CompTIA Network+ Certification Exam Questions and Answers
Which of the following attacks can cause users who are attempting to access a company website to be directed to an entirely different website?
A network engineer is installing new PoE wireless APs. The first five APs deploy successfully, but the sixth one fails to start. Which of the following should the engineer investigate first?
After a company installed a new IPS, the network is experiencing speed degradation. A network administrator is troubleshooting the issue and runs a speed test. The results from the different network locations are as follows:
LocationSpeed DownSpeed Up
Wireless laptop4.8 Mbps47.1 Mbps
Wired desktop5.2 Mbps49.3 Mbps
Firewall48.8 Mbps49.5 Mbps
Which of the following is the most likely issue?
A technician needs to quickly set up a network with five wireless devices. Which of the following network types should the technician configure to accomplish this task?
Which of the following, in addition to a password, can be asked of a user for MFA?
A systems administrator is looking for operating system information, running services, and network ports that are available on a server. Which of the following software tools should the administrator use to accomplish this task?
A help desk technician receives a report that users cannot access internet URLs. The technician performs ping tests and finds that sites fail when a URL is used but succeed when an IP is used. Which of the following tools should the technician utilize next?
Which of the following objectives does an evil twin achieve?
An organization wants to ensure that incoming emails were sent from a trusted source. Which of the following DNS records is used to verify the source?
A network administrator wants to increase network security by preventing client devices from communicating directly with each other on the same subnet. Which of the following technologies should be implemented?
Which of the following connector types would most likely be used to connect to an external antenna?
A network engineer is implementing a new connection between core switches. The engineer deploys the following configurations:
Core-SW01
vlan 100
name
interface Ethernet 1/1
channel-group 1 mode active
interface Ethernet 1/2
channel-group 1 mode active
interface port-channel 1
switchport mode trunk
switchport trunk allow vlan 100
Core-SW02
vlan 100
name
interface Ethernet 1/1
switchport mode trunk
switchport trunk allow vlan 100
interface Ethernet 1/2
switchport mode trunk
switchport trunk allow vlan 100
interface port-channel 1
switchport mode trunk
switchport trunk allow vlan 100
Which of the following is the state of the Core-SW01 port-channel interfaces?
Which of the following describes the best reason for using BGP?
Which of the following layers of the OSI model is responsible for end-to-end encryption?
Which of the following cloud service models most likely requires the greatest up-front expense by the customer when migrating a data center to the cloud?
A support engineer is troubleshooting a network outage that is affecting 3,000 users. The engineer has isolated the issue to the internet firewall. Packet captures confirm that the firewall is blocking the traffic. Which of the following is the next step in troubleshooting?
Which of the following concepts describes the idea of housing different customers in the same public cloud data center?
Which of the following is used to redistribute traffic between one source and multiple servers that run the same service?
Which of the following is a difference between EOL and EOS?
Which of the following involves an attacker traversing from one part of a network to another part that should be inaccessible?
Two companies successfully merged. Following the merger, a network administrator identified a connection bottleneck. The newly formed company plans to acquire a high-end 40GB switch and redesign the network from a three-tier model to a collapsed core. Which of the following should the administrator do until the new devices are acquired?
Which of the following Layer 1 devices is responsible for the termination of fiber-optic connections on an SFP-capable switch?
A customer wants to separate the finance department from the marketing department. The network administrator suggests segmenting the existing Class C network into two sections and readdressing all devices appropriately. Which of the following subnet masks should the network administrator use?
A junior network administrator gets a text message from a number posing as the domain registrar of the firm. The administrator is tricked into providing global administrator credentials. Which of the following attacks is taking place?
Which of the following protocols is used to route traffic on the public internet?
A company recently implemented a videoconferencing system that utilizes large amounts of bandwidth. Users start reporting slow internet speeds and an overall decrease in network performance. Which of the following are most likely the causes of the network performance issues? (Select two)
Voice traffic is experiencing excessive jitter. A network engineer wants to improve call performance and clarity. Which of the following features should the engineer configure?
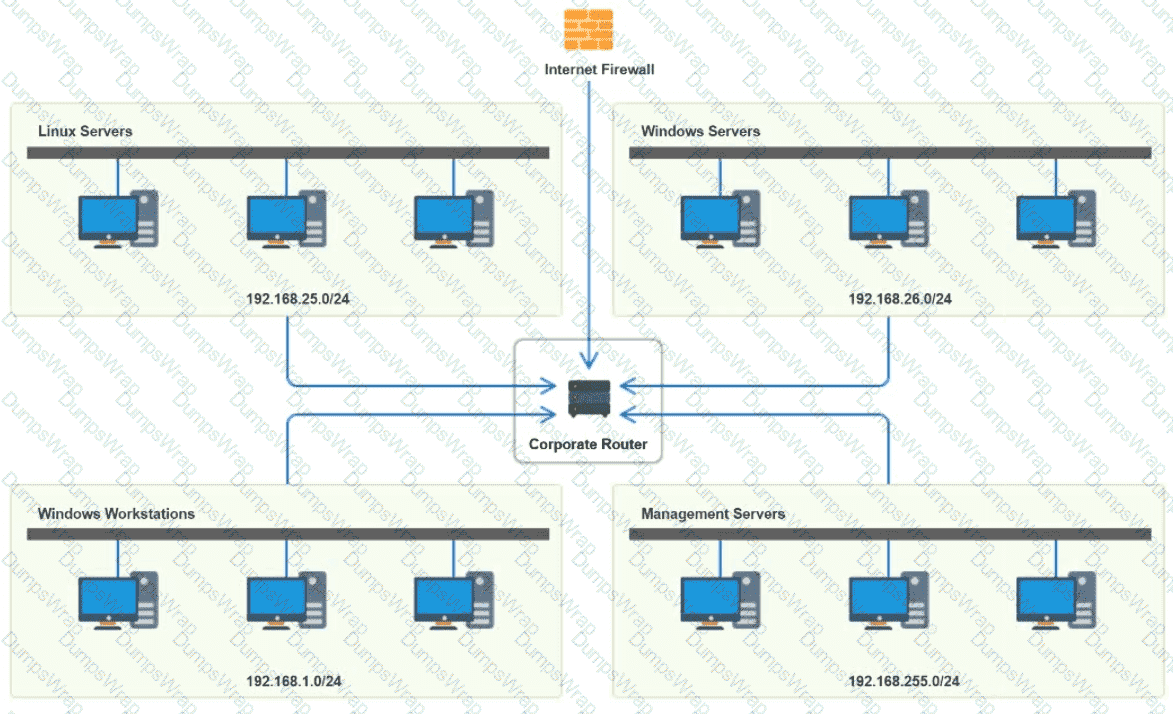
A network technician was recently onboarded to a company. A manager has
tasked the technician with documenting the network and has provided the technician With partial information from previous documentation.
