CompTIA Security+ Exam 2025 Questions and Answers
While reviewing a recent compromise, a forensics team discovers that there are hard-coded credentials in the database connection strings. Which of the following assessment types should be performed during software development to prevent this from reoccurring?
As part of new compliance audit requirements, multiple servers need to be segmented on different networks and should be reachable only from authorized internal systems. Which of the following would meet the requirements?
Which of the following would be the best way to block unknown programs from executing?
A network manager wants to protect the company's VPN by implementing multifactor authentication that uses:
. Something you know
. Something you have
. Something you are
Which of the following would accomplish the manager's goal?
A business received a small grant to migrate its infrastructure to an off-premises solution. Which of the following should be considered first?
Company A jointly develops a product with Company B, which is located in a different country. Company A finds out that their intellectual property is being shared with unauthorized companies. Which of the following has been breached?
A customer reports that software the customer downloaded from a public website has malware in it. However, the company that created the software denies any malware in its software at delivery time. Which of the following techniques will address this concern?
The Chief Information Security Officer (CISO) requires that new servers include hardware-level memory encryption. Which of the following data states does the CISO want to protect?
Which of the following would best ensure a controlled version release of a new software application?
Which solution is most likely used in the financial industry to mask sensitive data?
Which of the following can be used to compromise a system that is running an RTOS?
Which of the following would most likely be used by attackers to perform credential harvesting?
A security manager needs an automated solution that will take immediate action to protect an organization against inbound malicious traffic. Which of the following is the best solution?
Which of the following should be used to ensure that a device is inaccessible to a network-connected resource?
An organization is leveraging a VPN between its headquarters and a branch location. Which of the following is the VPN protecting?
Which of the following architecture models ensures that critical systems are physically isolated from the network to prevent access from users with remote access privileges?
Which of the following is the best safeguard to protect against an extended power failure?
Which of the following is the best way to validate the integrity and availability of a disaster recovery site?
Which of the following activities should a systems administrator perform to quarantine a potentially infected system?
Which of the following would most likely be deployed to obtain and analyze attacker activity and techniques?
A Chief Information Security Officer wants to monitor the company's servers for SQLi attacks and allow for comprehensive investigations if an attack occurs. The company uses SSL decryption to allow traffic monitoring. Which of the following strategies would best accomplish this goal?
Which of the following is used to protect a computer from viruses, malware, and Trojans being installed and moving laterally across the network?
After a security incident, a systems administrator asks the company to buy a NAC platform. Which of the following attack surfaces is the systems administrator trying to protect?
A penetration tester was able to gain unauthorized access to a hypervisor platform. Which of the following vulnerabilities was most likely exploited?
The Chief Information Security Officer (CISO) at a large company would like to gain an understanding of how the company's security policies compare to the requirements imposed by external regulators. Which of the following should the CISO use?
Which of the following steps in the risk management process involves establishing the scope and potential risks involved with a project?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
A company’s legal department drafted sensitive documents in a SaaS application and wants to ensure the documents cannot be accessed by individuals in high-risk countries. Which of the following is the most effective way to limit this access?
Which of the following is a primary security concern for a company setting up a BYOD program?
An unknown source has attacked an organization’s network multiple times. The organization has a firewall but no other source of protection against these attacks. Which of the following is the best security item to add?
A security manager is implementing MFA and patch management. Which of the following would best describe the control type and category? (Select two).
Which of the following aspects of the data management life cycle is most directly impacted by local and international regulations?
A company uses its backups to recover from a ransomware attack. Which of the following best guarantees that the backups are not infected?
Which of the following techniques would identify whether data has been modified in transit?
A malicious update was distributed to a common software platform and disabled services at many organizations. Which of the following best describes this type of vulnerability?
A company is developing a critical system for the government and storing project information on a fileshare. Which of the following describes how this data will most likely be classified? (Select two).
Which of the following roles, according to the shared responsibility model, is responsible for securing the company’s database in an IaaS model for a cloud environment?
A company makes a change during the appropriate change window, but the unsuccessful change extends beyond the scheduled time and impacts customers. Which of the following would prevent this from reoccurring?
A company is developing a business continuity strategy and needs to determine how many staff members would be required to sustain the business in the case of a disruption. Which of the following best describes this step?
A systems administrator notices that one of the systems critical for processing customer transactions is running an end-of-life operating system. Which of the following techniques would increase enterprise security?
