Forescout Certified Professional Exam Questions and Answers
Select the action that requires symmetrical traffic.
Options:
Assign to VLAN
WLAN block
Endpoint ACL
Start SecureConnector
Virtual Firewall
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and Switch Plugin documentation, the action that requires symmetrical traffic is the Endpoint Address ACL action (C).
What "Symmetrical Traffic" Means:
Symmetrical traffic refers to network traffic where CounterACT can monitor BOTH directions of communication:
Inbound - Traffic from the endpoint
Outbound - Traffic to the endpoint
This allows CounterACT to see the complete conversation flow.
Endpoint Address ACL Requirements:
According to the Switch Plugin documentation:
"The Endpoint Address ACL action applies an ACL that delivers blocking protection when endpoints connect to the network. Other benefits of Endpoint Address ACL include..."
For the Endpoint Address ACL to function properly, CounterACT must:
See bidirectional traffic - Monitor packets in both directions
Apply dynamic ACLs - Create filtering rules based on both source and destination
Verify endpoints - Ensure the endpoint IP/MAC matches expected patterns in both directions
Why Symmetrical Traffic is Required:
According to the documentation:
Endpoint Address ACLs work by:
Identifying the endpoint's MAC address and IP address through bidirectional observation
Creating switch ACLs that filter based on the endpoint's communication patterns
Verifying the endpoint is communicating in expected ways (symmetrically)
Without symmetrical traffic visibility, CounterACT cannot reliably identify and apply address-based filtering.
Why Other Options Do NOT Require Symmetrical Traffic:
A. Assign to VLAN - Only requires knowing the switch port; doesn't need traffic monitoring
B. WLAN block - Works at the wireless access point level without needing symmetrical traffic observation
D. Start SecureConnector - Deployment action that doesn't require traffic symmetry
E. Virtual Firewall - Works at the endpoint level and can function with asymmetrical or passive monitoring
Asymmetrical vs. Symmetrical Deployment:
According to the administrative guide:
Asymmetrical Deployment - CounterACT sees traffic from one direction only
Used for passive monitoring of device discovery
Sufficient for many actions
Symmetrical Deployment - CounterACT sees traffic in both directions
Required for endpoint ACL actions
Necessary for accurate address-based filtering
Referenced Documentation:
Endpoint Address ACL Action documentation
ForeScout CounterACT Administration Guide - Switch Plugin actions
Policies will recheck when certain conditions are met. These may include...
Options:
Admission event, group name change, Scope recheck timer expires
Policy recheck timer expires, admission event, SC event change
Admission event, policy categorization, SC event change
Policy categorization, admission event, action schedule activation
Policy recheck timer expires, group name change, SC event change
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, policies recheck when the following conditions are met: Policy recheck timer expires, admission event, or SC event change.
Policy Recheck Conditions:
According to the Main Rule Advanced Options documentation:
"By default, both matched endpoints and unmatched endpoints are rechecked every eight hours, and on any admission event."
Additionally, according to the documentation:
"You can also configure several recheck settings to work simultaneously. For example, when a host IP address changes every five hours, recheck settings can be configured for:
Policy recheck timer expires - Default 8 hours
Admission events - Triggers like DHCP request, IP address change
SC (SecureConnector) event change - When SecureConnector status changes"
Three Main Policy Recheck Triggers:
According to the documentation:
Policy Recheck Timer Expires
Default: Every 8 hours
Can be customized (1 hour to infinite)
Applies to all endpoints matching or not matching the policy
Admission Event
DHCP Request
IP Address Change
Switch Port Change
Authentication event
VPN user connection
Immediate recheck when triggered
SC Event Change
SecureConnector deployed or removed
SecureConnector status changes (online/offline)
SecureConnector version changes
Why Other Options Are Incorrect:
A. Admission event, group name change, Scope recheck timer expires - Group name change is NOT a recheck trigger
C. Admission event, policy categorization, SC event change - Policy categorization is NOT a recheck trigger
D. Policy categorization, admission event, action schedule activation - Neither policy categorization nor action schedule activation triggers rechecks
E. Policy recheck timer expires, group name change, SC event change - Group name change does NOT trigger policy rechecks
Recheck Configuration:
According to the documentation:
"You can configure under what conditions to perform a recheck. By default, endpoints are rechecked every eight hours, and on any admission event. To define the recheck policy, you can configure:
Custom recheck interval (instead of 8 hours)
Which admission events trigger rechecks
Whether SecureConnector events trigger rechecks"
Referenced Documentation:
Main Rule Advanced Options
Forescout eyeSight policy main rule advanced options
When Are Policies Run - Policy Recheck section
Which of the following is a switch plugin property that can be used to identify endpoint connection location?
Options:
Switch Location
Switch Port Alias
Switch IP/FQDN and Port Name
Switch Port Action
Wireless SSID
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and the Switch Properties documentation, the Switch IP/FQDN and Port Name property is used to identify an endpoint's connection location. The documentation explicitly states:
"The Switch IP/FQDN and Port Name property contains either the IP address or the fully qualified domain name of the switch and the port name (the physical connection point on that switch) to which the endpoint is connected."
Switch IP/FQDN and Port Name Property:
This property is fundamental for identifying where an endpoint is physically connected on the network. According to the documentation:
Purpose: Provides the exact physical location of an endpoint on the network by identifying:
Switch IP Address or FQDN - Which switch the endpoint is connected to
Port Name - Which specific port on that switch the endpoint uses
Example: A property value might look like:
10.10.1.50:Port Fa0/15 (IP address and port name)
core-switch.example.com:GigabitEthernet0/1/1 (FQDN and port name)
Use Cases for Location Identification:
According to the Switch Plugin Configuration Guide:
Physical Topology Mapping - Administrators can see exactly where each endpoint connects to the network
Port-Based Policies - Create policies that apply actions based on specific switch ports
Troubleshooting - Quickly locate endpoints by their switch port connection
Inventory Tracking - Maintain accurate records of device locations and connections
Switch Location vs. Switch IP/FQDN and Port Name:
According to the documentation:
Property
Purpose
Switch Location
The switch location based on the switch MIB (Management Information Base) - geographic location of the switch itself
Switch IP/FQDN and Port Name
The specific switch and port where an endpoint is connected - physical connection point
Switch Port Alias
The alias/description of the port (if configured on the switch)
The key difference: Switch Location identifies where the switch itself is located, while Switch IP/FQDN and Port Name identifies the specific connection point where the endpoint is attached.
Why Other Options Are Incorrect:
A. Switch Location - Identifies the location of the switch device itself (from MIB), not the endpoint's connection point
B. Switch Port Alias - This is an alternate name for a port (like "Conference Room Port"), not the connection location information
D. Switch Port Action - This indicates what action was performed on a port, not where the endpoint is located
E. Wireless SSID - This is a Wireless Plugin property, not a Switch Plugin property; identifies wireless network name, not switch connection location
Switch Properties for Endpoint Location:
According to the complete Switch Properties documentation:
The Switch Plugin provides these location-related properties:
Switch IP/FQDN - The switch to which the endpoint connects
Switch IP/FQDN and Port Name - The complete location (switch and port)
Switch Port Name - The specific port on the switch
Switch Port Alias - Alternate port name
Only Switch IP/FQDN and Port Name provides the complete endpoint connection location information in a single property.
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Properties documentation
Viewing Switch Information in the All Hosts Pane
About the Switch Plugin
Which of the following is true regarding how CounterACT restores a quarantined endpoint to its original production VLAN after the "Assign to VLAN Action" is removed?