Instructions:
Click on each switch to perform a network discovery by entering commands into the terminal. Fill in the missing information using drop-down menus provided.
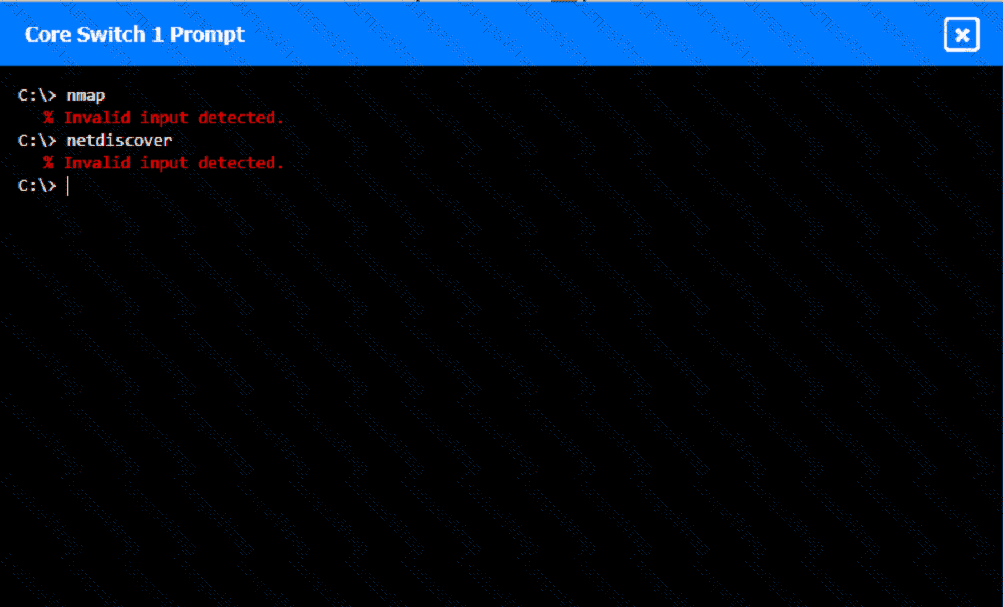
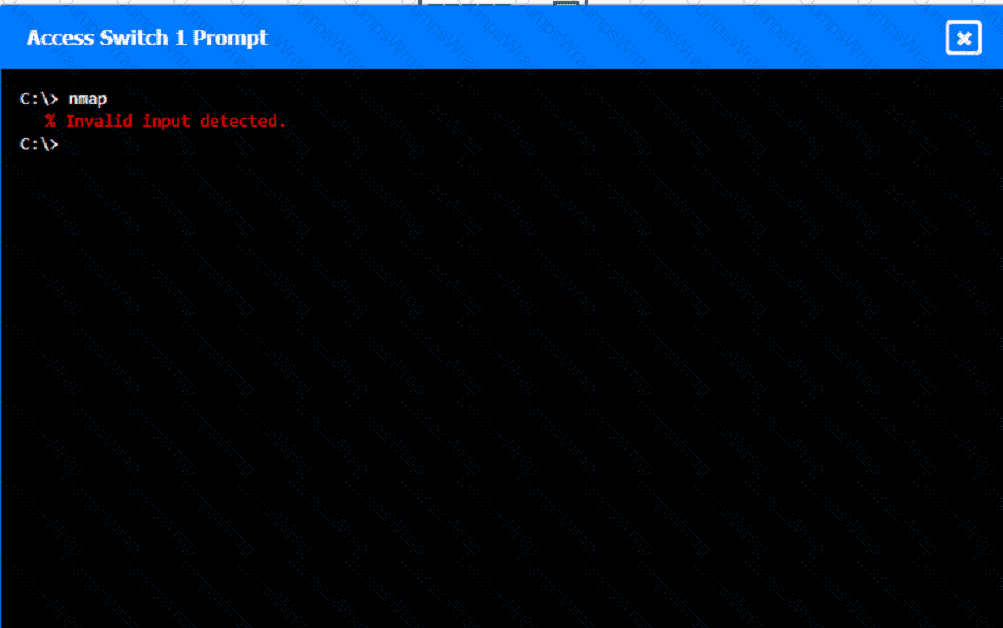
Which of the following enables an organization to leverage an identity provider to manage access across SaaS applications?
A Chief Information Officer wants a DR solution that runs only after a failure of the primary site and can be brought online quickly once recent backups are imported. Which of the following DR site solutions meets these requirements?
Which of the following fiber connector types is the most likely to be used on a network interface card?
A network administrator is implementing security zones for each department. Which of the following should the administrator use to accomplish this task?
A network engineer configures the network settings in a new server as follows:
IP address = 192.163.1.15
Subnet mask = 255.255.255.0
Gateway = 192.163.1.255
The server can reach other hosts on the same subnet successfully, but it cannot reach hosts on different subnets. Which of the following is most likely configured incorrectly?
Which of the following is most likely responsible for the security and handling of personal data in Europe?
Which of the following is the step that a troubleshooter should take immediately after implementing a solution?