Which of the following agreements defines response time, escalation points, and performance metrics?
A security analyst created a fake account and saved the password in a non-readily accessible directory in a spreadsheet. An alert was also configured to notify the security team if the spreadsheet is opened. Which of the following best describes the deception method being deployed?
Which of the following teams combines both offensive and defensive testing techniques to protect an organization's critical systems?
Which of the following is the best way to remove personal data from a social media account that is no longer being used?
Which of the following is the first step to secure a newly deployed server?
A security analyst needs to improve the company’s authentication policy following a password audit. Which of the following should be included in the policy? (Select two).
Which of the following security measures is required when using a cloud-based platform for loT management?
Which of the following should a security team do first before a new web server goes live?
Which of the following is the most likely motivation for a hacktivist?
Which of the following should a security analyst consider when prioritizing remediation efforts against known vulnerabilities?
Various stakeholders are meeting to discuss their hypothetical roles and responsibilities in a specific situation, such as a security incident or major disaster. Which of the following best describes this meeting?
Which of the following best describe why a process would require a two-person integrity security control?
An attacker posing as the Chief Executive Officer calls an employee and instructs the employee to buy gift cards. Which of the following techniques is the attacker using?
A security analyst receives an alert from a web server that contains the following logs:
GET /image?filename=../../../etc/passwd
Host: AcmeInc.web.net
useragent: python-request/2.27.1
GET /image?filename=../../../etc/shadow
Host: AcmeInc.web.net
useragent: python-request/2.27.1
Which of the following attacks is being attempted?
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device's drive if the device is lost?
Which of the following agreement types defines the time frame in which a vendor needs to respond?
A company that has a large IT operation is looking to better control, standardize, and lower the time required to build new servers. Which of the following architectures will best achieve the company’s objectives?
A systems administrate wants to implement a backup solution. the solution needs to allow recovery of the entire system, including the operating system, in case of a disaster. Which of the following backup types should the administrator consider?
An external security assessment report indicates a high click rate on suspicious emails. The Chief Intelligence Security Officer (CISO) must reduce this behavior. Which of the following should the CISO do first?
A company has begun labeling all laptops with asset inventory stickers and associating them with employee IDs. Which of the following security benefits do these actions provide? (Choose two.)
A company prevented direct access from the database administrators’ workstations to the network segment that contains database servers. Which of the following should a database administrator use to access the database servers?
An IT manager is putting together a documented plan describing how the organization will keep operating in the event of a global incident. Which of the following plans is the IT manager creating?
A security analyst is reviewing the following logs about a suspicious activity alert for a user's VPN log-ins. Which of the following malicious activity indicators triggered the alert?
✅Log Summary:
User logs in fromChicago, ILmultiple times, then suddenly a successful login appears fromRome, Italy, followed again by Chicago logins — all within ashort time span.
After reviewing the following vulnerability scanning report:
Server:192.168.14.6
Service: Telnet
Port: 23 Protocol: TCP
Status: Open Severity: High
Vulnerability: Use of an insecure network protocol
A security analyst performs the following test:
nmap -p 23 192.168.14.6 —script telnet-encryption
PORT STATE SERVICE REASON
23/tcp open telnet syn-ack
I telnet encryption:
| _ Telnet server supports encryption
Which of the following would the security analyst conclude for this reported vulnerability?
Which of the following is the most likely benefit of conducting an internal audit?
An employee receives a text message from an unknown number claiming to be the company's Chief Executive Officer and asking the employee to purchase several gift cards. Which of the following types of attacks does this describe?
Which of the following should a company use to provide proof of external network security testing?
The local administrator account for a company's VPN appliance was unexpectedly used to log in to the remote management interface. Which of the following would have most likely prevented this from happening'?
A growing company would like to enhance the ability of its security operations center to detect threats but reduce the amount of manual work required tor the security analysts. Which of the following would best enable the reduction in manual work?
Employees sign an agreement that restricts specific activities when leaving the company. Violating the agreement can result in legal consequences. Which of the following agreements does this best describe?
A company is expanding its threat surface program and allowing individuals to security test the company’s internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
A systems administrator is creating a script that would save time and prevent human error when performing account creation for a large number of users. Which of the following would be a good use case for this task?creating a script
Which of the following can best protect against an employee inadvertently installing malware on a company system?
A systems administrator discovers a system that is no longer receiving support from the vendor. However, this system and its environment are critical to running the business, cannot be modified, and must stay online. Which of the following risk treatments is the most appropriate in this situation?
