Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Questions and Answers
A container running a Python script is failing when it reaches the integration testing phase of the CI/CD process. The code has been reviewed thoroughly and the build process works on this container and all other containers pass unit and integration testing.
What should be verified to resolve the issue?
Which load balancing algorithm balances load based on the active sessions of a node?
Refer to the exhibit.

A network engineer created a simple Python Flask application but must incorporate a CSRF token. Which code snippet must be added in the blank in the script to manually incorporate the token?
Which Puppet manifest changes the NTP server and generates the traffic from VLAN 15?
A)

B)

C)

D)

A developer IS deploying an action to automate the configuration and management of Cisco network switches and routers. The application must use REST API interlace to achieve programmability. The security team mandates that the network must be protected against DDoS attacks. What mitigates the attacks without impacting genuine requests?
Which transport layer protocol does gRPC use to retrieve telemetry information?
Which RFC5988 (Web Linking) relation type is used in the Link header to control pagination in APIs?
Users report that they are no longer able to process transactions with the online ordering application, and the logging dashboard is
displaying these messages:
Fri Jan 10 19:37:31.123 ESI 2020 [FRONTEND] [NFO: Incoming request to add item to cart from user 45834534858
Fri Jan 10 19:37:31.247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31.250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused
What is causing the problem seen in these log messages?
Refer to the exhibit.
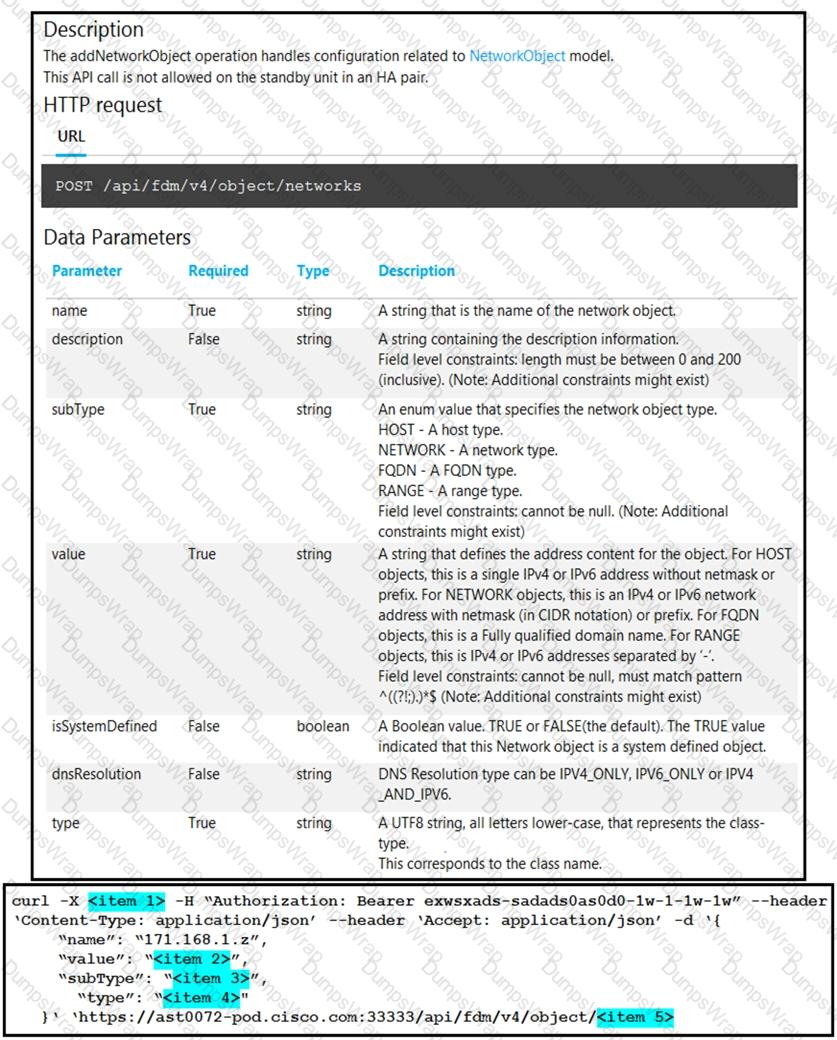
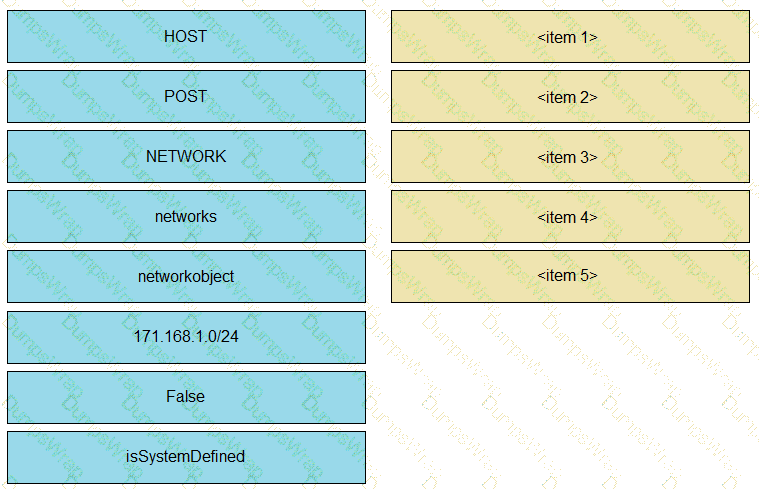
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the cURL exhibit to complete the cURL request to FirePower Device Manager API to create objects. Not all code snippets are used.