Options:
This happens automatically because CounterACT compares the running and startup configs
This happens automatically as long as configuration changes to the switchport access VLAN of affected ports are not changed in the switch running config
This happens automatically as long as no configuration changes to the switch are made to the running config
This happens automatically as long as configuration changes to the switchport access VLAN of affected ports are not saved in the startup config
A policy is required to ensure this happens correctly.
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and 8.14.2, CounterACT restores a quarantined endpoint to its original production VLAN automatically as long as configuration changes to the switchport access VLAN of affected ports are not saved in the startup config.
VLAN Restoration Mechanism:
According to the Switch Plugin documentation:
When the "Assign to VLAN" action is removed or expires, CounterACT can restore the original VLAN configuration by comparing the running configuration with the startup configuration on the switch.
The Key Requirement:
According to the documentation:
The restoration process works as follows:
Assign to VLAN Action Applied - Endpoint is moved to quarantine VLAN (switch running config is updated)
Assign to VLAN Action Removed - CounterACT wants to restore the original VLAN
Running vs. Startup Config Comparison - CounterACT compares running config to startup config
Restoration - The port is returned to its original VLAN as defined in the startup configuration
Critical Condition:
According to the documentation:
"This happens automatically as long as configuration changes to the switchport access VLAN of affected ports are not saved in the startup config"
This is critical because:
If manual changes are saved to the startup config, CounterACT cannot determine what the "original" VLAN should be
The startup config must remain unchanged for CounterACT to restore the correct VLAN
The running config changes are temporary and revert to startup config values
Why Other Options Are Incorrect:
A. CounterACT compares the running and startup configs - While true that comparison occurs, the condition is about whether changes are saved to startup, not just comparing
B. Configuration changes...are not changed in the switch running config - Too broad; there can be other running config changes; the specific requirement is about VLAN configuration being saved to startup
C. No configuration changes to the switch are made to the running config - Too strict; other changes can be made; only VLAN switchport access configuration matters
E. A policy is required - Incorrect; this is automatic behavior, not policy-dependent
Default VLAN Feature:
According to the Switch Plugin Configuration Guide:
The Default VLAN feature ensures that ports are automatically assigned to a default VLAN unless specifically configured otherwise. When the "Assign to VLAN" action is removed, the port returns to the default VLAN (as defined in the startup configuration).
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Plugin Configuration Guide v8.14.2
Global Configuration Options for the Switch Plugin
What should be done after the Managed Windows devices are sent to a policy to determine the Windows 10 patch delivery optimization setting?
Options:
Push out the proper DWORD setting via GPO
Non Windows 10 devices must be called out in sub-rules since they will not have the relevant DWORD
Manageable Windows devices are not required by this policy
Non Windows 10 devices must be called out in sub-rules so that the relevant DWORD value may be changed
Write sub-rules to check for each of the DWORD values used in patch delivery optimization
Answer:
EExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
After managed Windows devices are sent to a policy to determine the Windows 10 patch delivery optimization setting, the best practice is to write sub-rules to check for each of the DWORD values used in patch delivery optimization.
Windows 10 Patch Delivery Optimization DWORD Values:
Windows 10 patch delivery optimization is configured through DWORD registry settings in the following registry path:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DeliveryOptimization
The primary DWORD value is DODownloadMode, which supports the following values:
0 = HTTP only, no peering
1 = HTTP blended with peering behind the same NAT (default)
2 = HTTP blended with peering across a private group
3 = HTTP blended with Internet peering
63 = HTTP only, no peering, no use of DO cloud service
64 = Bypass mode (deprecated in Windows 11)
Why Sub-Rules Are Required:
When implementing a policy to manage Windows 10 patch delivery optimization settings, administrators must create sub-rules for each possible DWORD configuration value because:
Different Organizational Requirements - Different departments or network segments may require different delivery optimization modes (e.g., value 1 for some devices, value 0 for others)
Compliance Checking - Each sub-rule verifies whether a device has the correct DWORD value configured according to organizational policy
Enforcement Actions - Once each sub-rule identifies a specific DWORD value, appropriate remediation actions can be applied (e.g., GPO deployment, messaging, notifications)
Granular Control - Sub-rules allow for precise identification of devices with non-compliant delivery optimization settings
Implementation Workflow:
Device is scanned and identified as Windows 10 managed device
Policy queries the DODownloadMode DWORD registry value
Multiple sub-rules evaluate the current DWORD value:
Sub-rule for value "0" (HTTP only)
Sub-rule for value "1" (Peering behind NAT)
Sub-rule for value "2" (Peering across private group)
Sub-rule for value "3" (Internet peering)
Sub-rule for value "63" (No peering, no cloud)
Matching sub-rule triggers appropriate policy actions
Why Other Options Are Incorrect:
A. Push out the proper DWORD setting via GPO - This is what you do AFTER checking via sub-rules, not what you do after sending devices to the policy
B. Non Windows 10 devices must be called out in sub-rules since they will not have the relevant DWORD - While non-Windows 10 devices should be excluded, the answer doesn't address the core requirement of checking each DWORD value
C. Manageable Windows devices are not required by this policy - This is incorrect; managed Windows devices are the focus of this policy
D. Non Windows 10 devices must be called out in sub-rules so that the relevant DWORD value may be changed - This misses the point; you check the DWORD values first, not change them in sub-rules
Referenced Documentation:
Microsoft Delivery Optimization Reference - Windows 10 Deployment
Forescout Administration Guide - Defining Policy Sub-Rules
How to use Group Policy to configure Windows Update Delivery Optimization
Why would the patch delivery optimization mechanism used for Windows 10 updates be a potential security concern?
Options:
It can be configured to use a peer-to-peer file sharing protocol
CounterACT cannot initiate Windows updates for Windows 10 devices
It uses a peer-to-peer file sharing protocol by default
The registry DWORD controlling this behavior cannot be changed
It always uses a peer-to-peer file sharing protocol
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Windows Update Delivery Optimization documentation and security analysis, the potential security concern with patch delivery optimization for Windows 10 updates is that it CAN BE CONFIGURED to use a peer-to-peer file sharing protocol. While the feature includes security mechanisms like cryptographic signing, the capability to enable P2P sharing does create potential security concerns depending on the configuration.
Windows Update Delivery Optimization Overview:
According to the Windows Delivery Optimization documentation:
"Windows Update Delivery Optimization is a feature in Microsoft's Windows designed to improve the efficiency of downloading and distributing updates. Instead of each device independently downloading updates from Microsoft's servers, Update Delivery Optimization allows devices to share update files with each other, either within a local network or over the internet. This peer-to-peer (p2p) approach reduces bandwidth consumption and accelerates the update process."
Configuration Flexibility:
According to the documentation:
The P2P feature is configurable, not mandated:
Default Setting - By default, Delivery Optimization is enabled for local network sharing
Configurable Options:
PCs on my local network only (safer)
PCs on my local network and the internet (broader sharing, higher risk)
Disabled entirely
Security Concerns Related to P2P Configuration:
According to the security analysis:
When P2P is enabled, potential concerns include:
Network Isolation Risks - In firewalled or segmented networks, P2P discovery can expose endpoints
Bandwidth Consumption - Improperly configured P2P can saturate network resources
Peer Discovery Vulnerabilities - Devices must discover each other, potentially exposing endpoints
Internet-based Sharing Risks - When "internet peers" are enabled, updates are shared across the internet
Privacy Implications - Devices communicating for update sharing may leak information
Cryptographic Protection Does NOT Eliminate Configuration Risk:
According to the documentation:
"While Update Delivery Optimization ensures that all update files are cryptographically signed and verified before installation, some organizations may still be concerned about allowing peer-to-peer data sharing."