The Chief Information Security Officer wants to put security measures in place to protect PlI. The organization needs to use its existing labeling and classification system to accomplish this goal. Which of the following would most likely be configured to meet the requirements?
An enterprise security team is researching a new security architecture to better protect the company's networks and applications against the latest cyberthreats. The company has a fully remote workforce. The solution should be highly redundant and enable users to connect to a VPN with an integrated, software-based firewall. Which of the following solutions meets these requirements?
A security administrator needs a method to secure data in an environment that includes some form of checks so that the administrator can track any changes. Which of the following should the administrator set up to achieve this goal?
A data administrator is configuring authentication for a SaaS application and would like to reduce the number of credentials employees need to maintain. The company prefers to use domain credentials to access new SaaS applications. Which of the following methods would allow this functionality?
Which of the following is used to add extra complexity before using a one-way data transformation algorithm?
A security analyst sees an increase of vulnerabilities on workstations after a deployment of a company group policy. Which of the following vulnerability types will the analyst most likely find on the workstations?
A Chief Security Officer signs off on a request to allow inbound SMB and RDP from the internet to a single VLAN. Which of the following is the most likely explanation for this activity?
A security engineer configured a remote access VPN. The remote access VPN allows end users to connect to the network by using an agent that is installed on the endpoint, which establishes an encrypted tunnel. Which of the following protocols did the engineer most likely implement?
A security officer is implementing a security awareness program and is placing security-themed posters around the building and is assigning online user training. Which of the following would the security officer most likely implement?
Which of the following is the phase in the incident response process when a security analyst reviews roles and responsibilities?
A company wants to reduce the time and expense associated with code deployment. Which of the following technologies should the company utilize?
A company implemented an MDM policy 10 mitigate risks after repealed instances of employees losing company-provided mobile phones. In several cases. The lost phones were used maliciously to perform social engineering attacks against other employees. Which of the following MDM features should be configured to best address this issue? (Select two).
While reviewing logs, a security administrator identifies the following code:
Which of the following best describes the vulnerability being exploited?
A cyber operations team informs a security analyst about a new tactic malicious actors are using to compromise networks.
SIEM alerts have not yet been configured. Which of the following best describes what the security analyst should do to identify this behavior?
Which of the following should a security operations center use to improve its incident response procedure?
During a recent company safety stand-down, the cyber-awareness team gave a presentation on the importance of cyber hygiene. One topic the team covered was best practices for printing centers. Which of the following describes an attack method that relates to printing centers?
A company is concerned about the theft of client data from decommissioned laptops. Which of the following is the most cost-effective method to decrease this risk?
While updating the security awareness training, a security analyst wants to address issues created if vendors' email accounts are compromised. Which of the following recommendations should the security analyst include in the training?
Which of the following automation use cases would best enhance the security posture of an organization by rapidly updating permissions when employees leave a company?
During a penetration test in a hypervisor, the security engineer is able to inject a malicious payload and access the host filesystem. Which of the following best describes this vulnerability?
A security engineer needs to quickly identify a signature from a known malicious file. Which of the following analysis methods would the security engineer most likely use?
An organization is required to provide assurance that its controls are properly designed and operating effectively. Which of the following reports will best achieve the objective?
A security analyst learns that an attack vector, used as part of a recent incident, was a well-known IoT device exploit. The analyst needs to review logs to identify the time of the initial exploit. Which of the following logs should the analyst review first?
Which of the following should be used to ensure a device is inaccessible to a network-connected resource?
A network administrator deploys an FDE solution on all end user workstations. Which of the following data protection strategies does this describe?
A bank insists all of its vendors must prevent data loss on stolen laptops. Which of the following strategies is the bank requiring?
An organization failed to account for the right-to-be-forgotten regulations. Which of the following impacts might this action have on the company?
The security operations center is researching an event concerning a suspicious IP address A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced faded log-In attempts when authenticating from the same IP address:

Which of the following most likely describes attack that took place?
Which of the following is a common data removal option for companies that want to wipe sensitive data from hard drives in a repeatable manner but allow the hard drives to be reused?
A security officer observes that a software development team is not complying with its corporate security policy on encrypting confidential data. Which of the following categories refers to this type of non-compliance?
Which of the following is the most relevant reason a DPO would develop a data inventory?
Which of the following uses proprietary controls and is designed to function in harsh environments over many years with limited remote access management?
