Certified Cybersecurity Technician (CCT) Questions and Answers
Ruben, a crime investigator, wants to retrieve all the deleted files and folders in the suspected media without affecting the original files. For this purpose, he uses a method that involves the creation of a cloned copy of the entire media and prevents the contamination of the original media.
Identify the method utilized by Ruben in the above scenario.
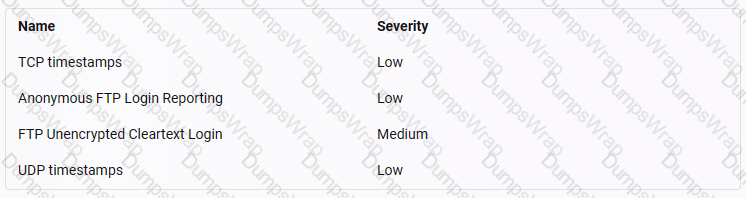
You are Harris working for a web development company. You have been assigned to perform a task for vulnerability assessment on the given IP address 20.20.10.26. Select the vulnerability that may affect the website according to the severity factor.
Hint: Greenbone web credentials: admin/password
Calvin spotted blazing flames originating from a physical file storage location in his organization because of a Short circuit. In response to the incident, he used a fire suppression system that helped curb the incident in the initial stage and prevented it from spreading over a large area. Which of the following firefighting systems did Calvin use in this scenario?
George, a security professional at an MNC, implemented an Internet access policy that allowed employees working from a remote location to access any site, download anyapplication, and access any computer or network without any restrictions. Identify the type of Internet access policy implemented by George in this scenario.
The SOC department in a multinational organization has collected logs of a security event as
"Windows.events.evtx". Study the Audit Failure logs in the event log file located in the Documents folder of the
-Attacker Maehine-1" and determine the IP address of the attacker. (Note: The event ID of Audit failure logs is
4625.)
(Practical Question)
Tenda, a network specialist at an organization, was examining logged data using Windows Event Viewer to identify attempted or successful unauthorized activities. The logs analyzed by Tenda include events related to Windows security; specifically, log-on/log-off activities, resource access, and also information based on Windows system's audit policies.
Identify the type of event logs analyzed by Tenda in the above scenario.
Jaden, a network administrator at an organization, used the ping command to check the status of a system connected to the organization's network. He received an ICMP error message stating that the IP header field contains invalid information. Jaden examined the ICMP packet and identified that it is an IP parameter problem.
Identify the type of ICMP error message received by Jaden in the above scenario.
You've been called in as a computer forensics investigator to handle a case involving a missing company laptop from the accounting department, which contained sensitive financial data. The company suspects a potential data breach and wants to recover any evidence from the missing device. What is your MOST important initial action regarding the digital evidence?
GlobalTech, a multinational tech conglomerate, has been operating across 50 countries for the past two decades. Recently, it faced a significant data breach that affected Its reputation and bottom line. As a result, the board of directors decided to overhaul its existing corporate strategy, with a pronounced focus on enhancing its Information Security Governance. The company believes that a robust governance structure would not only prevent future breaches but would also align with its long-term business objectives of expansion and dominance in the tech market. It has called upon several third-party consultants to pitch an optimal strategy for the conglomerate's unique position.
Which strategy best aligns with GlobalTech's requirement?
An IoT device that has been placed in a hospital for safety measures, it has sent an alert command to the server. The network traffic has been captured and stored in the Documents folder of the Attacker Machine-1. Analyze the loTdeviceTraffic.pcapng file and select the appropriate command that was sent by the IoT device over the network.
