CompTIA SecurityX Certification Exam Questions and Answers
The identity and access management team is sending logs to the SIEM for continuous monitoring. The deployed log collector isforwarding logs to
the SIEM. However, only false positive alerts are being generated. Which of the following is the most likely reason for the inaccurate alerts?
Source code snippets for two separate malware samples are shown below:
Sample 1:
knockEmDown(String e) {
if(target.isAccessed()) {
target.toShell(e);
System.out.printIn(e.toString());
c2.sendTelemetry(target.hostname.toString + " is " + e.toString());
} else {
target.close();
}
}
Sample 2:
targetSys(address a) {
if(address.islpv4()) {
address.connect(1337);
address.keepAlive("paranoid");
String status = knockEmDown(address.current);
remote.sendC2(address.current + " is " + status);
} else {
throw Exception e;
}
}
Which of the following describes the most important observation about the two samples?
Which of the following is the main reason quantum computing advancements are leading companies and countries to deploy new encryption algorithms?
A senior security engineer flags the following log file snippet as having likely facilitated an attacker’s lateral movement in a recent breach:
qry_source: 19.27.214.22 TCP/53
qry_dest: 199.105.22.13 TCP/53
qry_type: AXFR
| in comptia.org
------------ directoryserver1 A 10.80.8.10
------------directoryserver2 A 10.80.8.11
------------ directoryserver3 A 10.80.8.12
------------ internal-dns A 10.80.9.1
----------- www-int A 10.80.9.3
------------ fshare A 10.80.9.4
------------ sip A 10.80.9.5
------------ msn-crit-apcs A 10.81.22.33
Which of the following solutions, if implemented, would mitigate the risk of this issue reoccurring?
A security architect is performing threat-modeling activities related to an acquired overseas software company that will be integrated with existing products and systems Once its software is integrated, the software company will process customer data for the acqumng company Given the following:
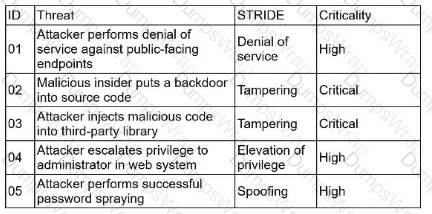
Which of the following mitigations would reduce the risk of the most significant threats?
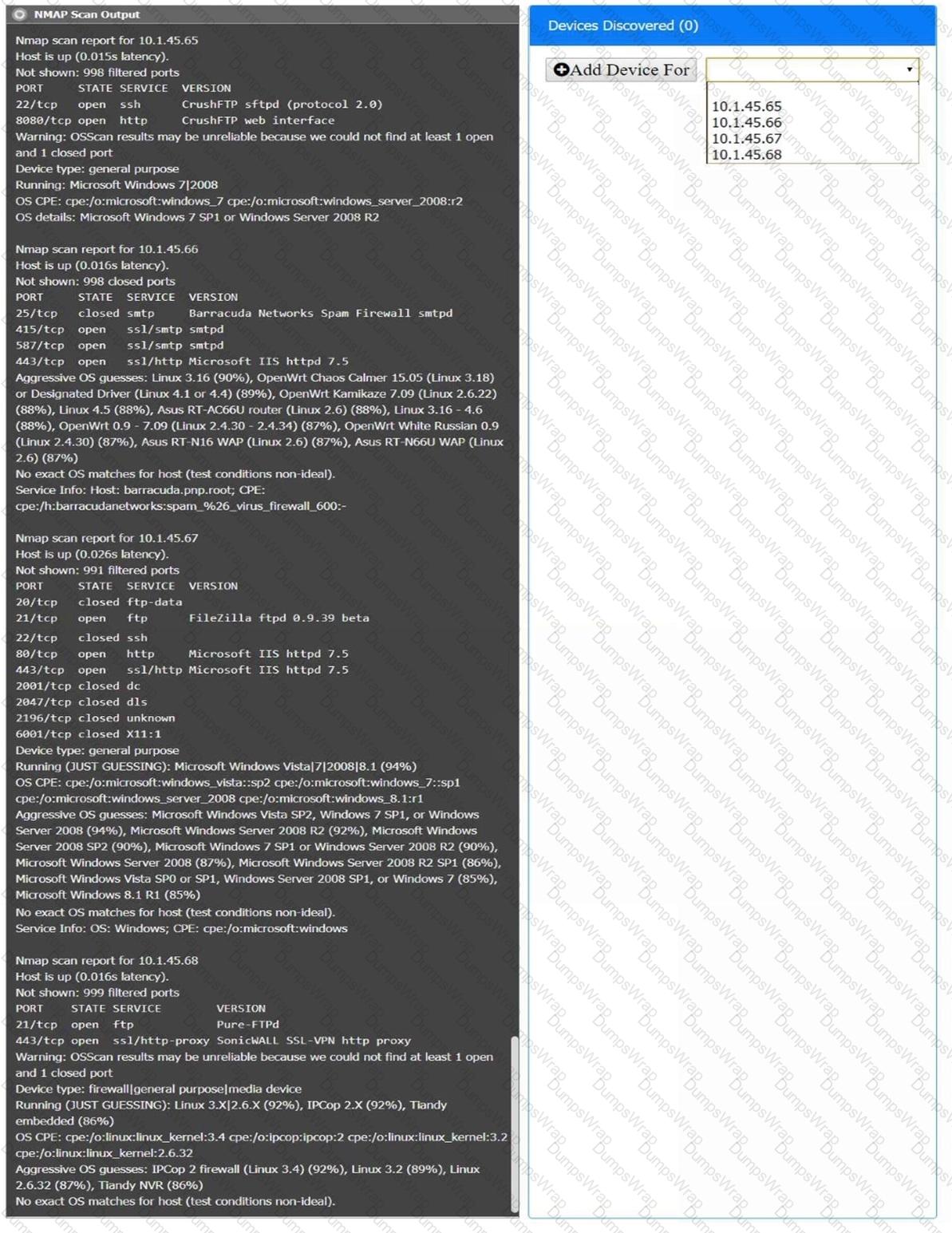
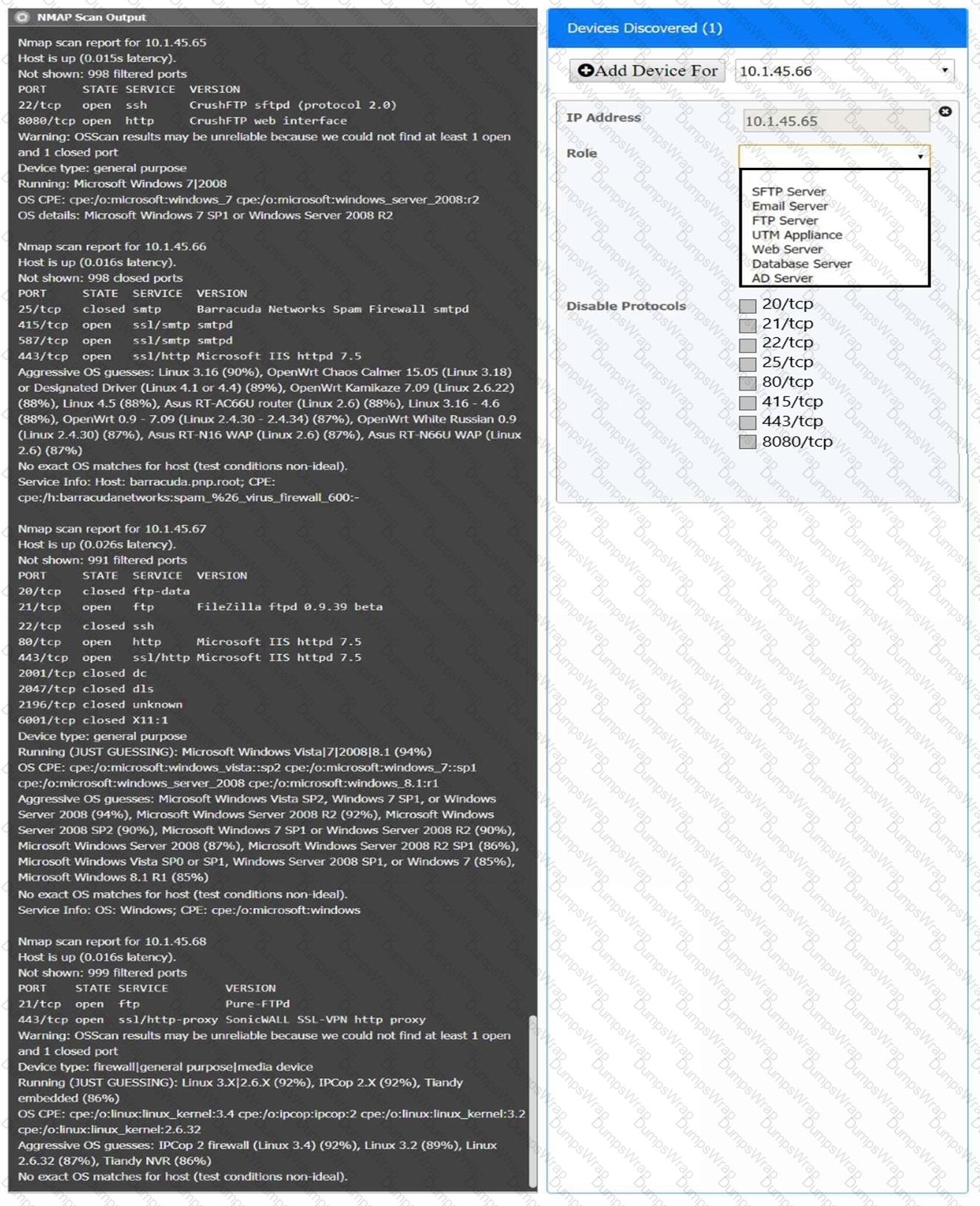
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A security professional is investigating a trend in vulnerability findings for newly deployed cloud systems Given the following output:
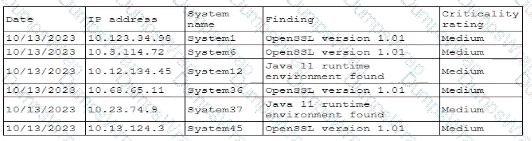
Which of the following actions would address the root cause of this issue?