While the updates themselves are protected, the act of enabling P2P configuration creates the security concern.
Why Other Options Are Incorrect:
B. CounterACT cannot initiate Windows updates for Windows 10 - Incorrect; CounterACT can initiate Windows updates; this is not the security concern
C. It uses peer-to-peer by default - Incorrect; while enabled by default for local networks, internet P2P sharing requires explicit configuration
D. The registry DWORD cannot be changed - Incorrect; the DO modes registry value (DODownloadMode) CAN be changed via GPO or registry
E. It always uses peer-to-peer - Incorrect; P2P is configurable, not mandatory; organizations can disable it entirely
Registry DWORD Configuration Options:
According to the Windows documentation:
The DODownloadMode DWORD value can be configured to:
0 = HTTP only, no peering (addresses security concern)
1 = HTTP blended with local peering (moderate risk)
3 = HTTP blended with internet peering (higher risk - the security concern)
99 = Simple download mode
This demonstrates that P2P can be configured, which is the security concern mentioned in the question.
Referenced Documentation:
What is Windows Update Delivery Optimization - Scalefusion Blog
Windows Delivery Optimization: Risks & Challenges - LinkedIn Article
Introduction to Windows Update Delivery Optimization - Sygnia Analysis
What should you do first when preparing for an upgrade to a new CounterACT version?
Options:
Upgrade the members first before upgrading the EM.
Upgrading an appliance is done through Options/Modules.
From the appliance CLI, fstool upgrade /tmp/counteract-v8.0.1.fsp
Consult the CounterACT® Release Notes for the appropriate version
Upgrade only the modules compatible with the version you are installing.
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Upgrade Guides for multiple versions, the first thing you should do when preparing for an upgrade to a new CounterACT version is consult the CounterACT Release Notes for the appropriate version.
Release Notes as First Step:
According to the official documentation:
"Review the Forescout Release Notes for important information before performing any upgrade."
The documentation emphasizes this as a critical first step before any other upgrade activities.
What Release Notes Contain:
According to the upgrade guidance:
The Release Notes provide essential information including:
Upgrade Paths - Which versions you can upgrade from and to
Pre-Upgrade Requirements - System requirements and prerequisites
End-of-Life Products - Products that must be uninstalled before upgrade
Non-Supported Products - Products not compatible with the new version
Module/Plugin Dependencies - Version compatibility requirements
Known Issues - Potential problems and workarounds
Upgrade Procedures - Step-by-step instructions
Rollback Information - How to revert if needed
Critical Pre-Upgrade Information:
According to the Release Notes guidance:
"The upgrade process does not continue when end-of-life products are detected."
Release Notes list:
End-of-Life (EOL) Products - Must be uninstalled before upgrade
Non-Supported Products - Must be uninstalled before upgrade
Plugin Version Compatibility - Which plugin versions work with the new Forescout version
Upgrade Order vs. Release Notes Review:
According to the documentation:
While the order of upgrade (EM first, then Appliances) is important, consulting Release Notes comes FIRST because it determines what needs to be done before any upgrade attempts.
The Release Notes tell you:
Whether you can upgrade at all
What must be uninstalled
System requirements
Compatibility information
Only AFTER reviewing Release Notes do you proceed with the actual upgrade sequence.
Why Other Options Are Incorrect:
A. Upgrade the members first before upgrading the EM - This is the OPPOSITE of correct order; EM (Enterprise Manager) should be upgraded first
B. Upgrading an appliance is done through Options/Modules - This is not the upgrade path; upgrades are done through Tools > Options > CounterACT Devices
C. From the appliance CLI, fstool upgrade /tmp/counteract-v8.0.1.fsp - This is ONE possible upgrade method, but not the first step; downloading and reviewing Release Notes comes first
E. Upgrade only the modules compatible with the version you are installing - This is a consideration found IN the Release Notes, not the first step itself
Correct Upgrade Sequence:
According to the comprehensive upgrade documentation:
text
1. FIRST: Review Release Notes (determine what's needed)
2. Second: Check system requirements
3. Third: Uninstall EOL/non-supported products
4. Fourth: Back up Enterprise Manager and Appliances
5. Fifth: Upgrade Enterprise Manager
6. Sixth: Upgrade Appliances
Referenced Documentation:
Before You Upgrade the Forescout Platform - v8.3
Before You Upgrade the Forescout Platform - v9.1.2
Forescout 8.1.3 Release Notes
Installation Guide v8.0 - Upgrade section
When configuring policies, which of the following statements is true regarding the indicated property?
Select one:
Options:
Irresolvable hosts would match the condition
Negates the criteria inside the property
Negates the criteria outside the property
Modifies the irresolvable condition to TRUE
Negates the "evaluate irresolvable as" setting
Answer:
BExplanation:
Based on the policy condition image provided showing the NOT checkbox on "Windows Antivirus Update Data", the correct statement is that the NOT operator negates the criteria inside the property.
Understanding the NOT Operator:
When the NOT checkbox is selected on a policy condition property, it performs a logical negation (NOT operation) on the criteria evaluation. According to the Forescout Administration Guide:
The NOT operator creates an inverted evaluation:
Without NOT: "Windows Antivirus Update Data = [value]"
Result: Matches endpoints where the property equals the specified value
With NOT (as shown in the image): "NOT (Windows Antivirus Update Data = [value])"
Result: Matches endpoints where the property does NOT equal the specified value
How the NOT Operator Works:
The NOT operator negates the criteria inside the property:
Criteria Evaluation - The property condition is evaluated normally first
Negation Applied - The result is then inverted (TRUE becomes FALSE, FALSE becomes TRUE)
Final Result - The endpoint matches only if the negated condition is true
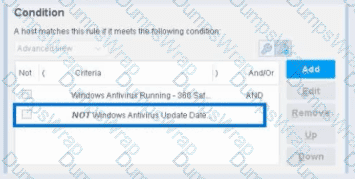
Example from the Image:
The image shows:
First criterion: "Windows Antivirus Running - 360 Sat" (AND)
Second criterion: "NOT Windows Antivirus Update Data" (checked)
This means:
The endpoint must have Windows Antivirus Running = True (360 Sat)
AND the endpoint must NOT have the Windows Antivirus Update Data property value (whatever was specified)
The NOT negates the criteria inside the property condition
NOT vs. "Evaluate Irresolvable As":
According to the documentation, these are independent settings:
Setting
Purpose
NOT Checkbox
Negates the criteria evaluation (inverts the match logic)
Evaluate Irresolvable As
Defines how to handle unresolvable properties (when data cannot be determined)
The NOT operator works inside the property evaluation, while "Evaluate Irresolvable As" is a separate setting that determines behavior when a property cannot be resolved.
Why Other Options Are Incorrect:
A. Irresolvable hosts would match the condition - The NOT operator doesn't specifically affect how irresolvable properties are handled
C. Negates the criteria outside the property - The NOT operator is internal to the property; it negates the criteria inside, not outside
D. Modifies the irresolvable condition to TRUE - The NOT operator doesn't modify the "Evaluate Irresolvable As" setting; these are independent
E. Negates the "evaluate irresolvable as" setting - The NOT operator and "Evaluate Irresolvable As" are separate; NOT doesn't affect or negate that setting
Policy Condition Structure:
According to the Forescout Administration Guide:
A policy condition is structured as:
text
[NOT] [Property Name] [Operator] [Value]
Where:
[NOT] - Optional negation operator (what the checkbox controls)
[Property Name] - The property being evaluated
[Operator] - The comparison operator (equals, contains, greater than, etc.)