A developer has created a local Docker alpine image that has the image ID 'dockapp432195596ffr' and tagged as ‘new’. Which command creates a running container based on the tagged image, with the container port 80 bound to port 8080 on the host?
Which statement about microservices architecture is true?
What are two principles according to the build, release, run principle of the twelve-factor app methodology?
(Choose two.)
A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls. Which approach enhances the responsiveness and performance of the API?
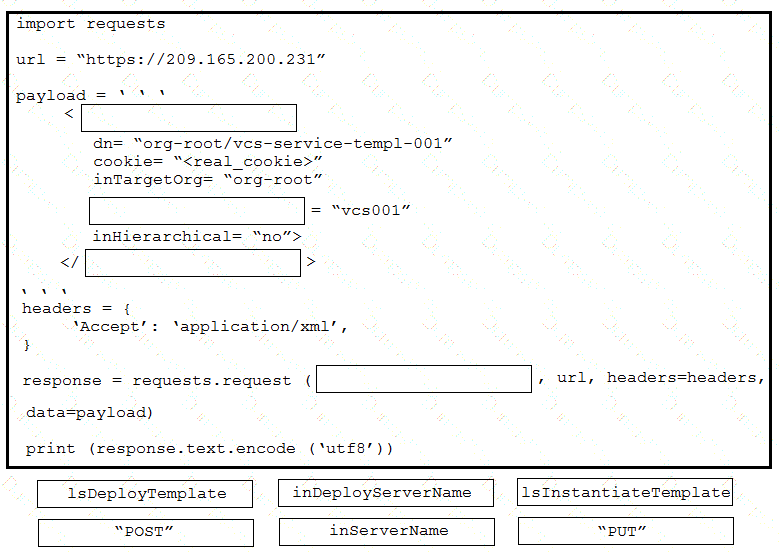
Drag and drop the code from the bottom onto the box where the code is missing to provision a new Cisco Unified Computing System server by using the UCS XML API. Options may be used more than once. Not all options are used.
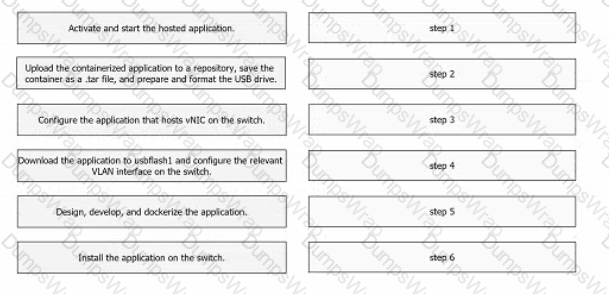
Drag and drop the steps from the left into the order on the right to host a Docker-contained application on a Cisco Catalyst 9000 Series Switch.
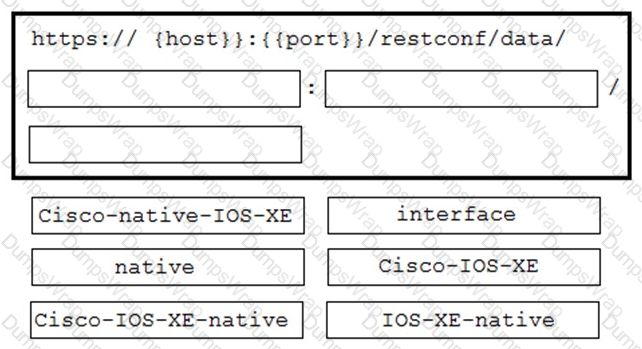
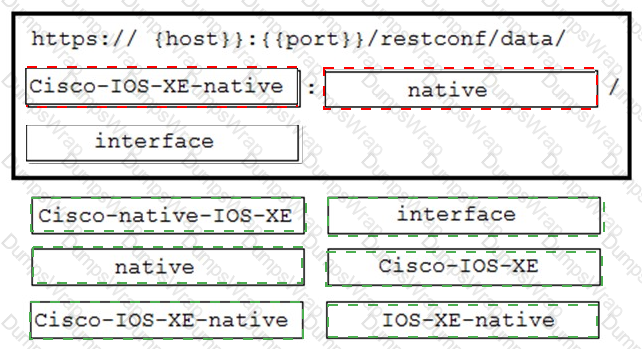
A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Drag and drop the
components from the bottom onto the box where the code is missing to complete the RESTCONF URI. Not all
options are used.
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch. Which two interface configuration options should be used? (Choose two.)
An application is made up of multiple microservices, each communicating via APIs. One service is beginning to be a bottleneck for the application because it can take a lot of time to complete requests. An engineer tried adding additional instances of this service behind the load balancer, but it did not have any effect. Which application design change must be implemented m this scenario?
Refer to the exhibit.
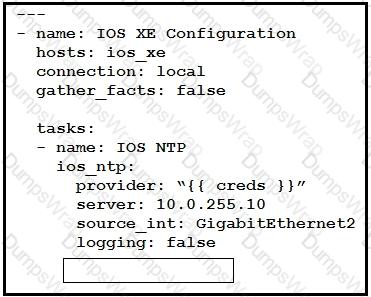
Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
Which security approach should be used for developing a REST API?
Refer to the exhibit.

