Certified Ethical Hacker Exam (CEHv13) Questions and Answers
A red team operator wants to obtain credentials from a Windows machine without touching LSASS memory due to security controls and Credential Guard. They use SSPI to generate NetNTLM responses in the logged-in user context and collect those responses for offline cracking. Which attack technique is being used?
A global media streaming platform experiences traffic surges every 10 minutes, with spikes over 300 Gbps followed by quiet intervals. Which DDoS attack explains this behavior?
How does a denial-of-service (DoS) attack work?
You receive an email prompting you to download “Antivirus 2010” software using a suspicious link. The software claims to provide protection but redirects you to an unknown site.
How will you determine if this is a Real or Fake Antivirus website?
Which of the following statements is FALSE with respect to Intrusion Detection Systems?
Which of the following is a passive wireless packet analyzer that works on Linux-based systems?
Jason, an attacker, targeted an organization to perform an attack on its Internet-facing web server with the intention of gaining access to backend servers, which are protected by a firewall. In this process, he used a URL to obtain a remote feed and altered the URL input to the local host to view all the local resources on the target server. What is the type of attack Jason performed In the above scenario?
Bob wants to ensure that Alice can check whether his message has been tampered with. He creates a checksum of the message and encrypts it using asymmetric cryptography. What key does Bob use to encrypt the checksum for accomplishing this goal?
A cybersecurity analyst monitors competitors’ web content for changes indicating strategic shifts. Which missing component is most crucial for effective passive surveillance?
Under what conditions does a secondary name server request a zone transfer from a primary name server?
While analyzing logs, you observe a large number of TCP SYN packets sent to various ports with no corresponding ACKs. What scanning technique was likely used?
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
The network users are complaining because their system are slowing down. Further, every time they attempt to go a website, they receive a series of pop-ups with advertisements. What types of malware have the system been infected with?
What would be the purpose of running "wget 192.168.0.15 -q -S" against a web server?
A vulnerability has a score of 9.8. What does this rating help explain?
Which of the following web vulnerabilities would an attacker be attempting to exploit if they delivered the following input?
Joel, a professional hacker, targeted a company and identified the types of websites frequently visited by its employees. Using this information, he searched for possible loopholes in these websites and injected a malicious script that can redirect users from the web page and download malware onto a victim's machine. Joel waits for the victim to access the infected web application so as to compromise the victim's machine. Which of the following techniques is used by Joel in the above scenario?
What would you enter if you wanted to perform a stealth scan using Nmap?
Leverox Solutions hired Arnold, a security professional, for the threat intelligence process. Arnold collected information about specific threats against the organization. From this information, he retrieved contextual information about security events and incidents that helped him disclose potential risks and gain insight into attacker methodologies. He collected the information from sources such as humans, social media, and chat rooms as well as from events that resulted in cyberattacks. In this process, he also prepared a report that includes identified malicious activities, recommended courses of action, and warnings for emerging attacks. What is the type of threat intelligence collected by Arnold in the above scenario?
Which of the following is a component of a risk assessment?
An ethical hacker conducts testing with full knowledge and permission. What type of hacking is this?
Which among the following is the best example of the third step (delivery) in the cyber kill chain?
CyberTech Inc. recently experienced SQL injection attacks on its official website. The company appointed Bob, a security professional, to build and incorporate defensive strategies against such attacks. Bob adopted a practice whereby only a list of entities such as the data type, range, size, and value, which have been approved for secured access, is accepted. What is the defensive technique employed by Bob in the above scenario?
An attacker examines differences in ciphertext outputs resulting from small changes in the input to deduce key patterns in a symmetric algorithm. What method is being employed?
An Nmap SMTP enumeration script returns valid usernames. What misconfiguration is being exploited?
Bob received this text message on his mobile phone: “Hello, this is Scott Smelby from the Yahoo Bank. Kindly contact me for a vital transaction on: scottsmelby@yahoo.com”. Which statement below is true?
Which best describes the role of a penetration tester?
Packet fragmentation is used as an evasion technique. Which IDS configuration best counters this?
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it? Select the best answers.
During a recent vulnerability assessment of a major corporation's IT systems, the security team identified several potential risks. They want to use a vulnerability scoring system to quantify and prioritize these vulnerabilities. They decide to use the Common Vulnerability Scoring System (CVSS). Given the characteristics of the identified vulnerabilities, which of the following statements is the most accurate regarding the metric
types used by CVSS to measure these vulnerabilities?
During a recent security assessment, you discover the organization has one Domain Name Server (DNS) in a Demilitarized Zone (DMZ) and a second DNS server on the internal network.
What is this type of DNS configuration commonly called?
Insecure direct object reference is a type of vulnerability where the application does not verify if the user is authorized to access the internal object via its name or key. Suppose a malicious user Rob tries to get access to the account of a benign user Ned.
Which of the following requests best illustrates an attempt to exploit an insecure direct object reference vulnerability?
Stephen, an attacker, targeted the industrial control systems of an organization. He generated a fraudulent email with a malicious attachment and sent it to employees of the target organization. An employee who manages the sales software of the operational plant opened the fraudulent email and clicked on the malicious attachment. This resulted in the malicious attachment being downloaded and malware being injected into the sales software maintained in the victim's system. Further, the malware propagated itself to other networked systems, finally damaging the industrial automation components.
What is the attack technique used by Stephen to damage the industrial systems?
PGP, SSL, and IKE are all examples of which type of cryptography?
Elante company has recently hired James as a penetration tester. He was tasked with performing enumeration on an organization's network. In the process of enumeration, James discovered a service that is accessible to external sources. This service runs directly on port 21.
What is the service enumerated by James in the above scenario?
A web server was compromised through DNS hijacking. What would most effectively prevent this in the future?
Henry Is a cyber security specialist hired by BlackEye - Cyber security solutions. He was tasked with discovering the operating system (OS) of a host. He used the Unkornscan tool to discover the OS of the target system. As a result, he obtained a TTL value, which Indicates that the target system is running a Windows OS. Identify the TTL value Henry obtained, which indicates that the target OS is Windows.
