CompTIA A+ Core 2 2025 Exam Questions and Answers
A technician needs to download and install a new web browser on a desktop. Which attribute should be used to verify the installer's authenticity?
A technician is 3-D printing high-strength, carbon fiber-based filament parts for a customer order. Which of the following is the most important for the technician to use?
A company executive is currently attending a major music festival with a large number of attendees and is having trouble accessing a work email account. The email application is not downloading emails and also appears to become stuck during connection attempts. Which of the following is most likely causing the disruption?
A technician is helping a remote user. The technician asks the user to open a specific folder on the root directory of the computer. The user cannot find a folder with that name. The technician explains that a few settings are needed to allow the folder to appear. Which of the following should the user do to be able to see the folder? (Select two).
A technician must install a legacy business application on a new computer. The new computer does not meet the application's requirements. Which of the following steps should the technician take to ensure the application installs and runs correctly?
Which of the following is used in addition to a password to implement MFA?
A technician reviews an organization's incident management policy. The organization uses a third-party vendor with multiple tools to protect its assets. What service type is this?
Which of the following provides information to employees, such as permitted activities when using the organization's resources?
An end user is unable to access the intranet. A technician needs to confirm whether the Windows web server is online and functioning. Which of the following default remote access technologies would the technician most likely use to remotely connect to the server?
A user's computer is running slowly. Web pages take several seconds to open, and applications are slow to respond. A technician opens the Windows Task Manager and sees the following:
Disk: 2%
Network: 12%
GPU: 15%
CPU: 70%
Memory: 97%
Which of the following would a technician most likely do to resolve the issue?
A user is unable to upload files to the corporate servers from their mobile phone when outside the office, but uploading files works without issue in the office. The user saw an error notification but dismissed it. Which of the following should a technician do to determine the root cause?
Which of the following describes a vulnerability that has been exploited before a patch or remediation is available?
Which of the following is the quickest way to move from Windows 10 to Windows 11 without losing data?
Due to recent security issues, the finance department requires a shorter screensaver timeout. Which of the following should a technician use to accomplish this task?
A user cannot upload files to corporate servers from their mobile device when outside the office, but uploads work fine in-office. What should a technician do to determine the root cause?
Which of the following methods would make data unrecoverable but allow the drive to be repurposed?