[Value] - The value to match against
When NOT is checked, it negates the entire criteria evaluation inside that property condition.
Referenced Documentation:
Forescout Administration Guide v8.3
Forescout Administration Guide v8.4
Define policy scope documentation
Forescout eyeSight policy sub-rule advanced options
When an admission event is seen, how are main rules and sub-rules processed?
Options:
Main rules process concurrently, sub-rules process sequentially.
Main rules process in parallel, sub-rules process concurrently.
Main rules process concurrently, sub-rules process in parallel.
Main rules process sequentially, sub-rules process concurrently.
Main rules process sequentially, sub-rules process in parallel.
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Policy Processing, when an admission event occurs, "Main rules process concurrently, sub-rules process sequentially".
Policy Processing Flow:
According to the Main Rule Advanced Options documentation:
When an admission event triggers policy evaluation:
Main Rules - Process concurrently/in parallel
All main rules are evaluated simultaneously
No ordering or sequencing
Each main rule evaluates independently
Sub-Rules - Process sequentially/in order
Sub-rules within each main rule execute one after another
First match wins - stops evaluating subsequent sub-rules
Order matters for sub-rule execution
Main Rule Concurrent Processing:
According to the documentation:
"Main rules are evaluated independently and concurrently. Multiple main rules can be processed simultaneously for the same endpoint."
Sub-Rule Sequential Processing:
According to the Defining Policy Sub-Rules documentation:
"Sub-rules are evaluated sequentially in the order defined. When an endpoint matches a sub-rule, that sub-rule's actions are taken and subsequent sub-rules are not evaluated."
Example Processing:
When admission event triggers:
text
CONCURRENT (Main Rules):
├─ Main Rule 1 evaluation → Sub-rule processing (sequential)
├─ Main Rule 2 evaluation → Sub-rule processing (sequential)
└─ Main Rule 3 evaluation → Sub-rule processing (sequential)
(All main rules evaluate at the same time)
Why Other Options Are Incorrect:
B. Parallel/Concurrently - "Concurrent" and "parallel" mean the same thing; sub-rules don't process concurrently
C. Concurrent/Parallel - Sub-rules don't process in parallel; they're sequential
D. Sequential/Concurrently - Main rules don't process sequentially; they're concurrent
E. Sequential/Parallel - Main rules don't process sequentially; they're concurrent
Referenced Documentation:
Main Rule Advanced Options
Defining Policy Sub-Rules
When configuring policies, which of the following statements is true regarding this image?
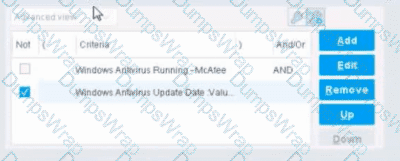
Options:
The NOT checkbox means the "Evaluate Irresolvable as" should be set to True
The external NOT does not change the meaning of "evaluate irresolvable as"
Has no effect on irresolvable hosts
Negates the criteria inside the property
The NOT checkbox means the "Evaluate Irresolvable as" should be set to False
Answer:
DExplanation:
The NOT checkbox negates the criteria inside the property. According to the Forescout Administration Guide, when the NOT checkbox is selected on a policy condition criteria, it reverses the logic of that specific criterion evaluation.
Understanding the NOT Operator in Policy Conditions:
In Forescout policy configuration, the NOT operator is a Boolean logic operator that inverts the result of the property evaluation. When you select the NOT checkbox:
Logical Inversion - The condition is evaluated normally, and then the result is inverted
Criteria Negation - If a criteria would normally match an endpoint, selecting NOT causes it NOT to match
Property-Level Operation - The NOT operator applies specifically to that individual property/criterion, not to the entire rule
Example of NOT Logic:
Without NOT:
Condition: "Windows Antivirus Running = True"
Result: Matches endpoints that HAVE antivirus running
With NOT:
Condition: "NOT (Windows Antivirus Running = True)"
Result: Matches endpoints that DO NOT have antivirus running
NOT vs. "Evaluate Irresolvable As":
According to the documentation, the NOT operator and "Evaluate Irresolvable As" are independent settings:
NOT operator - Negates/inverts the criteria evaluation itself
"Evaluate Irresolvable As" - Defines what happens when a property CANNOT be resolved (is irresolvable)
These serve different purposes:
NOT determines what value to match
Evaluate Irresolvable As determines how to handle unresolvable properties
Handling Irresolvable Criteria:
According to the administration guide documentation:
"If you do not select the Evaluate irresolvable criteria as option, the criteria is handled as irresolvable and the endpoint does not undergo further analysis."
The "Evaluate Irresolvable As" checkbox allows you to define whether an irresolvable property should be treated as True or False when the property value cannot be determined. This is independent of the NOT checkbox.
Why Other Options Are Incorrect:
A. The NOT checkbox means the "Evaluate Irresolvable as" should be set to True - Incorrect; NOT and Evaluate Irresolvable As are independent settings
B. The external NOT does not change the meaning of "evaluate irresolvable as" - While technically true that NOT doesn't change the Evaluate Irresolvable setting, the answer doesn't explain what NOT actually does
C. Has no effect on irresolvable hosts - Incorrect; NOT negates the criterion logic regardless of whether it's resolvable
E. The NOT checkbox means the "Evaluate Irresolvable as" should be set to False - Incorrect; NOT and Evaluate Irresolvable As are independent
Policy Condition Structure:
According to the documentation, a policy condition consists of:
Property criteria combined with Boolean logic operators
Individual criterion settings including NOT operator
Irresolvable handling options that are separate from the NOT operator
Referenced Documentation:
Forescout Administration Guide - Define policy scope
Forescout eyeSight policy sub-rule advanced options
Handling Irresolvable Criteria section
Working with Policy Conditions
Which of the following statements is true regarding Layer-2 channel?
Options:
Recommended when there are a large number of VLANs
Response interface is a VLAN trunk
Monitor interface is a trunk
Utilizes two interfaces
Appliance monitor interface must be connected to an access layer switch
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Installation Guide and Working with Appliance Channel Assignments documentation, a Layer-2 channel "Utilizes two interfaces" - one monitor interface and one response interface.
Layer-2 Channel Structure:
According to the documentation:
"A channel defines a pair of interfaces used by the Appliance to protect your network. In general, one interface monitors traffic going through the network (the monitor interface), and the other responds to traffic on the network (the response interface)."
Two Interface Components:
According to the Installation Guide:
Monitor Interface:
Monitors and tracks network traffic
Traffic is mirrored from switch ports
No IP address required
Can be any available interface
Response Interface:
Responds to monitored traffic
Used for policy actions and protections
Configuration depends on VLAN tagging
Can be same VLAN or trunk configuration
Layer-2 vs. Layer-3 Channel:
According to the documentation:
Layer-2 Channel - Two interfaces (monitor and response)
Layer-3 Channel - Uses IP layer for response
Why Other Options Are Incorrect:
A. Recommended for large number of VLANs - Actually, Layer-2 channels with VLAN tagging are recommended for multiple VLANs, but this doesn't define what a Layer-2 channel is
B. Response interface is a VLAN trunk - While response interface CAN be a trunk for multiple VLANs, it's not required for all configurations
C. Monitor interface is a trunk - The monitor interface receives mirrored traffic; trunk configuration depends on VLAN setup
E. Must be connected to access layer switch - The appliance can connect to various switch types; not specifically limited to access layer
Referenced Documentation:
Working with Appliance Channel Assignments
Quick Installation Guide v8.4
Quick Installation Guide v8.2
Add Channels
Monitor Interface
Set up the Forescout Platform Network
Which of the following switch actions cannot both be used concurrently on the same switch?
