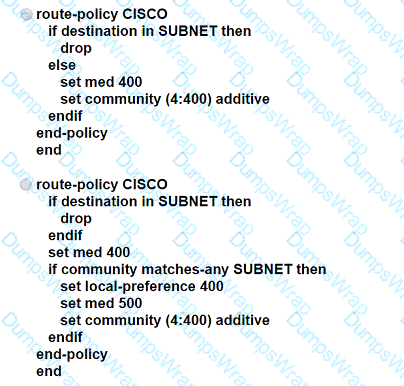
A network engineer is configuring a BGP route policy for the SUBNET prefix set. Matching traffic must be dropped, and other traffic must have its MED value set to 400 and community 4:400 added to the route. Which configuration must an engineer apply?

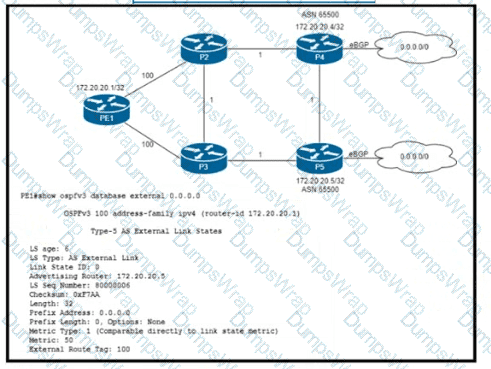
Refer to the exhibit. Router P4 and P5 receive the 0.0.0.0/0 route from the ISP via eBGP peering P4 is the primary Internet gateway router, and P5 is its Backup. P5 is already advertising a default route into OSPF domain. Which configuration must Be applied to P4 so that advertises a default route Into OSPF and Becomes me primary internet gateway for the network?

Refer to the exhibit.
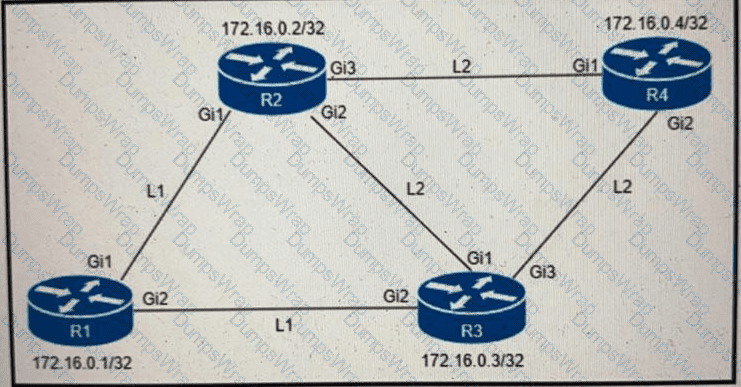
An engineer must configure router R2 as the new P router in the network. Which configuration must be applied to R2 to enable LDP-IGP Sync on its L2 IS-IS adjacencies?

Which characteristic describes prefix segment identifier?
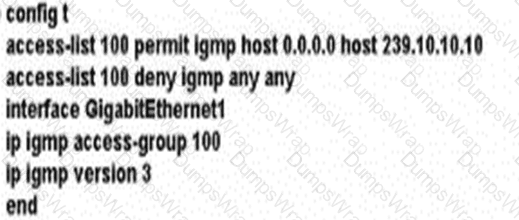
A network engineer is configuring a router to send multicast traffic for the 239.10.10.10 group. Which configuration must an .... forward the traffic?

Refer to the exhibit. A network engineer is configuring an SNMP community on router RB with these requirements:
Allow read-only access for all objects to members of Access-List 10 that use the comaccess community string.
Other SNMP managers must not have access to objects.
SNMP authentication failure traps must be sent to SNMPv2c and then to the host using SNMPv2c with the public community string.
Which configuration meets these requirements?

An engineer working for telecommunication company with an employee id: 3715 15 021 needs to secure the LAN network using a prefix list Which best practice should the engineer follow when he implements a prefix list?
Refer to the exhibit.

An engineer needs to implement this QoS policy on customer's network due to ongoing slow network issues. What will be the effect on the network when the engineer implements this configuration?

Refer to the exhibit. A network operator working for a private telecommunication company with an employee id: 7138: 13:414 just added new users to the network, which resides in VLANs connected to routers R1 and R4. The engineer now must configure the network so that routers R1 and R4 share routes to the VLANs, but routers R2 and R3 are prevented from including the routes in their routing tables. Which configuration must the engineer apply to R4 to begin implementing the request?
How is RSVP used with MPLS traffic engineering tunnels?
Network devices in the core layer use different IGPs, and the network is split into several areas. The engineer must use a NETCONF operation to load a full interface configuration on multiple Cisco devices to ensure that they meet company standards. The devices must work over SSH from the Linux jump server. Which action meets the configuration requirements?
A network team has failed to implement IS-IS multitopology. What is the reason for it?
What are the four primary components of an API?
The network team is planning to implement IPv6 on the company’s existing IPv4 network infrastructure. The network currently uses IS-IS to share routes between peers. Which task must the team perform so that IS-IS will run in multitopology mode on the updated IPv6 network?
A network operator with an employee ID 4531 26:504 must implement a PIM-SSM multicast configuration on the customer's network so that users in different domains are able to access and stream live traffic. The IGMP version must be enabled to support the SSM implementation. Which action must the engineer perform on R1 to complete the SSM implementation?