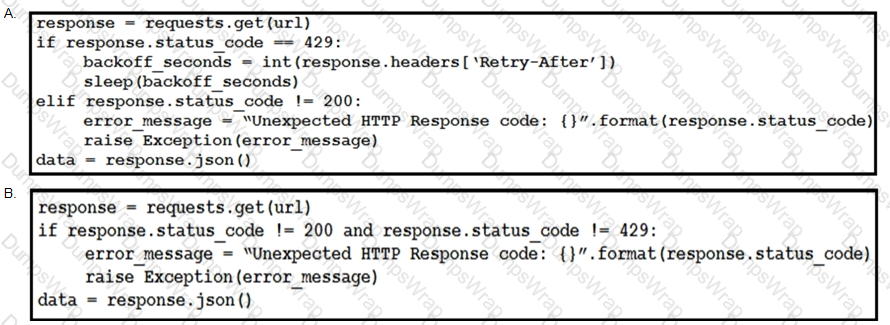
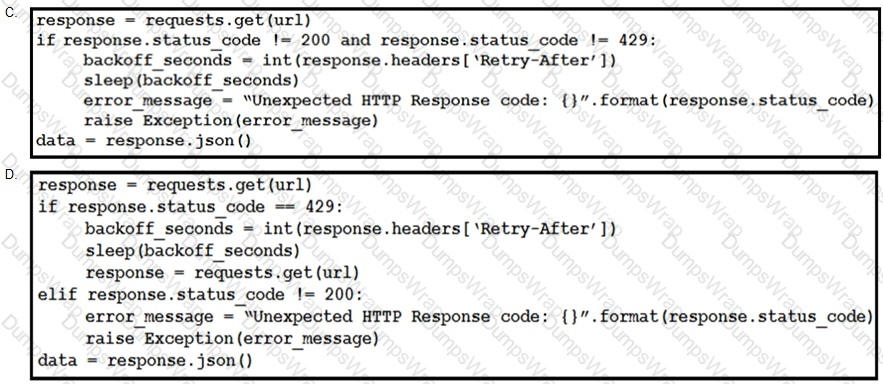
This snippet of a script has recently started exiting abnormally with an exception stating “Unexpected HTTP Response code: 429”.
Which solution handles rate limiting by the remote API?
What is a characteristic of event-driven architecture?
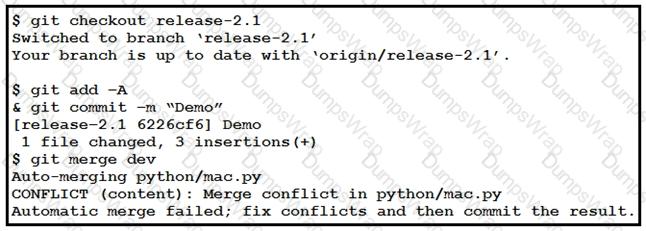
Refer to the exhibit. Which command resolves the merge conflict by removing the previous commit from the commit history?
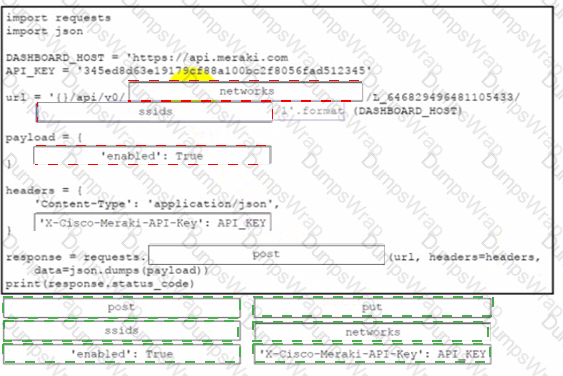
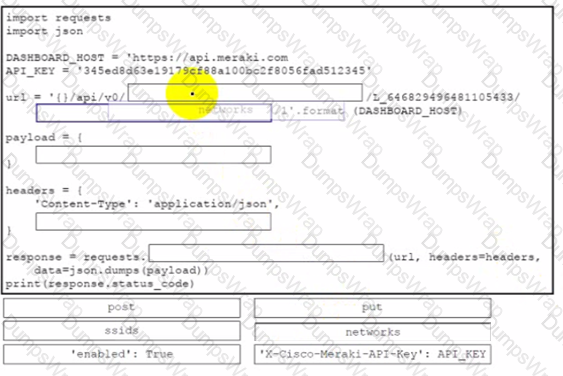
An engineer must enable an SSID in a Meraki network. Which request accomplishes this task?
An engineer is developing a Docket container for an application in Python For security reasons the application needs to be accessible on port 5001 only Which line should be added to the dockerfile m order to accomplish this?
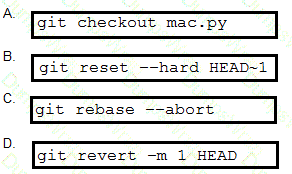
Drag and drop the code from the bottom onto the box where the code is missing to create a new IKEv2 policy Not all options are used
Refer to the exhibit.
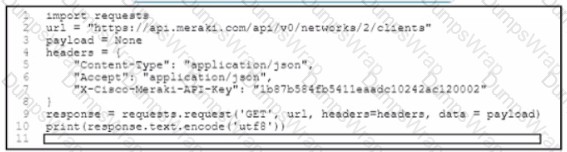
A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2 The number of client entries per returned page is restricted to 1.000 according to the API specification Network 2 has 2.500 clients What must be added where the code is missing to print the content of each response?
A)

