CompTIA Server+ Certification Exam Questions and Answers
A server administrator is trying to determine the cause of a slowdown on a database server. Upon investigation, the administrator determines the issue is in the storage subsystem. Which of the following will most likely resolve this issue?
The management team has requested that new software licenses be purchased out of the capital budget as one-time, non-renewing expenses this year. Which of the following types of software licenses would most likely be used to meet this request?
Which of the following types of locks utilizes key fobs or key cards held against a sensor/reader to gain access?
A video card in an application server was recently replaced. The server administrator is now able to log in locally and view the screen with no issues; however, the administrator notices other performance issues, including the server's slow response time. The administrator reboots the server, but the issues persist. The server's cooling fans are running as normal, and the BIOS shows the dual power supplies are each working at 30%. Which of the following is most likely causing the performance issues?
A server administrator deployed a new product that uses a non-standard port for web access on port 8443. However, users are unable to access the new
application. The server administrator checks firewall rules and determines 8443 is allowed. Which of the following is most likely the cause of the issue?
Which of the following distributes a load across all interfaces?
Which of the following security risks provides unauthorized access to an application?
A site is considered a warm site when it:
has basic technical facilities connected to it.
has faulty air conditioning that is awaiting service.
is almost ready to take over all operations from the primary site.
A technician is troubleshooting a database server that has 12 external disk arrays. Multiple disks are in a degraded state. The server is in a remote colocation facility and has on-site support. The technician notices all of the external storage arrays are degraded, but the internal arrays are functional. Which of the following steps should the technician take next to quickly address this issue?
A technician wants to duplicate a physical server to a remote private cloud for disaster recovery purposes. Which of the following techniques would best accomplish this goal?
Which of the following technologies can successfully back up files that are used by other processes without stopping those processes?
Which of the following is an architectural reinforcement that is used to attempt to conceal the exterior of an organization?
An administrator receives an alert that one of the virtual servers has suddenly crashed. The administrator confirms the data center does not have any power failures and then connects to the remote console of the crashed server After connecting to the server console, which of the following should the administrator complete first?
A systems administrator notices that a SAN is running out of space. There is no additional funding in the budget to upgrade the storage space. Which of the following will significantly reduce the storage space with the least effort? (Select two).
A server recently started sending error messages about running out of memory while in use. After a maintenance period during which more memory was added, the server is still unable to consistently remain powered on. Which of the following should the technician check first?
A technician set up a new multifunction printer. After adding the printer to the print server, the technician configured the printer on each user's machine. Several days later, users reported that they were no longer able to print, but scanning to email worked. Which of the following is most likely causing this issue?
A technician is tasked with upgrading 24 hosts simultaneously with a Type 1 hypervisor. Which of the following protocols should the technician use for this upgrade?
An administrator has deployed a new virtual server from a template. After confirming access to the subnet's gateway, the administrator is unable to log on with the domain credentials. Which of the following is the most likely cause of the issue?
An application server cannot communicate with a newly installed database server. The database server, which has static IP information, is reading the following output from ipconf ig:
The application server is reading the following output from ipconf ig:
Which of the following most likely contains an error?
A technician is installing a large number of servers in a data center with limited rack space. Which of the following would accomplish this goal while using the least amount of space?
Which of the following attacks is the most difficult to mitigate with technology?
An administrator is rebooting servers manually after a group of updates were deployed through SCCM. The administrator notices several of the servers did not receive the deployed update. Which of the following should the administrator review first?
A server technician is placing a newly configured server into a corporate environment. The server will be used by members of the accounting department, who are currently assigned by the VLAN identified below:
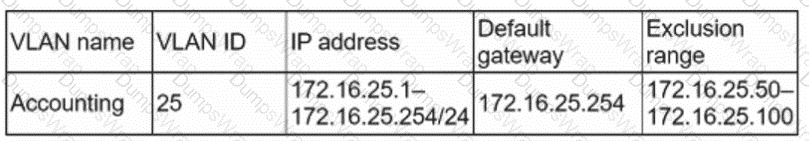
Which of the following IP address configurations should the technician assign to the new server so the members of the accounting group can access the server?