Attacker Rony Installed a rogue access point within an organization's perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
As a Certified Ethical Hacker, you are assessing a corporation’s serverless cloud architecture. The organization experienced an attack where a user manipulated a function-as-a-service (FaaS) component to execute malicious commands. The root cause was traced to an insecure third-party API used within a serverless function. What is the most effective countermeasure to strengthen the security posture?
During an internal penetration test within a large corporate environment, the red team gains access to an unrestricted network port in a public-facing meeting room. The tester deploys an automated tool that sends thousands of DHCPDISCOVER requests using randomized spoofed MAC addresses. The DHCP server’s lease pool becomes fully depleted, preventing legitimate users from obtaining IP addresses. What type of attack did the penetration tester perform?
Which of the following steps for risk assessment methodology refers to vulnerability identification?
Mirai malware targets IoT devices. After infiltration, it uses them to propagate and create botnets that are then used to launch which types of attack?
A penetration tester is assessing the security of a corporate wireless network that uses WPA2-Enterprise encryption with RADIUS authentication. The tester wants to perform a man-in-the-middle attack by tricking wireless clients into connecting to a rogue access point. What is the most effective method to achieve this?
Which of the following programs is usually targeted at Microsoft Office products?
An ethical hacker is hired to evaluate the defenses of an organization's database system which is known to employ a signature-based IDS. The hacker knows that some SQL Injection evasion techniques may allow him
to bypass the system's signatures. During the operation, he successfully retrieved a list of usernames from the database without triggering an alarm by employing an advanced evasion technique. Which of the following
could he have used?
A penetration tester discovers that a web application is using outdated SSL/TLS protocols (TLS 1.0) to secure communication. What is the most effective way to exploit this vulnerability?
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security. When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up.
What is the most likely cause?
What is correct about digital signatures?
James is working as an ethical hacker at Technix Solutions. The management ordered James to discover how vulnerable its network is towards footprinting attacks. James took the help of an open-source framework for performing automated reconnaissance activities. This framework helped James in gathering information using free tools and resources.
What is the framework used by James to conduct footprinting and reconnaissance activities?
You suspect a Man-in-the-Middle (MitM) attack inside the network. Which network activity would help confirm this?
Fred is the network administrator for his company. Fred is testing an internal switch. From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
An attacker uses many plaintext–ciphertext pairs and applies statistical analysis to XOR combinations of specific bits. Which technique is being used?
As an Ethical Hacker, you have been asked to test an application’s vulnerability to SQL injection. During testing, you discover an entry field that appears susceptible. However, the backend database is unknown, and regular SQL injection techniques have failed to produce useful information. Which advanced SQL injection technique should you apply next?
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed.
Which security policy must the security analyst check to see if dial-out modems are allowed?
Which of the following statements about a zone transfer is correct? (Choose three.)
An attacker identified that a user and an access point are both compatible with WPA2 and WPA3 encryption. The attacker installed a rogue access point with only WPA2 compatibility in the vicinity and forced the victim to go through the WPA2 four-way handshake to get connected. After the connection was established, the attacker used automated tools to crack WPA2-encrypted messages. What is the attack performed in the above scenario?
Which of the following scanning method splits the TCP header into several packets and makes it difficult for packet filters to detect the purpose of the packet?
Malware infecting multiple systems remains dormant until triggered and changes its code or encryption with each infection to evade detection. Which malware type best fits this description, and what is the most effective mitigation?
Which of the following is the primary objective of a rootkit?
Why is a penetration test considered to be more thorough than a vulnerability scan?
Scenario: Joe turns on his home computer to access personal online banking. When he enters the URL the website is displayed, but it prompts him to re-enter his credentials as if he has never visited the site before. When he examines the website URL closer, he finds that the site is not secure and the web address appears different. What type of attack he is experiencing?.
Vlady wants to improve security awareness among non-technical employees who demonstrate poor security practices. What should be his first step?
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
An ethical hacker audits a hospital’s wireless network secured with WPA using TKIP and successfully performs packet injection and decryption attacks. Which WPA vulnerability most likely enabled this?
Suppose that you test an application for the SQL injection vulnerability. You know that the backend database is based on Microsoft SQL Server. In the login/password form, you enter the following credentials:
Username: attack' or 1=1 --
Password: 123456
Based on the above credentials, which of the following SQL commands are you expecting to be executed by the server, if there is indeed an SQL injection vulnerability?
DHCP snooping is a great solution to prevent rogue DHCP servers on your network. Which security feature on switchers leverages the DHCP snooping database to help prevent man-in-the-middle attacks?
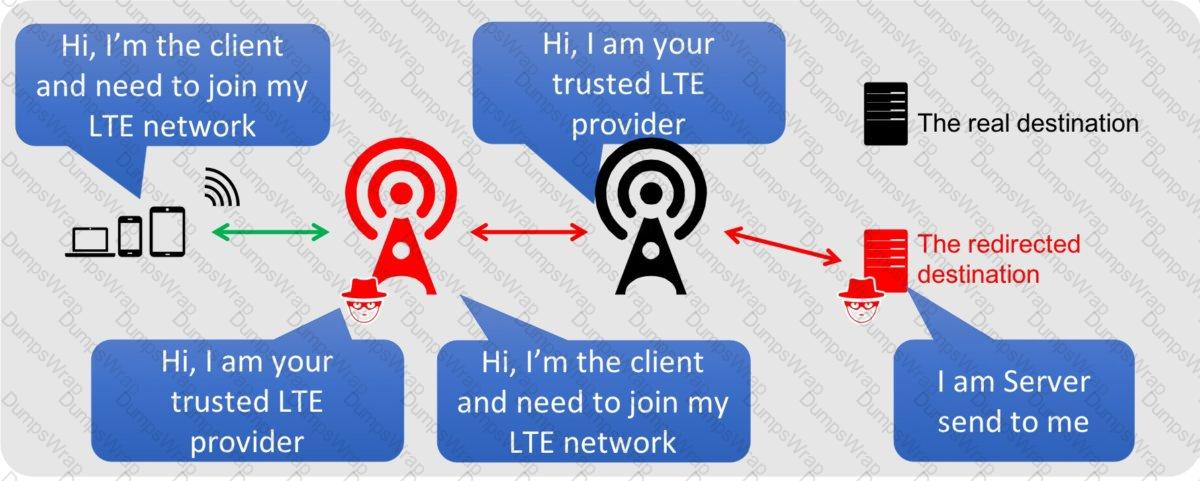
Bobby, an attacker, targeted a user and decided to hijack and intercept all their wireless communications. He installed a fake communication tower between two authentic endpoints to mislead the victim. Bobby used this virtual tower to interrupt the data transmission between the user and real tower, attempting to hijack an active session, upon receiving the users request. Bobby manipulated the traffic with the virtual tower and redirected the victim to a malicious website. What is the attack performed by Bobby in the above scenario?
