CyberArk Sentry PAM Questions and Answers
Which file must you edit to ensure the PSM for SSH server is not hardened automatically after installation?
You have been asked to limit a platform called “Windows_Servers” to safes called “WindowsDC1” and “WindowsDC2”. The platform must not be assigned to any other safe.
What is the correct way to accomplish this?
During the PSM installation process, Safes and a User are created.
In addition to Add Safes, Add/Update Users, Reset Users’ Passwords, and Activate Users, which authorization(s) does the Vault user installing the PSM need to enable them to be successfully created?
What is the purpose of the CPM_Preinstallation.ps1 script included with the CPM installation package?
The Remote Desktop Services role must be property licensed by Microsoft.
At what point is a transparent user provisioned in the vault?
A customer is moving from an on-premises to a public cloud deployment.
What is the best and most cost-effective option to secure the server key?
What are the basic network requirements to deploy a CPM server?
Arrange the steps to complete CPM Hardening for Out-of-Domain Deployment in the correct sequence.
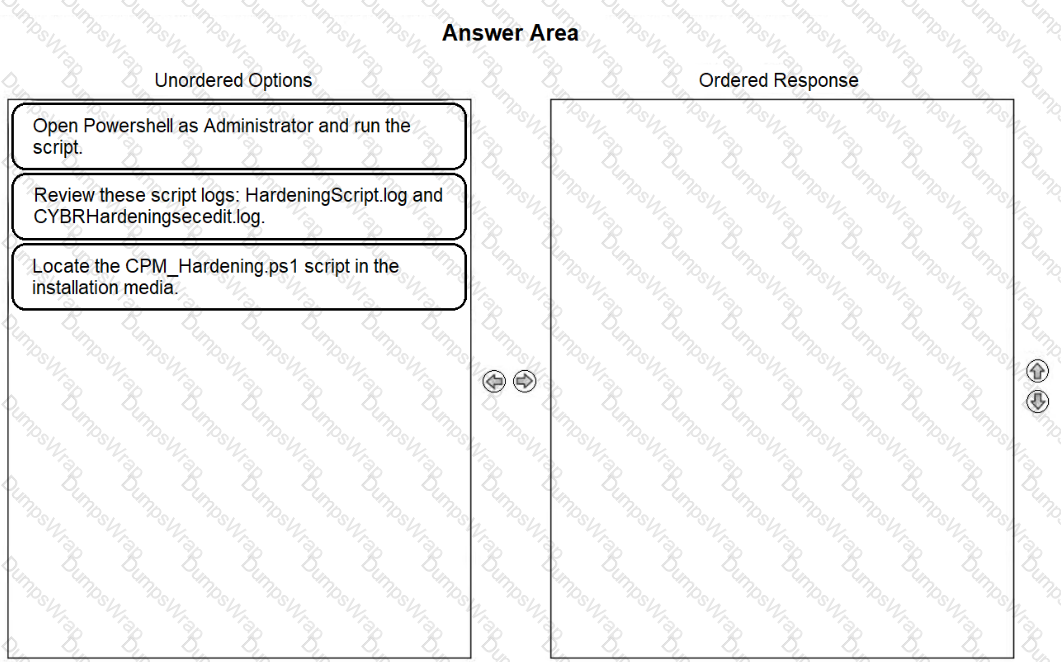
-
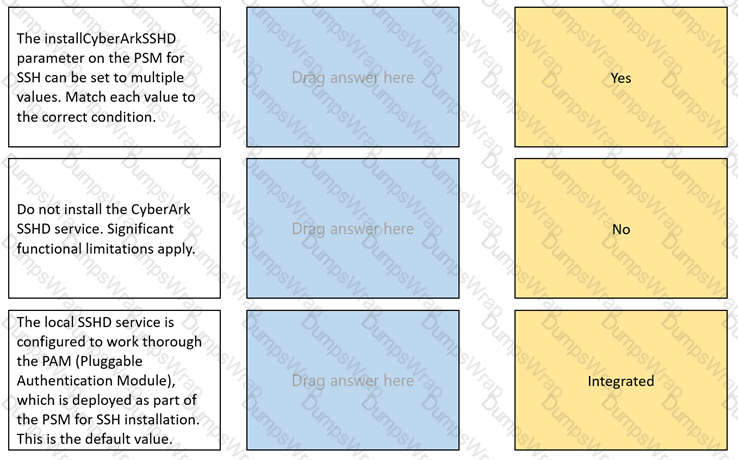
The installCyberArkSSHD parameter on the PSM for SSH can be set to multiple values.
Match each value to the correct condition.
You are installing the HTML5 gateway on a Linux host using the RPM provided.
After installing the Tomcat webapp, what is the next step in the installation process?
Which statement is correct about a post-install hardening?
You are installing a CPM.
