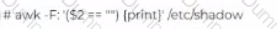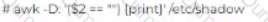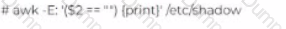Certified Network Defender (CND) Questions and Answers
Which RAID level does not provide data redundancy?
Liza was told by her network administrator that they will be implementing IPsec VPN tunnels to connect the branch locations to the main office. What layer of the OSI model do IPsec tunnels function on?
You are using Wireshark to monitor your network traffic and you see a lot of packages with FIN,
PUSH and URG flags activated; what can you infer about this behavior?
Harry has sued the company claiming they made his personal information public on a social networking site in the United States. The company denies the allegations and consulted a/an ______for legal advice to defend
them against this allegation.
James is working as a Network Administrator in a reputed company situated in California. He is monitoring his network traffic with the help of Wireshark. He wants to check and analyze the traffic against a PING sweep
attack. Which of the following Wireshark filters will he use?
An US-based organization decided to implement a RAID storage technology for their data backup plan. John wants to setup a RAID level that require a minimum of six drives but will meet high fault tolerance and with a
high speed for the data read and write operations. What RAID level is John considering to meet this requirement?
Which of the following systems includes an independent NAS Head and multiple storage arrays?
Which of the following can be used to suppress fire from Class K sources?
Which field is not included in the TCP header?
John is the Vice-President of a BPO. He wants to implement a policy allowing employees to use and manage devices purchased by the organization but restrict the use of the device for business use only. Which among the following policies does John want to implement?
If a network is at risk from unskilled individuals, what type of threat is this?
Which among the following filter is used to detect a SYN/FIN attack?
Fred is a network technician working for Johnson Services, a temporary employment agency in Boston. Johnson Services has three remote offices in New England and the headquarters in Boston where Fred works.
The company relies on a number of customized applications to perform daily tasks and unfortunately these applications require users to be local administrators. Because of this, Fred's supervisor wants to implement
tighter security measures in other areas to compensate for the inherent risks in making those users local admins. Fred's boss wants a solution that will be placed on all computers throughout the company and
monitored by Fred. This solution will gather information on all network traffic to and from the local computers without actually affecting the traffic. What type of solution does Fred's boss want to implement?
The company has implemented a backup plan. James is working as a network administrator for the company and is taking full backups of the data every time a backup is initiated. Alex who is a senior security manager
talks to him about using a differential backup instead and asks him to implement this once a full backup of the data is completed. What is/are the reason(s) Alex is suggesting that James use a differential backup?
(Select all that apply)
James was inspecting ARP packets in his organization's network traffic with the help of Wireshark. He is checking the volume of traffic containing ARP requests as well as the source IP address from which they are
originating. Which type of attack is James analyzing?
Which of the following VPN topologies establishes a persistent connection between an organization's main office and its branch offices using a third-party network or the Internet?
Which OSI layer does a Network Interface Card (NIC) work on?
John wants to implement a firewall service that works at the session layer of the OSI model. The firewall must also have the ability to hide the private network information. Which type of firewall service is John thinking of
implementing?
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is
called a________and it has to adhere to the_________
Who oversees all the incident response activities in an organization and is responsible for all actions of the IR team and IR function?
How can one identify the baseline for normal traffic?
John wants to implement a firewall service that works at the session layer of the OSI model. The firewall must also have the ability to hide the private network information. Which type of firewall service is John thinking of
implementing?
John, the network administrator and he wants to enable the NetFlow feature in Cisco routers to collect and monitor the IP network traffic passing through the router. Which command will John use to enable NetFlow on
an interface?
Sam wants to implement a network-based IDS in the network. Sam finds out the one IDS solution which works is based on patterns matching. Which type of network-based IDS is Sam implementing?
Steven is a Linux system administrator at an IT company. He wants to disable unnecessary services in the system, which can be exploited by the attackers. Which among the following is the correct syntax for
disabling a service?
Which type of attack is used to hack an IoT device and direct large amounts of network traffic toward a web server, resulting in overloading the server with connections and preventing any new connections?
Which of the following network security controls can an administrator use to detect, deflect or study attempts to gain unauthorized access to information systems?
James wants to implement certain control measures to prevent denial-of-service attacks against the organization. Which of the following control measures can help James?