A company needs a media server set up that provides the highest availability with a minimum requirement of at least 10TB. The company purchased five HDDs, each with a 4TB
capacity. Which of the options would provide the highest fault tolerance and meet the requirements?
A Windows server has experienced a BSOD, and the administrator needs to monitor thereboot. The server is in a datacenter with no OOB management. Which of the following tools should the administrator use to complete this task?
A server technician is installing application updates on a Linux server. When the technician tries to install a MySQL update, the GUI displays the following error message: AVC denial. Which of the following should the technician do for the MySQL update to install?
Which of the following should a server administrator configure to ensure access to motherboard software is restricted?
A technician needs to replace two RAID controllers on a database server as part of an upgrade. The server has six external storage arrays and eight internal disks that are controlled by the two RAID controllers. The technician completes the replacement and powers the systems back on, but the server OS detects several missing disks in the configuration. Which of the following steps should the technician take first to resolve this issue?
An administrator notices high traffic on a certain subnet and would like to identify the source of the traffic. Which of the following tools should the administrator utilize?
A server administrator is setting up a disk with enforcement policies on how much data each home share can hold. The amount of data that is redundant on the
server must also be minimized. Which of the following should the administrator perform on the server? (Select two).
A new virtual server was deployed in a perimeter network. Users have reported the time on the server has been incorrect. The engineer has verified the configuration, and the internal time servers are configured properly. Which of the following should the engineer do to resolve this issue?
A systems engineer is configuring a new VLAN for expansion of a campus network. The engineer configures a new DHCP scope on the existing Windows DHCP server cluster and activates the scope for the clients. However, new clients in the area report they are not receiving any DHCP address information. Which of the following should the engineer do first?
A technician is setting up a repurposed server. The minimum requirements are 2TB while ensuring the highest performance and providing support for one drive failure. The technician has the following six drives available:
500GB, 10,000rpm
600GB, 10,000rpm
500GB, 7,200rpm
500GB, 10,000rpm
600GB, 15,000rpm
600GB, 10,000rpm
Which of the following drive selections should the technician utilize to best accomplish this goal?
A systems administrator noticed a new network card is not being recognized by the operating system. Which of the following is most likely the cause?
IDS alerts indicate abnormal traffic patterns are coming from a specific server in a data center that hosts sensitive data. Upon further investigation, the server administrator notices this server has been infected with a virus due to an exploit of a known vulnerability from its database software. Which of the following should the administrator perform after removing the virus to mitigate this issue from reoccurring and to maintain high availability? (Select three).
After a technician upgrades the firmware on a database server that is connected to two external storage arrays, the server prompts the technician to configure RAID. The technician knows the server had several configured RAID sets and thinks the firmware upgrade cleared the RAID configurations. Which of the following should the technician do to troubleshoot this issue?
A server administrator is tasked with upgrading the network on a server to 40Gbps. After installing the card, which of the following connectors should the administrator use?
A systems administrator is selecting an authentication system for a data center. The company’s security policy requires that the system support MFA. Which of the following options should the administrator deploy to meet the policy requirements?
A software developer is unable to reach an internal website. The developer's attempt to ping the FQDN returns the following IP address: 104.18.17.32. Which of the following is the most likely reason for this result?
A corporation is implementing a cloud model that must meet security and privacy requirements for application development and testing. The company would like to use its own hardware to save money. Which of the following cloud models should be deployed?
A Linux server was recently updated. The server now stops during the boot process with a blank screen and an fs> prompt. Which of the following is the most likely cause of this issue?
An analyst is planning a new point-to-point Ethernet connection between a university campus and a newly acquired space downtown that is about 5mi (8km) away. The analyst would like the fastest possible connection speed. Which of the following would best meet the analyst's needs?
Due to a disaster incident on a primary site, corporate users are redirected to cloud services where they will be required to be authenticated just once in order to use all cloud services.
Which of the following types of authentications is described in this scenario?
Multiple users have reported an issue accessing files on a specific server. Which of the following should be the first step in troubleshooting this issue?