An loT device placed in a hospital for safety measures has sent an alert to the server. The network traffic has been captured and stored in the Documents folder of the "Attacker Machine-1". Analyze the loTdeviceTraffic.pcapng file and identify the command the loT device sent over the network. (Practical Question)
You are investigating a data leakage incident where an insider is suspected of using image steganography to send sensitive information to a competitor. You have also recovered a VeraCrypt volume file S3cr3t from the suspect. The VeraCrypt volume file is available In the Pictures folder of the Attacker Machined. Your task Is to mount the VeraCrypt volume, find an image file, and recover the secret code concealed in the file. Enter the code as the answer. Hint: If required, use sniffer@123 as the password to mount the VeraCrypt volume file.(Practical Question)
Kevin, a professional hacker, wants to penetrate CyberTech Inc.’s network. He employed a technique, using which he encoded packets with Unicode characters. The company’s IDS cannot recognize the packet, but the target web server can decode them.
What is the technique used by Kevin to evade the IDS system?
Hayes, a security professional, was tasked with the implementation of security controls for an industrial network at the Purdue level 3.5 (IDMZ). Hayes verified all the possible attack vectors on the IDMZ level and deployed a security control that fortifies the IDMZ against cyber-attacks.
Identify the security control implemented by Hayes in the above scenario.
Grace, an online shopping enthusiast, purchased a smart TV using her debit card. During online payment. Grace's browser redirected her from the e-commerce website to a third-party payment gateway, where she provided her debit card details and the OTP received on her registered mobile phone. After completing the transaction, Grace logged Into her online bank account and verified the current balance in her savings account, identify the state of data being processed between the e-commerce website and payment gateway in the above scenario.
An organization hired a network operations center (NOC) team to protect its IT infrastructure from external attacks. The organization utilized a type of threat intelligence to protect its resources from evolving threats. The threat intelligence helped the NOC team understand how attackers are expected to perform an attack on the organization, identify the information leakage, and determine the attack goals as well as attack vectors.
Identify the type of threat intelligence consumed by the organization in the above scenario.
Karter, a security professional, deployed a honeypot on the organization's network for luring attackers who attempt to breach the network. For this purpose, he configured a type of honeypot that simulates a real OS as well as the applications and services of a target network. Furthermore, the honeypot deployed by Karter only responds to pre-configured commands.
Identify the type of Honeypot deployed by Karter in the above scenario.
Dany, a member of a forensic team, was actively involved in an online crime investigation process. Dany's main responsibilities included providing legal advice on conducting the investigation and addressing legal issues involved in the forensic investigation process. Identify the role played by Dany in the above scenario.
Alpha Finance, a leading banking institution, is launching anew mobile banking app. Given the sensitive financial data involved, it wants to ensure that Its application follows the best security practices. As the primary recommendation, which guideline should Alpha Finance prioritize?
Myles, a security professional at an organization, provided laptops for all the employees to carry out the business processes from remote locations. While installing necessary applications required for the business, Myles has also installed antivirus software on each laptop following the company's policy to detect and protect the machines from external malicious events over the Internet.
Identify the PCI-DSS requirement followed by Myles in the above scenario.
Andre, a security professional, was tasked with segregating the employees' names, phone numbers, and credit card numbers before sharing the database with clients. For this purpose, he implemented a deidentification technique that can replace the critical information in database fields with special characters such as asterisks (*) and hashes (#).
Which of the following techniques was employed by Andre in the above scenario?
You are a penetration tester working to test the user awareness of the employees of the client xyz. You harvested two employees' emails from some public sources and are creating a client-side backdoor to send it to the employees via email. Which stage of the cyber kill chain are you at?
Mark, a security analyst, was tasked with performing threat hunting to detect imminent threats in an organization's network. He generated a hypothesis based on the observations in the initial step and started the threat-hunting process using existing data collected from DNS and proxy logs.
Identify the type of threat-hunting method employed by Mark in the above scenario.
A major metropolitan municipal corporation had deployed an extensive loT network for managing various facilities in the city. A recent cyber attack has paralyzed the city’s vital services, bringing them to a complete halt. The Security Operations Center (SOC) has captured the network traffic during the attack and stored It as loT_capture.pcapng in the Documents folder of the Attacker Machine-1. Analyze the capture file and identify the command that was sent to the loT devices over the network. (Practical Question)
Walker, a security team member at an organization, was instructed to check if a deployed cloud service is working as expected. He performed an independent examination of cloud service controls to verify adherence to standards through a review of objective evidence. Further, Walker evaluated the services provided by the CSP regarding security controls, privacy impact, and performance.