A tester evaluates a login form that constructs SQL queries using unsanitized user input. By submitting 1 OR 'T'='T'; --, the tester gains unauthorized access to the application. What type of SQL injection has occurred?
A penetration tester discovers that a web application is vulnerable to Local File Inclusion (LFI) due to improper input validation in a URL parameter. Which approach should the tester take to exploit this vulnerability?
A penetration tester is assessing a web application that employs secure, HTTP-only cookies, regenerates session IDs upon login, and uses strict session timeout policies. To hijack a user's session without triggering the application's security defenses, which advanced technique should the tester utilize?
During a UDP service enumeration scan, the tester sees that some ports respond with ICMP Type 3 Code 3 (Port Unreachable), while most remain silent. No firewall or IDS is interfering. What can the tester conclude about the non-responsive ports?
A zero-day vulnerability is actively exploited in a critical web server, but no vendor patch is available. What should be the FIRST step to manage this risk?
A hacker is analyzing a system that uses two rounds of symmetric encryption with different keys. To speed up key recovery, the attacker encrypts the known plaintext with all possible values of the first key and stores the intermediate ciphertexts. Then, they decrypt the final ciphertext using all possible values of the second key and compare the results to the stored values. Which cryptanalytic method does this approach represent?
Which of the following is the BEST way to defend against network sniffing?
Which Nmap switch helps evade IDS or firewalls?
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords.
Which of the following tools would not be useful for cracking the hashed passwords?
Ben purchased a new smartphone and received some updates on it through the OTA method. He received two messages: one with a PIN from the network operator and another asking him to enter the PIN received from the operator. As soon as he entered the PIN, the smartphone started functioning in an abnormal manner.
What is the type of attack performed on Ben in the above scenario?
in the Common Vulnerability Scoring System (CVSS) v3.1 severity ratings, what range does medium vulnerability fall in?
A penetration tester is assessing a web application that uses dynamic SQL queries for searching users in the database. The tester suspects the search input field is vulnerable to SQL injection. What is the best approach to confirm this vulnerability?
As part of a college project, you have set up a web server for hosting your team's application. Given your interest in cybersecurity, you have taken the lead in securing the server. You are aware that hackers often attempt to exploit server misconfigurations. Which of the following actions would best protect your web server from potential misconfiguration-based attacks?
After installing a backdoor on a web server, what action best ensures it remains undetected?
You are a cybersecurity consultant for a global organization. The organization has adopted a Bring Your Own Device (BYOD)policy, but they have recently experienced a phishing incident where an employee's device was compromised. In the investigation, you discovered that the phishing attack occurred through a third-party email app that the employee had installed. Given the need to balance security and user autonomy under the BYOD policy, how should the organization mitigate the risk of such incidents? Moreover, consider a measure that would prevent similar attacks without overly restricting the use of personal devices.
Alice, a professional hacker, targeted an organization's cloud services. She infiltrated the targets MSP provider by sending spear-phishing emails and distributed custom-made malware to compromise user accounts and gain remote access to the cloud service. Further, she accessed the target customer profiles with her MSP account, compressed the customer data, and stored them in the MSP. Then, she used this information to launch further attacks on the target organization. Which of the following cloud attacks did Alice perform in the above scenario?
A zone file consists of which of the following Resource Records (RRs)?
Robin, a professional hacker, targeted an organization's network to sniff all the traffic. During this process.
Robin plugged in a rogue switch to an unused port in the LAN with a priority lower than any other switch in the network so that he could make it a root bridge that will later allow him to sniff all the traffic in the network.
What is the attack performed by Robin in the above scenario?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
What is this attack?
SQL injection (SQLi) attacks attempt to inject SQL syntax into web requests, which may Bypass authentication and allow attackers to access and/or modify data attached to a web application.
Which of the following SQLI types leverages a database server's ability to make DNS requests to pass data to an attacker?
John, a professional hacker, targeted an organization that uses LDAP for accessing distributed directory services. He used an automated tool to anonymously query the IDAP service for sensitive information such as usernames. addresses, departmental details, and server names to launch further attacks on the target organization.
What is the tool employed by John to gather information from the IDAP service?
Clark is a professional hacker. He created and configured multiple domains pointing to the same host to switch quickly between the domains and avoid detection.
Identify the behavior of the adversary In the above scenario.
Sam is a penetration tester hired by Inception Tech, a security organization. He was asked to perform port scanning on a target host in the network. While performing the given task, Sam sends FIN/ACK probes and determines that an RST packet is sent in response by the target host, indicating that the port is closed.
What is the port scanning technique used by Sam to discover open ports?
A penetration tester must enumerate user accounts and network resources in a highly secured Windows environment where SMB null sessions are blocked. Which technique should be used to gather this information discreetly?
A city’s power management system relies on SCADA infrastructure. Recent anomalies include inconsistent sensor readings and intermittent outages. Security analysts suspect a side-channel attack designed to extract sensitive information covertly from SCADA devices. Which investigative technique would best confirm this type of attack?
Bob is acknowledged as a hacker of repute and is popular among visitors of "underground" sites. Bob is willing to share his knowledge with those who are willing to learn, and many have expressed their interest in learning from him. However, this knowledge has a risk associated with it, as it can be used for malevolent attacks as well.