Which of the following security concepts is accomplished with the installation of a RADIUS server?
Which of the following security controls is a company implementing by deploying HIPS? (Select two)
Which of the following would be the best ways to ensure only authorized personnel can access a secure facility? (Select two).
In which of the following will unencrypted PLC management traffic most likely be found?
Which of the following are cases in which an engineer should recommend the decommissioning of a network device? (Select two).
A security practitioner completes a vulnerability assessment on a company’s network and finds several vulnerabilities, which the operations team remediates. Which of the following should be done next?
After an audit, an administrator discovers all users have access to confidential data on a file server. Which of the following should the administrator use to restrict access to the data quickly?
A security analyst is examining a penetration test report and notices that the tester pivoted to critical internal systems with the same local user ID and password. Which of the following would help prevent this in the future?
Which vulnerability is most likely mitigated by setting up an MDM platform?
Which of the following should be used to select a label for a file based on the file's value, sensitivity, or applicable regulations?
An important patch for a critical application has just been released, and a systems administrator is identifying all of the systems requiring the patch. Which of the following must be maintained in order to ensure that all systems requiring the patch are updated?
Following a security review, an organization must ensure users verify their identities against the company's identity services with individual credentials leveraging WPA2-Enterprise for wireless access. Which of the following configuration steps correctly applies RADIUS in this environment?
A systems administrator is auditing all company servers to ensure. They meet the minimum security baseline While auditing a Linux server, the systems administrator observes the /etc/shadow file has permissions beyond the baseline recommendation. Which of the following commands should the systems administrator use to resolve this issue?
Visitors to a secured facility are required to check in with a photo ID and enter the facility through an access control vestibule Which of the following but describes this form of security control?
The marketing department set up its own project management software without telling the appropriate departments. Which of the following describes this scenario?
An organization recently started hosting a new service that customers access through a web portal. A security engineer needs to add to the existing security devices a new solution to protect this new service. Which of the following is the engineer most likely to deploy?
Sine© a recent upgrade (o a WLAN infrastructure, several mobile users have been unable to access the internet from the lobby. The networking team performs a heat map survey of the building and finds several WAPs in the area. The WAPs are using similar frequencies with high power settings. Which of the following installation considerations should the security team evaluate next?
Which of the following technologies assists in passively verifying the expired status of a digital certificate?
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
According to various privacy rules and regulations, users have the power to request that all data pertaining to them is deleted. This is known as:
Which of the following describes a situation where a user is authorized before being authenticated?
Which of the following threat actors is the most likely to be hired by a foreign government to attack critical systems located in other countries?
Which of the following is best used to detect fraud by assigning employees to different roles?
A security analyst investigates abnormal outbound traffic from a corporate endpoint. The traffic is encrypted and uses non-standard ports. Which of the following data sources should the analyst use first to confirm whether this traffic is malicious?
A company wants to ensure secure remote access to its internal network. The company has only one public IP and would like to avoid making any changes to the current network setup. Which of the following solutions would best accomplish this goal?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
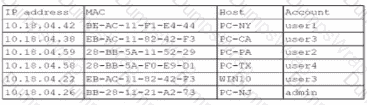
Which of the following is the most likely way a rogue device was allowed to connect?
Which of the following provides the best protection against unwanted or insecure communications to and from a device?
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were Inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while Inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following Is the most likely reason for this compromise?
A penetration tester begins an engagement by performing port and service scans against the client environment according to the rules of engagement. Which of the following reconnaissance types is the tester performing?
A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
A security analyst receives alerts about an internal system sending a large amount of unusual DNS queries to systems on the internet over short periods of time during non-business hours. Which of the following is most likely occurring?
A systems administrator is concerned users are accessing emails through a duplicate site that is not run by the company. Which of the following is used in this scenario?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
During a routine audit, an analyst discovers that a department at a high school uses a simul-ation program that was not properly vetted before deployment.
Which of the following threats is this an example of?
A security administrator needs to reduce the attack surface in the company's data centers. Which of the following should the security administrator do to complete this task?
A penetration testing report indicated that an organization should implement controls related to database input validation. Which of the following best identifies the type of vulnerability that was likely discovered during the test?
Which of the following would best prepare a security team for a specific incident response scenario?
A security administrator is deploying a DLP solution to prevent the exfiltration of sensitive customer data. Which of the following should the administrator do first?