A server administrator is replacing a faulty PSU. The management team has asked for a solution that prevents further downtime in the future. Which of the following can the server administrator implement?
Which of the following should be created to understand how long data is stored and how frequently data backups should be scheduled?
A college is planning for disaster recovery and needs to have access at all times to student data, which contains PII (Personally Identifiable Information). Which of the following would be the most appropriate for the college?
A server administrator created a new script and included the path to the script binary as the first line of the script. Which of the following scripting languages did the administrator most likely use?
Several mobile users are reporting intermittent performance issues when attempting to access network shares on the file server. After some investigation, the server administrator notices the server resources are running at maximum capacity, even during non-peak usage times. A recent port scan of the network identified this server as having too many unnecessary ports open to the public. Which of the following is the most likely cause of the performance issues?
A server technician is configuring the IP address on a newly installed server. The documented configuration specifies using an IP address of 10.20.10.15 and a default gateway of 10.20.10.254. Which of the following subnet masks would be appropriate for this setup?
Hosting data in different regional locations but not moving it for long periods of time describes:
Which of the following can be BEST described as the amount of time a company can afford to be down during recovery from an outage?
A server technician installs a new NIC on a server and configures the NIC for IP connectivity. The technician then tests the connection using thepingcommand. Given the following partial output of thepingandipconfigcommands:
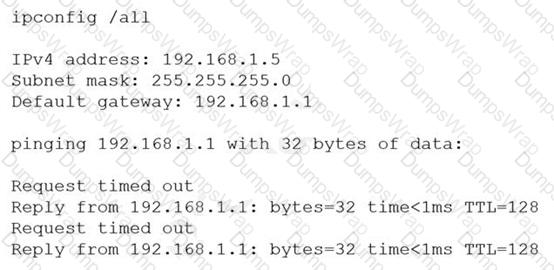
Which of the following caused the issue?
Which of the following access control methodologies can be described BEST as allowing a user the least access based on the jobs the user needs to perform?
A server administrator is completing an OS installation for a new server. The administrator patches the server with the latest vendor-suggested software, configures DHCP, and verifies all network cables are properly connected in the IDF, but there is no network connectivity. Which of the following is the MOST likely reason for the lack of connectivity?
Which of the following must a server administrator do to ensure data on the SAN is not compromised if it is leaked?
A technician is unable to access a server’s package repository internally or externally. Which of the following are the MOST likely reasons? (Choose two.)
A server administrator is installing an OS on a new server. Company policy states no one is to log in directly to the server. Which of the following Installation methods is BEST suited to meet the company policy?
A server administrator mounted a new hard disk on a Linux system with a mount point of /newdisk. It was later determined that users were unable to create directories or files on the new mount point. Which of the following commands would successfully mount the drive with the required parameters?
Which of the following DR testing scenarios is described as verbally walking through each step of the DR plan in the context of a meeting?
An administrator is investigating a physical server mat will not Boot into the OS. The server has three hard drives configured in a RAID 5 array. The server passes POST, out the OS does not load. The administrator verities the CPU and RAM are Doth seated correctly and checks the dual power supplies. The administrator then verifies all the BIOS settings are correct and connects a bootable USB drive in the server, and the OS loads correctly. Which of the following is causing the issue?
A server administrator is configuring a new server that will hold large amounts of information. The server will need to be accessed by multiple users at the same time. Which of the following server roles will the administrator MOST likely need to install?
A system administrator has been alerted to a zero-day vulnerability that is impacting a service enabled on a server OS. Which of the following would work BEST to limit an attacker from exploiting this vulnerability?
An administrator needs to disable root login over SSH. Which of the following tiles should be edited to complete this task?
A server administrator needs to deploy five VMs, all of which must have the same type of configuration. Which of the following would be the MOST efficient way to perform this task?
Which of the following BEST measures now much downtime an organization can tolerate Curing an unplanned outage?
A server administrator needs to create a new folder on a file server that only specific users can access. Which of the following BEST describes how the server administrator can accomplish this task?