In this context, what would be the most effective method to bridge the knowledge gap between the "black" hats or crackers and the "white" hats or computer security professionals?
When discussing passwords, what is considered a brute force attack?
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure instead of SQL’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
A penetration tester is tasked with identifying vulnerabilities on a web server running outdated software. The server hosts several web applications and is protected by a basic firewall. Which technique should the tester use to exploit potential server vulnerabilities?
These hackers have limited or no training and know how to use only basic techniques or tools. What kind of hackers are we talking about?
Which advanced session hijacking technique is hardest to detect and mitigate in a remote-access environment?
in this attack, an adversary tricks a victim into reinstalling an already-in-use key. This is achieved by manipulating and replaying cryptographic handshake messages. When the victim reinstall the key, associated parameters such as the incremental transmit packet number and receive packet number are reset to their initial values. What is this attack called?
A company’s policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wireshark to examine the captured traffic, which command can be used as display filter to find unencrypted file transfers?
John, a professional hacker, targeted CyberSol Inc., an MNC. He decided to discover the IoT devices connected in the target network that are using default credentials and are vulnerable to various hijacking attacks. For this purpose, he used an automated tool to scan the target network for specific types of IoT devices and detect whether they are using the default, factory-set credentials. What is the tool employed by John in the above scenario?
What type of analysis is performed when an attacker has partial knowledge of inner-workings of the application?
Mason, a professional hacker, targets an organization and spreads Emotet malware through malicious script. After infecting the victim's device. Mason further used Emotet to spread the infection across local networks and beyond to compromise as many machines as possible. In this process, he used a tool, which is a self-extracting RAR file, to retrieve information related to network resources such as writable share drives. What is the tool employed by Mason in the above scenario?
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE and can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
While browsing his Facebook feed, Matt sees a picture one of his friends posted with the caption, "Learn more about your friends!", along with a number of personal questions. Matt is suspicious and texts his friend, who confirms that he did indeed post it. With assurance that the post is legitimate, Matt responds to the questions in the post. A few days later, Matt's bank account has been accessed, and the password has been changed. What most likely happened?
Fleet vehicles with smart locking systems were compromised after attackers captured unique signals from key fobs. What should the security team prioritize to confirm and prevent this attack?
Which of the following is assured by the use of a hash?
A penetration tester finds that a web application does not properly validate user input and is vulnerable to reflected Cross-Site Scripting (XSS). What is the most appropriate approach to exploit this vulnerability?
_________ is a tool that can hide processes from the process list, can hide files, registry entries, and intercept keystrokes.
Websites and web portals that provide web services commonly use the Simple Object Access Protocol (SOAP).
Which of the following is an incorrect definition or characteristic of the protocol?
In the process of footprinting a target website, an ethical hacker utilized various tools to gather critical information. The hacker encountered a target site where standard web spiders were ineffective due to a specific file in its root directory. However, they managed to uncover all the files and web pages on the target site, monitoring the resulting incoming and outgoing traffic while browsing the website manually. What technique did the hacker likely employ to achieve this?
While testing a web application that relies on JavaScript-based client-side security controls, which method is most effective for bypassing these controls without triggering server-side alerts?
Jake, a professional hacker, installed spyware on a target iPhone to spy on the target user's activities. He can take complete control of the target mobile device by jailbreaking the device remotely and record audio, capture screenshots, and monitor all phone calls and SMS messages. What is the type of spyware that Jake used to infect the target device?
In a highly secure online banking environment, customers report unauthorized access to their accounts despite robust authentication controls. Investigation reveals attackers are using advanced session hijacking techniques to perform fraudulent transactions. Which advanced session-hijacking attack, resembling a scenario-based attack, presents the greatest challenge to detect and mitigate?
An organization is performing a vulnerability assessment tor mitigating threats. James, a pen tester, scanned the organization by building an inventory of the protocols found on the organization's machines to detect which ports are attached to services such as an email server, a web server or a database server. After identifying the services, he selected the vulnerabilities on each machine and started executing only the relevant tests. What is the type of vulnerability assessment solution that James employed in the above scenario?
You are a cybersecurity specialist at CloudTech Inc., a company providing cloud-based services. You are managing a project for a client who wants to migrate their sensitive data to a public cloud service. To comply with regulatory requirements, the client insists on maintaining full control over the encryption keys even when the data is at rest on the cloud. Which of the following practices should you implement to meet this requirement?
A cybersecurity analyst in an organization is using the Common Vulnerability Scoring System to assess and prioritize identified vulnerabilities in their IT infrastructure. They encountered a vulnerability with a base metric score of 7, a temporal metric score of 8, and an environmental metric score of 5. Which statement best describes this scenario?
A web application returns generic error messages. The analyst submits AND 1=1 and AND 1=2 and observes different responses. What type of injection is being tested?
Which payload is most effective for testing time-based blind SQL injection?
During a black-box internal penetration test, a security analyst identifies an SNMPv2-enabled Linux server using the default community string “public.” The analyst wants to enumerate running processes. Which Nmap command retrieves this information?
Which of the following provides a security professional with most information about the system’s security posture?
A penetration tester is tasked with gathering information about the subdomains of a target organization's website. The tester needs a versatile and efficient solution for the task. Which of the following options would be the most effective method to accomplish this goal?
You are an ethical hacker contracted to conduct a security audit for a company. During the audit, you discover that the company's wireless network is using WEP encryption. You understand the vulnerabilities associated with WEP and plan to recommend a more secure encryption method. Which of the following would you recommend as a Suitable replacement to enhance the security of the company's wireless network?
Attacker Steve targeted an organization's network with the aim of redirecting the company's web traffic to another malicious website. To achieve this goal, Steve performed DNS cache poisoning by exploiting the vulnerabilities In the DNS server software and modified the original IP address of the target website to that of a fake website. What is the technique employed by Steve to gather information for identity theft?
E-mail scams and mail fraud are regulated by which of the following?