A network engineer receives a vendor alert regarding a vulnerability in a router CPU. Which of the following should the engineer do to resolve the issue?
A research facility is expecting to see an exponential increase in global network traffic in the near future. The offices are equipped with 2.5Gbps fiber connections from the ISP, but the facility is currently only utilizing 1Gbps connections. Which of the following would need to be configured in order to use the ISP's connection speed?
A new network is being created to support 126 users. Which of the following CIDR ranges provides the most efficient use of space?
An organization has a security requirement that all network connections can be traced back to a user. A network administrator needs to identify a solution to implement on the wireless network. Which of the following is the best solution?
A network administrator needs to change where the outside DNS records are hosted. Which of the following records should the administrator change the registrar to accomplish this task?
A university is implementing a new campus wireless network. A network administrator needs to configure the network to support a large number of devices and high-bandwidth demands from students.
Which of the following wireless technologies should the administrator consider for this scenario?
Which of the following is a use case for a PaaS environment?
A group of users cannot connect to network resources. The technician runs ipconfig from one user's device and is able to ping the gateway shown from the command. Which of the following is most likely preventing the users from accessing network resources?
Which of the following layers in the OSI model is responsible for establishing, maintaining, and terminating connections between nodes?
After providing a username and password, a user must input a passcode from a phone application. Which of the following authentication technologies is used in this example?
Which of the following network devices converts wireless signals to electronic signals?
Which of the following kinds of targeted attacks uses multiple computers or bots to request the same resource repeatedly?
A support agent receives a report that a remote user’s wired devices are constantly disconnecting and have slow speeds. Upon inspection, the support agent sees that the user’s coaxial modern has a signal power of -97dB.
Which of the following is the most cost-efficient way to host email services?
Which of the following typically uses compromised systems that become part of a bot network?
Which of the following is enforced through legislation?
A network engineer is now in charge of all SNMP management in the organization. The engineer must use a SNMP version that does not utilize plaintext data. Which of the following is the minimum version of SNMP that supports this requirement?
Three access points have Ethernet that runs through the ceiling. One of the access points cannot reach the internet. Which of the following tools can help identify the issue?
A user tries to visit a website, but instead of the intended site, the page displays vmw.cba.com. Which of the following should be done to reach the correct website?
A network administrator wants users to be able to authenticate to the corporate network using a port-based authentication framework when accessing both wired and wireless devices. Which of the following is the best security feature to accomplish this task?
During a VoIP call, a user notices inconsistent audio and logs an incident ticket. A network administrator notices inconsistent delays in arrival of the RTP packets. Which of the following troubleshooting tools should the network administrator use to determine the issue?
After a recent merger, a large number of alerts are coming in regarding extremely high utilization. Which of the following should be generated to help inform new alerting requirements?
A systems administrator needs to connect two laptops to a printer via Wi-Fi. The office does not have access points and cannot purchase any. Which of the following wireless network types best fulfills this requirement?
Which of the following is a major difference between an IPS and IDS?
Which of the following does a hash provide?
A network administrator needs to fail over services to an off-site environment. This process will take four weeks to become fully operational. Which of the following DR (Disaster Recovery) concepts does this describe?
A virtual machine has the following configuration:
•IPv4 address: 169.254.10.10
•Subnet mask: 255.255.0.0
The virtual machine can reach colocated systems but cannot reach external addresses on the Internet. Which of the following Is most likely the root cause?
Which of the following is an XML-based security concept that works by passing sensitive information about users, such as login information and attributes, to providers?
A newtwork administrator needs to create an SVI on a Layer 3-capable device to separate voice and data traffic. Which of the following best explains this use case?
A technician is deploying new networking hardware for company branch offices. The bridge priority must be properly set. Which of the following should the technician configure?
A customer purchases a new UTM device and wants the development team to integrate some of the device’s data-reporting capabilities into the company’s custom internal support software. Which of the following features should the development team use to obtain the device’s data?
An imaging workstation at a hospital is experiencing intermittent connectivity loss. Which of the following would most likely be used to resolve the issue at the least expense?
A network engineer is testing a website to ensure it is compatible with IPv6. After attempting to ping the website by its IPv6 address, the engineer determines that the DNS has not been set up properly. Which of the following should the network engineer complete to resolve this issue?
A new SQL server is identified as allowing FTP access to all users. Which of the following would a systems administrator most likely do to ensure only the required services are allowed?
A company experiences an incident involving a user who connects an unmanaged switch to the network. Which of the following technologies should the company implement to help avoid similar incidents without conducting an asset inventory?
Which of the following devices can operate in multiple layers of the OSI model?
Which of the following is created to illustrate the effectiveness of wireless networking coverage in a building?
Which of the following should be configured so users can authenticate to a wireless network using company credentials?
Which of the following can be implemented to add an additional layer of security between a corporate network and network management interfaces?
Which of the following network ports is used when a client accesses an SFTP server?
Which of the following network topologies contains a direct connection between every node in the network?
A network administrator is conducting an assessment and finds network devices that do not meet standards. Which of the following configurations is considered a set of rules that devices should adhere to?
Several users in an organization report connectivity issues and lag during a video meeting. The network administrator performs a tcpdump and observes increased retransmissions for other non-video applications on the network. Which of the following symptoms describes the users' reported issues?
Which of the following is the most cost-effective way to safely expand outlet capacity in an IDF?
Early in the morning, an administrator installs a new DHCP server. In the afternoon, some users report they are experiencing network outages. Which of the following is the most likely issue?
Which of the following steps in the troubleshooting methodology would be next after putting preventive measures in place?
An administrator needs to configure an IoT device with a /21 subnet mask, but the device will only accept dotted decimal notation. Which of the following subnet masks should the administrator use?
A company is concerned that the public can use network wall jacks in publicly available conference rooms to access company servers. Which of the following is the best way to mitigate the vulnerability?
Which of the following steps in the troubleshooting methodology comes after using a top-to-top buttom examination of the OSI model to determine cause?