After some employees were caught uploading data to online personal storage accounts, a company becomes concerned about data leaks related to sensitive, internal documentation. Which of the following would the company most likely do to decrease this type of risk?
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
A vulnerability scan was performed on a website, and the following encryption suites were found:

Which of the following actions will remediate the vulnerability?
Which of the following best explains the importance of determining organization risk appetite when operating with a constrained budget?
Embedded malware has been discovered in a popular PDF reader application and is currently being exploited in the wild. Because the supply chain was compromised, this malware is present in versions 10.0 through 10.3 of the software's official versions. The malware is not present in version 10.4.
Since the details around this malware are still emerging, the Chief Information Security Officer has asked the senior security analyst to collaborate with the IT asset inventory manager to find instances of the installed software in order to begin response activities. The asset inventory manager has asked an analyst to provide a regular expression that will identify the affected versions. The software installation entries are formatted as follows:
Reader 10.0
Reader 10.1
Reader 10.2
Reader 10.3
Reader 10.4
Which of the following regular expression entries will accuratelyidentify all the affected versions?
An external threat actor attacks public infrastructure providers. In response to the attack and during follow-up activities, various providers share information obtained during response efforts. After the attack, energy sector companies share their status and response data:
Company
SIEM
UEBA
DLP
ISAC Member
TIP Integration
Time to Detect
Time to Respond
1
Yes
No
Yes
Yes
Yes
10 minutes
20 minutes
2
Yes
Yes
Yes
Yes
No
20 minutes
40 minutes
3
Yes
Yes
No
No
Yes
12 minutes
24 minutes
Which of thefollowing is the most important issue to address to defend against future attacks?
An organization recently migrated data to a new file management system. The architect decides to use a discretionary authorization model on the new system. Which of the following best explains the architect's choice?
A company wants to protect against the most common attacks and rapidly integrate with different programming languages. Which of the following technologies is most likely to meet this need?
A company plans to deploy a new online application that provides video training for its customers. As part of the design, the application must be:
• Fast for all users
• Available for users worldwide
• Protected against attacks
Which of the following are the best components the company should use to meet these requirements? (Select two).
A security engineer needs to remediate a SWEET32 vulnerability in an OpenSSH-based application and review existing configurations. Which of the following should the security engineer do? (Select two.)
An incident response analyst finds the following content inside of a log file that was collected from a compromised server:
.2308464678 ... whoami ..... su2032829%72%322/// ...... /etc/passwd .... 2087031731467478432 ...
$6490/90/./ ..< XML ?.. .... nty.
Which of the following is the best action to prevent future compromise?
A company undergoing digital transformation is reviewing the resiliency of a CSP and is concerned about meeting SLA requirements in the event of a CSP incident. Which of the following would be best to proceed with the transformation?
An organization recently implemented a new email DLP solution. Emails sent from company email addresses to matching personal email addresses generated a large number of alerts, but the content of the emails did not include company data. The security team needs to reduce the number of emails sent without blocking all emails to common personal email services. Which of the following should the security team implement first?
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
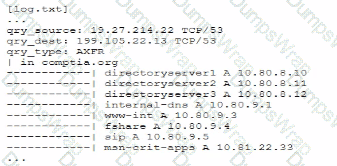
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A manufacturing plant is updating its IT services. During discussions, the senior management team created the following list of considerations:
• Staff turnover is high and seasonal.
• Extreme conditions often damage endpoints.
• Losses from downtime must be minimized.
• Regulatory data retention requirements exist.
