CompTIA PenTest+ Exam Questions and Answers
A penetration tester is trying to get unauthorized access to a web application and executes the following command:
GET /foo/images/file?id=2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2fetc%2fpasswd
Which of the following web application attacks is the tester performing?
A penetration tester writes the following script to enumerate a /24 network:
1 #!/bin/bash
2 for i in {1..254}
3 ping -c1 192.168.1.$i
4 done
The tester executes the script, but it fails with the following error:
-bash: syntax error near unexpected token 'ping'
Which of the following should the tester do to fix the error?
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
During an engagement, a penetration tester runs the following command against the host system:
host -t axfr domain.com dnsl.domain.com
Which of the following techniques best describes what the tester is doing?
A penetration tester wants to check the security awareness of specific workers in the company with targeted attacks. Which of the following attacks should the penetration tester perform?
During a penetration testing exercise, a team decides to use a watering hole strategy. Which of the following is the most effective approach for executing this attack?
An external legal firm is conducting a penetration test of a large corporation. Which of the following would be most appropriate for the legal firm to use in the subject line of a weekly email update?
A penetration tester plans to conduct reconnaissance during an engagement using readily available resources. Which of the following resources would most likely identify hardware and software being utilized by the client?
A penetration tester is conducting reconnaissance on a target network. The tester runs the following Nmap command: nmap -sv -sT -p - 192.168.1.0/24. Which of the following describes the most likely purpose of this scan?
A penetration tester identifies an exposed corporate directory containing first and last names and phone numbers for employees. Which of the following attack techniques would be the most effective to pursue if the penetration tester wants to compromise user accounts?
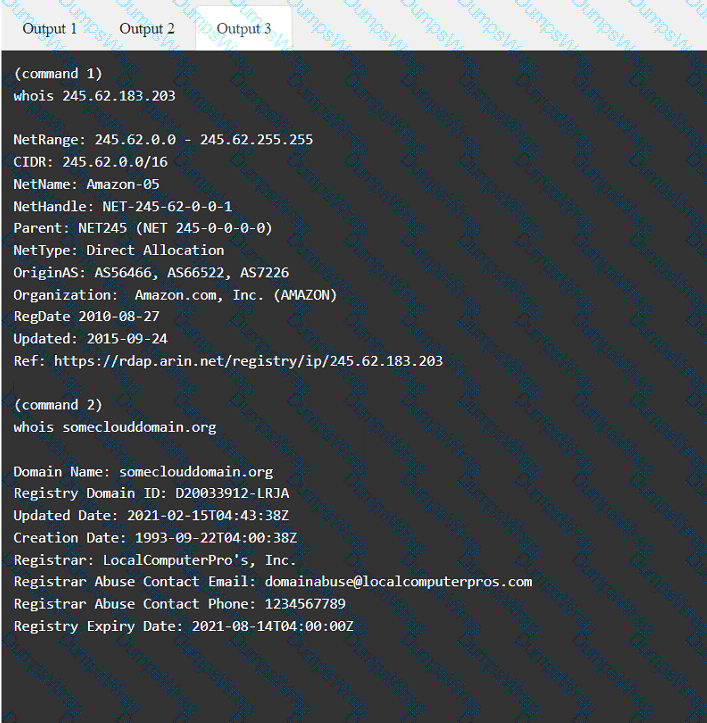
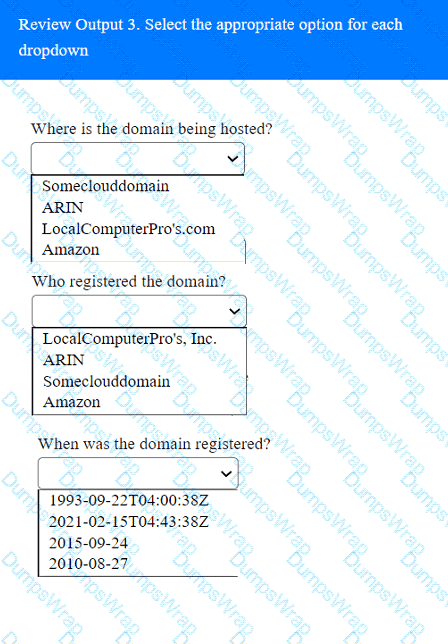
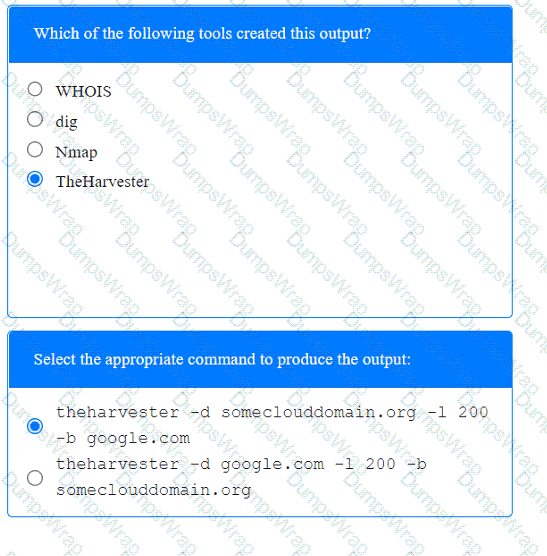
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1
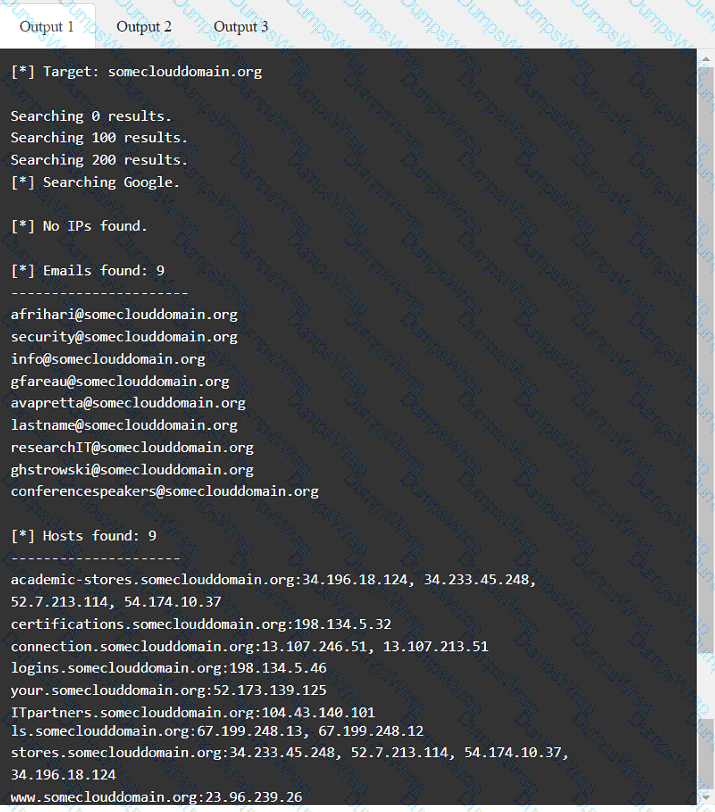
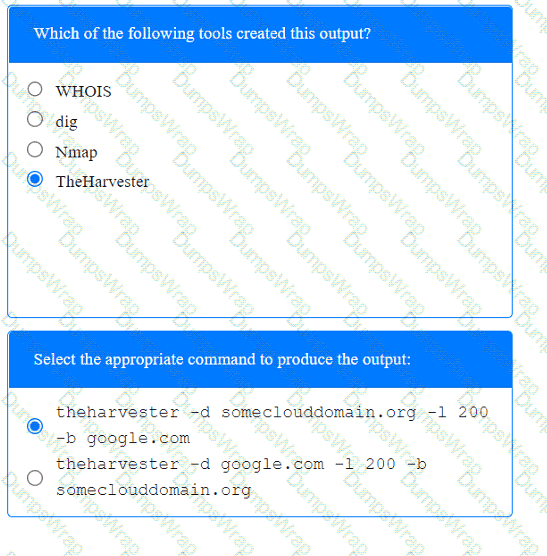
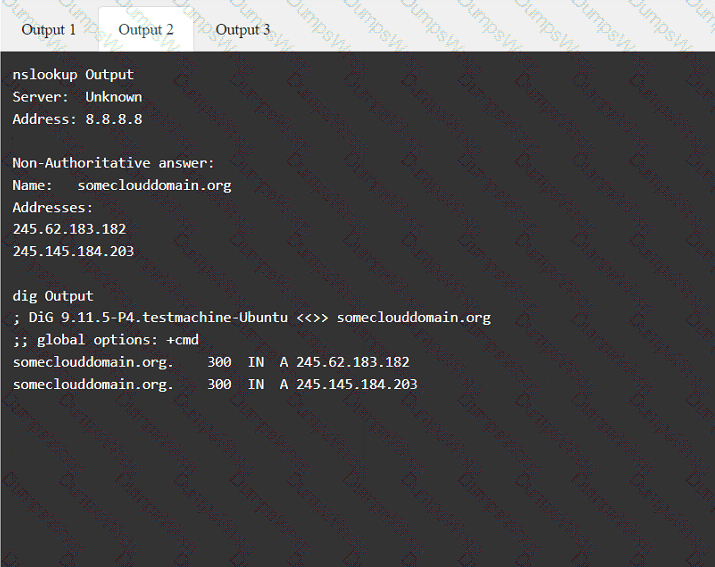
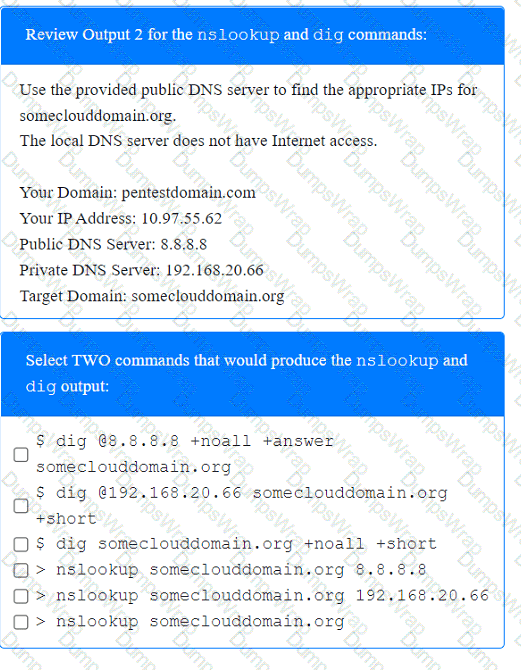
Which of the following are valid reasons for including base, temporal, and environmental CVSS metrics in the findings section of a penetration testing report? (Select two).