Which of the following protocols has a default administrative distance value of 90?
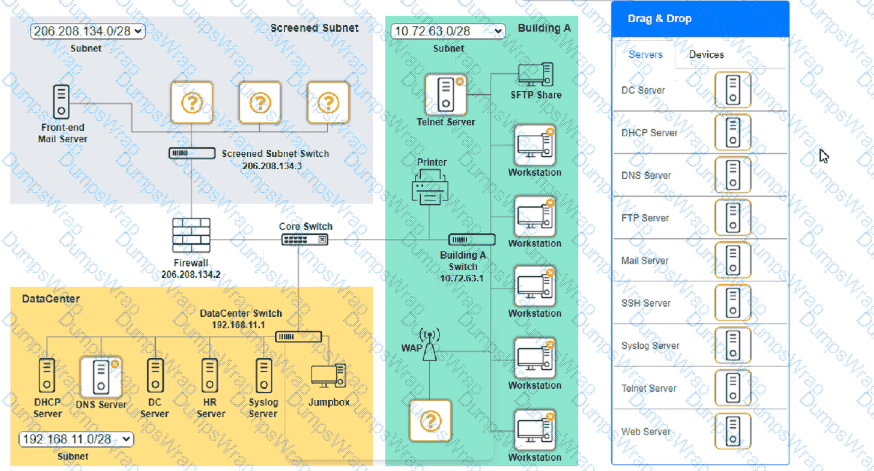
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
Building A
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide devices to support 5 additional different office users
Add an additional mobile user
Replace the Telnet server with a more secure solution
Screened subnet
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a server to handle external 80/443 traffic
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
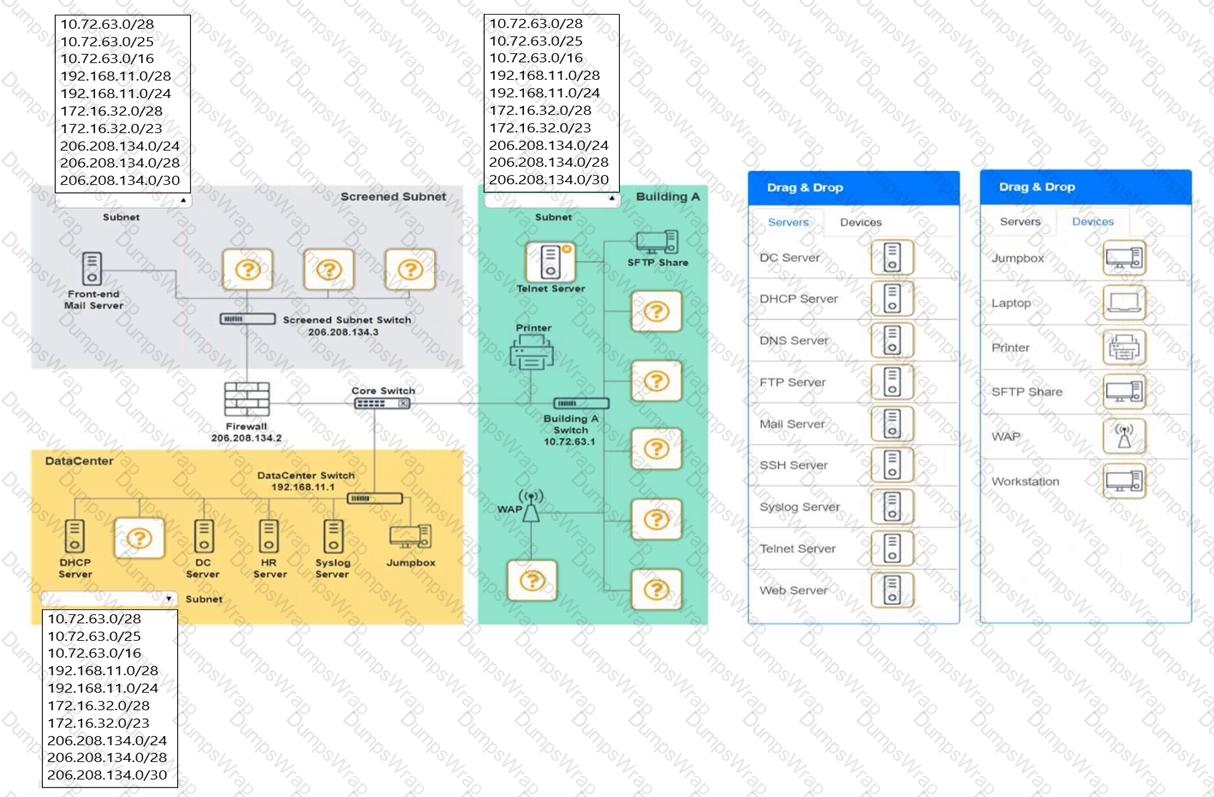
Which of the following dynamic routing protocols is used on the internet?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses, one for a computer and one for a phone connected to the network. Which of the following classful IPv4 address ranges will be best-suited for the network?
A network engineer configures a new switch and connects it to an existing switch for expansion and redundancy. Users immediately lose connectivity to the network. The network engineer notes the following spanning tree information from both switches:
Switch 1
Port State Cost
1 Forward 2
2 Forward 2
Switch 2
Port State Cost
1 Forward 2
2 Forward 2
Which of the following best describes the issue?
A network administrator is notified that a user cannot access resources on the network. The network administrator checks the physical connections to the workstation labeled User 3 and sees the Ethernet is properly connected. However, the network interface’s indicator lights are not blinking on either the computer or the switch. Which of the following Is the most likely cause?
A network architect needs to create a wireless field network to provide reliable service to public safety vehicles. Which of the following types of networks is the best solution?
A network administrator needs to implement a solution to filter access to the internet. Which of the following should the administrator most likely implement?
A network administrator is creating a subnet that will include 45 separate hosts on a small private network within a large network architecture. Which of the following options is the most efficient use of network addresses when assigning this network?