-----------is a group of broadband wireless communications standards for Metropolitan Area Networks (MANs)
John has been working a* a network administrator at an IT company. He wants to prevent misuse of accounts by unauthorized users. He wants to ensure that no accounts have empty passwords. Which of the following commands does John use to list all the accounts with an empty password?
Identify the attack where an attacker manipulates or tricks people into revealing their confidential details like bank account information, credit card details, etc.?
During a security awareness program, management was explaining the various reasons which create threats to network security. Which could be a possible threat to network security?
USB ports enabled on a laptop is an example of____
How does Windows’ in-built security component, AppLocker, whitelist applications?
Which of the following Wireshark filters allows an administrator to detect SYN/FIN DDoS attempt on
the network?
Will is working as a Network Administrator. Management wants to maintain a backup of all the company data as soon as it starts operations. They decided to use a RAID backup storage technology for their data backup
plan. To implement the RAID data backup storage, Will sets up a pair of RAID disks so that all the data written to one disk is copied automatically to the other disk as well. This maintains an additional copy of the data.
Which RAID level is used here?
What is the correct order of activities that a IDS is supposed to attempt in order to detect an intrusion?
A company wants to implement a data backup method that allows them to encrypt the data ensuring its security as well as access it at any time and from any location. What is the appropriate backup method
that should be implemented?
Which of the following helps prevent executing untrusted or untested programs or code from untrusted or unverified third-parties?
Which authorization lets users access a requested resource on behalf of others?
Which of following are benefits of using loT devices in loT-enabled environments? I. loT device car be connected anytime M. loT device can be connected at any place ill. loT devices connected to anything
The GMT enterprise is working on their internet and web usage policies. GMT would like to control
internet bandwidth consumption by employees. Which group of policies would this belong to?
Byron, a new network administrator at FBI, would like to ensure that Windows PCs there are up-to-date and have less internal security flaws. What can he do?
Mark is monitoring the network traffic on his organization’s network. He wants to detect TCP and UDP ping sweeps on his network. Which type of filter will be used to detect this?
How can a WAF validate traffic before it reaches a web application?
John, a network administrator, is configuring Amazon EC2 cloud service for his organization. Identify the type of cloud service modules his organization adopted.
Which of the following security models enable strict identity verification for every user or device attempting to access the network resources?
1. Zero-trust network model
2. Castle-and-Moat model
Geon Solutions INC., had only 10 employees when it started. But as business grew, the organization had to increase the amount of staff. The network administrator is finding it difficult to accommodate an increasing
number of employees in the existing network topology. So the organization is planning to implement a new topology where it will be easy to accommodate an increasing number of employees. Which network topology
will help the administrator solve the problem of needing to add new employees and expand?
Sophie has been working as a Windows network administrator at an MNC over the past 7 years. She wants to check whether SMB1 is enabled or disabled. Which of the following command allows Sophie
to do so?
Which type of information security policy addresses the implementation and configuration of technology and user behavior?
Which of the Windows security component is responsible for controlling access of a user to Windows resources?
Which type of modulation technique is used in local area wireless networks (LAWNs)?
Frank is a network technician working for a medium-sized law firm in Memphis. Frank and two other IT employees take care of all the technical needs for the firm. The firm's partners have asked that a secure wireless
network be implemented in the office so employees can move about freely without being tied to a network cable. While Frank and his colleagues are familiar with wired Ethernet technologies, 802.3, they are not familiar
with how to setup wireless in a business environment. What IEEE standard should Frank and the other IT employees follow to become familiar with wireless?
Identify the virtualization level that creates a massive pool of storage areas for different virtual machines running on the hardware.
Daniel works as a network administrator in an Information Security company. He has just deployed
an IDS in his organization’s network and wants to calculate the false positive rate for his
implementation. Which of the following formulae can he use to so?
A popular e-commerce company has recently received a lot of complaints from its customers. Most
of the complaints are about the customers being redirected to some other website when trying to
access the e-com site, leading to all their systems being compromised and corrupted. Upon
investigation, the network admin of the firm discovered that some adversary had manipulated the
company’s IP address in the domain name server’s cache. What is such an attack called?
Docker provides Platforms-a-Service (PaaS) through __________ and deliver*; containerized software packages
Who is an IR custodian?