Which Intrusion Detection System is the best applicable for large environments where critical assets on the network need extra scrutiny and is ideal for observing sensitive network segments?
Cross-site request forgery involves:
John, a professional hacker, decided to use DNS to perform data exfiltration on a target network, in this process, he embedded malicious data into the DNS protocol packets that even DNSSEC cannot detect. Using this technique. John successfully injected malware to bypass a firewall and maintained communication with the victim machine and C&C server. What is the technique employed by John to bypass the firewall?
What is the most common method to exploit the “Bash Bug” or “Shellshock” vulnerability?
An ethical hacker is testing the security of a website's database system against SQL Injection attacks. They discover that the IDS has a strong signature detection mechanism to detect typical SQL injection patterns.
Which evasion technique can be most effectively used to bypass the IDS signature detection while performing a SQL Injection attack?
An attacker scans a host with the below command. Which three flags are set?
# nmap -sX host.domain.com
A penetration tester suspects that the web application's "Order History" page is vulnerable to SQL injection because it displays user orders based on an unprotected user ID parameter in the URL. What is the most appropriate approach to test this?
During a security assessment of an internal network, a penetration tester discovers that UDP port 123 is open, indicating that the NTP service is active. The tester wants to enumerate NTP peers, check synchronization status, offset, and stratum levels. Which command should the tester use?
A penetration tester evaluates a secure web application using HTTPS, secure cookies, and multi-factor authentication. To hijack a legitimate user’s session without triggering alerts, which technique should be used?
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?
Which of the following DoS tools is used to attack target web applications by starvation of available sessions on the web server? The tool keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value.
Calvin, a software developer, uses a feature that helps him auto-generate the content of a web page without manual involvement and is integrated with SSI directives. This leads to a vulnerability in the developed web application as this feature accepts remote user inputs and uses them on the page. Hackers can exploit this feature and pass malicious SSI directives as input values to perform malicious activities such as modifying and erasing server files. What is the type of injection attack Calvin's web application is susceptible to?
Which sophisticated DoS technique is hardest to detect and mitigate?
A web server is overwhelmed by many slow, incomplete HTTP connections. What attack is occurring?
Susan has attached to her company's network. She has managed to synchronize her boss's sessions with that of the file server. She then intercepted his traffic destined for the server, changed it the way she wanted to and then placed it on the server in his home directory.
What kind of attack is Susan carrying on?
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, volumes. Images, and networks. What is the component of the Docker architecture used by Annie in the above scenario?
Why should the security analyst disable/remove unnecessary ISAPI filters?
A penetration tester is tasked with scanning a network protected by an IDS and firewall that actively blocks connection attempts on non-standard ports. The tester needs to gather information on the target system without triggering alarms. Which technique should the tester use to evade detection?
Joseph was the Web site administrator for the Mason Insurance in New York, whose main website was located at Joseph uses his laptop computer regularly to administer the website. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance website had been vandalized! All of its normal content was removed and replaced with an attacker’s message:
“H@cker Mess@ge: Y0u @re De@d! Fre@ks!”
From his office network (internal), Joseph saw the normal site. But from an external DSL connection, users saw the defaced site. Joseph checked the web server with Tripwire and found no system file or content change.
How did the attacker accomplish this hack?
A penetration tester evaluates a company's secure web application, which uses HTTPS, secure cookie flags, and strict session management to prevent session hijacking. To bypass these protections and hijack a legitimate user's session without detection, which advanced technique should the tester employ?
Which Metasploit Framework tool can help penetration tester for evading Anti-virus Systems?
During a stealth assessment, an attacker exploits intermittent delays in ARP responses from a target system. By injecting fake ARP replies before legitimate ones, the attacker temporarily redirects traffic to their own device, allowing intermittent packet capture. What type of sniffing attack is occurring?
A penetration tester is tasked with mapping an organization's network while avoiding detection by sophisticated intrusion detection systems (IDS). The organization employs advanced IDS capable of recognizing common scanning patterns. Which scanning technique should the tester use to effectively discover live hosts and open ports without triggering the IDS?
A multinational corporation recently survived a severe Distributed Denial-of-Service (DDoS) attack and has implemented enhanced security measures. During an audit, you discover that the organization uses both hardware- and cloud-based solutions to distribute incoming traffic in order to absorb and mitigate DDoS attacks while ensuring legitimate traffic remains available. What type of DDoS mitigation strategy is the company utilizing?
A penetration tester observes that traceroutes to various internal devices always show 10.10.10.1 as the second-to-last hop, regardless of the destination subnet. What does this pattern most likely indicate?
Which is the first step followed by Vulnerability Scanners for scanning a network?
ping - * 6 192.168.0.101
Output:
Pinging 192.168.0.101 with 32 bytes of data:
Reply from 192.168.0.101: bytes=32 time<1ms TTL=128
...
Packets: Sent = 6, Received = 6, Lost = 0 (0% loss)
What does the option * indicate?
John wants to send Marie an email that includes sensitive information, and he does not trust the network that he is connected to. Marie gives him the idea of using PGP. What should John do to communicate correctly using this type of encryption?
What is the first step for a hacker conducting a DNS cache poisoning (DNS spoofing) attack against an organization?
A CEH has mirrored a website, identified session hijacking risk, and wants to minimize detection. What is the most appropriate next step?
A global fintech company receives extortion emails threatening a severe DDoS attack unless ransom is paid. The attacker briefly launches an HTTP flood to demonstrate capability. The attack uses incomplete POST requests that overload application-layer resources, causing performance degradation. The attacker reinforces their demand with a second threat email. What type of DDoS attack is being carried out?
You are performing a penetration test for a client and have gained shell access to a Windows machine on the internal network. You intend to retrieve all DNS records for the internal domain. If the DNS server is at 192.168.10.2 and the domain name is abccorp.local, what command would you type at the nslookup prompt to attempt a zone transfer?
What type of a vulnerability/attack is it when the malicious person forces the user’s browser to send an authenticated request to a server?