A server is reporting a hard drive S.M.A.R.T. error. When a technician checks on the drive, however, it appears that all drives in the server are functioning normally. Which of the following is the reason for this issue?
A server administrator has noticed that the storage utilization on a file server is growing faster than planned. The administrator wants to ensure that, in the future, there is a more direct relationship between the number of users using the server and the amount of space that might be used. Which of the following would BEST enable this correlation?
A company’s IDS has identified outbound traffic from one of the web servers coming over port 389 to an outside address. This server only hosts websites. The company’s SOC administrator has asked a technician to harden this server. Which of the following would be the BEST way to complete this request?
Which of the following are measures that should be taken when a data breach occurs? (Select TWO).
A technician is working on a Linux server. The customer has reported that files in the home directory are missing. The /etc/ f stab file has the following entry:
nfsserver:/home /home nfs defaults 0 0
However, a df -h /home command returns the following information:
/dev/sda2 10G 1G 9G 10% /home
Which of the following should the technician attempt FIRST to resolve the issue?
Which of the following relates to how much data loss a company agrees to tolerate in the event of a disaster?
Users at a company work with highly sensitive data. The security department implemented an administrative and technical control to enforce least-privilege access assigned to files. However, the security department has discovered unauthorized data exfiltration. Which of the following is the BEST way to protect the data from leaking?
An organization implements split encryption keys for sensitive files. Which of the following types of risks does this mitigate?
Which of me following is the BEST action to perform before applying patches to one of the hosts in a high availability cluster?
Following a recent power outage, a server in the datacenter has been constantly going offline and losing its configuration. Users have been experiencing access issues while using the application on the server. The server technician notices the data and time are incorrect when the server is online. All other servers are working. Which of the following would MOST likely cause this issue? (Choose two.)
A server administrator has configured a web server. Which of the following does the administrator need to install to make the website trusted?
A technician needs to provide a VM with high availability. Which of the following actions should the technician take to complete this task as efficiently as possible?
A company wants to deploy software to all users, Out very few of men will be using the software at any one point in time. Which of the following licensing models would be BEST lot the company?
The Chief Information Officer (CIO) of a datacenter is concerned that transmissions from the building can be detected from the outside. Which of the following would resolve this concern? (Choose two.)
A technician is installing a variety of servers in a rack. Which of the following is the BEST course of action for the technician to take while loading the rack?
Which of the following would MOST likely be part of the user authentication process when implementing SAML across multiple applications?
Which of the following steps in the troubleshooting theory should be performed after a solution has been implemented? (Choose two.)
A server technician has been asked to upload a few files from the internal web server to the internal FTP server. The technician logs in to the web server using PuTTY, but the connection to the FTP server fails. However, the FTP connection from the technician’s workstation is suсcessful. To troubleshoot the issue, the technician executes the following command on both the web server and the workstation:
ping ftp.acme.local
The IP address in the command output is different on each machine. Which of the following is the MOST likely reason for the connection failure?
Which of the following encryption methodologies would MOST likely be used to ensure encrypted data cannot be retrieved if a device is stolen?
A server administrator is configuring the IP address on a newly provisioned server in the testing environment. The network VLANs are configured as follows:
The administrator configures the IP address for the new server as follows:
IP address: 192.168.1.1/24
Default gateway: 192.168.10.1
A ping sent to the default gateway is not successful. Which of the following IP address/default gateway combinations should the administrator have used for the new server?
Which of the following allows for a connection of devices to both sides inside of a blade enclosure?
An administrator needs to perform bare-metal maintenance on a server in a remote datacenter. Which of the following should the administrator use to access the server’s console?
Which of the following is an example of load balancing?
A technician needs to deploy an operating system that would optimize server resources. Which of the following server installation methods would BEST meet this requirement?
Which of me following BEST describes a disaster recovery site with a target storage array that receives replication traffic and servers that are only powered on In the event of a disaster?
Users have noticed a server is performing below Baseline expectations. While diagnosing me server, an administrator discovers disk drive performance has degraded. The administrator checks the diagnostics on the RAID controller and sees the battery on me controller has gone bad. Which of the following is causing the poor performance on the RAID array?