B)

C)

D)

Refer to the exhibit.
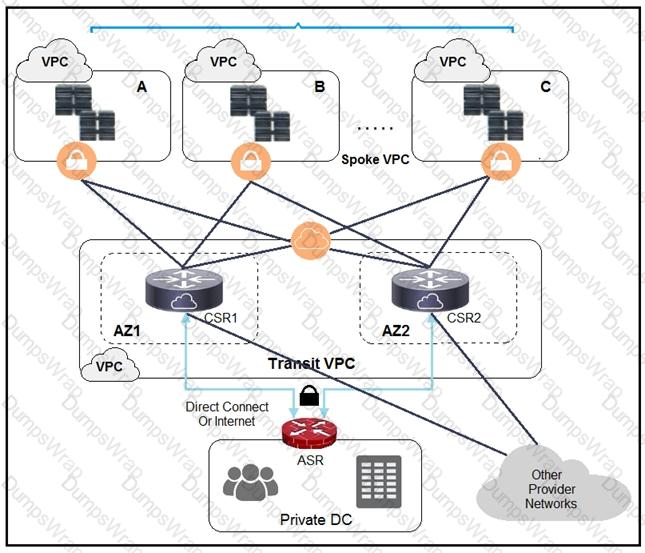
A company has extended networking from the data center to the cloud through Transit VPC.
Which two statements describe the benefits of this approach? (Choose two.)
Refer to the exhibit.
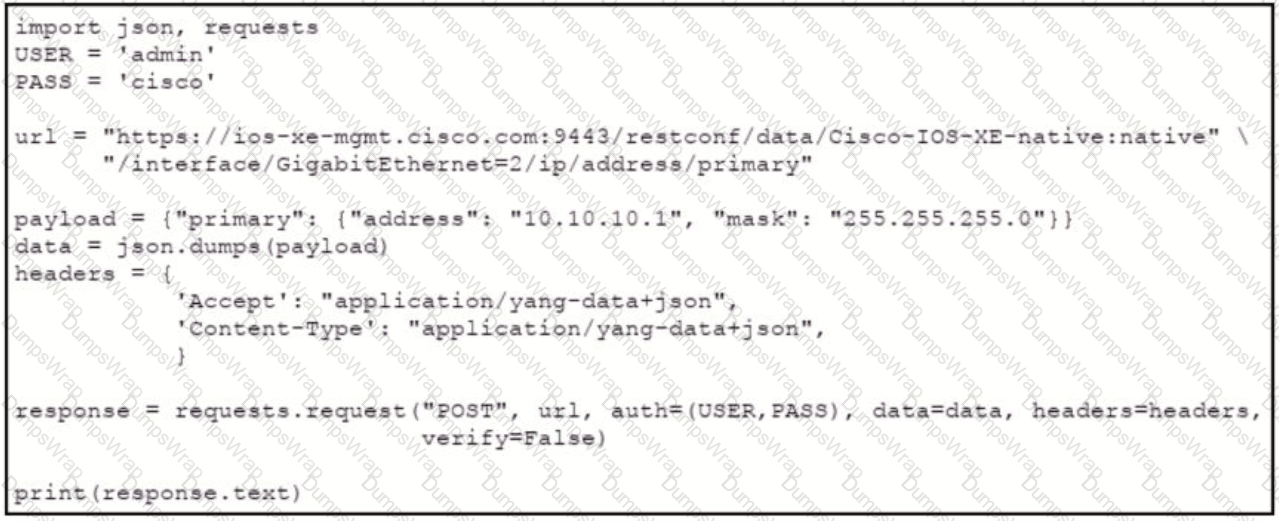
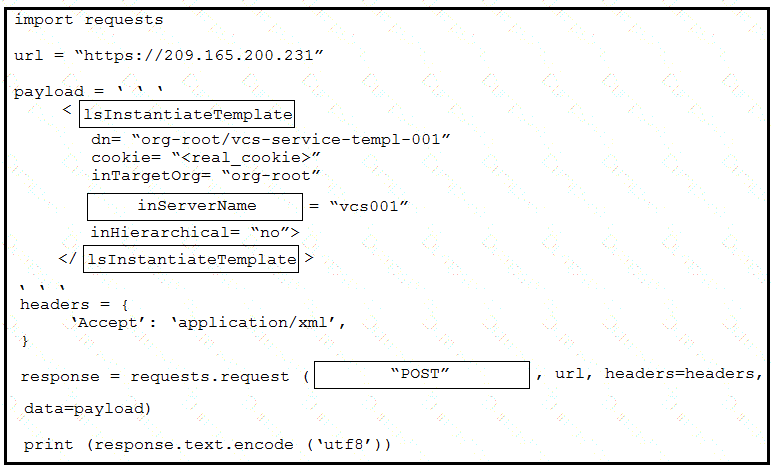
An engineer needs to change the IP address via RESTCOMF on interface GigabitEthernet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?
Which two principles are included in the codebase tenet of the 12-factor app methodology? (Choose two.)
Refer to the exhibit.
An application has been created to serve a whole enterprise. Based on use and department requirements, changes are requested on a quarterly basis. When evaluating the application design, which two actions improve code maintainability?