Which of the following creates passwords for individual administrator accounts and stores them in Windows AD?
What is the name of the authority that verifies the certificate authority in digital certificates?
Oliver is a Linux security administrator at an MNC. An employee named Alice has resigned from his organization and Oliver wants to disable this user in Ubuntu. Which of the following commands can be used to accomplish this?
Harry has successfully completed the vulnerability scanning process and found serious vulnerabilities exist in the organization's network. Identify the vulnerability management phases through which he will proceed to
ensure all the detected vulnerabilities are addressed and eradicated. (Select all that apply)
Which of the following data security technology can ensure information protection by obscuring specific areas of information?
Which category of suspicious traffic signatures includes SYN flood attempts?
A local bank wants to protect their card holder data. The bank should comply with the________standard to ensure the security of card holder data.
According to the company's security policy, all access to any network resources must use Windows Active Directory Authentication. A Linux server was recently installed to run virtual servers and it is not using Windows
Authentication. What needs to happen to force this server to use Windows Authentication?
Ryan is a network security administrator, who wants to implement local security policies for privileges granted to users and groups, system security audit settings, user authentication, and want to
send security audit messages to the Event Log. Which Windows security component fulfills Ryan’s requirement?
James is a network administrator working at a student loan company in Minnesota. This company processes over 20,000 student loans a year from colleges all over the state. Most communication between the company
schools, and lenders is carried out through emails. Much of the email communication used at his company contains sensitive information such as social security numbers. For this reason, James wants to utilize email
encryption. Since a server-based PKI is not an option for him, he is looking for a low/no cost solution to encrypt emails. What should James use?
Malone is finishing up his incident handling plan for IT before giving it to his boss for review. He is outlining the incident response methodology and the steps that are involved. Which step should Malone list as the last step in the incident response methodology?
Which of the following wireless encryption provides enhanced password protection, secured IoT connections, and encompasses stronger encryption techniques?
Which of the following connects the SDN controller and SDN networking devices and relays information from network services to network devices such as switches and routers?
Which of the following standards does a cloud service provider has to comply with, to protect the privacy of its customer’s personal information?
A local bank wants to protect their cardholder data. Which standard should the bark comply with in order to ensure security of this data?
Bankofamerica Enterprise is working on an internet and usage policy in a way to control the
internet demand. What group of policy does this belong to?
Kyle, a front office executive, suspects that a Trojan has infected his computer. What should be his first course of action to deal with the incident?
George was conducting a recovery drill test as a part of his network operation. Recovery drill tests are conducted on the______________.
Jorge has developed a core program for a mobile application and saved it locally on his system. The
next day, when he tried to access the file to work on it further, he found it missing from his system.
Upon investigation, it was discovered that someone got into his system since he had not changed his
login credentials, and that they were the ones that were given to him by the admin when he had joined
the organization. Which of the following network security vulnerabilities can be attributed to Jorge’s
situation?
To secure his company’s network, Tim the network admin, installed a security device that inspected
all inbound and outbound network traffic for suspicious patterns. The device was configured to alert him
if it found any such suspicious activity. Identify the type of network security device installed by Tim?
Identify the attack signature analysis technique carried out when attack signatures are contained in packet headers.
Which of the following network security protocols protects from sniffing attacks by encrypting entire communication between the clients and server including user passwords?
During the recovery process, RTO and RPO should be the main parameters of your disaster
recovery plan. What does RPO refer to?
Which of the following statement holds true in terms of containers?
Identify the Password Attack Technique in which the adversary attacks cryptographic hash functions based on the probability, that if a hashing process is used for creating a key, then the same is
used for other keys?
John has planned to update all Linux workstations in his network. The organization is using various Linux distributions including Red hat, Fedora and Debian. Which of following commands will he use to
update each respective Linux distribution?
XX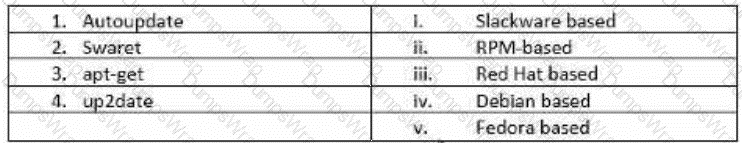
Kelly is taking backups of the organization's data. Currently, he is taking backups of only those files which are created or modified after the last backup. What type of backup is Kelly using?