Options:
Access Port ACL & Switch Block
Switch Block & Assign to VLAN
Endpoint Address ACL & Assign to VLAN
Access Port ACL & Endpoint Address ACL
Access Port ACL & Assign to VLAN
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide, Access Port ACL and Endpoint Address ACL cannot both be used concurrently on the same endpoint. These two actions are mutually exclusive because they both apply ACL rules to control traffic, but through different mechanisms, and attempting to apply both simultaneously creates a conflict.
Switch Restrict Actions Overview:
The Forescout Switch Plugin provides several restrict actions that can be applied to endpoints:
Access Port ACL - Applies an operator-defined ACL to the access port of an endpoint
Endpoint Address ACL - Applies an operator-defined ACL based on the endpoint's address (MAC or IP)
Assign to VLAN - Assigns the endpoint to a specific VLAN
Switch Block - Completely isolates endpoints by turning off their switch port
Action Compatibility Rules:
According to the Switch Plugin Configuration Guide:
Endpoint Address ACL vs Access Port ACL - These CANNOT be used together on the same endpoint because:
Both actions modify switch filtering rules
Both actions can conflict when applied simultaneously
The Switch Plugin cannot determine priority between conflicting ACL configurations
Applying both would create ambiguous filtering logic on the switch
Actions That CAN Be Used Together:
Access Port ACL + Assign to VLAN -✓Can be used concurrently
Endpoint Address ACL + Assign to VLAN -✓Can be used concurrently
Switch Block + Assign to VLAN - This is semantically redundant (blocking takes precedence) but is allowed
Access Port ACL + Switch Block -✓Can be used concurrently (though Block takes precedence)
Why Other Options Are Incorrect:
A. Access Port ACL & Switch Block - These CAN be used concurrently; Switch Block would take precedence
B. Switch Block & Assign to VLAN - These CAN be used concurrently (though redundant)
C. Endpoint Address ACL & Assign to VLAN - These CAN be used concurrently
E. Access Port ACL & Assign to VLAN - These CAN be used concurrently; they work on different aspects of port management
ACL Action Definition:
According to the documentation:
Access Port ACL - "Use the Access Port ACL action to define an ACL that addresses one or more than one access control scenario, which is then applied to an endpoint's switch port"
Endpoint Address ACL - "Use the Endpoint Address ACL action to apply an operator-defined ACL, addressing one or more than one access control scenario, which is applied to an endpoint's address"
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Plugin Configuration Guide v8.14.2
Switch Restrict Actions documentation
Which field in the User Directory plugin should be configured for Active Directory subdomains?
Options:
Replicas
Address
Parent Groups
Domain Aliases
DNS Detection
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide - Microsoft Active Directory Server Settings, the field that should be configured for Active Directory subdomains is "Domain Aliases".
Domain Aliases for Subdomains:
According to the Microsoft Active Directory Server Settings documentation:
"Configure the following additional server settings in the Directory and Additional Domain Aliases sections: Domain Aliases - Configure additional domain names that users can use to log in, such as subdomains."
Purpose of Domain Aliases:
According to the documentation:
Domain Aliases are used to specify:
Subdomains - Alternative domain names like subdomain.company.com
Alternative Domain Names - Other domain name variations
User Login Options - Additional domains users can use to authenticate
Alias Resolution - Maps aliases to the primary domain
Example Configuration:
For an organization with the primary domain company.com and subdomain accounts.company.com:
Domain Field - Set to: company.com
Domain Aliases Field - Add: accounts.company.com
This allows users from either domain to authenticate successfully.
Why Other Options Are Incorrect:
A. Replicas - Replicas configure redundant User Directory servers, not subdomains
B. Address - Address field specifies the server IP/FQDN, not domain aliases
C. Parent Groups - Parent Groups relate to group hierarchy, not domain subdomains
E. DNS Detection - DNS Detection is not a User Directory configuration field
Additional Domain Configuration:
According to the documentation:
text
Primary Configuration:
├─ Domain: company.com
├─ Domain Aliases: accounts.company.com
│ services.company.com
│ mail.company.com
└─ Port: 636 (default)
Referenced Documentation:
Microsoft Active Directory Server Settings
Define User Directory Servers - Domain Aliases section
Which of the following User Directory server settings is necessary to enable guest approval by sponsors?
Options:
Policy to control
Guest Tags
Sponsor Group
Guest password policy
Authentication Server
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
The Sponsor Group is the necessary User Directory server setting required to enable guest approval by sponsors. According to the Forescout User Directory Plugin Configuration Guide and Guest Management Portal documentation, Sponsor Groups must be created and configured to define the corporate employees (sponsors) who are authorized to approve or decline guest network access requests.
Sponsor Group Configuration:
In the Guest Management pane, the Sponsors tab is used to define the corporate employees who are authorized to log into the Guest Management Portal to approve network access requests from guests. These employees are assigned to specific Sponsor Groups, which control which sponsors can approve guest access requests.
How Sponsor Groups Enable Guest Approval:
Sponsor Definition - Corporate employees must be designated as sponsors and assigned to a Sponsor Group
Approval Authority - Sponsors in assigned groups can approve or decline guest network access requests
Authentication - When "Enable sponsor approval without authentication via emailed link" is selected, sponsors in the designated group can approve guests based on email link authorization
Guest Registration - Guest registration options connect Sponsor Groups to the guest approval workflow
Why Other Options Are Incorrect:
A. Policy to control - While policies are used for guest control, they do not define which sponsors can approve guests
B. Guest Tags - Guest Tags are used to classify and organize guest accounts, not to enable sponsor approval
D. Guest password policy - This setting controls password requirements for guests, not sponsor approval authority
E. Authentication Server - Authentication servers verify credentials but do not establish sponsor approval groups
Referenced Documentation:
Forescout User Directory Plugin Configuration Guide - Create Sponsors section
Guest Management Portal - Sponsor Configuration documentation
"Create sponsors" - Forescout Administration Guide section
Which of the following is true when setting up an Enterprise Manager as a High Availability Pair?
Options:
If HA reboots, this is an indication of a problem.
Set up HA on the Secondary node first.
Connect devices to the network and to each other.
HA needs to be manually configured on the secondary appliance in order to sync correctly.
HA requires a license.
Answer:
EExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Resiliency Solutions User Guide and the Forescout Platform Installation Guide, High Availability (HA) requires a license. The documentation explicitly states:
"If your deployment is using Centralized Licensing Mode, you must acquire a valid ForeScout CounterACT Resiliency license. The Resiliency license supports: High Availability Pairing for Enterprise Manager is supported by the Forescout CounterACT See License."
High Availability Licensing Requirements:
According to the official documentation:
Per-Appliance Licensing Mode:
"The demo license for your High Availability system is valid for 30 days. You must install a permanent license before this period expires."
Centralized Licensing Mode:
"If your deployment is using Centralized Licensing Mode, you must acquire a valid ForeScout CounterACT Resiliency license for Appliances, or a CounterACT See License for Enterprise Manager High Availability Pairing."