A security team purchases a tool for cloud security posture management. The team is quickly overwhelmed by the number of misconfigurations that the tool detects. Which of the following should the security team configure to establish workflows for cloud resource security?
A company is in the process of migrating to cloud-based services. The company's IT department has limited resources for migration and ongoing support. Which of the following best meets the company's needs?
Which of the following technologies must be used in an organization that intends to automate infrastructure deployment?
A company processes and stores sensitive data on its own systems. Which of the following steps should the company take first to ensure compliance with privacy regulations?
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device.
Which of the following best describes the user’s activity?
A company is considering an expansion of access controls for an application that contractors and internal employees use to reduce costs. Which of the following risk elements should the implementation team understand before granting access to the application?
When trying to access an internal website, an employee reports that a prompt displays, stating that the site is insecure. Which of the following certificate types is the site most likely using?
A security administrator is addressing an issue with a legacy system that communicates data using an unencrypted protocol to transfer sensitive data to a third party. No software updates that use an encrypted protocol are available, so a compensating control is needed. Which of the following are the most appropriate for the administrator to suggest? (Select two.)
A software developer released a new application and is distributing application files via the developer’s website. Which of the following should the developer post on the website to allow users to verify the integrity of the downloaded files?
An organization wants to deploy software in a container environment to increase security. Which of the following will limit the organization's ability to achieve this goal?
Which of the following techniques would attract the attention of a malicious attacker in an insider threat scenario?
Which of the following are the most important considerations when encrypting data? (Select two).
Which of the following can a security director use to prioritize vulnerability patching within a company's IT environment?
During a recent log review, an analyst discovers evidence of successful injection attacks. Which of the following will best address this issue?
An administrator discovers that some files on a database server were recently encrypted. The administrator sees from the security logs that the data was last accessed by a domain user. Which of the following best describes the type of attack that occurred?
A security consultant is working with a client that wants to physically isolate its secure systems. Which of the following best describes this architecture?
A company is aware of a given security risk related to a specific market segment. The business chooses not to accept responsibility and target their services to a different market segment. Which of the following describes this risk management strategy?
A systems administrator notices that the research and development department is not using the company VPN when accessing various company-related services and systems. Which of the following scenarios describes this activity?
Which of the following hardening techniques must be applied on a container image before deploying it to a production environment? (Select two).
An administrator wants to automate an account permissions update for a large number of accounts. Which of the following would best accomplish this task?
An attorney prints confidential documents to a copier in an office space near multiple workstations and a reception desk. When the attorney goes to the copier to retrieve the documents, the documents are missing. Which of the following would best prevent this from reoccurring?
A company's Chief Information Security Officer (CISO) wants to enhance the capabilities of the incident response team. The CISO directs the incident response team to deploy a tool that rapidlyanalyzes host and network data from potentially compromised systems and forwards the data for further review. Which of the following tools should the incident response team deploy?
Which of the following is the most likely to be included as an element of communication in a security awareness program?
A security analyst is reviewing logs and discovers the following:

Which of the following should be used lo best mitigate this type of attack?
Which of the following data protection strategies can be used to confirm file integrity?
Which of the following is a reason why a forensic specialist would create a plan to preserve data after an modem and prioritize the sequence for performing forensic analysis?
An administrator investigating an incident is concerned about the downtime of a critical server due to a failed drive. Which of the following would the administrator use to estimate the time needed to fix the issue?
For which of the following reasons would a systems administrator leverage a 3DES hash from an installer file that is posted on a vendor's website?
Which of the following threat actors is the most likely to use large financial resources to attack critical systems located in other countries?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
Which of the following methods to secure credit card data is best to use when a requirement is to see only the last four numbers on a credit card?
A systems administrator receives an alert that a company's internal file server is very slow and is only working intermittently. The systems administrator reviews the server management software and finds the following information about the server:
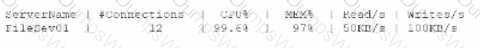
Which of the following indicators most likely triggered this alert?
Which of the following activities uses OSINT?
Which of the following can automate vulnerability management?
A security team created a document that details the order in which critical systems should be through back online after a major outage. Which of the following documents did the team create?
After a recent ransomware attack on a company's system, an administrator reviewed the log files. Which of the following control types did the administrator use?
Which of the following is the first step to take when creating an anomaly detection process?
Which of the following is a directive managerial control?
Which of the following should an organization focus on the most when making decisions about vulnerability prioritization?