An IT department asks a newly hired employee to use a personal laptop until the company can provide one. Which of the following policies is most applicable to this situation?
A user reports issues accessing a file server on a LAN with the IP address 192.168.50.140 at a large facility with incomplete infrastructure documentation. The following are the results of the ping command:
ping -c 10 192.168.50.140
Packets: Sent = 10, Received = 5, Lost = 5 (50% loss)
Round-trip times: Minimum = 3ms, Maximum = 144ms, Average = 42ms
Which of the following should a technician do next to continue troubleshooting the issue at the switch with minimal impact?
A storage network requires reduced overhead and increased efficiency for the amout of data being sent. Which of the following should an engineer likely configure to meet these requirements>?
Which of the following is the best way to keep devices on during a loss of power?
A server administrator needs to add a record to the company's DNS server to verify ownership of a web domain. The administrator has the record's name and value. Which of the following record types should the administrator use to add the record to the DNS server?
A company implements a new network utilizing only IPv6 addressing and needs to connect to the internet. Which of the following must be enabled in order for the internal network to contact servers on the internet?
Which of the following routing technologies uses an attribute list for path selection?
A network administrator prepares a VLAN for a new office while planning for minimal IP address waste. The new office will have approximately 800 workstations. Which of the following network schemes meets the requirements?
Which of the following must be implemented to securely connect a company's headquarters with a branch location?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host’s TCP/IP stack first. Which of the following commands should the network administrator run?
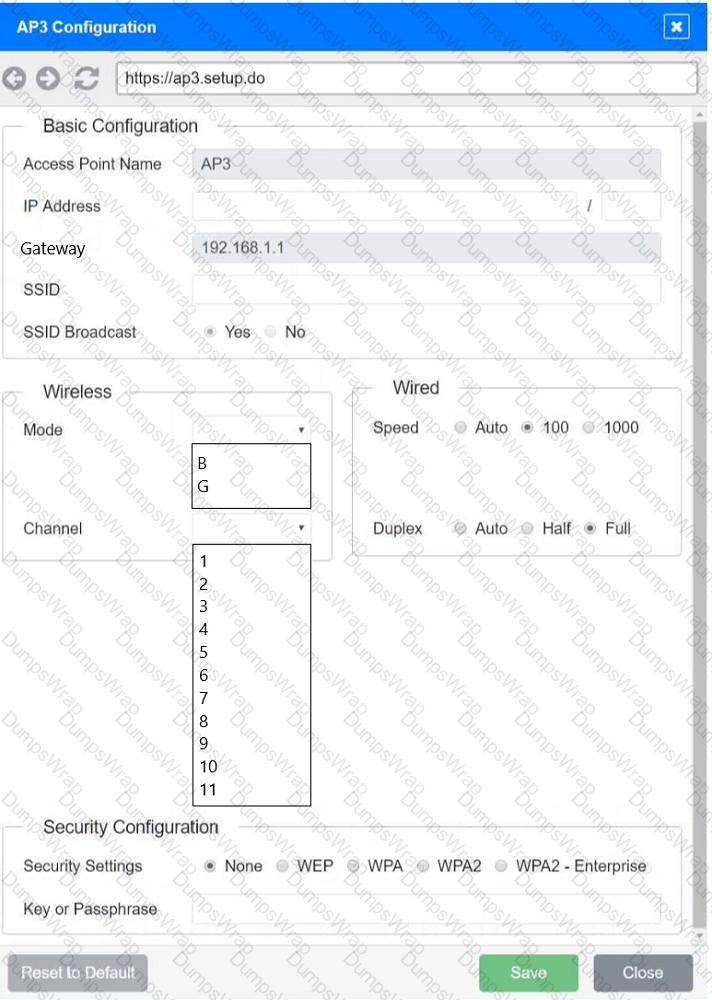
SIMULATION
You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters:
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The wireless signals should not interfere with each other
The subnet the Access Points and switch are on should only support 30 devices maximum
The Access Points should be configured to only support TKIP clients at a maximum speed
INSTRUCTONS
Click on the wireless devices and review their information and adjust the settings of the access points to meet the given requirements.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
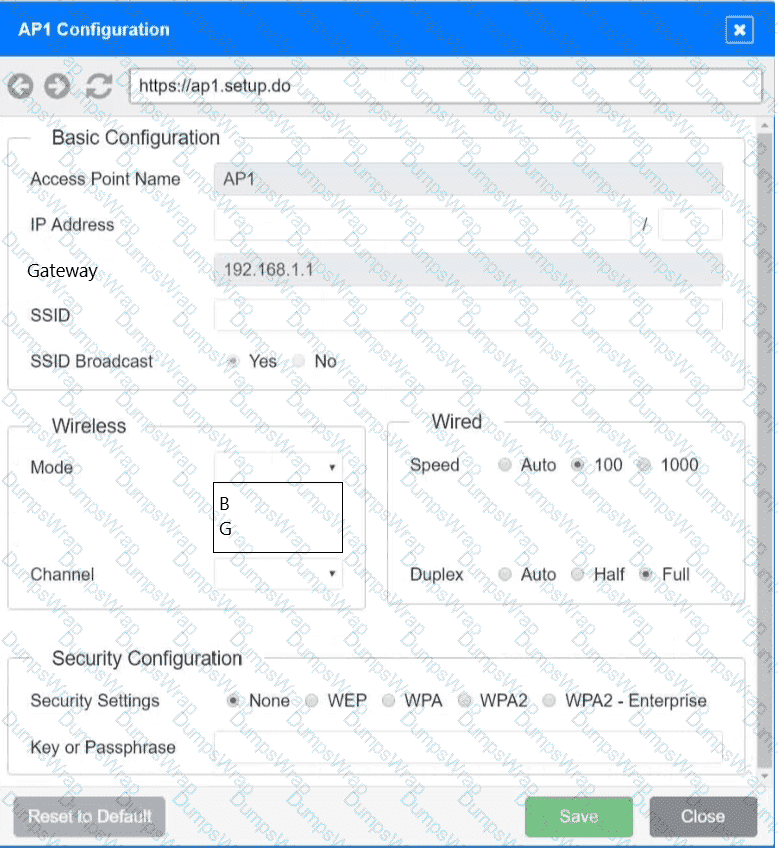
Which of the following are environmental factors that should be considered when installing equipment in a building? (Select two).