Refer to the exhibit:

If router A is the RP, which PIM mode can you configure so that devices will send multicast traffic toward the RP?

Refer to the exhibit. A growing company wants to ensure high availability and redundancy for its critical web servers, which are located in an offsite data center. The network architect decided to implement BGP so that the network can use redundant paths for outbound traffic toward the destination subnet 10.2.2.0/24. A network engineer already configured basic BGP settings on edge router R1, which is a Cisco ASR-1001X router. The engineer also confirmed loopback reachability to routers R2 and R3, and the AS path length toward the destination is the same via R2 and R3. Which action must the engineer take on R1 to complete the implementation?

Refer to the exhibit. A client wants to filter routes to a BGP peer to limit access to restricted areas within the network. The engineer configures the route map ciscotest to filter routes from the BGP neighbor. The engineer also sets a tag that will be used for QoS in the future. Which task must be performed to complete the Implementation?
Refer to the exhibit.

A network engineer must configure an LDP neighborship between two newly installed routers that are located in two different offices. Router 1 is the core router in the network and it has already established OSPF adjacency with router 2. On router 1 and router 2. interface fa0/0 is configured for BFD. Which additional configuration must the engineer apply to the two devices to meet the requirement?
What Is the primary role of Ansible In a network?
Refer to the exhibit:

What does the REST API command do?
Which type of attack is a Protocol attack?
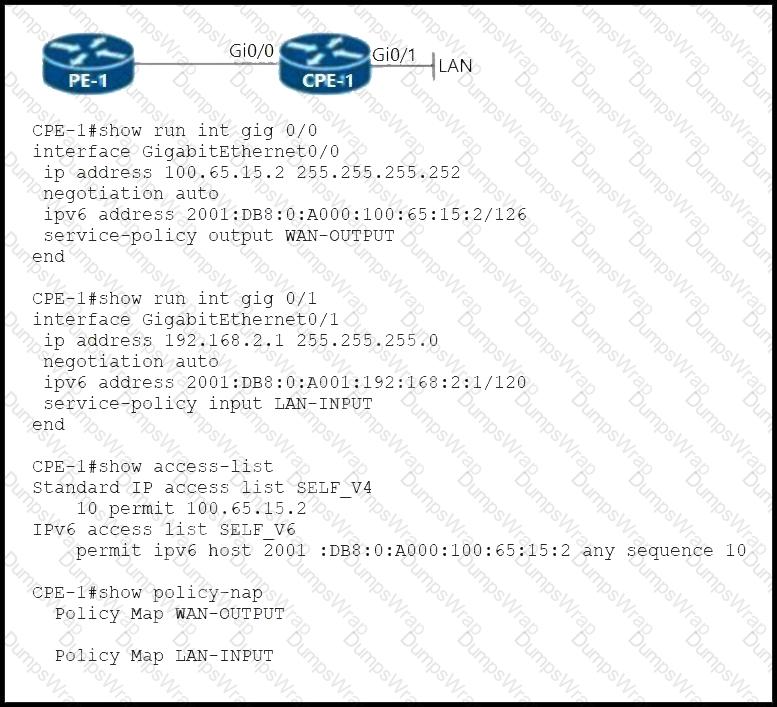
Refer to the exhibit. A network engineer configures CPE-1 for QoS with these requirements:
IPv4 and IPv6 traffic originated by the CPE-1 WAN IP address must be marked with DSCP CS3.
IPv4 LAN traffic must be marked with DSCP CS1.
IPv6 LAN traffic must be marked with DSCP default.
Which configuration must the engineer implement on CPE-1?
Refer to the exhibit:
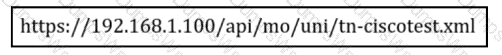
What is the URL used for with REST API?
What is the purpose of microsegments in the SRv6 architecture?
What is the difference between SNMP and model-driven telemetry?
Why is the keyword none needed when implementing management plane security using TACACS?
Refer to the exhibit:

Which effect of this configuration is true?
What is the primary purpose of the flexible algorithm in a segment-routing environment?
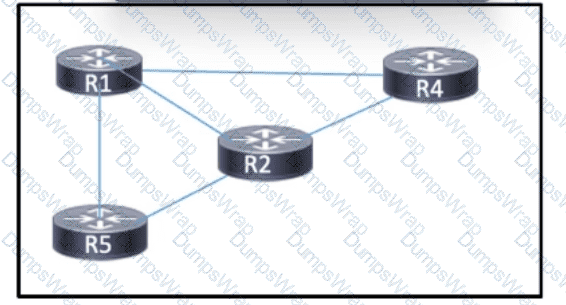
Refer to the exhibit. MPLS is running in the network with OSPF as the IGP. Full routes are shared between the routers, and each connected link has an MPLS neighbor relationship. A network engineer must update the network configuration so that it will maintain LDP neighbor relationships if a directly connected link goes down. Which action must the engineer take as part of the process?
Which two tasks must an engineer perform when implementing LDP NSF on the network? (Choose two.)

Refer to the exhibit. An engineer must Implement a traceroute operation to verity the R1 point-to-multipoint LSP connections. The traceroute operation must return all labels and hop-by-hop IP addresses for destinations 10.20.0.1. 10.30.0.1, and 10.40.0.1. and the maximum number of hops is 4. Which command must be executed to meet the requirements?