Allen, a professional pen tester, was hired by xpertTech solutWns to perform an attack simul-ation on the organization's network resources. To perform the attack, he took advantage of the NetBIOS API and targeted the NetBIOS service. B/enumerating NetBIOS, he found that port 139 was open and could see the resources that could be accessed or viewed on a remote system. He came across many NetBIOS codes during enumeration.
identify the NetBIOS code used for obtaining the messenger service running for the logged-in user?
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user’s password or activate disabled Windows accounts?
Shellshock allowed an unauthorized user to gain access to a server. It affected many Internet-facing services, which OS did it not directly affect?
Which of the following Metasploit post-exploitation modules can be used to escalate privileges on Windows systems?
An attacker analyzes how small changes in plaintext input affect ciphertext output to deduce encryption key patterns in a symmetric algorithm. What technique is being used?
In an attempt to damage the reputation of a competitor organization, Hailey, a professional hacker, gathers a list of employee and client email addresses and other related information by using various search engines, social networking sites, and web spidering tools. In this process, she also uses an automated tool to gather a list of words from the target website to further perform a brute-force attack on the previously gathered email addresses.
What is the tool used by Hailey for gathering a list of words from the target website?
Abel, a security professional, conducts penetration testing in his client organization to check for any security loopholes. He launched an attack on the DHCP servers by broadcasting forged DHCP requests and leased all the DHCP addresses available in the DHCP scope until the server could not issue any more IP addresses. This led to a Dos attack, and as a result, legitimate employees were unable to access the clients network. Which of the following attacks did Abel perform in the above scenario?
A penetration tester evaluates the security of an iOS mobile application that handles sensitive user information. The tester discovers that the application is vulnerable to insecure data transmission. What is the most effective method to exploit this vulnerability?
Gerard, a disgruntled ex-employee of Sunglass IT Solutions, targets this organization to perform sophisticated attacks and bring down its reputation in the market. To launch the attacks process, he performed DNS footprinting to gather information about ONS servers and to identify the hosts connected in the target network. He used an automated tool that can retrieve information about DNS zone data including DNS domain names, computer names. IP addresses. DNS records, and network Who is records. He further exploited this information to launch other sophisticated attacks. What is the tool employed by Gerard in the above scenario?
Which technique is most likely used to evade detection by an Intrusion Detection System (IDS)?
A large corporate network is being subjected to repeated sniffing attacks. To increase security, the company’s IT department decides to implement a combination of several security measures. They permanently add theMAC address of the gateway to the ARP cache, switch to using IPv6 instead of IPv4, implement the use of encrypted sessions such as SSH instead of Telnet, and use Secure File Transfer Protocol instead of FTP.
However, they are still faced with the threat of sniffing. Considering the countermeasures, what should be their next step to enhance network security?
You are attempting to crack LM Manager hashes from a Windows 2000 SAM file. You will be using an LM brute-force hacking tool for decryption.
What encryption algorithm will you be decrypting?
Working as an Information Security Analyst at a technology firm, you are designing training material for employees about the dangers of session hijacking. As part of the training, you want to explain how attackers could use sidejacking to compromise user accounts. Which of the following scenarios most accurately describes a sidejacking attack?
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing "server publishing"?
At what stage of the cyber kill chain theory model does data exfiltration occur?
A penetration tester is conducting a security assessment for a client and needs to capture sensitive information transmitted across multiple VLANs without being detected by the organization's security monitoring systems. The network employs strict VLAN segmentation and port security measures. Which advanced sniffing technique should the tester use to discreetly intercept and analyze traffic across all VLANs?
An employee finds a USB drive labeled “Employee Salary Info 2024” and plugs it into a company computer, causing erratic behavior. What type of social engineering attack is this?
A penetration tester identifies that a web application's login form is not using secure password hashing mechanisms, allowing attackers to steal passwords if the database is compromised. What is the best approach to exploit this vulnerability?
Robert, a professional hacker, is attempting to execute a fault injection attack on a target IoT device. In this process, he injects faults into the power supply that can be used for remote execution, also causing the skipping of key instructions. He also injects faults into the clock network used for delivering a synchronized signal across the chip.
Which of the following types of fault injection attack is performed by Robert in the above scenario?
You have compromised a server and successfully gained a root access. You want to pivot and pass traffic undetected over the network and evade any possible Intrusion Detection System. What is the best approach?
OpenSSL on Linux servers includes a command line tool for testing TLS. What is the name of the tool and the correct syntax to connect to a web server?
Study the snort rule given below and interpret the rule:
alert tcp any any --> 192.168.1.0/24 111 (content:"|00 01 86 a5|"; msg: "mountd access";)
During enumeration, a tool sends requests to UDP port 161 and retrieves a large list of installed software due to a publicly known community string. What enabled this technique to work so effectively?
Targeted, logic-based credential guessing using prior intel best describes which technique?
As a cybersecurity professional, you are responsible for securing a high-traffic web application that uses MySQL as its backend database. Recently, there has been a surge of unauthorized login attempts, and you suspect that a seasoned black-hat hacker is behind them. This hacker has shown proficiency in SQL Injection and
appears to be using the 'UNION' SQL keyword to trick the login process into returning additional data.
However, your application's security measures include filtering special characters in user inputs, a method usually effective against such attacks. In this challenging environment, if the hacker still intends to exploit this SQL Injection vulnerability, which strategy is he most likely to employ?
A penetration tester has gained access to a target system using default credentials. What is the most effective next step to escalate privileges on the system?
Which method of password cracking takes the most time and effort?
You discover an unpatched Android permission-handling vulnerability on a device with fully updated antivirus software. What is the most effective exploitation approach that avoids antivirus detection?
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
Techno Security Inc. recently hired John as a penetration tester. He was tasked with identifying open ports in the target network and determining whether the ports are online and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan on the target network. Which of the following Nmap commands must John use to perform the TCP SYN ping scan?
During security awareness training, which scenario best describes a tailgating social engineering attack?
In this attack, a victim receives an e-mail claiming to be from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN, and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
What is not a PCI compliance recommendation?