A firewall receives traffic on port 80 and forwards it to an internal server on port 88. Which of the following technologies is being leveraged?
Before using a guest network, an administrator requires users to accept the terms of use Which of the following is the best way to accomplish this goal?
Which of the following connector types is most commonly associated with Wi-Fi antennas?
A customer needs six usable IP addresses. Which of the following best meets this requirement?
A user's home mesh wireless network is experiencing latency issues. A technician has:
•Performed a speed test.
•Rebooted the devices.
•Performed a site survey.
•Performed a wireless packet capture.
The technician reviews the following information:

The technician notices in the packet capture that frames were retransmitted. Which of the following is the most likely cause of the user's network issue?
A company upgrades its network and PCs to gigabit speeds. After the upgrade, users are not getting the expected performance. Technicians discover that the speeds of the endpoint NICs are inconsistent. Which of the following should be checked first to troubleshoot the issue?
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
Which of the following ports should a network administrator enable for encrypted login to a network switch?
In an environment with one router, which of the following will allow a network engineer to communicate between VLANs without purchasing additional hardware?
A technician is designing a cloud service solution that will accommodate the company's current size, compute capacity, and storage capacity. Which of the following cloud deployment models will fulfill these requirements?
A network administrator needs to connect two routers in a point-to-point configuration and conserve IP space. Which of the following subnets should the administrator use?
A network engineer is deploying switches at a new remote office. The switches have been preconfigured with hostnames and STP priority values. Based on the following table:
Switch Name
Priority
core-sw01
24576
access-sw01
28672
distribution-sw01
32768
access-sw02
36864
Which of the following switches will become the root bridge?
An organization is struggling to get effective coverage using the wireless network. The organization wants to implement a solution that allows for continuous connectivity anywhere in the facility. Which of the following should the network administrator suggest to ensure the best coverage?
A network administrator is in the process of installing 35 PoE security cameras. After the administrator installed and tested the new cables, the administrator installed the cameras. However, a small number of the cameras do not work. Which of the following is the most reason?
A network consultant needs to decide between running an ethernet uplink or using the built-in 5GHz-to-point functionality on a WAP. Which of the following documents provides the best information to assist the consultant with this decision?
You have been tasked with implementing an ACL on the router that will:
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network engineer needs to virtualize network services, including a router at a remote branch location. Which of the following solutions meets the requirements?
Which of the following troubleshooting steps provides a change advisory board with the information needed to make a decision?
An organization moved its DNS servers to new IP addresses. After this move, customers are no longer able to access the organization's website. Which of the following DNS entries should be updated?
A network administrator changed an external DNS to point customers to a new server. Which of the following tools should the administrator use to test the new server's configuration?
A Linux server is running a log collector that needs to be hardened. A network administrator executes netstat to find open ports on the server. Which of the following ports should be disabled?
A network engineer is designing an internal network that needs to support both IPv4 and IPv6 routing. Which of the following routing protocols is capable of supporting both IPv4 and IPv6?
A network administrator recently configured an autonomous wireless AP and performed a throughput test via comptiaspeedtester.com. The result was 75 Mbps. When connected to other APs, the results reached 500 Mbps. Which of the following is most likely the reason for this difference?
Which of the following offers the ability to manage access at the cloud VM instance?
A network administrator is setting up a firewall to protect the organization’s network from external threats. Which of the following should the administrator consider first when configuring the firewall?
A network manager wants to implement a SIEM system to correlate system events. Which of the following protocols should the network manager verify?
Which of the following requires network devices to be managed using a different set of IP addresses?
Which of the following is the most likely reason an insurance brokerage would enforce VPN usage?
A network engineer needs to change, update, and control APs remotely, with real-time visibility over HTTPS. Which of the following will best allow these actions?
After installing a series of Cat 8 keystones, a data center architect notices higher than normal interference during tests. Which of the following steps should the architect take to troubleshoot the issue?
Which of the following indicates a computer has reached end-of-support?
A network engineer needs to add a boundary network to isolate and separate the internal network from the public-facing internet. Which of the following security defense solutions would best accomplish this task?
Which of the following is the most secure way to provide site-to-site connectivity?
Which of the following physical installation factors is the most important when a network switch is installed in a sealed enclosure?
Which of the following is the most likely benefit of installing server equipment in a rack?
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
A network administrator receives complaints of intermittent network connectivity issues. The administrator investigates and finds that the network design contains potential loop scenarios. Which of the following should the administrator do?
Which of the following facilities is the best example of a warm site in the event of information system disruption?
A network administrator suspects users are being sent to malware sites that are posing as legitimate sites. The network administrator investigates and discovers that user workstations are configured with incorrect DNS IP addresses. Which of the following should the network administrator implement to prevent this from happening again?
A media company is implementing a global streaming service. Which of the following should the company apply to each regional point of presence in order to comply with local laws?
A network engineer configures an application server so that it automatically adjusts resource allocation as demand changes. This server will host a new application and demand is not predictable. Which of the following concepts does this scenario demonstrate?
A company security policy requires all network traffic from remote employees' corporate laptops to use the company’s VPN. Which of the following network access methods best describes this scenario?
A network engineer runs ipconfig and notices that the default gateway is 0.0.0.0. Which of the following address types is in use?
A network administrator is developing a method of device monitoring with the following requirements:
•Allows for explicit, by user, privilege management
•Includes centralized logging of changes
•Offers widely accessible remote management
•Provides support of service accounts
Which of the following will most closely meet these requirements?