An organization is creating a new application. As part of the deployment, the roles and responsibilities for supporting the application need to be documented. Which of the following is designed to contain this information?
A security administrator teaches all of an organization's staff members to use BitLocker To Go. Which of the following best describes the reason for this training?
An administrator received an email stating that the OS they are currently supporting will no longer be issued security updates and patches. Which of the following is most likely the reason the administrator received this message?
A user receives a new personal computer but is unable to run an application. An error displays saying that .NET Framework 3.5 is required and not found. Which of the following actions is the best way to resolve this issue?
A technician thinks that an application a user downloaded from the internet may not be the legitimate one, even though the name is the same. The technician needs to confirm whether the application is legitimate. Which of the following should the technician do?
What is the next step a technician should take after completing malware cleanup?
The screen of a previously working computer repeatedly displays an OS Not Found error message when the computer is started. Only a USB drive, a keyboard, and a mouse are plugged into the computer. Which of the following should a technician do first?
The battery on a user’s smartphone discharges quickly during travel. The phone was replaced two weeks ago. What should the technician do first?
Why would a network engineering team provide a help desk technician with IP addresses for a wired network segment?
Performance on a user’s smartphone is degrading. Applications take a long time to start, and switching between windows also takes a long time. Which of the following diagnostic steps should a mobile technician take first?
A technician needs to install an operating system on a large number of workstations. Which of the following is the fastest method?
A user is working from home and is unable to access work files on a company laptop. Which of the following should a technician configure to fix the network access issue?
A technician is attempting to join a workstation to a domain but is receiving an error message stating the domain cannot be found. However, the technician is able to ping the server and access the internet. Given the following information:
IP Address – 192.168.1.210
Subnet Mask – 255.255.255.0
Gateway – 192.168.1.1
DNS1 – 8.8.8.8
DNS2 – 1.1.1.1
Server – 192.168.1.10
Which of the following should the technician do to fix the issue?
Which of the following methods involves requesting a user’s approval via a push notification to verify the user’s identity?
An engineer notices that many websites prompt users to input login and payment details. The engineer wants to require the browser to encrypt communications. Which of the following best helps to protect sensitive data?
An end user's laptop is having network drive connectivity issues in the office. The end user submits a help desk ticket, and a support technician is able to establish a remote connection and fix the issue. The following day, however, the network drive is disconnected again. Which of the following should the technician do next?
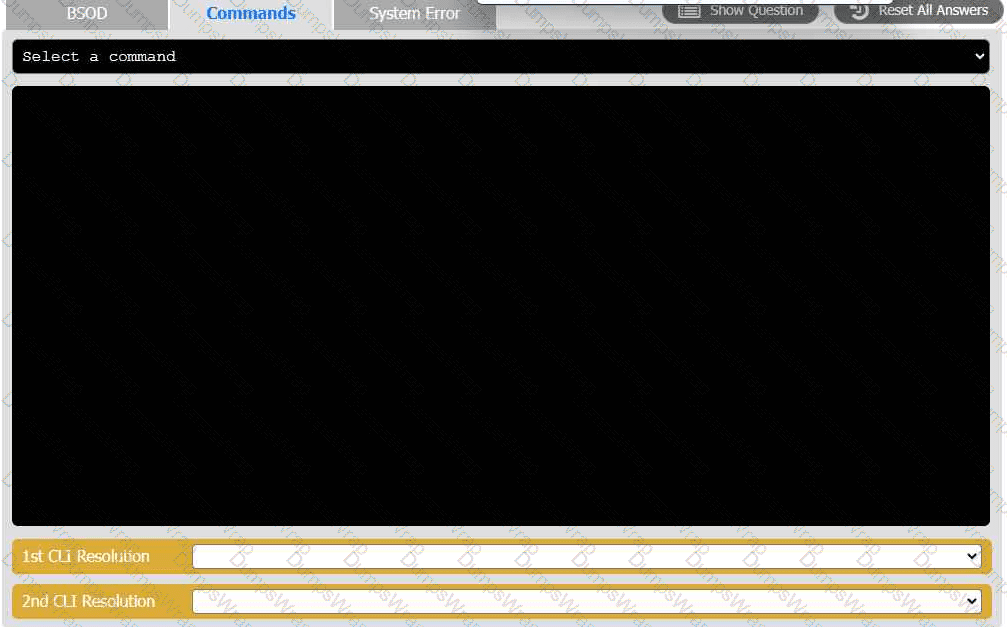