During a covert red team engagement, a penetration tester is tasked with identifying live hosts in a target organization’s internal subnet (10.0.0.0/24) without triggering intrusion detection systems (IDS). To remain undetected, the tester opts to use the command nmap -sn -PE 10.0.0.0/24, which results in several "Host is up" responses, even though the organization’s IDS is tuned to detect high-volume scans. After the engagement, the client reviews the logs and is surprised that the scan was not flagged. What allowed the scan to complete without triggering alerts?
A penetration tester was assigned to scan a large network range to find live hosts. The network is known for using strict TCP filtering rules on its firewall, which may obstruct common host discovery techniques. The tester needs a method that can bypass these firewall restrictions and accurately identify live systems. What host discovery technique should the tester use?
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
During an internal security assessment of a medium-sized enterprise network, a security analyst notices an unusual spike in ARP traffic. Closer inspection reveals that one particular MAC address is associated with multiple IP addresses across different subnets. The ARP packets were unsolicited replies rather than requests, and several employees from different departments have reported intermittent connection drops, failed logins, and broken intranet sessions. The analyst suspects an intentional interference on the local network segment. What is the most likely cause of this abnormal behavior?
During testing against a network protected by a signature-based IDS, the tester notices that standard scans are blocked. To evade detection, the tester sends TCP headers split into multiple small IP fragments so the IDS cannot reassemble or interpret them, but the destination host can. What technique is being used?
Which scenario best represents a social engineering attack?
A payload causes a significant delay in response without visible output when testing an Oracle-backed application. What SQL injection technique is being used?
How can rainbow tables be defeated?
Which action would most effectively increase the security of a virtual-hosted web server?
Which type of security feature stops vehicles from crashing through the doors of a building?
A friend of yours tells you that he downloaded and executed a file that was sent to him by a coworker. Since the file did nothing when executed, he asks you for help because he suspects that he may have installed a Trojan on his computer.
What tests would you perform to determine whether his computer is infected?
Which advanced mobile attack is hardest to detect and mitigate?
Johnson, an attacker, performed online research for the contact details of reputed cybersecurity firms. He found the contact number of sibertech.org and dialed the number, claiming himself to represent a technical support team from a vendor. He warned that a specific server is about to be compromised and requested sibertech.org to follow the provided instructions. Consequently, he prompted the victim to execute unusual commands and install malicious files, which were then used to collect and pass critical Information to Johnson's machine. What is the social engineering technique Steve employed in the above scenario?
Encrypted session tokens vary in length, indicating inconsistent encryption strength. What is the best mitigation?
Systems are communicating with unknown external entities, raising concerns about exfiltration or malware. Which strategy most directly identifies and mitigates the risk?
During a red team engagement, an ethical hacker discovers that a thermostat accepts older firmware versions without verifying their authenticity. By loading a deprecated version containing known vulnerabilities, the tester gains unauthorized access to the broader network. Which IoT security issue is most accurately demonstrated in this scenario?
Which wireless security protocol replaces the personal pre-shared key (PSK) authentication with Simultaneous Authentication of Equals (SAE) and is therefore resistant to offline dictionary attacks?
When configuring wireless on his home router, Javik disables SSID broadcast. He leaves authentication “open” but sets the SSID to a 32-character string of random letters and numbers.
What is an accurate assessment of this scenario from a security perspective?
You want to analyze packets on your wireless network. Which program would you use?
A skilled ethical hacker was assigned to perform a thorough OS discovery on a potential target. They decided to adopt an advanced fingerprinting technique and sent a TCP packet to an open TCP port with specific flags enabled. Upon receiving the reply, they noticed the flags were SYN and ECN-Echo. Which test did the ethical hacker conduct and why was this specific approach adopted?
During an ethical hacking exercise, a security analyst is testing a web application that manages confidential information and suspects it may be vulnerable to SQL injection. Which payload would most likely reveal whether the application is vulnerable to time-based blind SQL injection?
Working as an Information Security Analyst, you are creating training material on session hijacking. Which scenario best describes a side jacking attack?
What is the main difference between ethical hacking and malicious hacking?
A penetration tester is attacking a wireless network running WPA3 encryption. Since WPA3 handshake protections prevent offline brute-force cracking, what is the most effective approach?
What kind of detection techniques is being used in antivirus software that identifies malware by collecting data from multiple protected systems and instead of analyzing files locally it’s made on the provider’s environment?
Emily, an extrovert obsessed with social media, posts a large amount of private information, photographs, and location tags of recently visited places. Realizing this. James, a professional hacker, targets Emily and her acquaintances, conducts a location search to detect their geolocation by using an automated tool, and gathers information to perform other sophisticated attacks. What is the tool employed by James in the above scenario?
What is the known plaintext attack used against DES which gives the result that encrypting plaintext with one DES key followed by encrypting it with a second DES key is no more secure than using a single key?
How is the public key distributed in an orderly, controlled fashion so that the users can be sure of the sender’s identity?
ViruXine.W32 virus hides its presence by changing the underlying executable code. This virus code mutates while keeping the original algorithm intact — the code changes itself each time it runs, but the function of the code (its semantics) does not change at all.
Here is a section of the virus code (refer to image), where the loop performs XOR encryption and changes the way the code looks every time it is executed.
What is this technique called?
When considering how an attacker may exploit a web server, what is web server footprinting?
Jack, a disgruntled ex-employee of Incalsol Ltd., decided to inject fileless malware into Incalsol's systems. To deliver the malware, he used the current employees' email IDs to send fraudulent emails embedded with malicious links that seem to be legitimate. When a victim employee clicks on the link, they are directed to a fraudulent website that automatically loads Flash and triggers the exploit. What is the technique used byjack to launch the fileless malware on the target systems?
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
A penetration tester needs to map open ports on a target network without triggering the organization’s intrusion detection systems (IDS), which are configured to detect standard scanning patterns and abnormal traffic volumes. To achieve this, the tester decides to use a method that leverages a third-party host to obscure the origin of the scan. Which scanning technique should be employed to accomplish this stealthily?
Why are containers less secure than virtual machines?
Which information CANNOT be directly obtained from DNS interrogation?