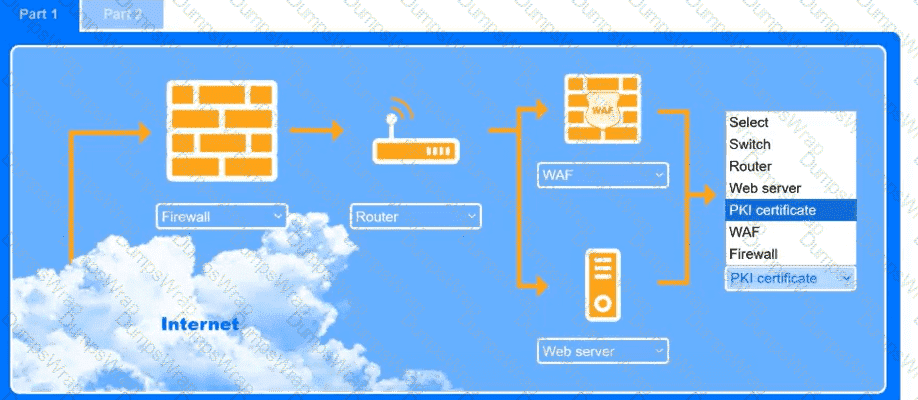
A recent black-box penetration test of discovered that external
website vulnerabilities exist, such as directory traversals, cross-site scripting, cross-site forgery, and insecure protocols.
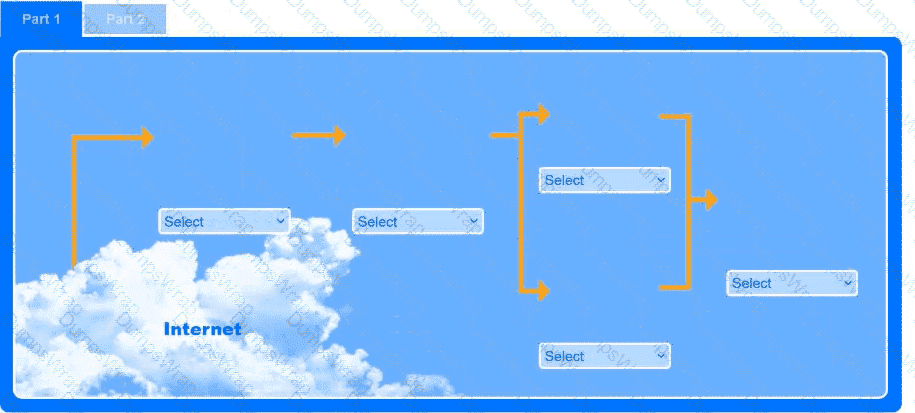
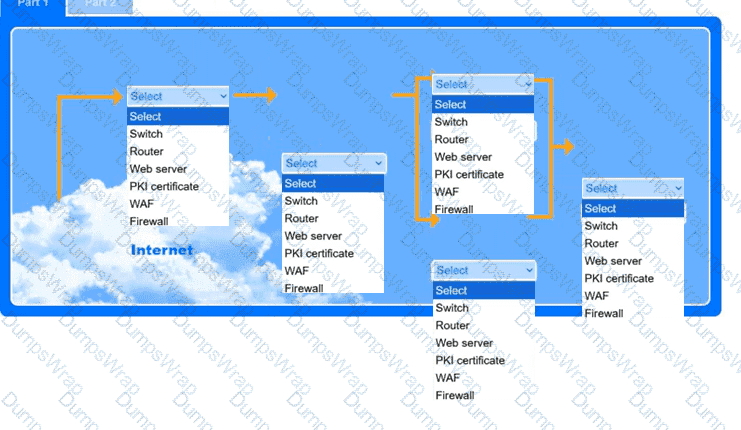
You are tasked with reducing the attack space and enabling secure protocols.
INSTRUCTIONS
Part 1
Use the drop-down menus to select the appropriate technologies for each location to implement a secure and resilient web architecture. Not all technologies will be used, and technologies may be used multiple times.