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
What are two benefits of using a centralized logging service? (Choose two.)
An application must be able to print the values of the variables in specific modules. Different message levels will be used for production and for development. Proof of access and activity must be documented. What must be included in the implementation to support these observability requirements?
Refer to the exhibit.
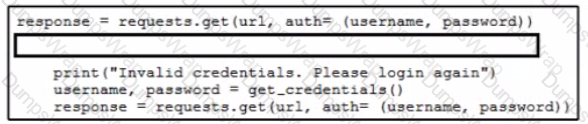
Which code snippet must be added to the blank in the code to automate the evaluation and handling of errors due to wrong credentials when Basic Authorization is used?
A)

B)

C)

D)

Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
DRAG DROP
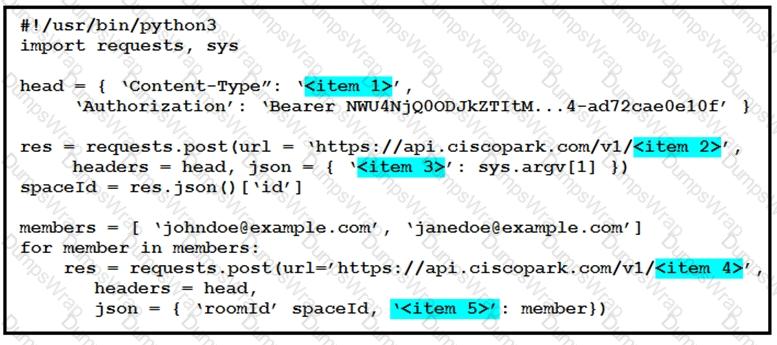
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question.
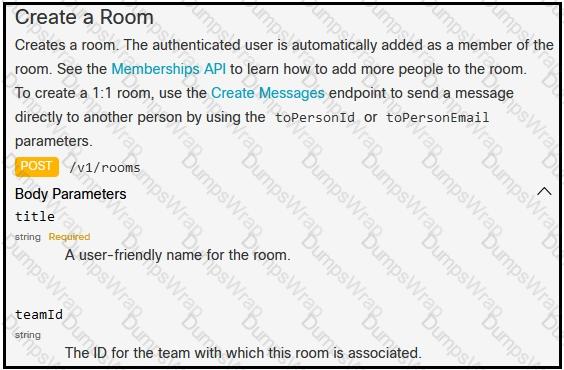