Which of the following best addresses the considerations?
A company migrated a critical workload from its data center to the cloud. The workload uses a very large data set that requires computational-intensive data processing. The business unit that uses the workload is projecting the following growth pattern:
• Storage requirements will double every six months.
• Computational requirements will fluctuate throughout the year.
• Average computational requirements will double every year.
Which of the following should the company do to address the business unit's requirements?
A security engineer is implementing a code signing requirement for all code developed by the organization. Currently, the PKI only generates website certificates. Which of the following steps should the engineer perform first?
A security analyst needs to ensure email domains that send phishing attempts without previous communications are not delivered to mailboxes The following email headers are being reviewed
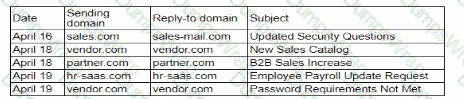
Which of thefollowing is the best action for the security analyst to take?
A local government that is investigating a data exfiltration claim was asked to review the fingerprint of the malicious user's actions. An investigator took a forensic image of the VM and downloaded the image to a secured USB drive to share with the government. Which of the following should be taken into consideration during the process of releasing the drive to the government?
An organization plans to deploy new software. The project manager compiles a list of roles that will be involved in different phases of the deployment life cycle. Which of the following should the project manager use to track these roles?
A user from the sales department opened a suspicious file attachment. The sales department then contacted the SOC to investigate a number of unresponsive systems, and the team successfully identified the file and the origin of the attack. Which of the following is the next step of the incident response plan?
A systems administrator wants to introduce a newly released feature for an internal application. The administrate docs not want to test the feature in the production environment. Which of the following locations is the best place to test the new feature?
The ISAC for the retail industry recently released a report regarding social engineering tactics in which small groups create distractions for employees while other malicious individuals install advanced card skimmers on the payment systems. The Chief Information Security Officer (CISO) thinks that security awareness training, technical control implementations, and governance already in place is adequate to protect from this threat. The board would like to test these controls. Which of the following should the CISO recommend?
A company experienced a data breach, resulting in the disclosure of extremely sensitive data regarding a merger. As a regulated entity, the company must comply with reporting and disclosure requirements. The company is concerned about its public image and shareholder values. Which of the following best supports the organization in addressing its concerns?
An external SaaS solution user reports a bug associated with the role-based access control module. This bug allows users to bypass system logic associated with client segmentation in the multitenant deployment model. When assessing the bug report, the developer finds that the same bug was previously identified and addressed in an earlier release. The developer then determines the bug was reintroduced when an existing software component was integrated from a prior version of the platform. Which of the following is the best way to prevent this scenario?
A company wants to modify its process to comply with privacy requirements after an incident involving PII data in a development environment. In order to perform functionality tests, the QA team still needs to use valid data in the specified format. Which of the following best addresses the risk without impacting the development life cycle?
A financial services organization is using Al lo fully automate the process of deciding client loan rates Which of the following should the organization be most concerned about from a privacy perspective?
A user reports application access issues to the help desk. The help desk reviews the logs for the user:
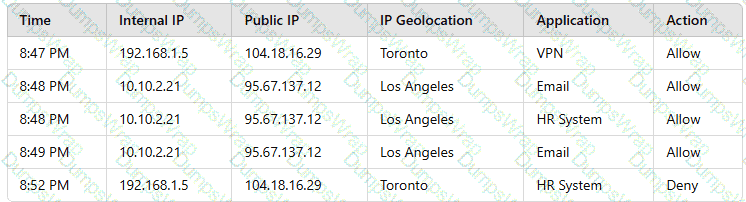
Which of the following is most likely the reason for the issue?
Which of the following are risks associated with vendor lock-in? (Select two).
During a security assessment using an CDR solution, a security engineer generates the following report about the assets in me system:
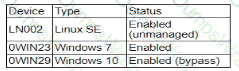
After five days, the EDR console reports an infection on the host 0WIN23 by a remote access Trojan Which of the following is the most probable cause of the infection?
A security analystreviews the following report:
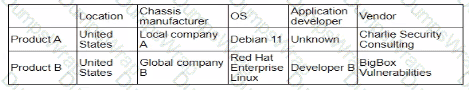
Which of the following assessments is the analyst performing?
A company SIEM collects information about the log sources. Given the following report information:
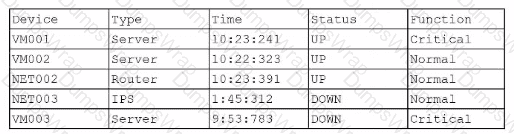
Which of the following actions should a security engineer take to enhance the security monitoring posture?