License Usage Considerations:
According to the documentation:
"You should use the IP address of the High Availability pair when requesting a High Availability license"
"If a license is only issued to the Active node in a High Availability pair, the system may not operate after failover to the Standby node"
"Both nodes must be up when requesting a license"
Why Other Options Are Incorrect:
A. If HA reboots, this is an indication of a problem - According to the documentation, reboots can occur during the setup process: "Following the second reboot in the high availability setup, allow time for data synchronization" - this is normal, not an indication of a problem
B. Set up HA on the Secondary node first - Incorrect order. According to the documentation, "Before you begin setting up the Secondary node Forescout Platform device, verify that the Primary node Forescout Platform device is powered on" - the Primary node must be set up first
C. Connect devices to the network and to each other - While devices must be connected, this is a general infrastructure requirement, not specific to HA setup. The more specific requirement is licensing
D. HA needs to be manually configured on the secondary appliance in order to sync correctly - According to the documentation, the Secondary node configuration uses a setup process that is distinct from the Primary node: "When setting up the Secondary node device, use the same sync interfaces and netmask settings used in the Primary node device" - this is guided setup, not manual configuration for sync
High Availability Setup Process:
According to the documentation:
Set up Primary Node - "Select High Availability mode: 1) Standard Installation 2) High Availability – Primary Node"
Set up Secondary Node - "Set up a device as the secondary node" (secondary node connects to primary automatically)
Licensing - "You must install a permanent license before this period expires"
Referenced Documentation:
Forescout Resiliency Solutions User Guide (v8.0)
Forescout Installation Guide v8.1.x
Forescout Resiliency and Recovery Solutions User Guide v8.1
Set up and configure a device as the primary node
Set up a device as the secondary node
Which of the following is a User Directory feature?
Options:
Guest authentication
Dashboard
Radius authorization
Query Switches
Assets portal
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
Guest authentication is a User Directory feature. According to the Forescout Authentication Module Overview Guide and the User Directory Plugin Configuration Guide, the User Directory Plugin enables guest authentication and management through configured directory servers.
User Directory Plugin Features:
The User Directory Plugin (version 6.4+) provides the following core features:
Endpoint User Resolution - Resolves endpoint user details by querying directory servers
User Authentication - Performs user authentication via configured internal and external directory servers (Active Directory, LDAP, etc.)
Guest Authentication - Enables authentication and registration of guest users on the network
Guest Sponsorship - Allows corporate employee sponsors to approve guest network access
Guest Management Portal - Provides functionality for managing guest hosts and guest portal access
Directory Server Integration - Integrates with enterprise directory servers for credential validation
Guest Management Capabilities:
The User Directory Plugin specifically enables:
Guest user registration and authentication
Guest approval workflows through sponsor groups
Guest session management
Guest password policies
Guest tag management for categorization
Why Other Options Are Incorrect:
B. Dashboard - This is a general console feature, not specific to the User Directory plugin
C. Radius authorization - This is the function of the RADIUS plugin, not the User Directory plugin (though they work together in the Authentication Module)
D. Query Switches - This is a function of the Switch plugin, not the User Directory plugin
E. Assets portal - This is a general Forescout platform feature, not specific to the User Directory plugin
Authentication Module Structure:
According to the documentation, the Authentication Module consists of two plugins:
RADIUS Plugin - Handles 802.1X authentication, authorization, and accounting
User Directory Plugin - Handles user resolution, authentication, and guest management
These work together but have distinct responsibilities. The User Directory Plugin specifically handles guest authentication among its feature set.
Referenced Documentation:
Forescout Authentication Module Overview Guide Version 1.1
About the User Directory Plugin documentation
User Directory Plugin Server and Guest Management Configuration Guide
When using the discover properties OS, Function, Network Function and NIC Vendor and Module, certain hosts may not be correctly profiled. What else may be used to provide additional possible details to assist in correctly profiling the host?
Options:
Monitoring traffic
Packet engine
Advanced Classification
NMAP Scanning
Function
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and List of Properties by Category documentation, NMAP Scanning provides additional discovery details that can assist in correctly profiling hosts when the standard discover properties (OS, Function, Network Function, NIC Vendor) do not provide sufficient information.
Standard Discovery Properties:
According to the Device Profile Library and classification documentation:
The standard discovery properties include:
OS - Operating System classification
Function - Network function (printer, workstation, server, etc.)
Network Function - Specific network device role
NIC Vendor - MAC address vendor information
These properties provide basic device identification but may not be sufficient for complete profiling.
NMAP Scanning for Enhanced Profiling:
According to the Advanced Classification Properties documentation:
"NMAP Scanning - Indicates the service and version information, as determined by Nmap. Due to the activation of Nmap, this..."
NMAP scanning provides advanced discovery including:
Service Banner Information - Service name and version (e.g., Apache 2.4, OpenSSH 7.6)
Open Port Detection - Identifies which ports are open and responding
Service Fingerprinting - Determines exact service versions through banner grabbing
Application Detection - Identifies specific applications and their versions
Why NMAP Provides Additional Details:
According to the documentation:
When standard properties (OS, Function, NIC Vendor) are insufficient for profiling:
NMAP banner scanning uses active probing of open ports
Returns service version information through banner grabbing
Enables more precise device classification
Helps identify specific applications running on endpoints
Example of NMAP Enhancement:
According to the documentation:
Standard properties might show: "Windows 7, Workstation, Dell NIC"
NMAP scanning additionally shows:
Open ports: 80, 135, 445, 3389
Services: Apache 2.4.41, MS RPC, SMB 3.0
This enables more precise classification (e.g., "Development workstation running web services")
Why Other Options Are Incorrect:
A. Monitoring traffic - While traffic monitoring provides insights, it doesn't provide the specific service and version details that NMAP banner scanning does
B. Packet engine - The Packet Engine provides network visibility through passive monitoring, but not active service version detection like NMAP
C. Advanced Classification - This is a category that encompasses NMAP scanning and other methods, not a specific profiling enhancement
E. Function - This is already listed as one of the discover properties that may be insufficient; it's not an additional tool for profiling
NMAP Configuration:
According to the HPS Inspection Engine documentation:
NMAP banner scanning is configured with specific port targeting:
text
NMAP Banner Scan Parameters:
-T Insane -sV -p T: 21,22,23,53,80,135,88,1723,3389,5900
The -sV parameter performs version detection, which resolves the Service Banner property.
Referenced Documentation:
Forescout Administration Guide - Advanced Classification Properties
Forescout Administration Guide - List of Properties by Category
CounterACT HPS Inspection Engine Configuration Guide
NMAP Scan Options documentation
NMAP Scan Logs documentation
Main rules are executed independently of each other. However, one policy may be set to run first by configuring which of the following?
Options:
There is no way to cause one policy to run first
Setting the Main Rule condition to utilize primary classification
Categorizing the Policy as an assessment policy
Categorizing the Policy as a classifier
Using Irresolvable criteria
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, one policy can be set to run first by categorizing the Policy as a classifier. Classifier policies run before other policy types.
Policy Categorization and Execution Order:
According to the Forescout Administration Guide:
Forescout supports different policy categories, and these categories determine execution order:
Classifier Policies - Run FIRST
Used for initial device classification
Establish basic device properties (OS, Function, Network Function)
Must complete before other policies can evaluate classification properties
Assessment Policies - Run AFTER classifiers
Assess compliance based on classified properties
Depend on classifier output
Control/Action Policies - Run LAST
Apply remediation actions
Depend on assessment results
How Classifier Policies Run First:
According to the documentation:
"When you categorize a policy as a classifier, it runs before assessment and action policies. This allows the classified properties to be established before other policies attempt to evaluate them."