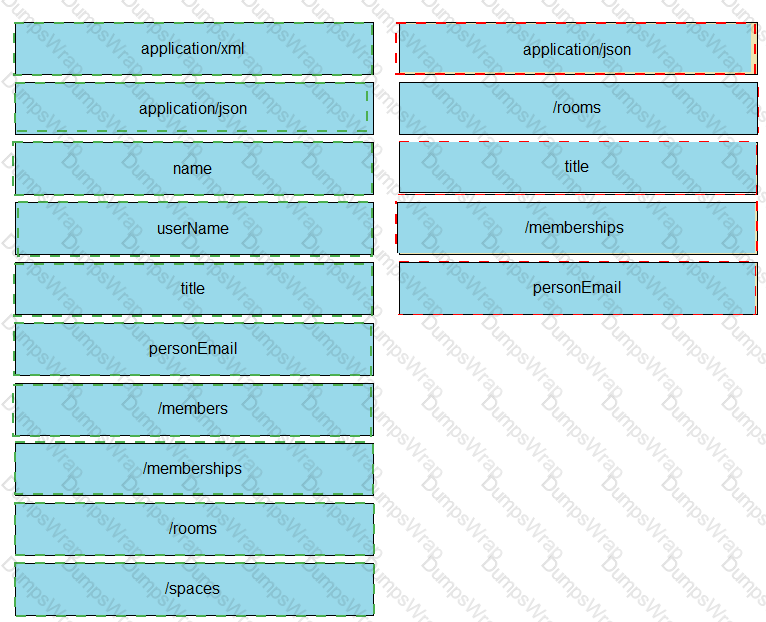
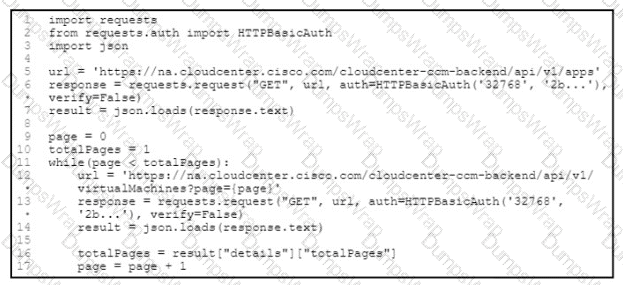
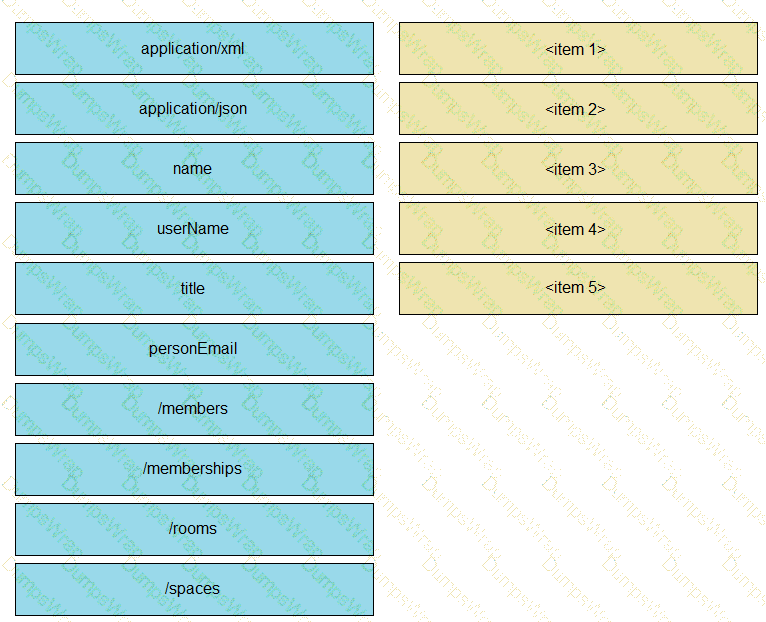
A developer is creating a Python Script that will use the Webex Teams REST API to automatically create a new collaboration space with him and his team leads on-demand via a Linux terminal command. Drag and drop the code snippets from the left onto the numbers on the right that match the missing sections in the exhibit to complete the script. Not all code snippets are used.
Which two design considerations should be considered when building a Cisco Meraki dashboard out of available APIs? (Choose two,)
Drag and drop the code from the bottom onto the box where the code is missing to enable an SSID by using the Cisco Meraki Dashboard API. Not all options are used.
Refer to the exhibit.
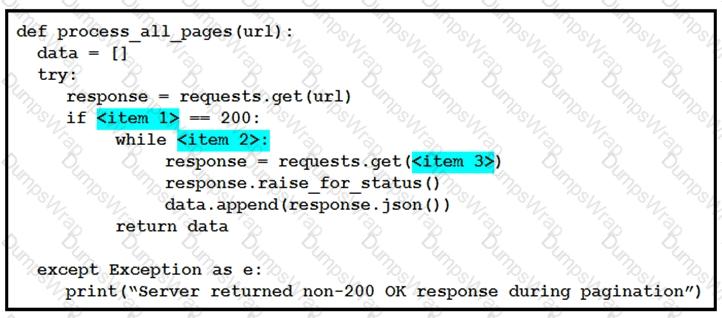
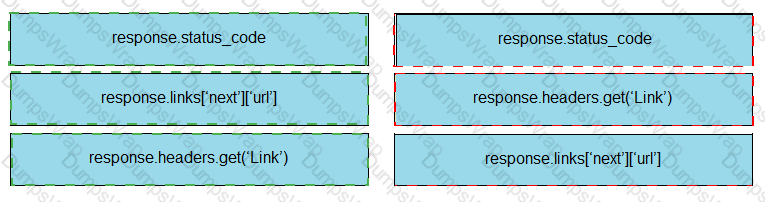
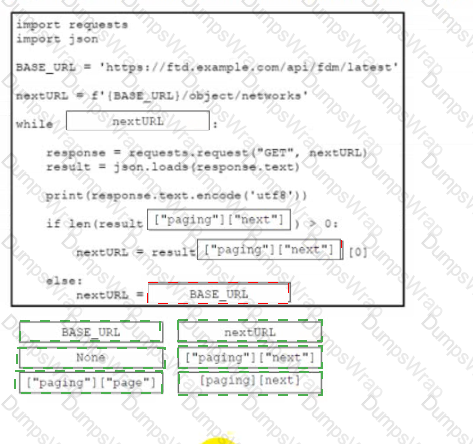
Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit that consumes REST API pagination.
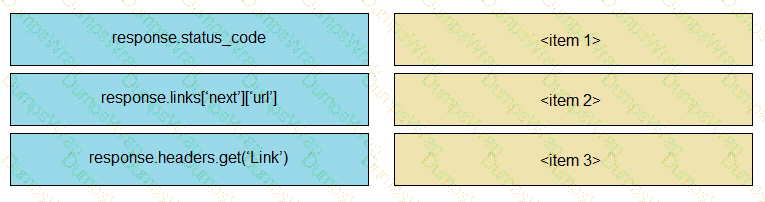
Refer to the exhibit.