A small business is deploying new phones, and some of the phones have full HD videoconferencing features. The Chief Information Officer (CIO) is concerned that the network might not be able to handle the traffic if it reaches a certain threshold. Which of the following can the network engineer configure to help ease these concerns?

 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.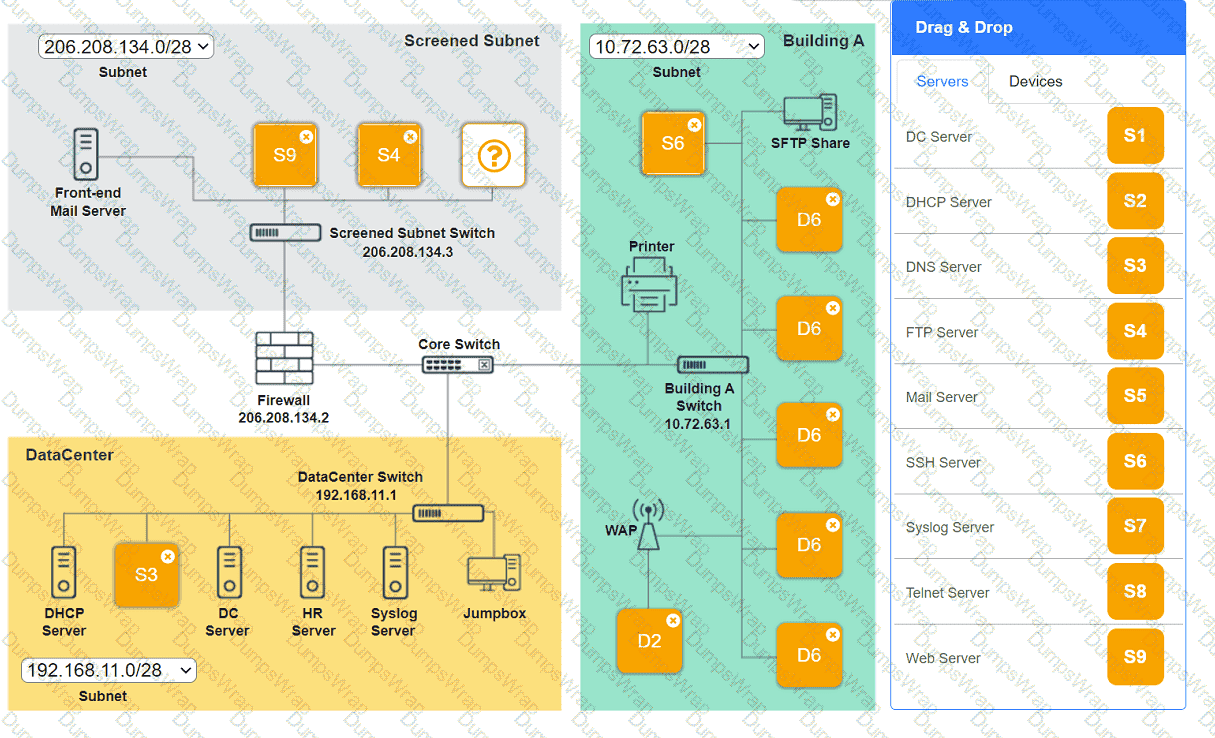 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.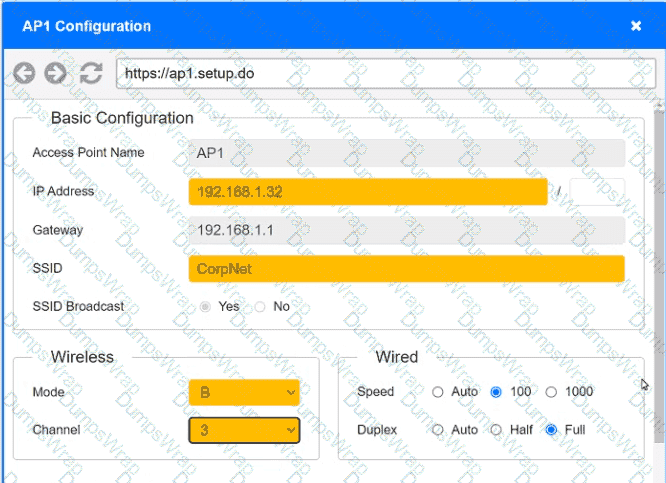 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect. A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect. A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.