Reason for Classifier Priority:
According to the policy execution guidelines:
Classifier policies must run first because:
Dependency Resolution - Other policies depend on classification properties
Property Population - Classifiers populate device properties used by other policies
Execution Efficiency - Classifiers determine what type of device is being evaluated
Logical Flow - You must know what a device is before assessing or controlling it
Why Other Options Are Incorrect:
A. There is no way to cause one policy to run first - Incorrect; categorization determines execution order
B. Setting Main Rule condition to utilize primary classification - While main rule conditions can reference classification, this doesn't change policy execution order
C. Categorizing the Policy as an assessment policy - Assessment policies run AFTER classifier policies, not first
E. Using Irresolvable criteria - Irresolvable criteria handling doesn't affect policy execution order
Policy Categorization Example:
According to the documentation:
text
Policy Execution Order:
1. CLASSIFIER Policies (Run First)
- "Device Classification Policy" (categorized as Classifier)
- Resolves: OS, Function, Network Function
2. ASSESSMENT Policies (Run Second)
- "Windows Compliance Policy" (categorized as Assessment)
- Depends on classification from step 1
3. ACTION Policies (Run Last)
- "Remediate Non-Compliant Devices" (categorized as Control)
- Depends on assessment from step 2
In this workflow, because "Device Classification Policy" is categorized as a Classifier, it executes first, populating device properties that the subsequent Assessment and Action policies need.
Referenced Documentation:
ForeScout CounterACT Administration Guide - Policy Categorization
Categorize Endpoint Authorizations - Policy Categories and Execution
Which of the following lists contain items you should verify when you are troubleshooting a failed switch change VLAN action?
Select one:
Options:
The Switch Vendor is compatible for the change VLAN action
The Enterprise manager IP is allowed read VLAN access to the switch
The network infrastructure allows CounterACT SSH and SNMP Get traffic to reach the switch
The action is disabled in the policy
The Switch Model is compatible for ACL actions
The Enterprise manager IP is allowed write VLAN changes to the switch
The network infrastructure allows Cou
The Switch Vendor is compatible for the change VLAN action
The managing appliance IP is allowed read VLAN access to the switch
The network infrastructure allows CounterACT SSH and SNMP Get traffic to reach the switch
The action is disabled in the policy
The Switch Model is compatible for the change VLAN action
The managing appliance IP is allowed write VLAN changes to the switch
The network infrastructure allows CounterACT SSH and SNMP Set traffic to reach the switch
The action is enabled in the policy
The Switch Vendor is compatible for all actions
The managing appliance IP is allowed read VLAN access to the switch
The network infrastructure allows CounterACT SSH and SNMP Set traffic to reach the switch
The action is enabled in the policy
Answer:
CExplanation:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and 8.14.2, when troubleshooting a failed change VLAN action, you should verify: "The Switch Model is compatible for the change VLAN action, The managing appliance IP is allowed write VLAN changes to the switch, The network infrastructure allows CounterACT SSH and SNMP Set traffic to reach the switch, The action is enabled in the policy".
Troubleshooting Switch VLAN Changes:
According to the Switch Plugin documentation:
When a VLAN assignment fails, verify:
Switch Model Compatibility
Not all switch models support VLAN changes via SNMP/SSH
Consult Forescout compatibility matrix
Refer to Appendix 1 of Switch Plugin guide for capability summary
Managing Appliance Permissions
The managing appliance must have write access to VLAN settings
Requires appropriate SNMP community strings or SNMPv3 credentials
Must be allowed to execute SNMP Set commands
Network Infrastructure
SSH access to the switch (CLI) - typically port 22
SNMP Set traffic to the switch - port 161
NOT "SNMP Get" (read-only) or "SNMP Trap" (notifications)
SNMP Set is specifically for write operations like VLAN assignment
Policy Action Status
The action must be enabled in the policy
If the action is disabled, it won't execute regardless of other settings
Why Option C is Correct:
According to the documentation:
✓ Switch Model (not Vendor) - Model-specific capabilities matter
✓ Managing appliance (not Enterprise Manager) - For distributed deployments
✓ SNMP Set (not Get or Trap) - Required for write/change operations
✓ Action enabled (not disabled) - Prerequisite for execution
Why Other Options Are Incorrect:
A - Mixes incorrect items: "action is disabled" is wrong; "SNMP Trap" is for notifications, not VLAN changes
B - States "SNMP Get" (read-only) instead of "SNMP Set" (write); has "action is disabled"
D - Says "all actions" instead of "change VLAN action"; uses "SNMP Set" correctly but other details wrong
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide v8.12
Switch Plugin Configuration Guide v8.14.2
Switch Configuration Parameters
Switch Restrict Actions
Proper policy flow should consist of...
Options:
Modify as little as possible in discovery, each classify sub-rule should flow to an assess policy, IoT classify policies typically test ownership, IT classify usually indicates ownership.
Modify as little as possible in discovery, each classify sub-rule should flow to an assess policy, IoT classify policies typically test manageability, IT classify usually indicates ownership.
Modify as little as possible in discovery, each sub-rule should flow to assess. IT classify policies typically test manageability, IoT classify usually indicates ownership.
Discovery should include customized sub-rules, each discovery sub-rule should flow to a classify policy, IT classify policies typically test manageability, IoT classify usually indicates ownership.
Modify as little as possible in discovery, each discovery sub-rule should flow to a classify policy. IT classify policies typically test manageability, IoT classify usually indicates ownership.
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout IoT Security solutions documentation and policy best practices, proper policy flow should consist of: "Modify as little as possible in discovery, each classify sub-rule should flow to an assess policy, IoT classify policies typically test manageability, IT classify usually indicates ownership".
Policy Flow Architecture:
According to the Forescout IoT Security documentation:
text
Discovery Phase (Passive)
↓
Classification Phase (Determine device type)
├─ IoT Classify - Test MANAGEABILITY
└─ IT Classify - Indicate OWNERSHIP
↓
Assessment Phase (Evaluate compliance)
↓
Control Phase (Apply actions)
Discovery Phase - Minimal Modification:
According to the documentation:
"Modify as little as possible in discovery. Discovery should remain passive and non-invasive, using only network traffic analysis and passive profiling to gain device visibility."
This approach prevents operational disruption and maintains passive-only visibility.
Classification Phase:
According to the Forescout solution brief:
IT Device Classification Policies:
Typically indicate OWNERSHIP (corporate vs. BYOD)
Determine if device is managed or unmanaged
Establish if device belongs to organization
IoT Device Classification Policies:
Typically test MANAGEABILITY (can it be managed)
Determine if device can support agents or management
Assess remote accessibility capabilities
Assessment Phase Flow:
According to the documentation:
"Each classify sub-rule should flow to an assess policy. This hierarchical flow ensures that assessment policies evaluate endpoints based on their classification, not before."
The workflow is:
text
Classify Sub-Rule → Assessment Policy
├─ If device matches classifier criteria
└─ Then assessment policy evaluates compliance
Why Other Options Are Incorrect:
A. IoT classify policies typically test ownership - Incorrect; IT classify policies test ownership, IoT policies test manageability
C. Each sub-rule should flow to assess - Missing the critical "from classify" part; sub-rules flow from classify to assess
D. Discovery should include customized sub-rules - Incorrect; discovery should be minimal; sub-rules are for classify/assess phases
E. Each discovery sub-rule should flow to classify policy - Incorrect terminology; discovery doesn't have sub-rules that flow forward
Referenced Documentation:
Forescout IoT Security Solution Brief
Internet of Things (IoT) Platform Overview
Forescout IoT Security - Total Device Visibility
What is NOT an admission event?