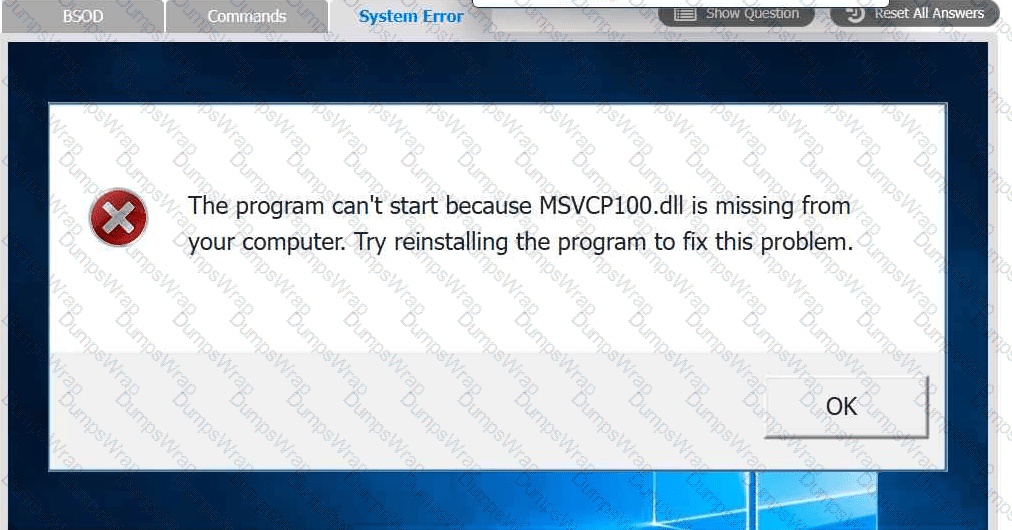
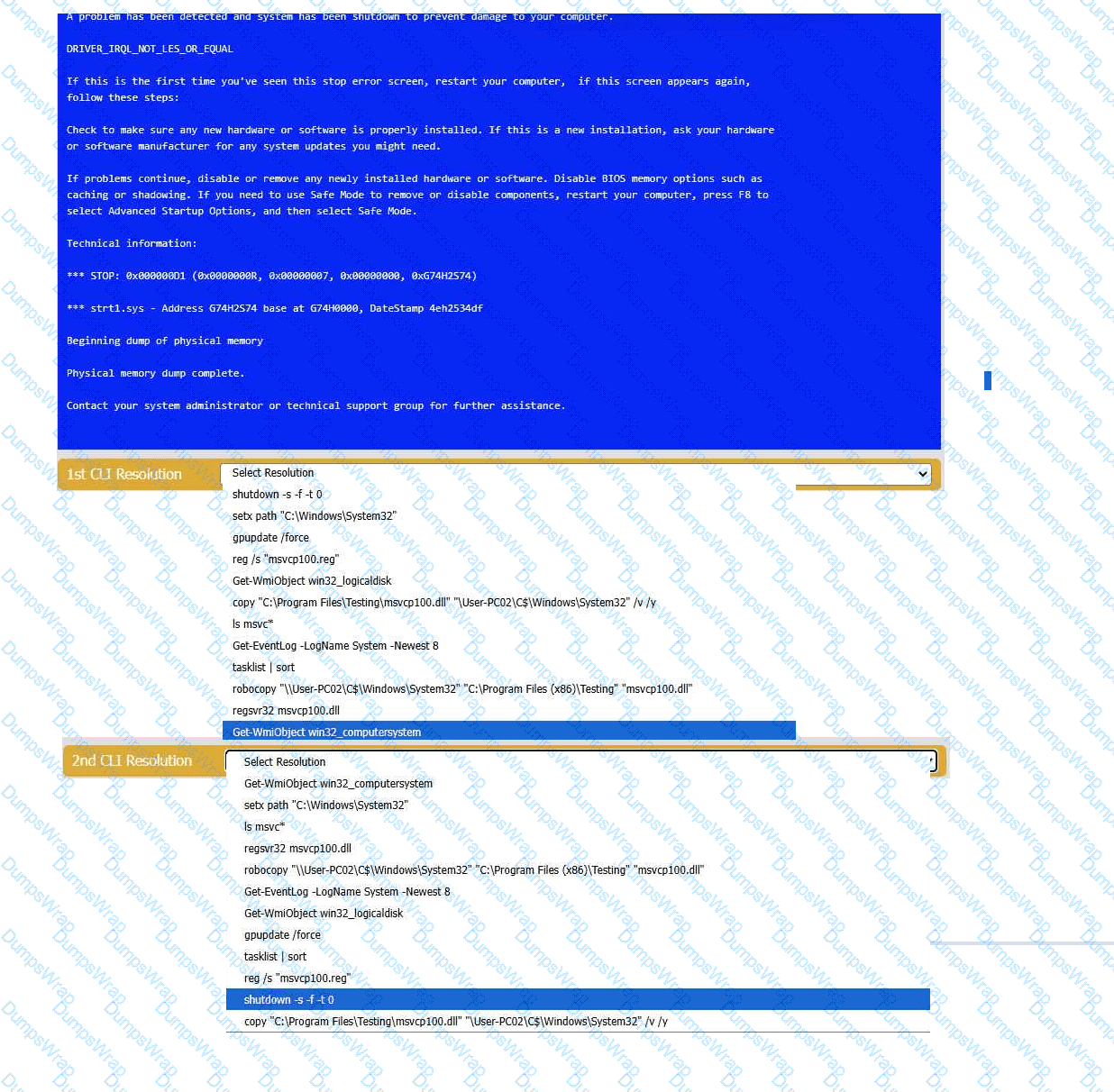
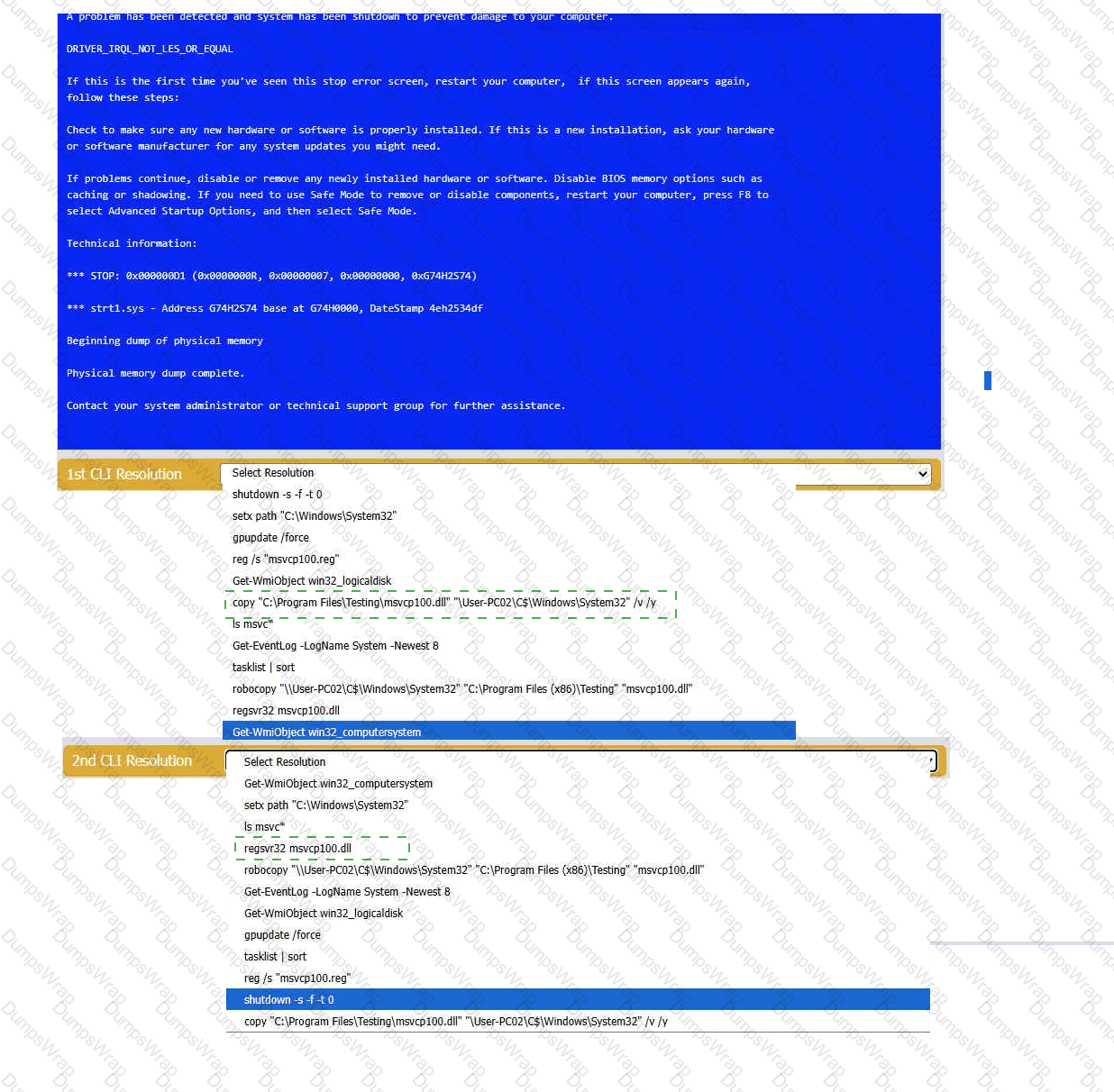
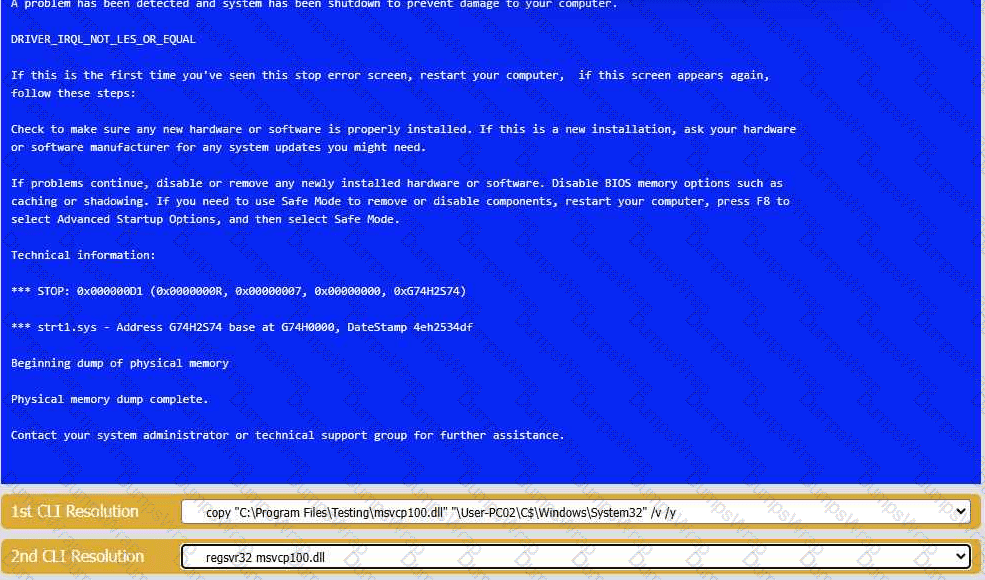
A user reports that after a recent software deployment to upgrade the Testing application, they can no longer use it. However, other employees can successfully
use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve
any issues discovered by selecting the:
· First command to resolve the issue
· Second command to resolve the issue
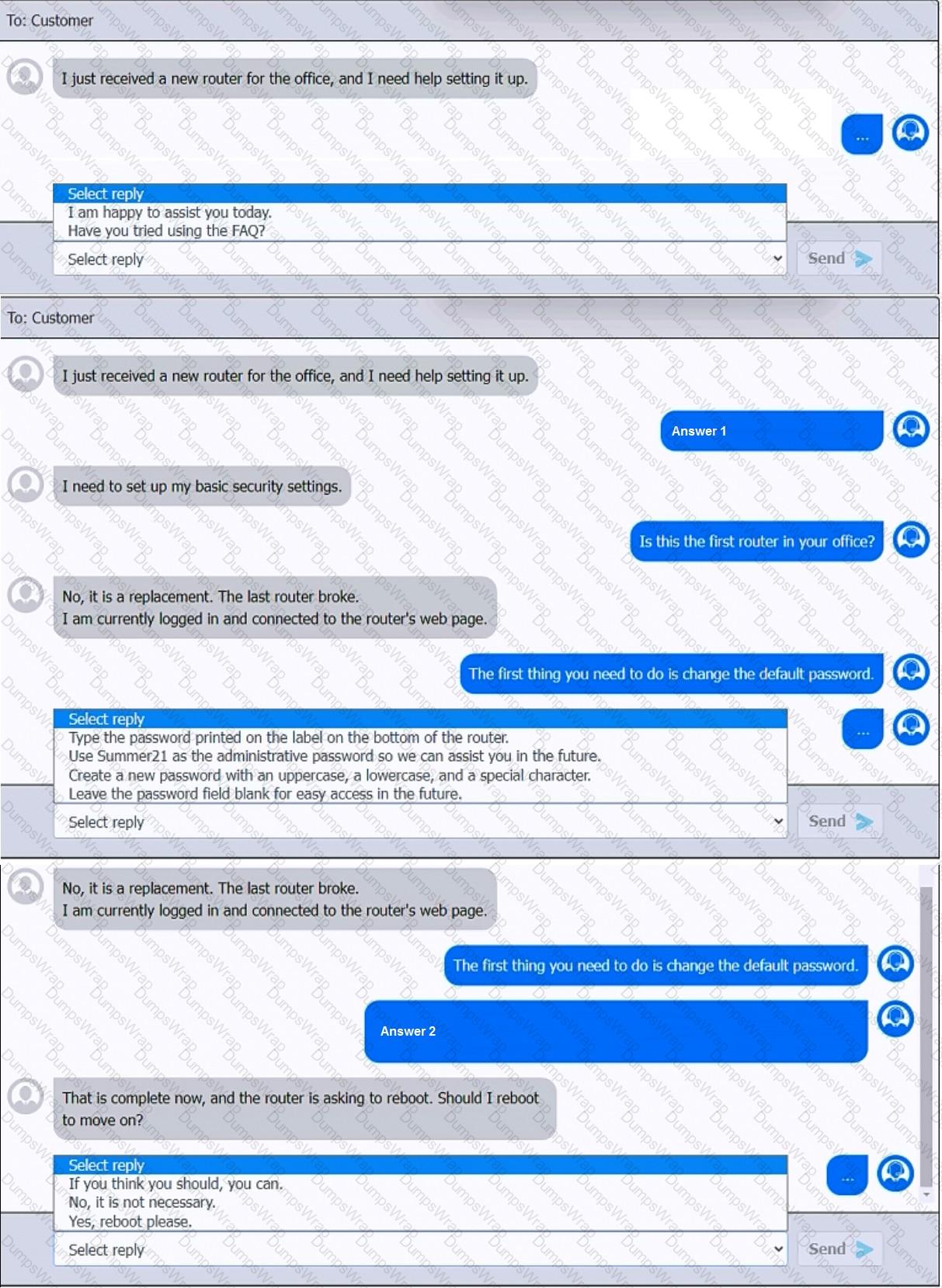
You have been contacted through the help desk chat application. A user is setting up a replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
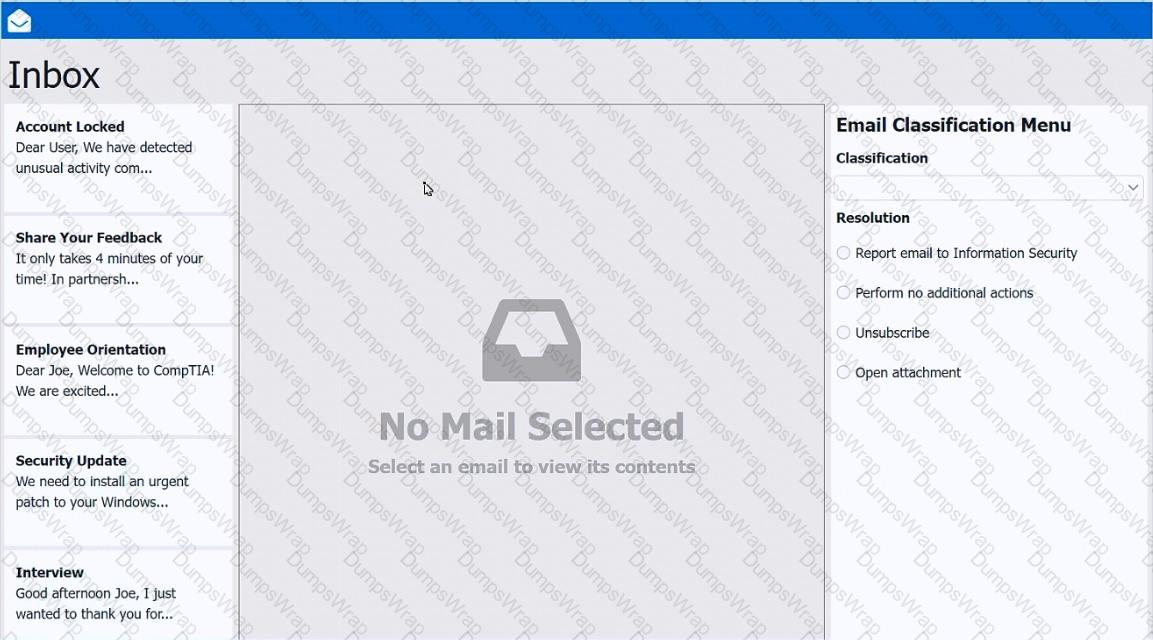
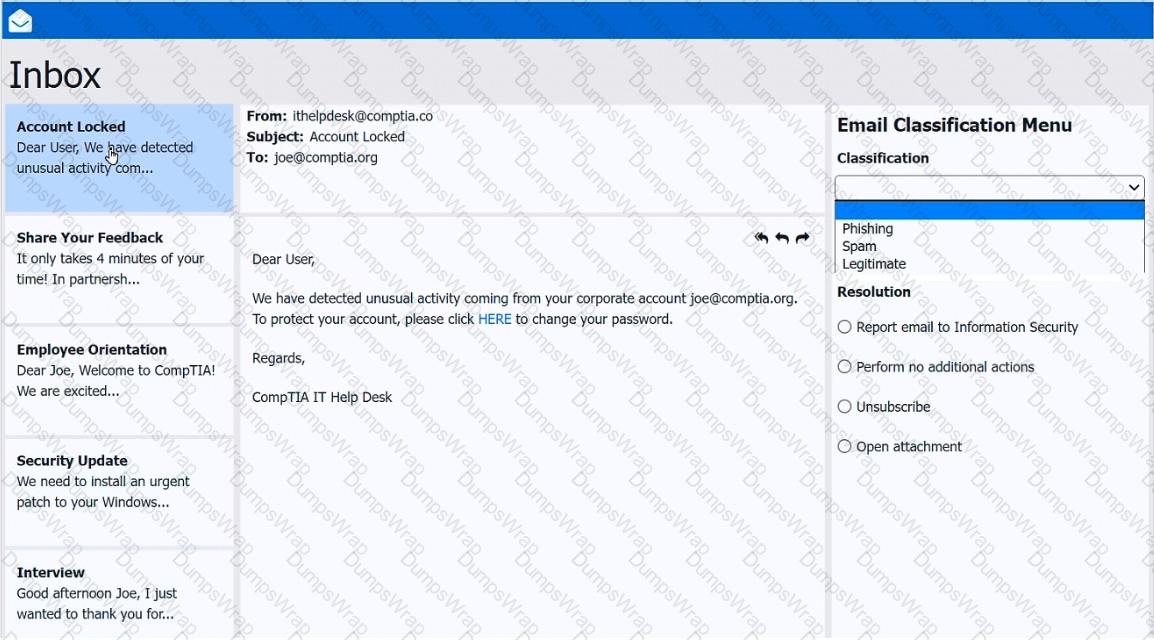
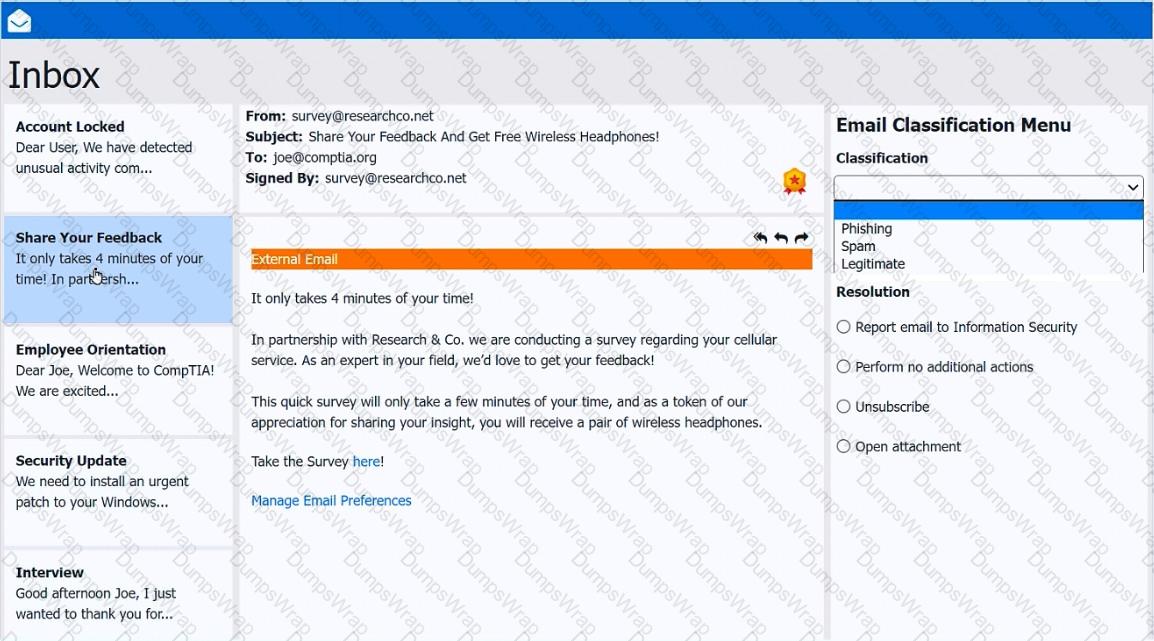
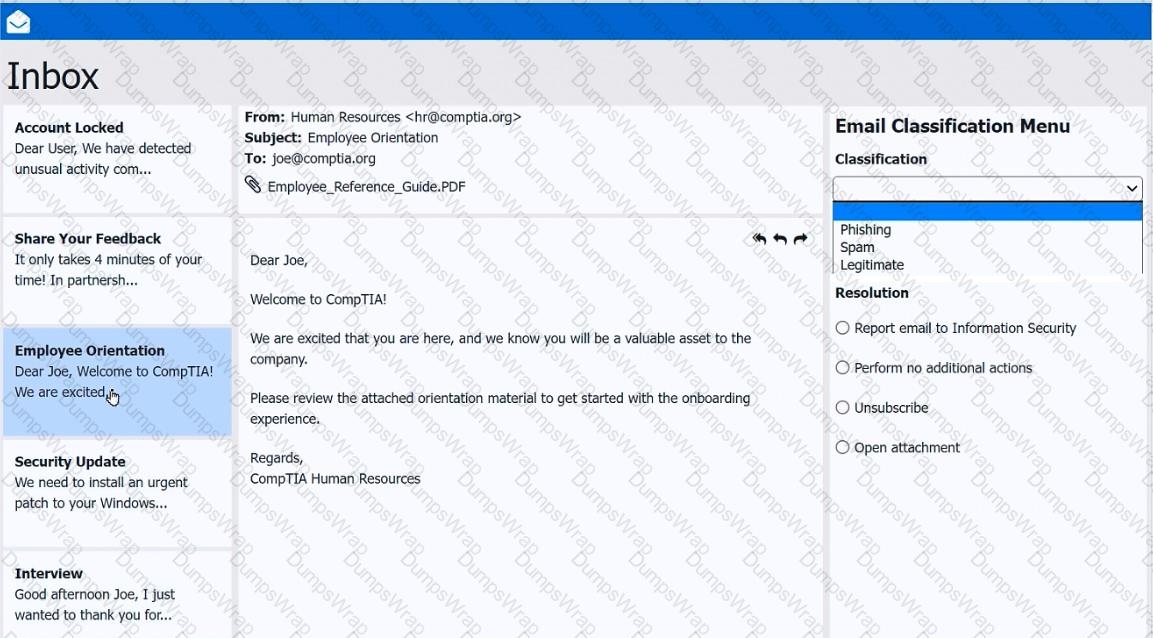
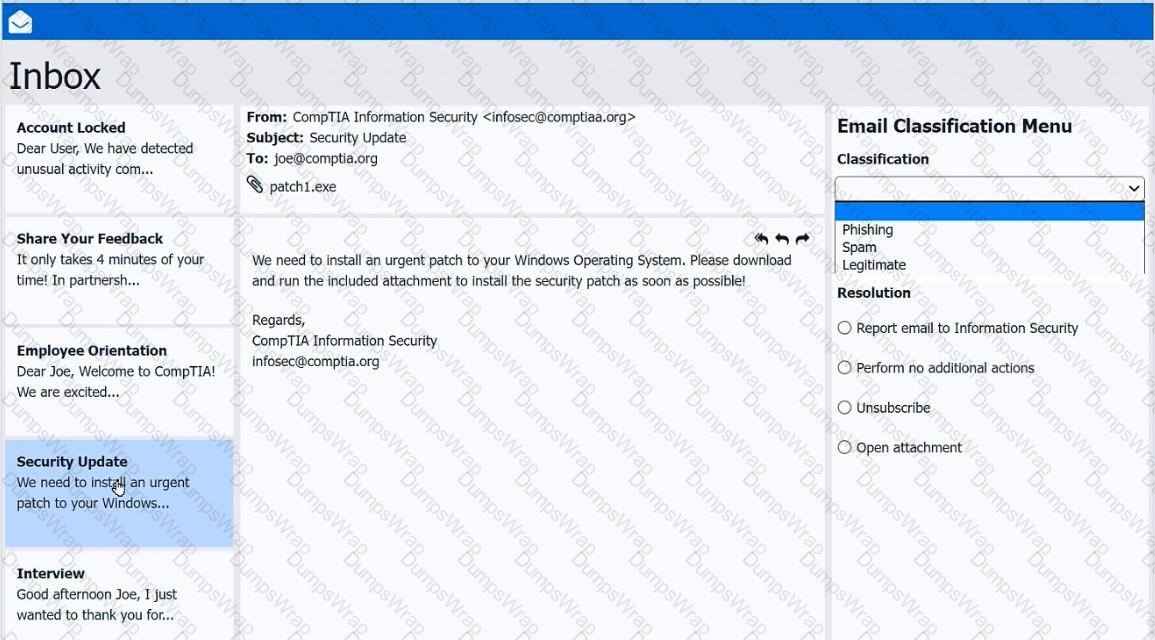
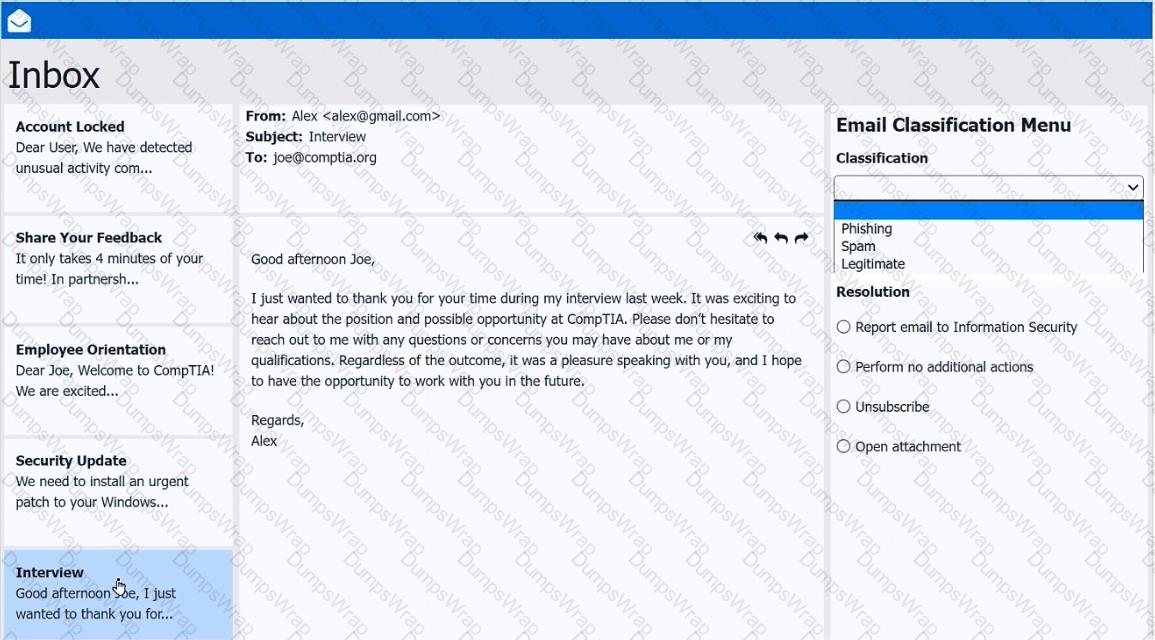
As a corporate technician, you are asked to evaluate several suspect email messages on a client's computer. Corporate policy requires the following:
>All phishing attempts must be reported.
>Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the following within the email:
>Classify the emails
>Identify suspicious items, if applicable, in each email
>Select the appropriate resolution
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
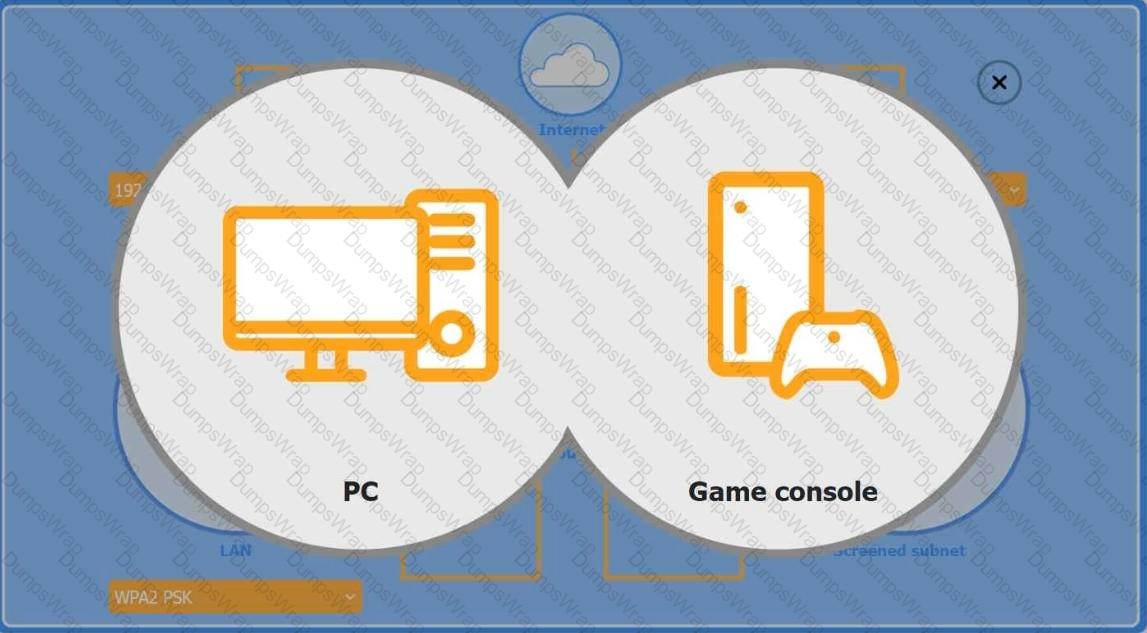
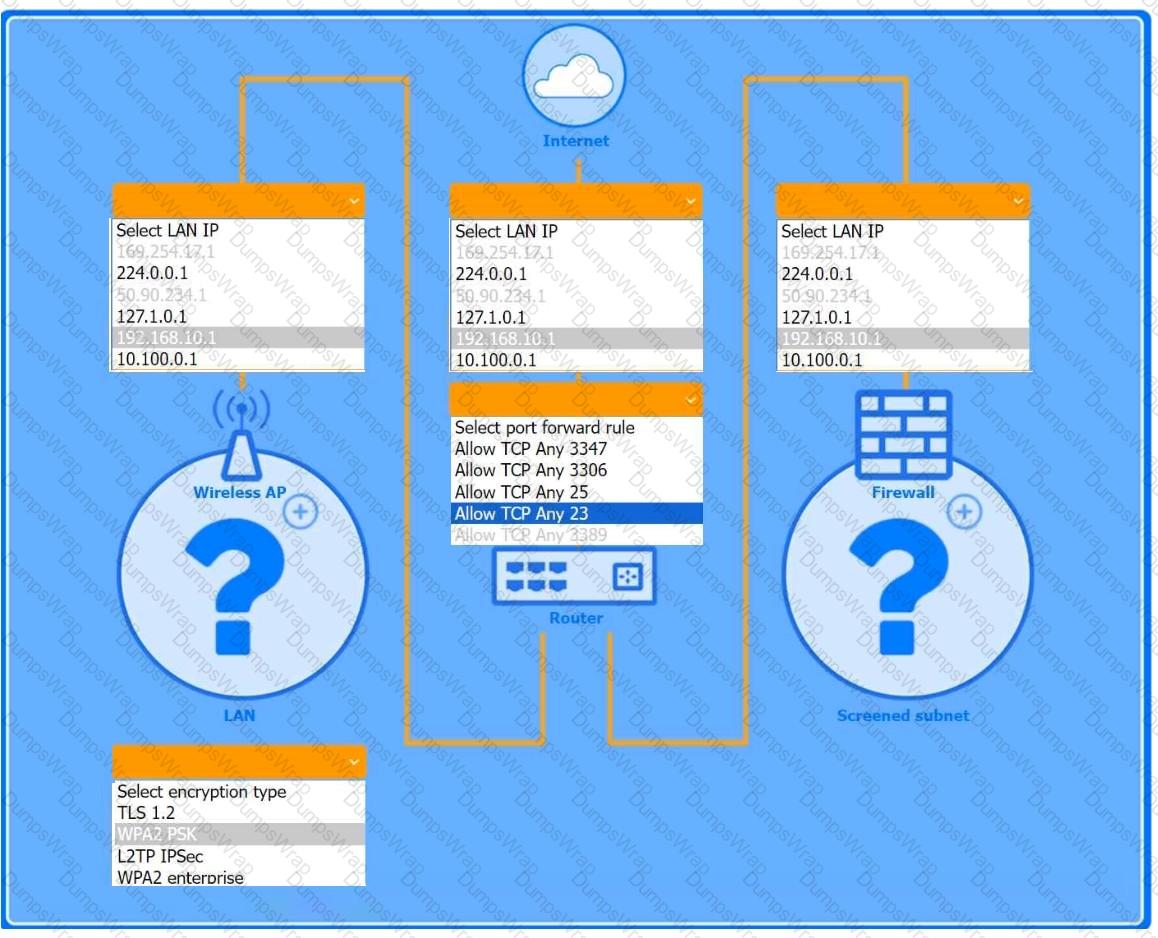
You are configuring a home network for a customer. The customer has requested the ability to access a Windows PC remotely, and needs all chat and optional functions to work in their game console.