During host discovery, a security analyst wants to obtain GeoIP information and a comprehensive summary of exposed services. Which of the following tools is best for this task?
Which of the following scenarios would most likely lead a client to reprioritize goals after a penetration test begins?
A penetration tester needs to scan a remote infrastructure with Nmap. The tester issues the following command:
nmap 10.10.1.0/24
Which of the following is the number of TCP ports that will be scanned?
Which of the following describes the process of determining why a vulnerability scanner is not providing results?
During a security assessment of an e-commerce website, a penetration tester wants to exploit a vulnerability in the web server’s input validation that will allow unauthorized transactions on behalf of the user. Which of the following techniques would most likely be used for that purpose?
During a discussion of a penetration test final report, the consultant shows the following payload used to attack a system:
html
Copy code
7/
Based on the code, which of the following options represents the attack executed by the tester and the associated countermeasure?

 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated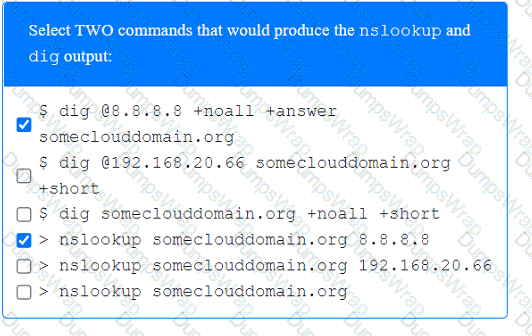 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated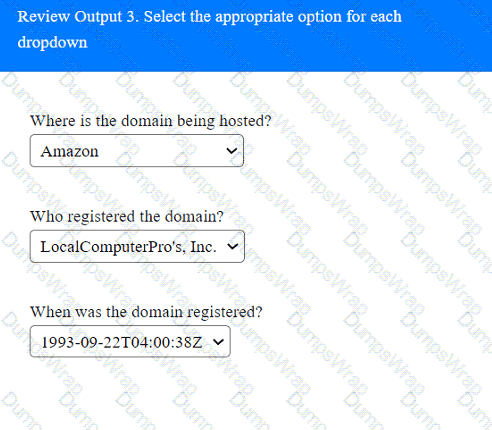 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated