CyberArk CDE Recertification Questions and Answers
You want to generate a license capacity report.
Which tool accomplishes this?
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
Assuming a safe has been configured to be accessible during certain hours of the day, a Vault Admin may still access that safe outside of those hours.
You are installing multiple PVWAs behind a load balancer. Which statement is correct?
Which is the primary purpose of exclusive accounts?
Which report provides a list of account stored in the vault.
For Digital Vault Cluster in a high availability configuration, how does the cluster determine if a node is down?
You need to enable the PSM for all platforms. Where do you perform this task?
You need to move a platform from using PMTerminal to using Terminal Plugin Controller (TPC) What must you do?
Target account platforms can be restricted to accounts that are stored m specific Safes using the Allowed Safes property.
Which components support fault tolerance.
Which option in the Private Ark client is used to update users’ Vault group memberships?
A customer installed multiple PVWAs in the production environment behind a load balancer VIP. They subsequently observed that all incoming traffic from the load balancer VIP goes to only one PVWA, even though all the PVWAs are up and running. What could be the likely cause of this situation?
SAFE Authorizations may be granted to____________.
Select all that apply.
You have been asked to configure SNMP remote monitoring for your organization's Vault servers. In the PARAgent.ini, which parameter specifies the destination of the Vault SNMP Traps?
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
Can the 'Connect' button be used to initiate an SSH connection, as root, to a Unix system when SSH access for root is denied?
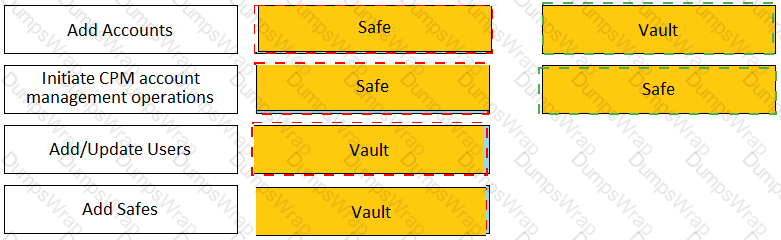
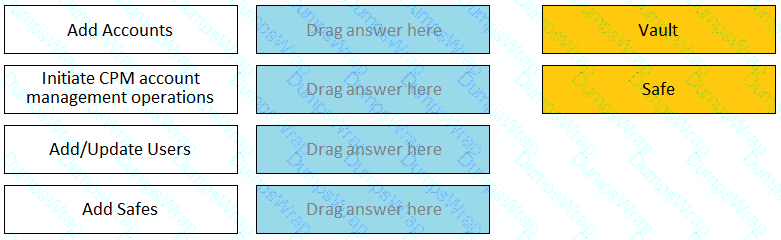
Match each permission to where it can be found.
Which authentication methods does PSM for SSH support?
What is a requirement for setting fault tolerance for PSMs?
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA Hardening.ps1 perform when run?
What is the purpose of the Immediate Interval setting in a CPM policy?
You are configuring the vault to send syslog audit data to your organization's SIEM solution. What is a valid value for the SyslogServerProtocol parameter in DBPARM.ini file?
Which of the following options is not set in the Master Policy?
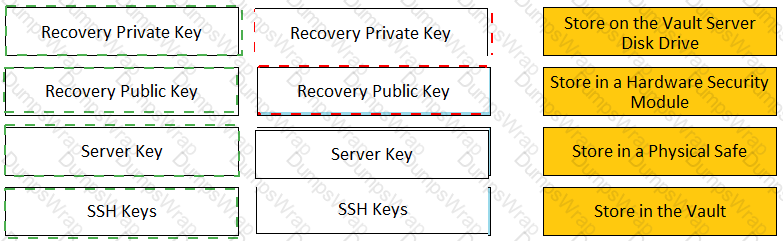
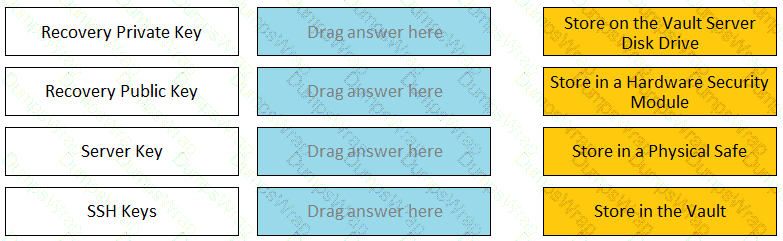
Match each key to its recommended storage location.
What is mandatory for a PVWA installation?
A Reconcile Account can be specified in the Master Policy.
Which parameter controls how often the CPM looks for accounts that need to be changed from recently completed Dual control requests.
Within the Vault each password is encrypted by:
What are the basic network requirements to deploy a CPM server?
Which of the following PTA detections require the deployment of a Network Sensor or installing the PTA Agent on the domain controller?
The vault supports Subnet Based Access Control.
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
What is the purpose of the CyberArk Event Notification Engine service?
The vault supports Role Based Access Control.
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment.
Which security configuration should you recommend?
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
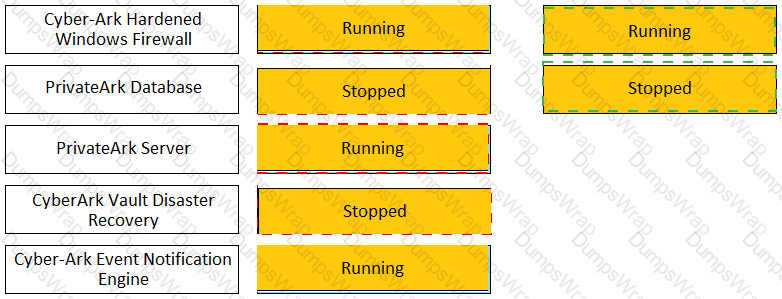
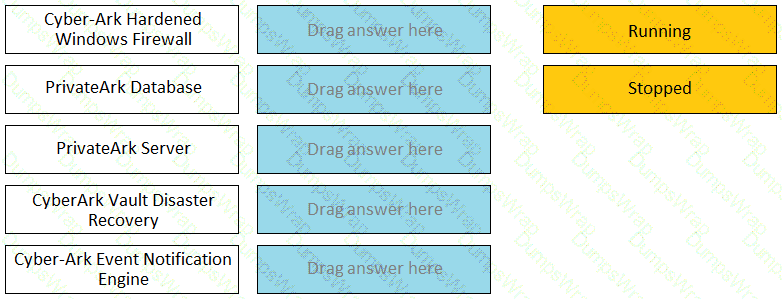
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode.
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
Which of the following PTA detections are included in the Core PAS offering?
You have been asked to design the number of PVWAs a customer must deploy. The customer has three data centers with a distributed vault in each, requires high availability, and wants to use all vaults, at all times. How many PVWAs does the customer need?
Which of the following components can be used to create a tape backup of the Vault?
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
Secure Connect provides the following. Choose all that apply.
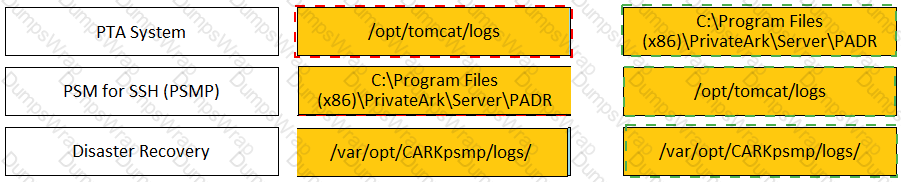
Match each component to its respective Log File location.

Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to be changed.
For an account attached to a platform that requires Dual Control based on a Master Policy exception, how would you configure a group of users to access a password without approval.
A user is receiving the error message “ITATS006E Station is suspended for User jsmith” when attempting to sign into the Password Vault Web Access (PVWA). Which utility would a Vault administrator use to correct this problem?
You have associated a logon account to one your UNIX cool accounts in the vault. When attempting to [b]change [/b] the root account’s password the CPM will…..
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
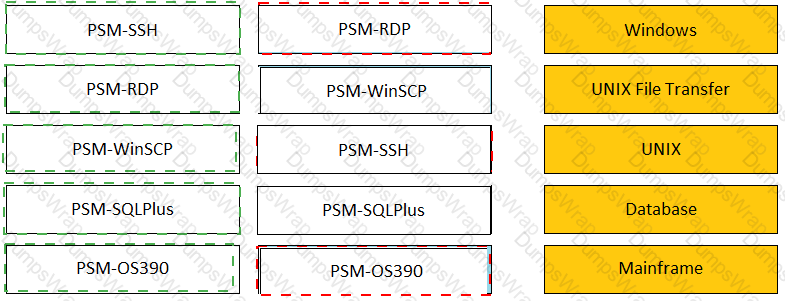
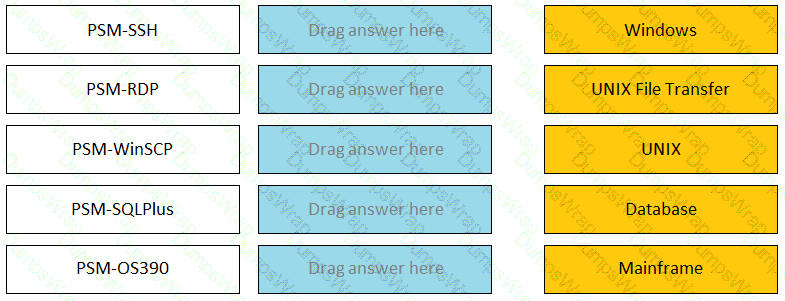
Match the connection component to the corresponding OS/Function.
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
Which usage can be added as a service account platform?
A customer's environment three data centers, consisting of 5,000 servers in Germany, 10,000 servers in Canada, 1,500 servers in Singapore. You want to manage target servers and avoid complex firewall rules. How many CPM's should you deploy?
In accordance with best practice, SSH access is denied for root accounts on UNIX/LINUX system. What is the BEST way to allow CPM to manage root accounts.
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
When on-boarding account using Accounts Feed, Which of the following is true?
A company requires challenge/response multi-factor authentication for PSMP sessions. Which server must you integrate with the CyberArk vault?
What is the purpose of the PrivateArk Server service?
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens.
Which piece of the platform is missing?
You are onboarding an account that is not supported out of the box.
What should you do first to obtain a platform to import?
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server, which user will be utilized?
What is a prerequisite step before CyberArk can be configured to support RADIUS authentication?
Accounts Discovery allows secure connections to domain controllers.
A Logon Account can be specified in the Master Policy.