Associate - Information Storage and Management (Version 5.0) Questions and Answers
Refer to the exhibit:
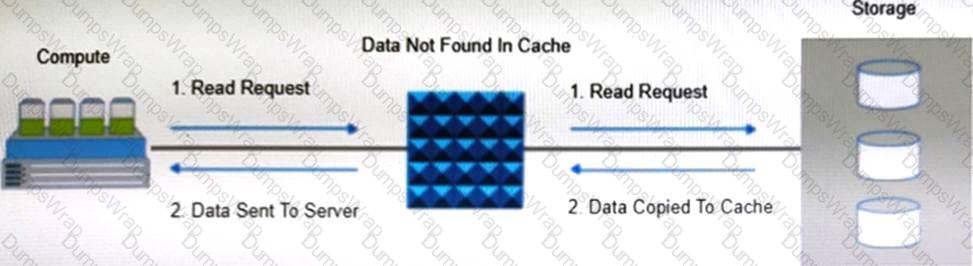
Which operation is represented?
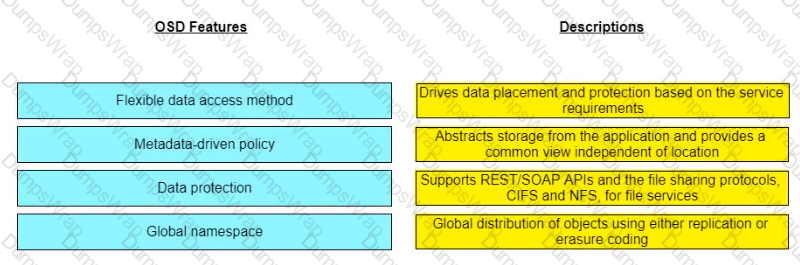
Match the object-based storage device (OSD) features with their descriptions.
In a NAS environment, which file system enables file sharing with Windows clients and uses the TCP/IP protocol?
Which method automatically allocates a large capacity secondary cache using SSD and SCM?
What is a feature a hypervisor?
Which management monitoring parameter involves examining the amount of infrastructure resources used?
What is a goal of cyber recovery?
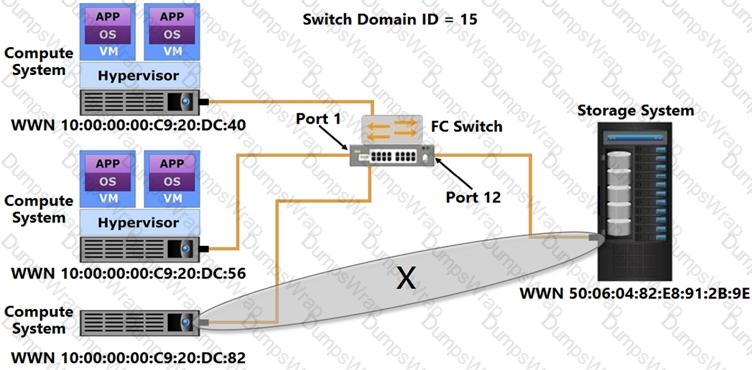
Refer to the Exhibit:
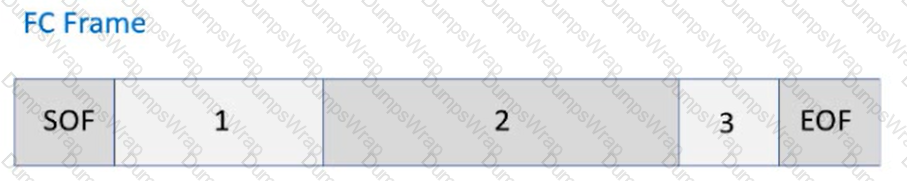
Identify the following FC Frame fields:
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
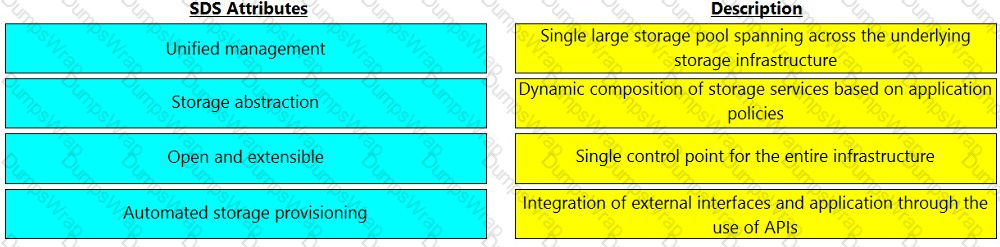
Match the software-defined storage (SDS) attributes with their respective description.