An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice. Which of the following should the organization consider first to address this requirement?
An organization determines existing business continuity practices are inadequate to support critical internal process dependencies during a contingency event. A compliance analyst wants the Chief Information Officer (CIO) to identify the level of residual risk that is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
An audit finding reveals that a legacy platform has not retained loos for more than 30 days The platform has been segmented due to its interoperability with newer technology. As a temporarysolution, the IT department changed the log retention to 120 days. Which of the following should the security engineer do to ensure the logs are being properly retained?
A security engineer performed a code scan that resulted in many false positives. The security engineer must find asolution that improves the quality of scanning results before application deployment. Which of the following is the best solution?
A security analyst received anotification from a cloud service provider regarding an attack detected on a web server The cloud service provider shared the following information about the attack:
• The attack came from inside the network.
• The attacking source IP was from the internal vulnerability scanners.
• The scanner is not configured to target the cloud servers.
Which of the following actions should the security analyst take first?
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
A security officer received several complaints from usersabout excessive MPA push notifications at night The security team investigates and suspects malicious activities regarding user account authentication Which of the following is the best way for the security officer to restrict MI~A notifications''
To prevent data breaches, security leaders at a company decide to expand user education to:
• Create a healthy security culture.
• Comply with regulatory requirements.
• Improve incident reporting.
Which of the following would best meet their objective?
During a gap assessment, an organization notes that OYOD usage is asignificant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
A news organization wants to implement workflows that allow users to request that untruthful data be retraced and scrubbed from online publications to comply with the right to be forgotten Which of the following regulations is the organization most likely trying to address'
After an organization met with its ISAC, the organization decided to test the resiliency of its security controls against a small number of advanced threat actors. Which of the following will enable the security administrator to accomplish this task?
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
While reviewing recent modem reports, a security officer discovers that several employees were contacted by the same individual who impersonated a recruiter. Which of the following best describes this type of correlation?
A company was recently infected by malware. During the root cause analysis, the company determined that several users were installing their own applications. To prevent further compromises, the company has decided it will onlyallow authorized applications to run on its systems. Which of the following should the company implement?
A security analyst is reviewing the following authentication logs:
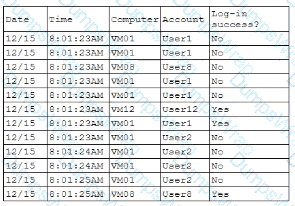
Which of the following should the analyst do first?
A company's security policy states that any publicly available server must be patched within 12 hours after a patch is released A recent llS zero-day vulnerability was discovered that affects all versions of the Windows Server OS:
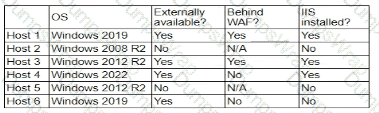
Which of the following hosts should a security analyst patch first once a patch is available?
During DAST scanning, applications are consistently reporting code defects in open-source libraries that were used to build web applications. Most of the code defects are from using libraries with known vulnerabilities. The code defects are causing product deployment delays. Which of the following is the best way to uncover these issues earlier in the life cycle?
As part of a security audit in the software development life cycle, a product manager must demonstrate and provide evidence of a complete representation of the code and modules used within the production-deployed application prior to the build. Which of the following best provides the required evidence?
A SOC analyst is investigating an event in which a penetration tester was able to successfully create and execute a payload. The analyst pulls the following command history from the affected server-
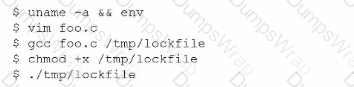
Which of the following should the analyst implement lo improve the security of the server?
A large organization deployed a generative AI platform for its global user population to use. Based on feedback received during beta testing, engineers have identified issues with user interface latency and page-loading performance for international users. The infrastructure is currently maintained within two separate data centers, which are connected using high-availability networking and load balancers. Which of the following is the best way to address the performance issues?
A software development team requires valid data for internal tests. Company regulations, however do not allow the use of this data in cleartext. Which of the following solutions best meet these requirements?
A security analyst notices a number of SIEM events that show the following activity:
10/30/2020 - 8:01 UTC - 192.168.1.1 - sc stop HinDctend
10/30/2020 - 8:05 UTC - 192.168.1.2 - c:\program files\games\comptidcasp.exe
10/30/2020 - 8:07 UTC - 192.168.1.1 - c:\windows\system32\cmd.exe /c powershell
10/30/2020 - 8:07 UTC - 192.168.1.1 - powershell —> 40.90.23.154:443
Which of the following response actions should the analyst take first?