INSTRUCTIONS
Use the drop-down menus to complete the network configuration for the customer. Each option may only be used once, and not all options will be used.
Then, click the + sign to place each device in its appropriate location.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Wireless AP LAN
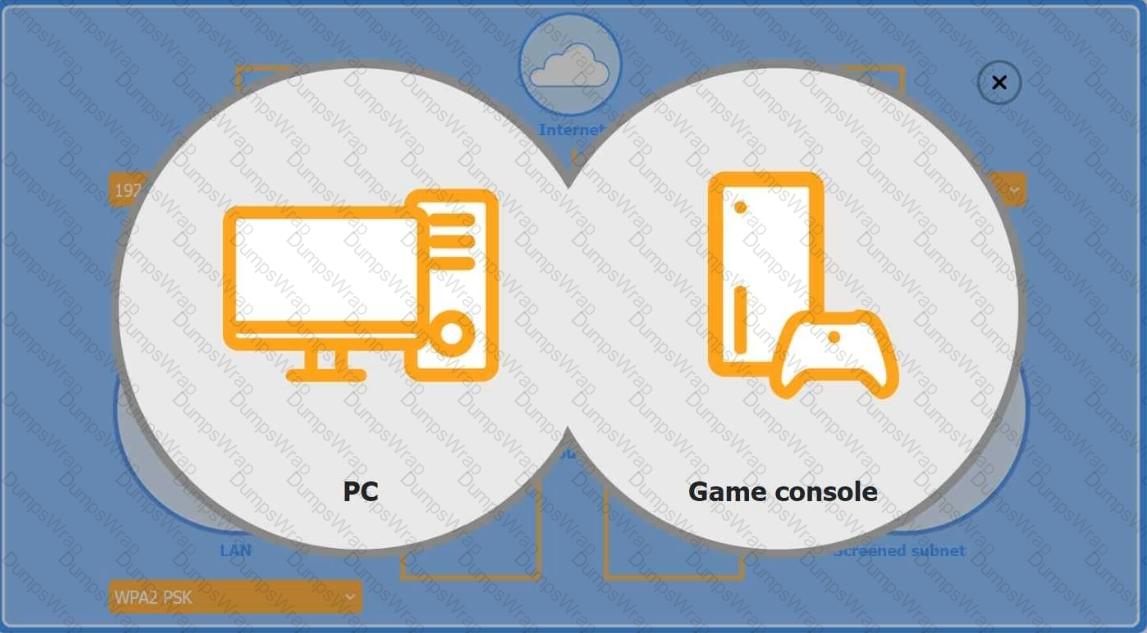
Firewall Screened Subnet