An administrator is troubleshooting a RAID issue in a failed server. The server reported a drive failure, and then it crashed and would no longer boot. There are two arrays on the failed server: a two-drive RAIO 0 set tor the OS, and an eight-drive RAID 10 set for data. Which of the following failure scenarios MOST likely occurred?
A technician recently upgraded several pieces of firmware on a server. Ever since the technician rebooted the server, it no longer communicates with the network. Which of the following should the technician do FIRST to return the server to service as soon as possible?
A technician has been asked to check on a SAN. Upon arrival, the technician notices the red LED indicator shows a disk has failed. Which of the following should the technician do NEXT, given the disk is hot swappable?
A server in a remote datacenter is no longer responsive. Which of the following is the BEST solution to investigate this failure?
A very old PC is running a critical, proprietary application in MS-DOS. Administrators are concerned about the stability of this computer. Installation media has been lost, and the vendor is out of business. Which of the following would be the BEST course of action to preserve business continuity?
Which of the following describes a configuration inwinch both nodes of a redundant system respond to service requests whenever possible?
A systems administrator recently installed a new virtual server. After completing the installation, the administrator was only able to reach a few of the servers on the network. While testing, the administrator discovered only servers that had similar IP addresses were reachable. Which of the following is the most likely cause of the issue?
An administrator is investigating several unexpected documents and video files that recently appeared in a network share. The administrator checks the properties of the files and sees the author's name on the documents is not a company employee. The administrator questions the other users, but no one knows anything about the files. The administrator then checks the log files and discovers the FTP protocol was used to copy the files to the server. Which of the following needs to be done to prevent this from happening again?
A developer is creating a web application that will contain five web nodes. The developer's main goal is to ensure the application is always available to the end users. Which ofthefollowing should the developer use when designing the web application?
Which of the following asset management documents is used to identify the location of a serves within a data center?
An administrator receives an alert stating a S.MAR.T. error has been detected. Which of the following should the administrator run FIRST to determine the issue?
Which of the following BEST describes a warm site?
An administrator gave Ann modify permissions to a shared folder called DATA, which is located on the company server. Other users need read access to the files in this folder. The current configuration is as follows:
The administrator has determined Ann cannot write anything to the DATA folder using the network. Which of the following would be the best practice to set up Ann's permissions correctly, exposing only the minimum rights required?
A staff memberwho a monitoring a data center reports one rack is experiencing higher temperatures than the racks next to it, despite the hardware in each rack being the same. Which of the following actions would MOST likely remediate the heal issue?
A server administrator is creating a new server that will be used to house customer sales records. Which of the following roles will MOST likely be Installed on the server?
A technician installed a kernel upgrade to a Linux server. The server now crashes regularly. Which of the following is the most likely cause?
A server administrator needs to ensure all Window-based servers within a data center have RDP disabled. There are thousands of servers performing various roles. Which of the following is the best way to meet this requirement?
Which of the following backup methods protects all the changes that have occurred since the last full backup?
A systems administrator needs to create a data volume out of four disks with the MOST redundancy. Which of the following is the BEST solution?
Which of the following backup types copies changed data from a server and then combines the backups on the backup target?
A server administrator wants to check the open ports on a server. Which of the following commands should the administrator use to complete the task?
A Linux server was recently updated. Now, the server stops during the boot process with a blank screen and an f prompt. Which of the following is the most likely cause of this issue?
Which of the following often-overlooked parts of the asset life cycle can cause the greatest number of issues in relation to Pll exposure?
The Chief Information Officer of a data center is concerned that transmissions from the building can be detected from the outside. Which of the
following would resolve this concern? (Select TWO).
Which of the following script types would MOST likely be used on a modern Windows server OS?
A systems administrator needs to back up changes made to a data store on a daily basis during a short time frame. The administrator wants to maximize RTO when restoring data. Which of the following backup methodologies would best fit this scenario?
A technicianretailed a new4TBharddrive inaWindows server. Which of the following should the technician perform FIRST to provision the newdrive?