A security architect is mitigating a vulnerability that previously led to a web application data breach. An analysis into the root cause of the issue finds the following:
An administrator’s account was hijacked and used on several Autonomous System Numbers within 30 minutes.
All administrators use named accounts that require multifactor authentication.
Single sign-on is used for all company applications.Which of the following should the security architect do to mitigate the issue?
An analyst reviews a SIEM and generates the following report:
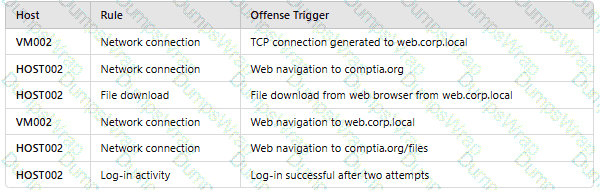
OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
An organization wants to implement a platform to better identify which specific assets are affected by a given vulnerability. Which of the following components provides the best foundation to achieve this goal?
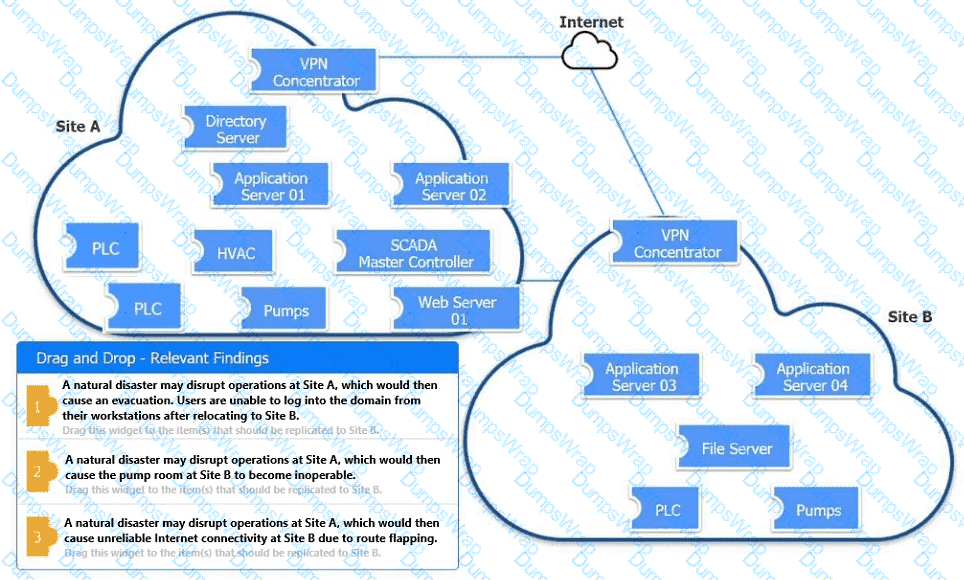
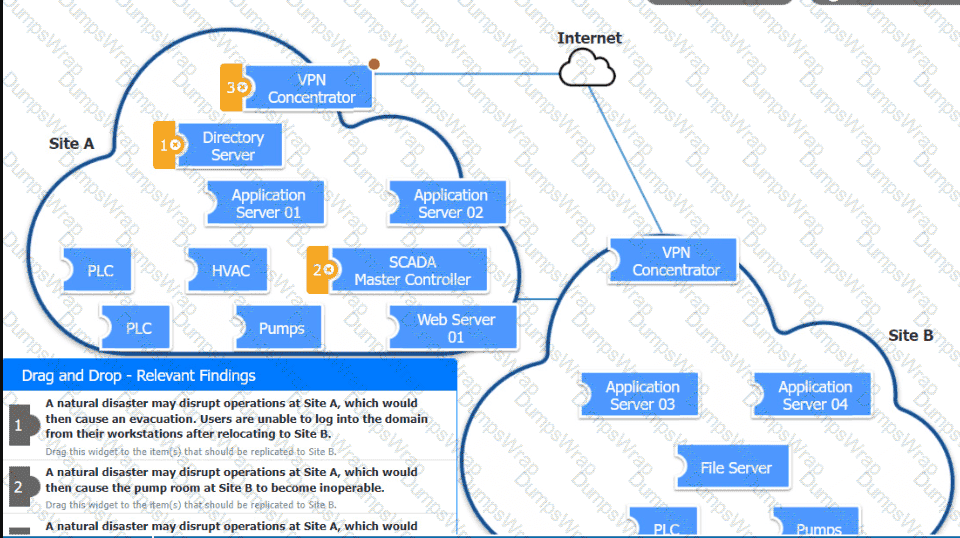
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
Which of the following best describes the reason a network architect would enable forward secrecy on all VPN tunnels?