During a routine security audit, administrators discover that cloud storage backups were illegally accessed and modified. Which countermeasure would most directly mitigate such incidents in the future?
You discover a Web API integrated with webhooks and an existing administrative web shell. Your objective is to compromise the system while leaving minimal traces. Which technique is most effective?
In your cybersecurity class, you are learning about common security risks associated with web servers. One topic that comes up is the risk posed by using default server settings. Why is using default settings ona web - server considered a security risk, and what would be the best initial step to mitigate this risk?
Which advanced evasion technique poses the greatest challenge to detect and mitigate?
As a security analyst, you are testing a company’s network for potential vulnerabilities. You suspect an attacker may be using MAC flooding to compromise network switches and sniff traffic. Which of the following indicators would most likely confirm your suspicion?
What kind of detection technique is used in antivirus software that collects data from multiple protected systems and performs analysis in a cloud-based environment?
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host
10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he
applied his ACL configuration in the router, nobody can access the ftp, and the permitted hosts cannot access
the Internet. According to the next configuration, what is happening in the network?
access-list 102 deny tcp any any
access-list 104 permit udp host 10.0.0.3 any
access-list 110 permit tcp host 10.0.0.2 eq www any
access-list 108 permit tcp any eq ftp any
Why is using Google Hacking justified during passive footprinting?
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of control objectives. Each objective contains one or more requirements, which must be followed in order to achieve compliance. Which of the following requirements would best fit under the objective, "Implement strong access control measures"?
Larry, a security professional in an organization, has noticed some abnormalities In the user accounts on a web server. To thwart evolving attacks, he decided to harden the security of the web server by adopting a countermeasures to secure the accounts on the web server.
Which of the following countermeasures must Larry implement to secure the user accounts on the web server?
While conducting a covert penetration test on a UNIX-based infrastructure, the tester decides to bypass intrusion detection systems by sending specially crafted TCP packets with an unusual set of flags enabled. These packets do not initiate or complete any TCP handshake. During the scan, the tester notices that when certain ports are probed, there is no response from the target, but for others, a TCP RST (reset) packet is received. The tester notes that this behavior consistently aligns with open and closed ports. Based on these observations, which scanning technique is most likely being used?
As a cybersecurity analyst for SecureNet, you are performing a security assessment of a new mobile payment application. One of your primary concerns is the secure storage of customer data on the device. The application
stores sensitive information such as credit card details and personal identification numbers (PINs) on the device. Which of the following measures would best ensure the security of this data?
You're the security manager for a tech company that uses a database to store sensitive customer data. You have implemented countermeasures against SQL injection attacks. Recently, you noticed some suspicious
activities and suspect an attacker is using SQL injection techniques. The attacker is believed to use different forms of payloads in his SQL queries. In the case of a successful SQL injection attack, which of the following
payloads would have the most significant impact?
Which scenario best describes a slow, stealthy scanning technique?
A penetration tester is running a vulnerability scan on a company’s network. The scan identifies an open port with a high-severity vulnerability linked to outdated software. What is the most appropriate next step for the tester?
Dorian Is sending a digitally signed email to Polly, with which key is Dorian signing this message and how is Poly validating It?
The tools which receive event logs from servers, network equipment, and applications, and perform analysis and correlation on those logs, and can generate alarms for security relevant issues, are known as what?
To invisibly maintain access to a machine, an attacker utilizes a toolkit that sits undetected In the core components of the operating system. What is this type of rootkit an example of?
In the field of cryptanalysis, what is meant by a “rubber-hose” attack?
Ricardo has discovered the username for an application in his targets environment. As he has a limited amount of time, he decides to attempt to use a list of common passwords he found on the Internet. He compiles them into a list and then feeds that list as an argument into his password-cracking application, what type of attack is Ricardo performing?
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
Which command can be used to show the current TCP/IP connections?
While performing a security audit of a web application, an ethical hacker discovers a potential vulnerability.
The application responds to logically incorrect queries with detailed error messages that divulge the underlying database's structure. The ethical hacker decides to exploit this vulnerability further. Which type of SQL Injection attack is the ethical hacker likely to use?
On performing a risk assessment, you need to determine the potential impacts when some of the critical business processes of the company interrupt its service.
What is the name of the process by which you can determine those critical businesses?
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124. An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is: nmap 192.168.1.64/28.
Why he cannot see the servers?
A penetration tester is performing an enumeration on a client's network. The tester has acquired permission to perform enumeration activities. They have identified a remote inter-process communication (IPC) share and are trying to collect more information about it. The tester decides to use a common enumeration technique to collect the desired data. Which of the following techniques would be most appropriate for this scenario?
An experienced cyber attacker has created a fake Linkedin profile, successfully impersonating a high-ranking official from a well-established company, to execute a social engineering attack. The attacker then connected with other employees within the organization, receiving invitations to exclusive corporate events and gaining
access to proprietary project details shared within the network. What advanced social engineering technique has the attacker primarily used to exploit the system and what is the most likely immediate threat to the organization?
Which of the following tools is used to detect wireless LANs using the 802.11a/b/g/n WLAN standards on a linux platform?
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list prevents you from establishing a successful connection.
You want to retrieve the Cisco configuration from the router. How would you proceed?
In the context of password security, a simple dictionary attack involves loading a dictionary file into a cracking application such as L0phtCrack or John the Ripper. The brute force method is slow but exhaustive. If you use both brute force and dictionary methods combined to vary words, what would you call such an attack?
A penetration tester is tasked with uncovering historical content from a company’s website, including previously exposed login portals or sensitive internal pages. Direct interaction with the live site is prohibited due to strict monitoring policies. To stay undetected, the tester decides to explore previously indexed snapshots of the organization’s web content saved by external sources. Which approach would most effectively support this passive information-gathering objective?
A penetration tester is investigating a web server that allows unrestricted file uploads without validating file types. Which technique should be used to exploit this vulnerability and potentially gain control of the server?
What is the file that determines the basic configuration (specifically activities, services, broadcast receivers, etc.) in an Android application?