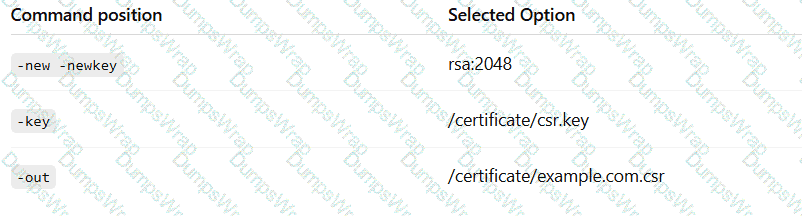
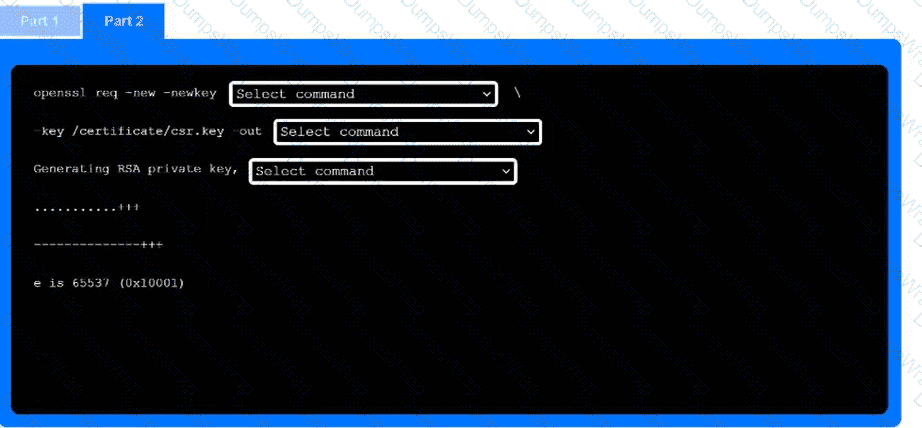
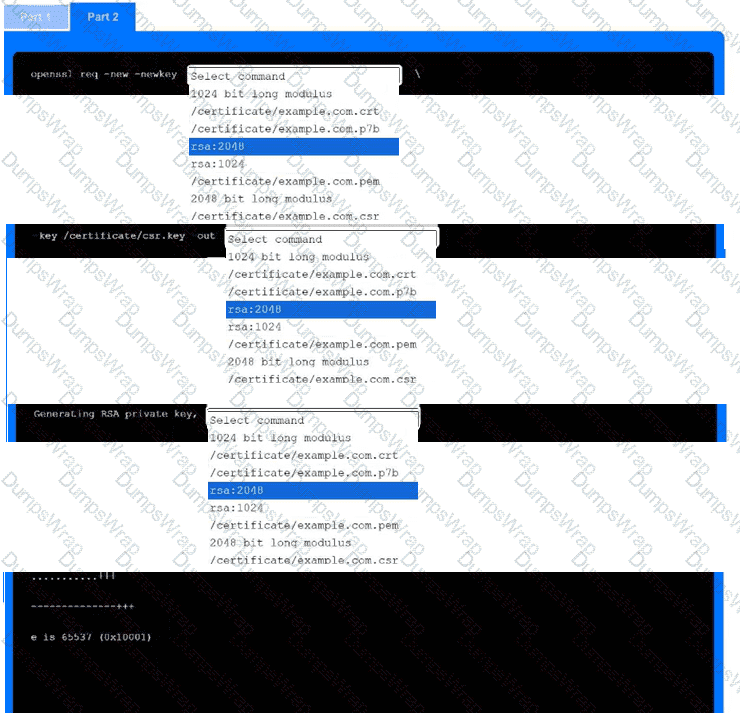
Part 2
Use the drop-down menus to select the appropriate command snippets from the drop-down menus. Each command section must be filled.
An employee receives a text message that appears to have been sent by the payroll department and is asking for credential verification. Which of the following social engineering techniques are being attempted? (Choose two.)
Which of the following is a reason environmental variables are a concern when reviewing potential system vulnerabilities?
An employee decides to collect PII data from the company's system for personal use. The employee compresses the data into a single encrypted file before sending the file to their personal email. The security department becomes aware of the attempted misuse and blocks the attachment from leaving the corporate environment. Which of the following types of employee training would most likely reduce the occurrence of this type of issue?
(Select two).
An organization issued new laptops to all employees and wants to provide web filtering both in and out of the office without configuring additional access to the network. Which of the following types of web filtering should a systems administrator configure?
An organization wants to limit potential impact to its log-in database in the event of a breach. Which of the following options is the security team most likely to recommend?
Which of the following actions must an organization take to comply with a person's request for the right to be forgotten?
A government official receives a blank envelope containing photos and a note instructing the official to wire a large sum of money by midnight to prevent the photos from being leaked on the Internet. Which of the following best describes the threat actor's intent?