Identify the role played by Walker in the above scenario.
In an organization, all the servers and database systems are guarded in a sealed room with a single-entry point. The entrance is protected with a physical lock system that requires typing a sequence of numbers and letters by using a rotating dial that intermingles with several other rotating discs.
Which of the following types of physical locks is used by the organization in the above scenario?
Rickson, a security professional at an organization, was instructed to establish short-range communication between devices within a range of 10 cm. For this purpose, he used a mobile connection method that employs electromagnetic induction to enable communication between devices. The mobile connection method selected by Rickson can also read RFID tags and establish Bluetooth connections with nearby devices to exchange information such as images and contact lists.
Which of the following mobile connection methods has Rickson used in above scenario?
Gideon, a forensic officer, was examining a victim's Linux system suspected to be involved in online criminal activities. Gideon navigated to a directory containing a log file that recorded information related to user login/logout. This information helped Gideon to determine the current login state of cyber criminals in the victim system, identify the Linux log file accessed by Gideon in this scenario.
A global financial services firm Is revising its cybersecurity policies to comply with a diverse range of international regulatory frameworks and laws. The firm operates across multiple continents, each with distinct legal requirements concerning data protection, privacy, and cybersecurity. As part of their compliance strategy, they are evaluating various regulatory frameworks to determine which ones are most critical to their operations. Given the firm's international scope and the nature of its services, which of the following regulatory frameworks should be prioritized for compliance?
Martin, a network administrator at an organization, received breaching alerts for an application. He identified that a vulnerability in the application allowed attackers to enter malicious input. Martin evaluated the threat severity and extent of damage that could be caused by this vulnerability. He then escalated the issue to the security management team to determine appropriate mitigation strategies. In which of the following threat-modeling steps did Martin evaluate the severity level of the threat?
As the senior network analyst for a leading fintech organization, you have been tasked with ensuring seamless communication between the firm's global offices. Your network has been built with redundancy in mind, leveraging multiple service providers and a mixture of MPLS and public internet connections.
A large multinational corporation is In the process of upgrading its network infrastructure to enhance security and protect sensitive data. As part of the upgrade, the IT team is considering implementing stateful multilayer inspection firewalls and application-level gateway firewalls.
How do stateful multilayer inspection firewalls differ from application-level gateway firewalls in terms of their packet filtering capabilities and the layers of the OSI model they inspect?
Jordan, a network administrator in an organization, was instructed to identify network-related issues and improve network performance. While troubleshooting the network, he received a message indicating that the datagram could not be forwarded owing to the unavailability of IP-related services (such as FTP or web services) on the target host, which of the following network issues did Jordan find in this scenario?
A government agency's confidential Information is leaked to the public, causing significant embarrassment and damage to its reputation. The leaked data includes sensitive documents related to military operations and diplomatic communications. Considering the scenario, which threat actor group is typically employed by governments to penetrate and gather top-secret information from other government or military organizations?
Rhett, a security professional at an organization, was instructed to deploy an IDS solution on their corporate network to defend against evolving threats. For this purpose, Rhett selected an IDS solution that first creates models for possible intrusions and then compares these models with incoming events to make detection decisions.
Identify the detection method employed by the IDS solution in the above scenario.
Richards, a security specialist at an organization, was monitoring an IDS system. While monitoring, he suddenly received an alert of an ongoing intrusion attempt on the organization's network. He immediately averted the malicious actions by implementing the necessary measures.
Identify the type of alert generated by the IDS system in the above scenario.
Rickson, a security professional at an organization, was instructed to establish short-range communication between devices within a range of 10 cm. For this purpose, he used a mobile connection method that employs electromagnetic induction to enable communication between devices. The mobile connection method selected by Rickson can also read RFID tags and establish Bluetooth connections with nearby devices to exchange information such as images and contact lists.