A network engineer needs to handle API errors in their requests when users do not have permission to access the resource, even if they are authenticated and authorized. Which line of code needs to be placed on the snippet where the code is missing to handle these API errors?
A developer in a learn of distributed authors is working on code in an isolated Git branch named 'update4a2f5464771 The developer attempts to merge the new code with a branch named ’dvcapp2a3f1564733' however the merge operation encounters a conflict error during the process. Which Git command must the developer use to exit from the merge process and return the branch to the previous state?
An application has been developed for monitoring rooms in Cisco Webex. An engineer uses the application to
retrieve all the messages from a Cisco Webex room, but the results are slowly presented. Which action
optimizes calls to retrieve the messages from the /v1/messages endpoint?
Refer to the exhibit.
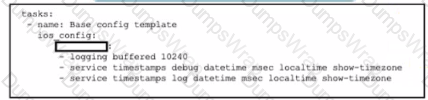
Which word is missing from this Ansible playbook shown, to allow the Cisco IOS XE commands for router configuration to be pushed after the playbook is executed?
Refer to the exhibit.
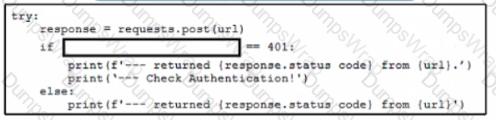
A network engineer writes a script to test authentication workflow using Python and REST API. The engineer wants to ensure that the script handles expected errors by matching output to HTTP status codes The scnpt uses the Python requests module. Which line of code must be added on the snippet where the code is missing?
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
Refer to the exhibit.