In addition to Add Safes, Add/Update Users, Reset Users’ Passwords and Manage Server File Categories, which Vault authorization(s) does a CyberArk user need to install the CPM?
By default, the vault secure protocol uses which IP port and protocol.
Which is the correct order of installation for PAS components?
As a member of a PAM Level-2 support team, you are troubleshooting an issue related to load balancing four PVWA servers at two data centers. You received a note from your Level-1 support team stating “When testing PVWA website from a workstation, we noticed that the “Source IP of last sign-in” was shown as the VIP (Virtual IP address) assigned to the four PVWA servers instead of the workstation IP where the PVWA site was launched from.”
Which step should you take?
In which configuration file on the Vault can filters be configured to either include or exclude log messages that are sent through SNMP?
What is a prerequisite step before installing the Vault on Windows 2019?
What is the PRIMARY reason for installing more than 1 active CPM?
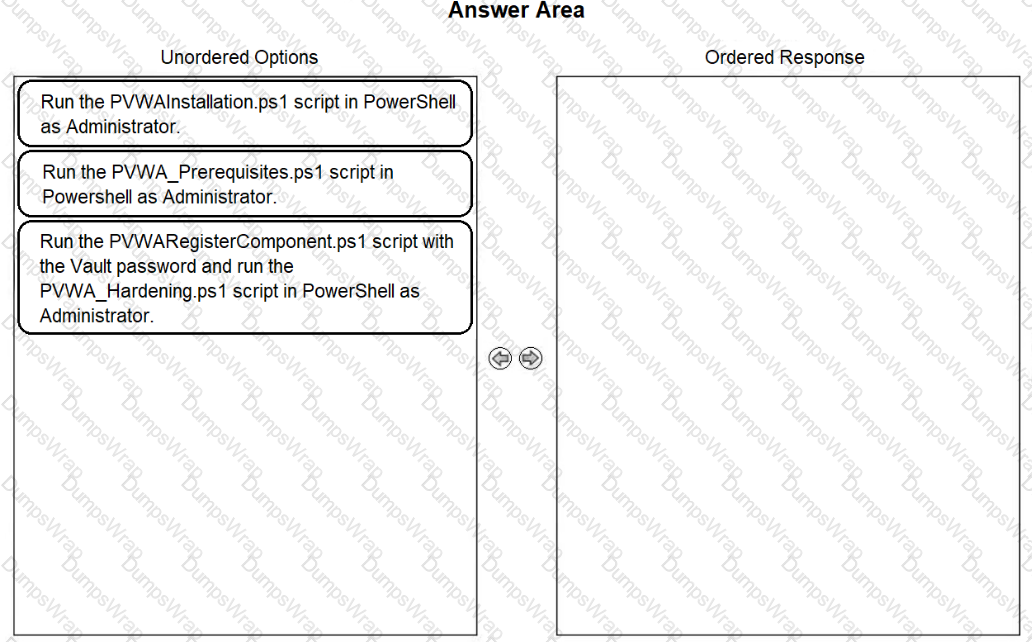
Arrange the steps to install the Password Vault Web Access (PVWA) in the correct sequence.
Which component should be installed on the Vault if Distributed Vaults are used with PSM?
What is a step to enable NTP synchronization on a stand-alone Vault?
If a customer has one data center and requires fault tolerance, how many PVWAs should be deployed?
You are installing PSM for SSH with AD-Bridge and CyberArkSSHD mode set to integrated for your customer.
Which additional packages do you need to install to meet the customer’s needs? (Choose two.)
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
Which utility should be used to register the Vault in Amazon Web Services?
A customer wants to store PSM recordings for 100 days and estimates they will have 10 Windows sessions per day for 100 minutes each.
What is the minimum storage required for the Vault and PAReplicate for the PSM recordings?
A first PSM server has been installed.
What should you confirm before installing any additional PSM servers?
For redundancy, you want to add a secondary RADIUS server.
What must you do to accomplish this?
In a SIEM integration it is possible to use the fully-qualified domain name (FQDN) when specifying the SIEM server address(es)
What must you do to prepare a Windows server for PVWA installation?
Which files does the Vault Installation Wizard prompt you for during the Vault install?
What must you do to synchronize a new Vault server with an organization’s NTP server?
What would be a good use case for the Replicate module?
You are configuring SNMP remote monitoring for your organization’s Vault servers.
In the PARAgent.ini, which parameter specifies the destination of the Vault SNMP traps?
A customer has five main data centers with one PVWA in each center under different URLs.
How can you make this setup fault tolerant?
A vault admin received an email notification that a password verification process has failed Which service sent the message?
As Vault Admin, you have been asked to enable your organization's CyberArk users to authenticate using LDAP.
In addition to Audit Users, which permission do you need to complete this task?
To apply a new license file you must:
What is a valid combination of primary and secondary layers of authentication to a company's two-factor authentication policy?