Which of the following mobile connection methods has Rickson used in above scenario?
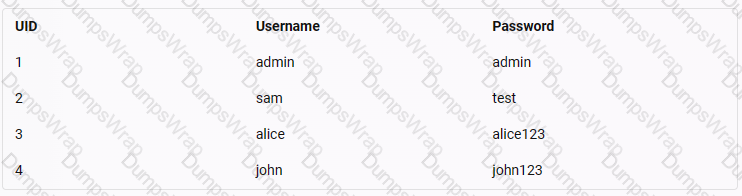
A web application, was found to be prone to SQL injection attacks. You are tasked to exploit the web application and fetch the user data. Identify the contact number (Contact) of a user, Steve, in the moviescope database. Note: You already have an account on the web application, and your credentials are sam/test. (Practical Question)
A web application was found to be prone to SQL injection attack. You are given a task to exploit the web application and fetch the user credentials. Select the UID which is mapped to user john in the database table.
Note:
Username: sam
Pass: test
Desmond, a forensic officer, was investigating a compromised machine involved in various online attacks. For this purpose. Desmond employed a forensic tool to extract and analyze computer-based evidence to retrieve information related to websitesaccessed from the victim machine. Identify the computer-created evidence retrieved by Desmond in this scenario.
Leilani, a network specialist at an organization, employed Wireshark for observing network traffic. Leilani navigated to the Wireshark menu icon that contains items to manipulate, display and apply filters, enable, or disable the dissection of protocols, and configure user-specified decodes.
Identify the Wireshark menu Leilani has navigated in the above scenario.
Hotel Grande offers luxury accommodations and emphasizes top-notch service for its guests. One such service is secure, high-speed Wi-FI access In every room. The hotel wishes to deploy an authentication method that would give individual guests a seamless experience without compromising security. This method should ideally provide a balance between convenience and strong security. Which of the following should Hotel Grande use?
SecuraCorp, a leading financial institution, is worried about zero-day vulnerabilities. With a sprawling network infrastructure and multiple transaction points, it needs a system that does not solely rely on signatures but can effectively identify suspicious patterns based on the behavior in the network. Which type of IDS/IPS should SecuraCorp primarily deploy for its needs?
Tristan, a professional penetration tester, was recruited by an organization to test its network infrastructure. The organization wanted to understand its current security posture and its strength in defending against external threats. For this purpose, the organization did not provide any information about their IT infrastructure to Tristan. Thus, Tristan initiated zero-knowledge attacks, with no information or assistance from the organization.
Which of the following types of penetration testing has Tristan initiated in the above scenario?
Sam, a software engineer, visited an organization to give a demonstration on a software tool that helps in business development. The administrator at the organization created a least privileged account on a system and allocated that system to Sam for the demonstration. Using this account, Sam can only access the files that are required for the demonstration and cannot open any other file in the system.
Which of the following types of accounts the organization has given to Sam in the above scenario?
Thomas, an employee of an organization, is restricted from accessing specific websites from his office system. He is trying to obtain admin credentials to remove the restrictions. While waiting for an opportunity, he sniffed communication between the administrator and an application server to retrieve the admin credentials. Identify the type of attack performed by Thomas in the above scenario.
An attacker with malicious intent used SYN flooding technique to disrupt the network and gain advantage over the network to bypass the Firewall. You are working with a security architect to design security standards and plan for your organization. The network traffic was captured by the SOC team and was provided to you to perform a detailed analysis. Study the Synflood.pcapng file and determine the source IP address.
Note: Synflood.pcapng file is present in the Documents folder of Attacker-1 machine.
Finley, a security professional at an organization, was tasked with monitoring the organizational network behavior through the SIEM dashboard. While monitoring, Finley noticed suspicious activities in the network; thus, he captured and analyzed a single network packet to determine whether the signature included malicious patterns. Identify the attack signature analysis technique employed by Finley in this scenario.