Two developers are working together on a project, and they have built out a set of snared servers that both developers can access over the internet. Which of the following cloud models is this an example of?
An administrator is working on improving the security of a new domain controller. A report indicates several open ports on the server. Which of the following ports should the administrator disable?
A server administrator just installed a new physical server and needs to harden the applications on the server. Which of the following best describes a method of application hardening?
A technician is creating a network snare that will be used across both Unix and Windows clients at the same time. Users need read and write access to the files. Which of the following would be BEST for the technician to deploy?
A change in policy requires a complete backup of the accounting server every seven days and a backup of modified data every day. Which of the following would be BEST to restore a full backup as quickly as possible in the event of a complete loss of server data?
An administrate is helping to replicate a large amount of data between two Windows servers. The administrator is unsure how much data has already been transferred. Which of the following will BEST ensure all the data is copied consistently?
Which of the following script types uses commands That start with sec-?
The management team has mandated the use of data-at-rest encryption on all corporate servers. Using this encryption paradigm will ensure:
Corporate policy mandates that logs from all servers be available for review regardless of the state of the server. Which of the following must be configured to comply with this policy?
An organization purchased six new 4TB drives for a server. An administrator is tasked with creating an efficient RAID given the minimum disk space requirement of 19TBs. Which of the following should the administrator choose to get the most efficient use of space?
After installing a new file server, a technician notices the read times for accessing the same file are slower than the read times for other file servers.
Which of the following is the first step the technician should take?
An administrator notices nigh traffic on a certain subnetand wouldlike to identify the source of the traffic. Which of the following tools should the administrator utilize?
A user logs in to a Linux server and attempts to run the following command:
sudo emacs /root/file
However the user gets the following message:
User userid is not allowed to execute Temacs' on this server. Which of the following would BEST allow the user to find out which commands can be used?
An administrator has been asked to verify that all traffic egressing from a company is secured. The administrator confirms all the information that is sent over the network is encrypted. Which of the following describes the type of traffic being encrypted?
Users are able to connect to the wireless network, but they are unable to access the internet. The network administrator verifies connectivity to all network devices, and there are no ISP outages. The server administrator removes the old address leases from the active leases pool, which allows users to access the internet. Which of the following is most likely causing the internet issue?
A security technician generated a public/private key pair on a server. The technician needs to copy the key pair to another server on a different subnet. Which of the following is the most secure method to copy the keys?
HTTP
A VLAN needs to be configured within a virtual environment for a new VM. Which of the following will ensure the VM receives a correct IP address?
A server administrator has a system requirement lo install the virtual OS on Dare metalhardware.Which of the following hypervisor virtualization technologies should the administrator use to BEST meet the system requirements? (Select TWO)
Which of the following BEST measures how much downtime an organization can tolerate during an unplanned outage?
A junior administrator needs to configure a single RAID 5 volume out of four 200GB drives attached to the server using the maximum possible capacity. Upon completion, the server reports that all drives were used, and the approximate volume size is 400GB. Which of the following BEST describes the result of this configuration?
A server administrator purchased a single license key to use for all the new servers that will be imaged this year. Which of the following MOST likely refers to the licensing type that will be used?
A technician needs to install a Type 1 hypervisor on a server. The server has SD card slots, a SAS controller, and a SATA controller, and it is attached to a NAS. On which of the following drive types should the technician install the hypervisor?
Which of the following BEST describes overprovisioning in a virtual server environment?
A server administrator is building a pair of new storage servers. The servers will replicate; therefore, no redundancy is required, but usable capacity
must be maximized. Which of the following RAID levels should the server administrator implement?
The HIDS logs on a server indicate a significant number of unauthorized access attempts via USB devices at startup. Which of the following steps should a server administrator take to BEST secure the server without limiting functionality?
A Linux server was recently updated. Now, the server stops during the boot process with a blank screen and an£s> prompt. When of the following is the MOST likely cause of this issue?
Which of the following licensing models is MOST appropriate tor a data center that has a variable daily equipment count?