Based on the exhibit, what does the "X" represent in the FCIP tunnel configuration?

Refer to the exhibit.
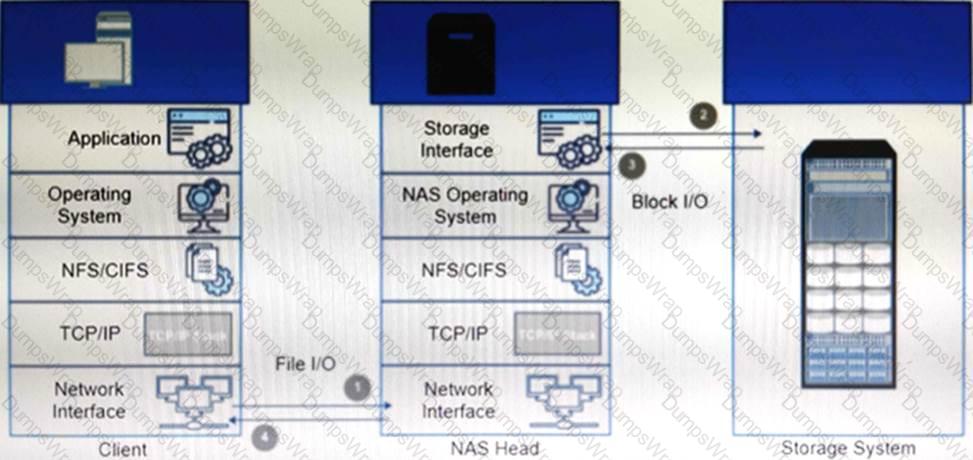
What type of NAS system(s) processes file write and read operations as described in the example?
Which type of zoning does the “X” represent?
What describes an incident in a storage infrastructure?
A company's assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
What is the maximum number of VLANs that can be supported with one VLAN tag field?
What is determined by the amount of space configured for the journal in continuous data protection (CDP) replication?
Which interface does an SCM device use to connect to intelligent storage system controllers?
Which file system provides a streaming interface using the MapReduce framework?
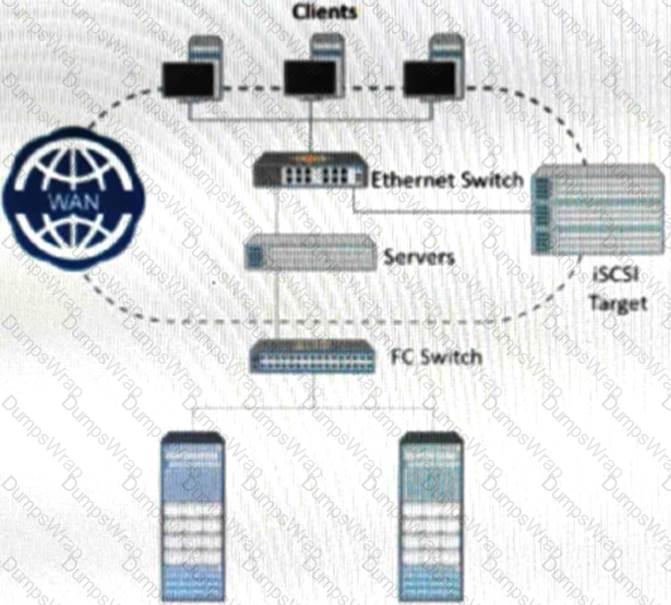
What type of network connectivity is illustrated in the image below?
What is a function of a continuous data protection (CDP) appliance?