A security analyst is performing threat modeling for a new AI chatbot. The AI chatbot will be rolled out to help customers develop configuration information within the company's SaaS offering. Which of the following issues would require involvement from the company's internal legal team?
After a cybersecurity incident, a security analyst was able to collect a binary that the attacker used on the compromised server. Then the analyst ran the following command:
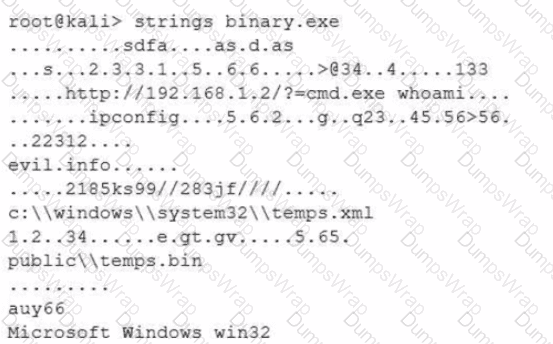
Which of the following options describes what the analyst is trying to do?
A company reduced its staff 60 days ago, and applications are now starting to fail. The security analyst is investigating to determine if there is malicious intent for the application failures. The security analyst reviews the following logs:
22:03:50 sshd[21502]: Success login for user01 from 192.168.2.5
22:10:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:11:40 sshd[21502]: Success login for user07 from 192.168.2.58
22:12:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:13:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:13:00 sshd[21502]: Success login for user03 from 192.168.2.27
22:13:00 sshd[21502]: Failed login for user10 from 192.168.2.5
Which of the following is the most likely reason for the application failures?
A company implements an Al model that handles sensitive and personally identifiable information. Which of the following threats is most likely the company's primary concern?
A security engineer is developing a solution to meet the following requirements:
• All endpoints should be able to establish telemetry with a SIEM.
• All endpoints should be able to be integrated into the XDR platform.
• SOC services should be able to monitor the XDR platform.
Which of the following should the security engineer implement to meet the requirements? (Select Two.)
Emails that the marketing department is sending to customers are pomp to the customers' spam folders. The security team is investigating the issue and discovers that the certificates used by the email server were reissued, but DNS records had not been updated. Which of the following should the security team update in order to fix this issue? (Select three.)
Engineers are unable to control pumps at Site A from Site B when the SCADA controller at Site A experiences an outage. A security analyst must provide a secure solution that ensures Site A pumps can be controlled by a SCADA controller at Site B if a similar outage occurs again. Which of the following represents the most cost-effective solution?
A security engineer wants to improve the security of an application as part of the development pipeline. The engineer reviews the following component of an internally developed web application that allows employees to manipulate documents from a number of internal servers:
response = requests.get(url)
Users can specify the document to be parsed by passing the document URL to the application as a parameter. Which of the following is the best solution?
An endpoint security engineer finds that a newly acquired company has a variety of non-standard applications running and no defined ownership for those applications. The engineer needs to find a solution thatrestricts malicious programs and software from running in that environment, while allowing the non-standard applications to function without interruption. Which of the following application control configurations should the engineer apply?
An organization has been using self-managed encryption keys rather than the free keys managed by the cloud provider. The Chief Information Security Officer (CISO) reviews the monthly bill and realizes the self-managed keys are more costly than anticipated. Which of the following should the CISO recommend to reduce costs while maintaining a strong security posture?
Which of the following are the best ways to mitigate the threats that are the highest priority? (Select two).
A subcontractor develops safety critical avionics software for a major aircraft manufacturer. After an incident, a third-party investigator recommends the company begin to employ formal methods in the development life cycle. Which of the following findings from the investigation most directly supports the investigator's recommendation?
Asoftware company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?
A security architect is establishing requirements to design resilience in un enterprise system trial will be extended to other physical locations. The system must
• Be survivable to one environmental catastrophe
• Re recoverable within 24 hours of critical loss of availability
• Be resilient to active exploitation of one site-to-site VPN solution
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent Which of the following actions should the company lake to most likely improve the vulnerability management process'
A developer needs toimprove the cryptographic strength of a password-storage component in a web application without completely replacing the crypto-module. Which of the following is the most appropriate technique?
A company designs policies and procedures for hardening containers deployed in the production environment. However, a security assessment reveals that deployed containers are not complying with the security baseline. Which of the following solutions best addresses this issue throughout early life-cycle stages?
After a penetration test on the internal network, the following report was generated:
Attack Target Result
Compromised host ADMIN01S.CORP.LOCAL Successful
Hash collected KRBTGT.CORP.LOCAL Successful
Hash collected SQLSV.CORP.LOCAL Successful
Pass the hash SQLSV.CORP.LOCAL Failed
Domain control CORP.LOCAL Successful
Which of the following should be recommended to remediate the attack?