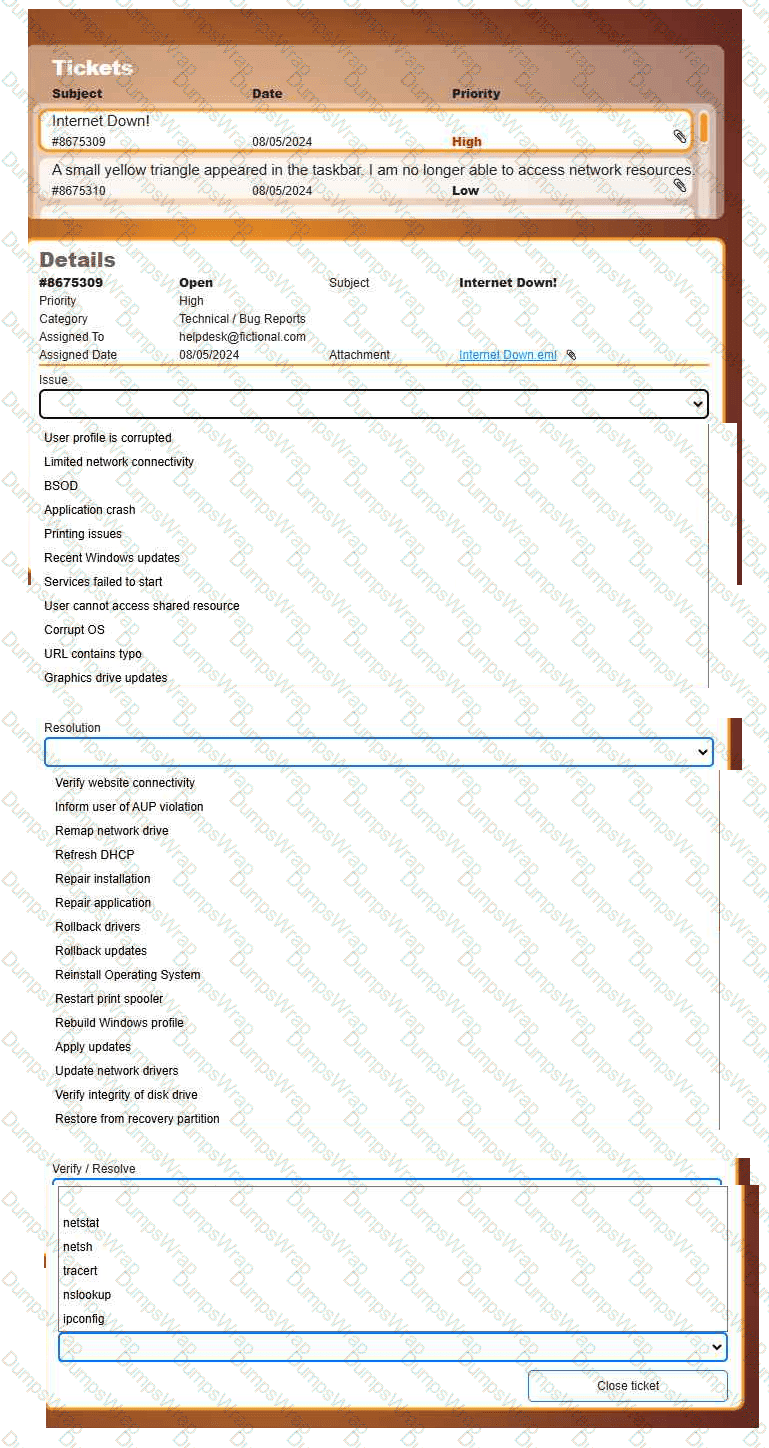
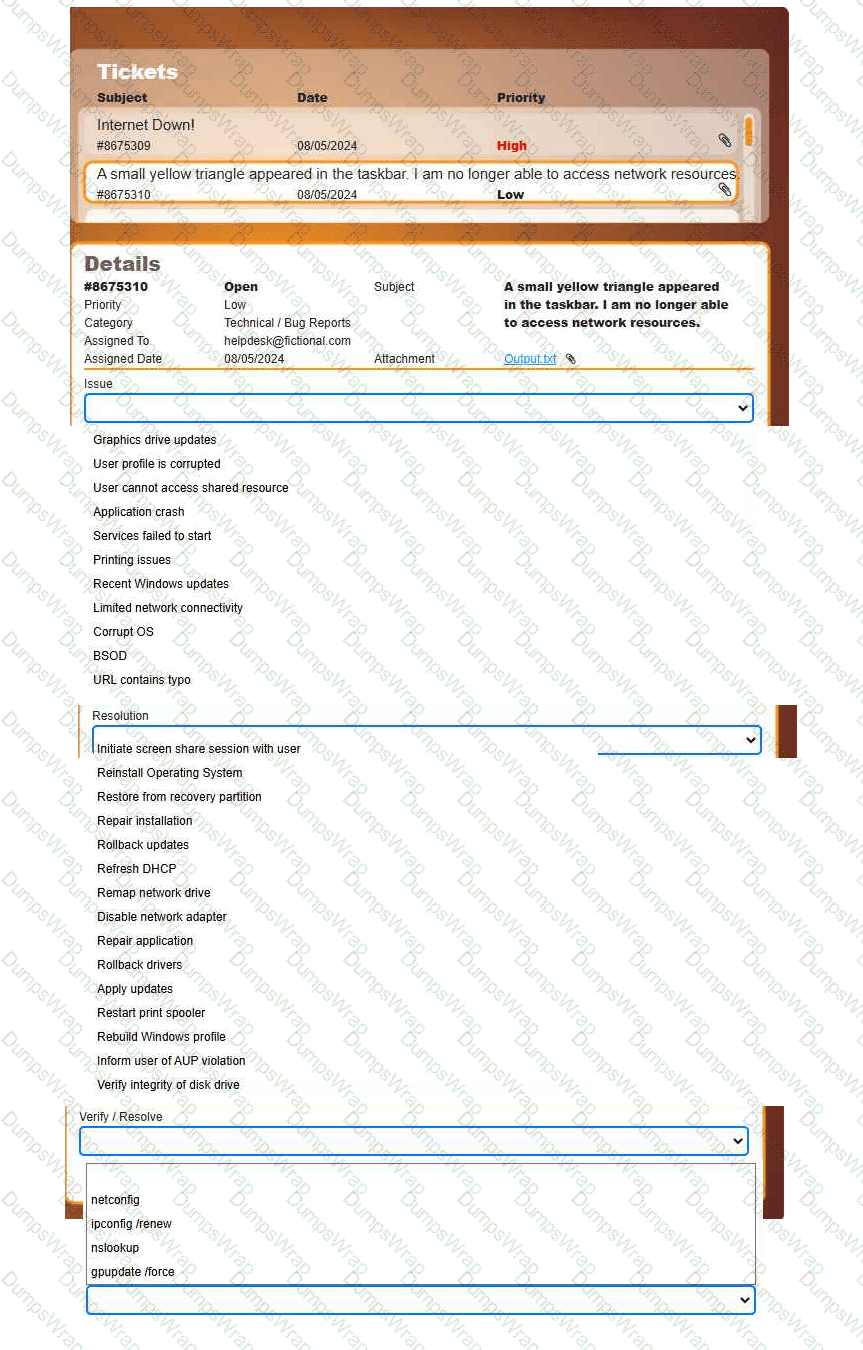
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
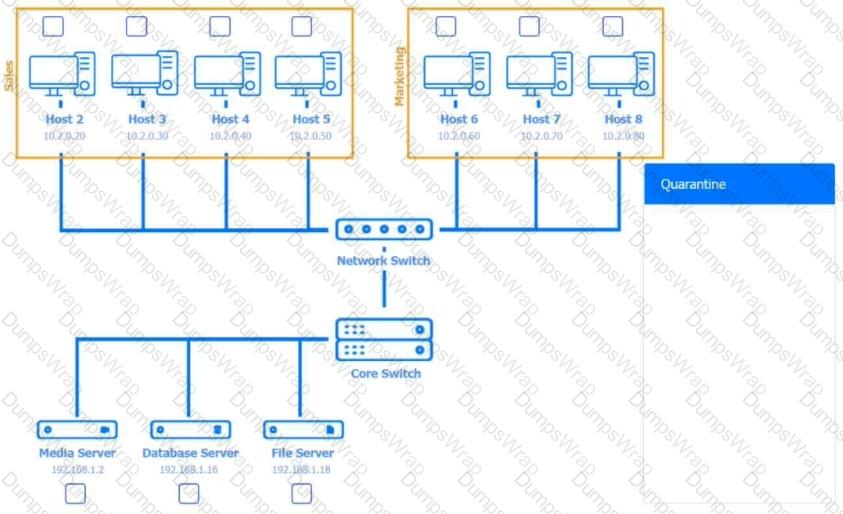
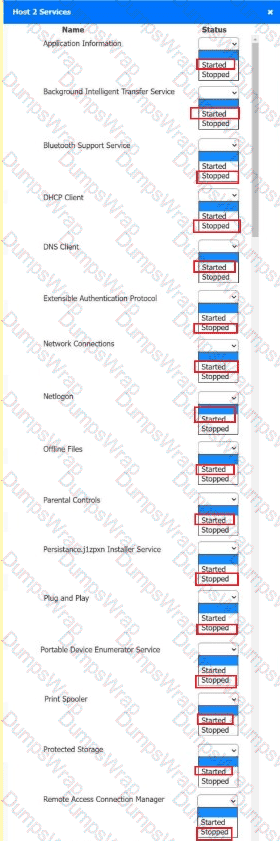
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users’ audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
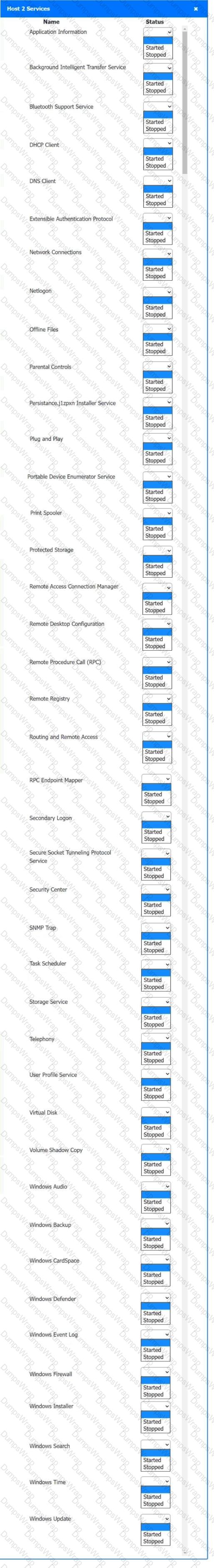