Which subdirectory in /var/log directory stores information related to Apache web server?
Daniel is giving training on designing and implementing a security policy in the organization. He is explaining the hierarchy of the security policy which demonstrates how policies are drafted, designed and implemented.
What is the correct hierarchy for a security policy implementation?
What is the IT security team responsible for effectively managing the security of the organization’s IT infrastructure, called?
Who is responsible for conveying company details after an incident?
Which of the following is NOT an AWS Shared Responsibility Model devised by AWS?
An organization’s web server was recently compromised triggering its admin team into action to
defend the network. The admin team wants to place the web server in such a way that, even if it is
attacked, the other network resources will be unavailable to the attacker. Moreover, the network
monitoring will easily detect the future attacks. How can the admin team implement this plan?
An administrator wants to monitor and inspect large amounts of traffic and detect unauthorized attempts from inside the organization, with the help of an IDS. They are not able to
recognize the exact location to deploy the IDS sensor. Can you help him spot the location where the IDS sensor should be placed?
An employee of a medical service company clicked a malicious link in an email sent by an attacker. Suddenly, employees of the company are not able to access billing information or client record as it is
encrypted. The attacker asked the company to pay money for gaining access to their data. Which type of malware attack is described above?
Daniel who works as a network administrator has just deployed an in his organizations network. He wants to calculate the False Positive rate for his implementation. Which of the following formulas will he use to calculate the False Positive rate?
Which command list all ports available on a server?
A company has the right to monitor the activities of their employees on different information systems according to the _______policy.
Which policies exist only on AWS IAM identity (user, group, or role)?
You are responsible for network functions and logical security throughout the corporation. Your company has over 250 servers running Windows Server 2012, 5000 workstations running Windows 10, and 200 mobile
users working from laptops on Windows 8. Last week 10 of your company's laptops were stolen from a salesman, while at a conference in Barcelona. These laptops contained proprietary company information. While
doing a damage assessment, a news story leaks about a blog post containing information about the stolen laptops and the sensitive information. What built-in Windows feature could you have implemented to protect the
sensitive information on these laptops?
Which of the following indicators refers to potential risk exposures that attackers can use to breach the security of an organization?
What represents the ability of an organization to respond under emergency in order to minimize the damage to its brand name, business operation, and profit?
Assume that you are a network administrator and the company has asked you to draft an Acceptable Use Policy (AUP) for employees. Under which category of an information security policy does AUP fall into?
The bank where you work has 600 windows computers and 400 Red Hat computers which primarily serve as bank teller consoles. You have created a plan and deployed all the patches to the Windows computers and
you are now working on updating the Red Hat computers. What command should you run on the network to update the Red Hat computers, download the security package, force the package installation, and update all
currently installed packages?
Which of the following is an example of MAC model?
Simon had all his systems administrators implement hardware and software firewalls to ensure network security. They implemented IDS/IPS systems throughout the network to check for and stop any unauthorized
traffic that may attempt to enter. Although Simon and his administrators believed they were secure, a hacker group was able to get into the network and modify files hosted on the company's website. After searching
through the firewall and server logs, no one could find how the attackers were able to get in. He decides that the entire network needs to be monitored for critical and essential file changes. This monitoring tool alerts
administrators when a critical file is altered. What tool could Simon and his administrators implement to accomplish this?
Simran is a network administrator at a start-up called Revolution. To ensure that neither party in the company can deny getting email notifications or any other communication, she mandates authentication
before a connection establishment or message transfer occurs. What fundamental attribute of network defense is she enforcing?
You are an IT security consultant working on a contract for a large manufacturing company to audit their entire network. After performing all the tests and building your report, you present a number of recommendations
to the company and what they should implement to become more secure. One recommendation is to install a network-based device that notifies IT employees whenever malicious or questionable traffic is found. From
your talks with the company, you know that they do not want a device that actually drops traffic completely, they only want notification. What type of device are you suggesting?
Which phase of vulnerability management deals with the actions taken for correcting the discovered vulnerability?
Which of the following connects the SDN application layer and SDN controller and allows communication between the network services and business applications?