A security team determines that the most significant risks within the pipeline are:
• Unauthorized code changes
• The current inability to perform independent verification of software modules
Which of the following best addresses these concerns?
A systems administrator is working with clients to verify email-based services are performing properly. The administrator wants to have the email server digitally sign outbound emails using the organization's private key. Which of the following should the systems administrator configure?
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
A company receives several complaints from customers regarding its website. An engineer implements a parser for the web server logs that generates the following output:
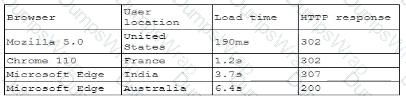
which of the following should the company implement to best resolve the issue?
During a security review for the CI/CD process, a security engineer discovers the following information in a testing repository from the company:
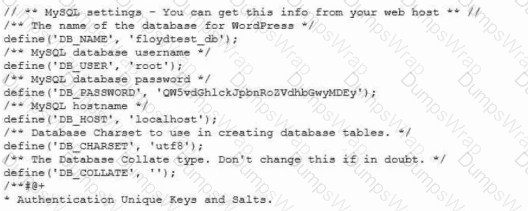
Which of the following options is the best countermeasure to prevent this issue in the future?
A security engineer is reviewing the following vulnerability scan report:
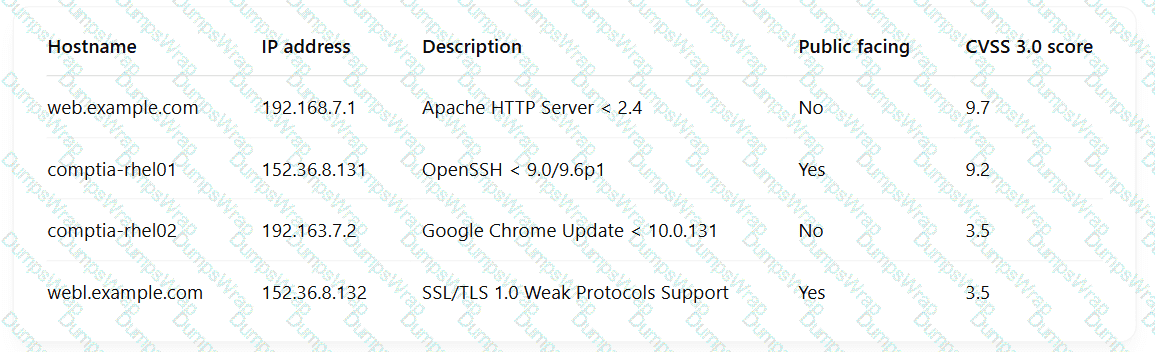
Which of the following should the engineer prioritize for remediation?
A cloud engineer wants to configure mail security protocols to support email authenticity and enable the flow of email security information to a third-party platform for further analysis. Which of the following must be configured to achieve these requirements? (Select two).
An organization currently has IDS, firewall, and DLP systems in place. The systems administrator needs to integrate the tools in the environment to reduce response time. Which of the following should the administrator use?
A building camera is remotely accessed and disabled from the remote console application during off-hours. A security analyst reviews the following logs:
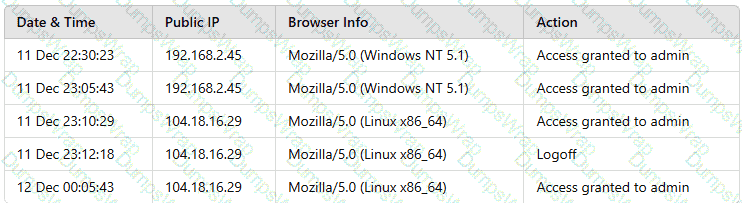
Which of the following actions should the analyst take to best mitigate the threat?
An organization is researching the automation capabilities for systems within an OT network. A security analyst wants to assist with creating secure coding practices and would like to learn about the programming languages used on the PLCs. Which of the following programming languages is the most relevant for PLCs?
PKI can be used to support security requirements in the change management process. Which of the following capabilities does PKI provide for messages?
Developers have been creating and managing cryptographic material on their personal laptops fix use in production environment. A security engineer needs to initiate a more secure process. Which of thefollowing is the best strategy for the engineer to use?


 A computer screen shot of a diagram Description automatically generated
A computer screen shot of a diagram Description automatically generated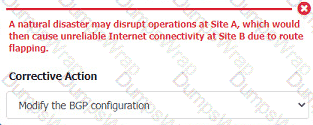 A screenshot of a computer error Description automatically generated
A screenshot of a computer error Description automatically generated