Which of the following would enable a data center to remain operational through a multiday power outage?
An engineer needs to find a solution that creates an added layer of security by preventing unauthorized access to internal company resources. Which of the following would be the best solution?
During a routine audit, an analyst discovers that a department uses software that was not vetted. Which threat is this?
An organization’s internet-facing website was compromised when an attacker exploited a buffer overflow. Which of the following should the organization deploy to best protect against similar attacks in the future?
Which of the following actions best addresses a vulnerability found on a company's web server?
A company wants to protect a specialized legacy platform that controls the physical flow of gas inside of pipes. Which of the following environments does the company need to secure to best achieve this goal?
Which of the following security principles most likely requires validation before allowing traffic between systems?
A company's accounts payable clerk receives a message from a vendor asking to change their bank account before paying an invoice. The clerk makes the change and sends the payment to the new account. Days later, the clerk receives another message from the same vendor with a request for a missing payment to the original bank account. Which of the following has most likely occurred?
A company discovered its data was advertised for sale on the dark web. During the initial investigation, the company determined the data was proprietary data. Which of the following is the next step the company should take?
The internal audit team determines a software application is no longer in scope for external reporting requirements. Which of the following will confirm management’s perspective that the application is no longer applicable?
The Chief Information Security Officer wants to discuss options for a disaster recovery site that allows the business to resume operations as quickly as possible. Which of the following solutions meets this requirement?
Which of the following Is a common, passive reconnaissance technique employed by penetration testers in the early phases of an engagement?
A vendor salesperson is a personal friend of a company’s Chief Financial Officer (CFO). The company recently made a large purchase from the vendor, which was directly approved by the CFO. Which of the following best describes this situation?
Which of the following provides the details about the terms of a test with a third-party penetration tester?
A company is considering an expansion of access controls for an application that contractors and internal employees use to reduce costs. Which of the following risk elements should the implementation team understand before granting access to the application?
A systems administrator is redesigning now devices will perform network authentication. The following requirements need to be met:
• An existing Internal certificate must be used.
• Wired and wireless networks must be supported
• Any unapproved device should be Isolated in a quarantine subnet
• Approved devices should be updated before accessing resources
Which of the following would best meet the requirements?
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
Which of the following can best contribute to prioritizing patch applications?
An analyst is reviewing an incident in which a user clicked on a link in a phishing email. Which of the following log sources would the analyst utilize to determine whether the connection was successful?
A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
While a school district is performing state testing, a security analyst notices all internet services are unavailable. The analyst discovers that ARP poisoning is occurring on the network and then terminates access for the host. Which of the following is most likely responsible for this malicious activity?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
Which of the following describes the process of concealing code or text inside a graphical image?
A security administrator recently reset local passwords and the following values were recorded in the system:
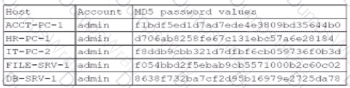
Which of the following in the security administrator most likely protecting against?
A legacy device is being decommissioned and is no longer receiving updates or patches. Which of the following describes this scenario?
Which of the following describes the reason for using an MDM solution to prevent jailbreaking?
A healthcare organization wants to provide a web application that allows individuals to digitally report health emergencies.
Which of the following is the most important consideration during development?
A user is attempting to patch a critical system, but the patch fails to transfer. Which of the following access controls is most likely inhibiting the transfer?
A systems administrator needs to encrypt all data on employee laptops. Which of the following encryption levels should be implemented?
An organization is looking to optimize its environment and reduce the number of patches necessary for operating systems. Which of the following will best help to achieve this objective?
An organization implemented cloud-managed IP cameras to monitor building entry points and sensitive areas. The service provider enables direct TCP/IP connection to stream live video footage from each camera. The organization wants to ensure this stream is encrypted and authenticated. Which of the following protocols should be implemented to best meet this objective?
An organization would like to calculate the time needed to resolve a hardware issue with a server. Which of the following risk management processes describes this example?
Which of the following security controls would best guard a payroll system against insider manipulation threats?
An MSSP manages firewalls for hundreds of clients. Which of the following tools would be most helpful to create a standard configuration template in order to improve the efficiency of firewall changes?
A company wants to improve the availability of its application with a solution that requires minimal effort in the event a server needs to be replaced or added. Which of the following would be the best solution to meet these objectives?
Which of the following is a prerequisite for a DLP solution?