An application is being developed as an information repository. The application will be used to store details about television shows, including the scenario, year, and category. Which database type must used for high performance for the data structure?
While working with the Webex Teams API, on an application that uses end-to-end encryption, a webhook has
been received. What must be considered to read the message?
Refer to the exhibit.
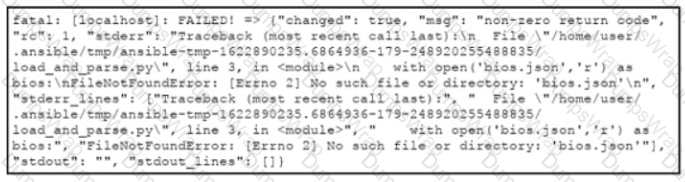
An engineer creates an application that leverages the Ansible framework to provision CPE endpoints that have configuration changes. The application contains an Ansible playbook named provision_cpes.yml that uses the ansible.builtin.script Ansible module to execute these two Python scripts:
•gather and_create.py. which creates a JSON file named bios.json that contains the CPE models and their respective IOS file information
•load and parse.py. which loads the file data and parses it for later consumption
After several successful runs, the application fails. During a review of the Ansible execution logs, the engineer discovers an error output that indicates that one of the stages failed. What is the cause of this issue?
A team is developing a cloud-native application for network monitoring and management of various devices. An increased growth rate of users is expected. The solution must be easily managed and meet these requirements:
•able to use dependencies
•easy disposability
•flexible configuration
Which application design approach must be used?
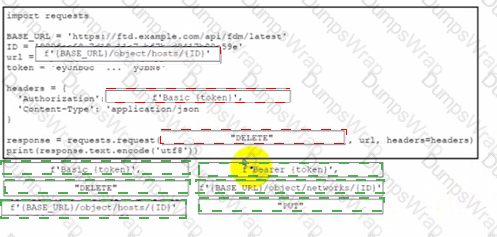
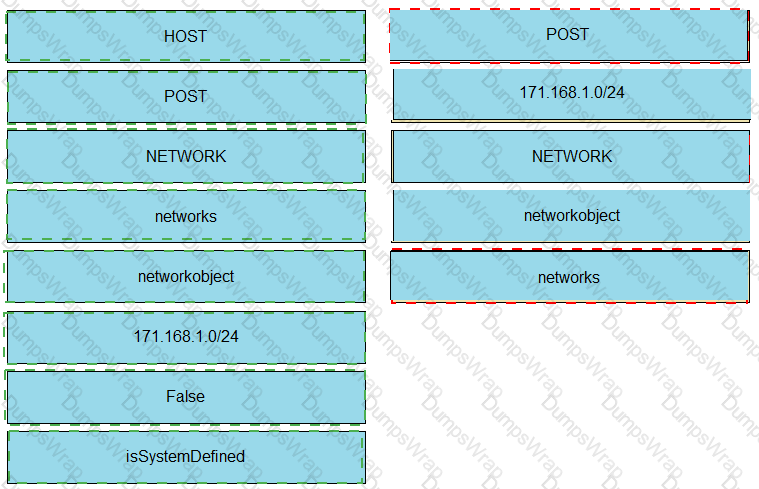
Drag and drop the code from the bottom onto the box where the code is missing to delete a host object by using the Cisco Firepower Device Manager API Not all options are used.

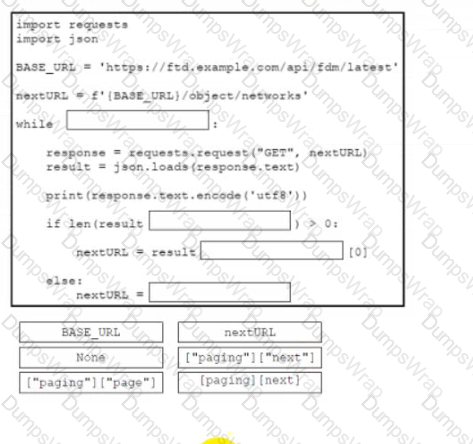
Drag and drop the code from the bottom onto the box where the code is missing to list objects that use the paginated Cisco FDM API. Some options may be used more than once. Not all options are used.
Which two statements about a stateless application are true? (Choose two.)


 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated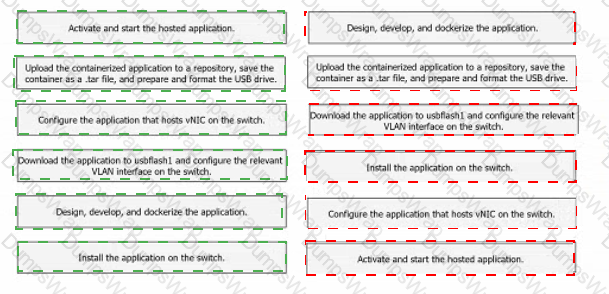

 C:\Users\wk\Desktop\mudassar\Untitled.png
C:\Users\wk\Desktop\mudassar\Untitled.png