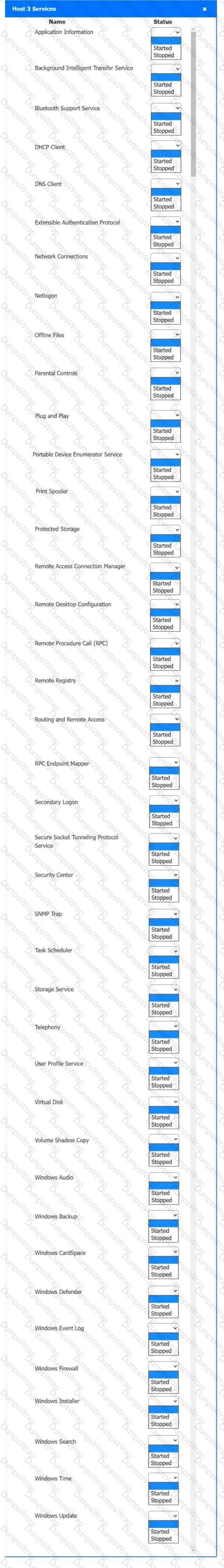
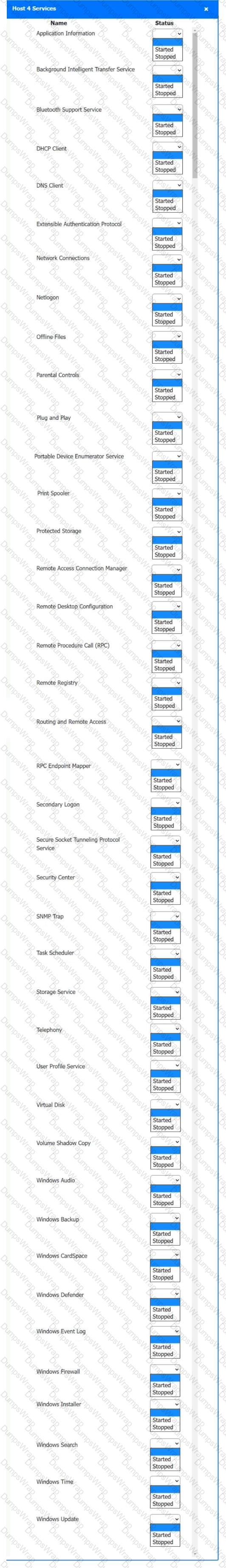
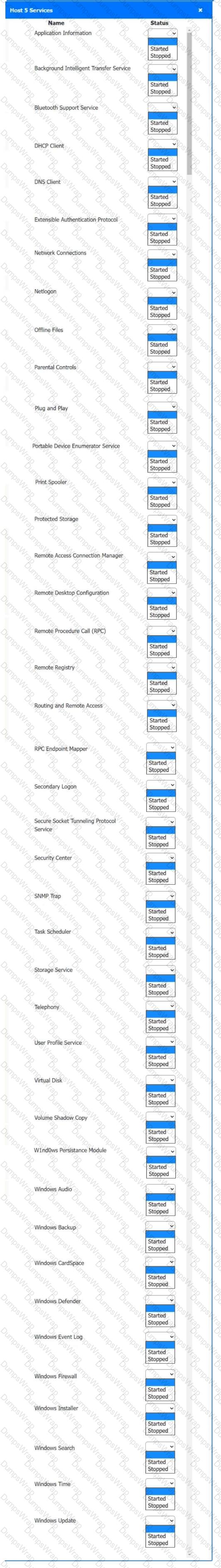
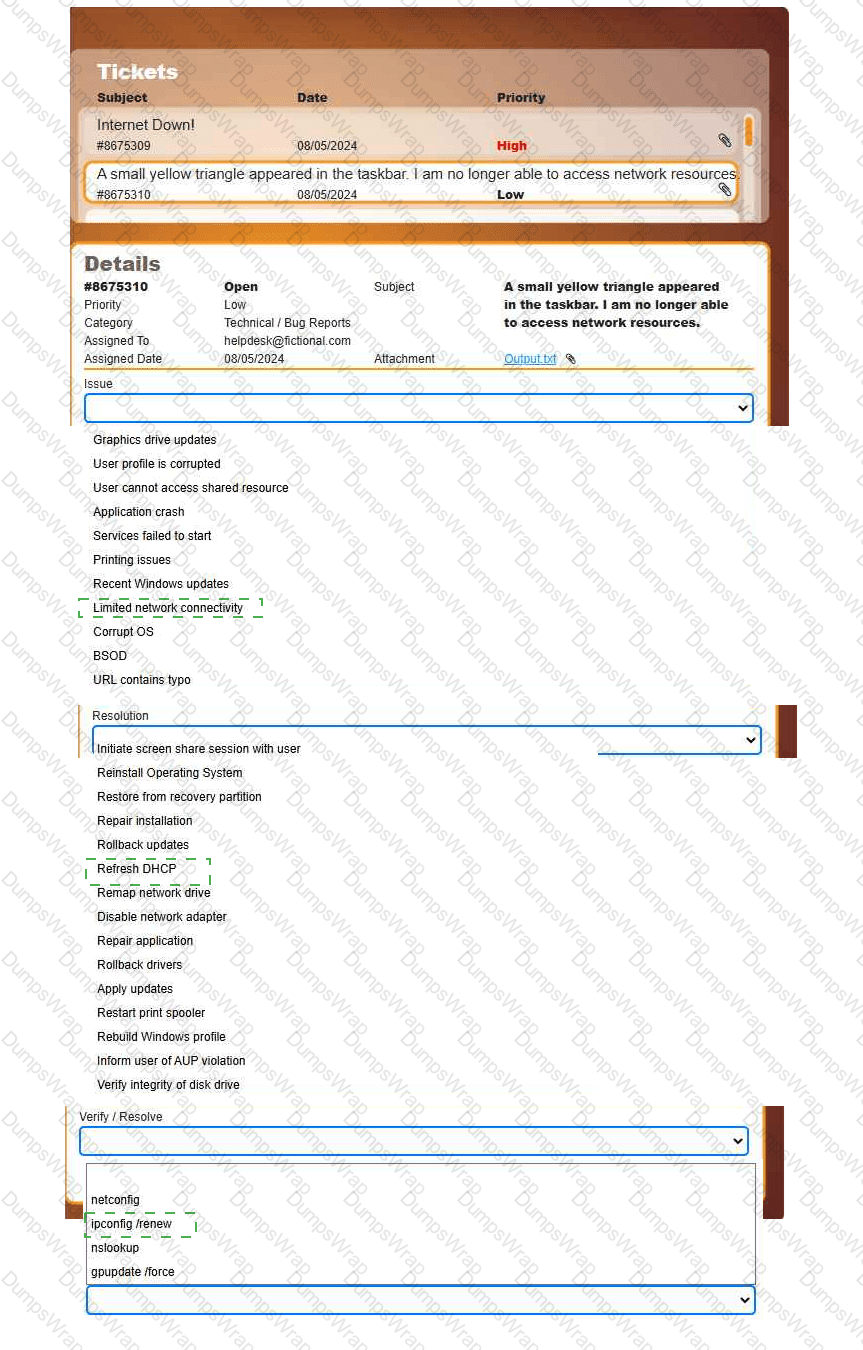
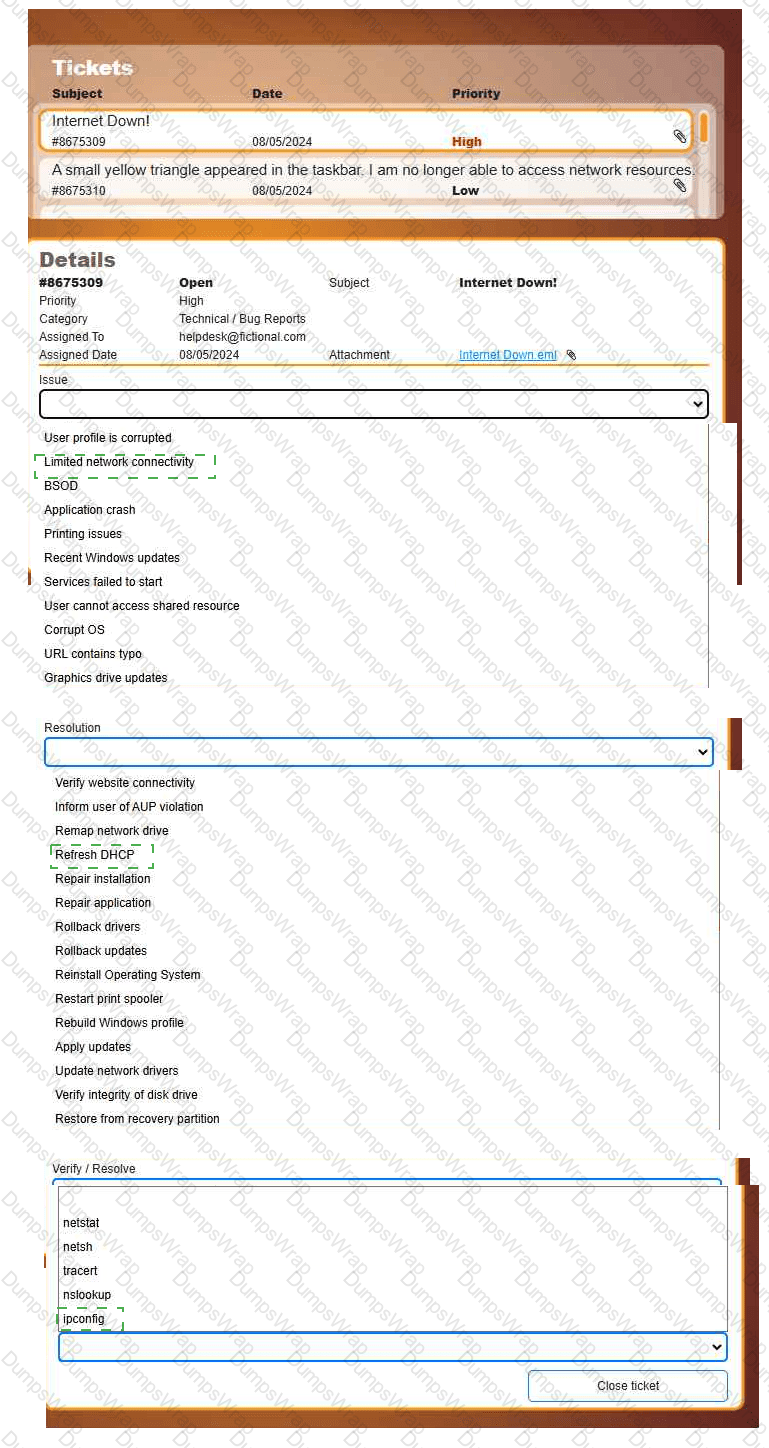
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.

 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect. A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.