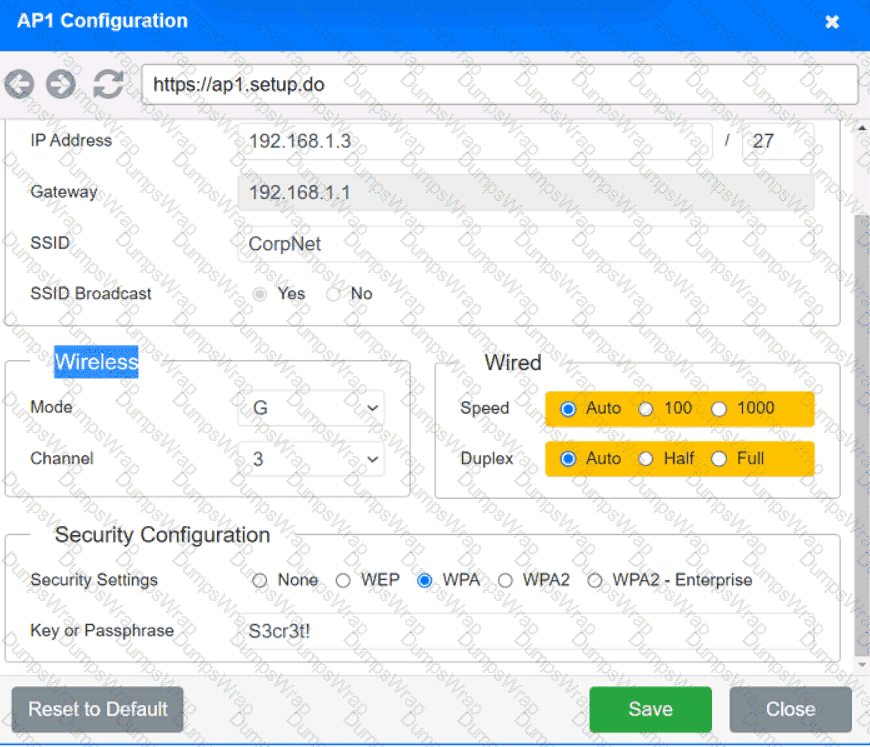 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.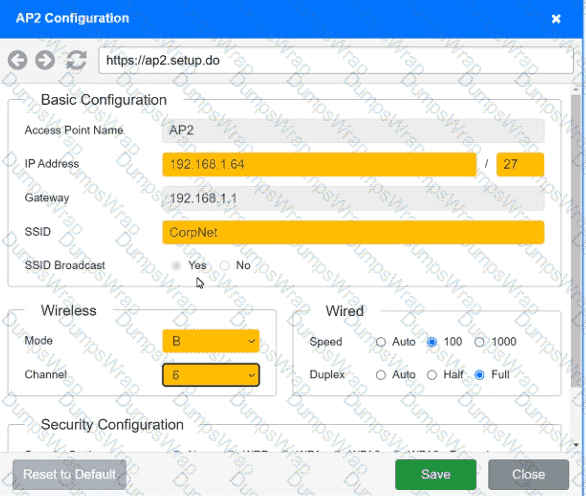 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.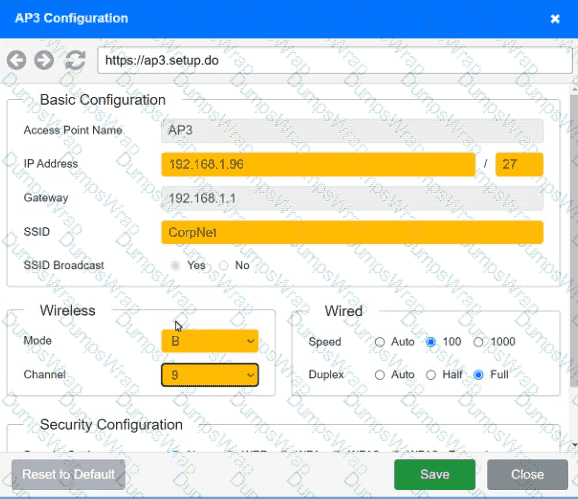 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect. A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.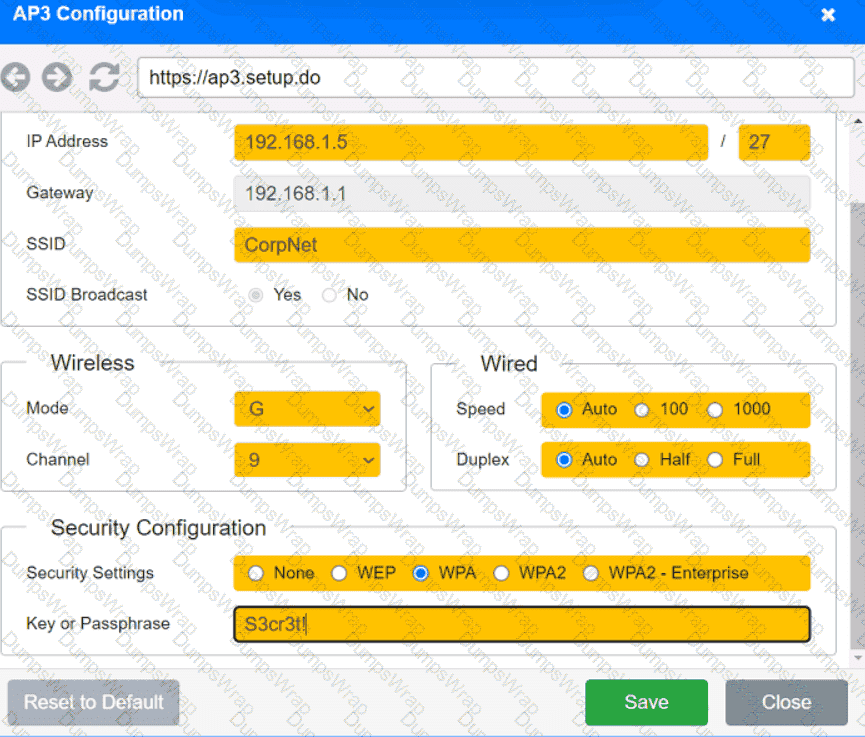 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.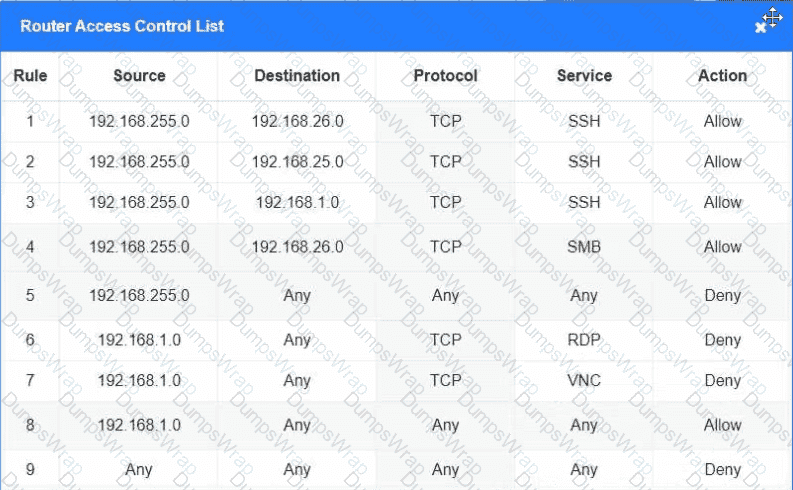 A screenshot of a computer screen AI-generated content may be incorrect.
A screenshot of a computer screen AI-generated content may be incorrect.