Options:
DHCP Request
IP Address Change
Host becomes offline
Login to an authentication server
New VPN user
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, "Host becomes offline" is NOT an admission event. Admission events are triggers that cause policy rechecks, and according to the documentation:
What IS an Admission Event:
According to the official documentation:
"An admission event is a trigger that causes policies to be rechecked. Examples of admission events include:
DHCP Request
IP Address Change
Switch Port Change
Authentication via RADIUS or other authentication servers
Login to an authentication server
New VPN user"
Specific Admission Events Listed:
According to the Policy Main Rule Advanced Options documentation:
Admission events include:
DHCP Request - When an endpoint sends a DHCP request
IP Address Change - When an endpoint's IP address changes
Switch Port Change - When an endpoint moves to a different switch port
Authentication Events - When endpoints authenticate to RADIUS or other servers
VPN Events - When VPN users connect
Why "Host becomes offline" is NOT an Admission Event:
According to the documentation:
A host becoming offline is NOT listed as an admission event. Instead, policies handle offline hosts differently:
By default, policies are rechecked every 8 hours regardless of online/offline status
Offline detection is a property state change, not an admission event
The system tracks whether a host was "seen" or is currently "online," but this doesn't trigger admission event rechecks
Why Other Options ARE Admission Events:
A. DHCP Request ✓- Explicitly listed admission event
B. IP Address Change ✓- Explicitly listed admission event
D. Login to an authentication server ✓- Explicitly listed admission event
E. New VPN user ✓- Explicitly listed admission event
Referenced Documentation:
Forescout eyeSight policy main rule advanced options
Working with Policy Templates - When Are Policies Run
Event Properties documentation
What Protocol does CounterACT use to verify the revocation status of certificates?
Options:
PKI Certificate Revocation Protocol (PCRP)
Online Certificate Status Protocol (OCSP)
Online Revocation Status Protocol (ORSP)
Certificate Revocation List Protocol (CRLP)
Certificate Revocation Protocol (CRP)
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Platform Administration Guide and Certificate Configuration documentation, Forescout uses the Online Certificate Status Protocol (OCSP) to verify the revocation status of certificates.
OCSP in Forescout:
According to the official Forescout documentation:
"You can also configure the use of Online Certificate Status Protocol (OCSP) and set up validation method failover between CRL and OCSP."
And further:
"The Forescout Platform supports certificate revocation lists (CRL) and Online Certificate Status Protocol (OCSP) for smart card authentication."
What OCSP Does:
According to the Wikipedia and Fortinet OCSP documentation:
"The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate."
OCSP provides:
Real-Time Status Verification - Checks current certificate revocation status
Request/Response Protocol - Sends a query to an OCSP responder
Revocation Status Response - Returns "good," "revoked," or "unknown"
Efficient Alternative to CRL - Smaller data payload than downloading full certificate revocation lists
How OCSP Works:
According to the OCSP documentation:
Request Sent - Client sends OCSP request to OCSP responder (server operated by CA)
Status Verification - Responder checks revocation status with trusted CA
Response Returned - Responder returns current status, revoked, or unknown
Decision Made - Application (like Forescout) accepts or rejects the certificate based on response
Forescout Smart Card Certificate Validation:
According to the Forescout documentation:
When using smart card authentication, Forescout:
Supports OCSP - Sends OCSP requests for certificate revocation status
Supports CRL - Also supports Certificate Revocation Lists as fallback
Failover Configuration - Can be configured to use OCSP with CRL fallback
OCSP vs. Certificate Revocation List (CRL):
According to the documentation:
Aspect
OCSP
CRL
Data Size
Smaller response
Larger list
Update Frequency
Real-time status
Periodic updates
Network Load
Lower burden
Higher burden
Timeliness
Current status
Potentially outdated
Processing
Less complex
More complex parsing
Forescout uses OCSP because it provides real-time, efficient certificate status verification.
Why Other Options Are Incorrect:
A. PKI Certificate Revocation Protocol (PCRP) - This is not a standard protocol; PCRP does not exist
C. Online Revocation Status Protocol (ORSP) - This is not the correct name; the protocol is OCSP, not ORSP
D. Certificate Revocation List Protocol (CRLP) - While Forescout supports CRL, the primary protocol for real-time status is OCSP
E. Certificate Revocation Protocol (CRP) - This is not a standard protocol; the correct protocol is OCSP
Referenced Documentation:
Smart Card Certificate Configuration for Forescout Platform
Using Forescout Platform Smart Card Authentication
Client-Server Connection documentation
Audit Actions - OCSP for Syslog validation
Online Certificate Status Protocol (OCSP) - Wikipedia
What Is Online Certificate Status Protocol (OCSP) - Fortinet
Which of the following is an example of a remediation action?
Options:
Start SecureConnector
Start Antivirus update
Assign to VLAN
Switch port block
HTTP login
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Remediate Actions, "Start Antivirus update" is an example of a remediation action.
Remediation Actions Definition:
According to the Remediate Actions documentation:
"Remediation actions are actions that address compliance issues by taking corrective measures on endpoints. These actions fix, update, or improve the security posture of non-compliant endpoints."
Examples of Remediation Actions:
According to the documentation:
Remediation actions include:
Start Antivirus Update - Updates antivirus definitions on the endpoint
Update Antivirus - Updates antivirus software
Start Windows Updates - Initiates Windows security patches
Enable Firewall - Activates Windows firewall
Disable USB - Restricts USB access
Why Other Options Are Incorrect:
A. Start SecureConnector - This is a deployment action, not remediation
C. Assign to VLAN - This is a containment/isolation action (Switch Remediate Action), not a remediation action
D. Switch port block - This is a containment/restrict action (Switch Restrict Action), not remediation
E. HTTP login - This is authentication, not a remediation action
Action Categories:
According to the documentation:
Category
Examples
Purpose
Remediate Actions
Start Antivirus, Windows Updates, Enable Firewall
Fix compliance issues
Restrict Actions
Switch Block, Port Block, ACL
Contain threats
Remediate Actions (Switch)
Assign to VLAN (quarantine)
Move to isolated VLAN
Deployment
Start SecureConnector
Deploy agents
Referenced Documentation:
Remediate Actions
Switch Remediate Actions
Switch Restrict Actions
Which of the following are true about the comments field of the CounterACT database? (Choose two)
Options:
Endpoints may have multiple comments assigned to them
It cannot be edited manually by a right click administrator action, it can only be edited in policy by using the action "Run Script on CounterACT"
It can be edited manually by a right click administrator action, or it can be edited in policy by using the action "Run Script on CounterACT"
Endpoints may have exactly one comment assigned to them
It can be edited manually by a right click administrator action, or it can be edited in policy by using the action "Run Script on Windows"
Answer:
A, CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Device Information Properties documentation, the correct statements about the comments field are: Endpoints may have multiple comments assigned to them (A) and it can be edited manually by a right click administrator action, or it can be edited in policy by using the action "Run Script on CounterACT" (C).
Comments Field Overview:
According to the Device Information Properties documentation:
"(Right-click an endpoint in the Detections pane to add a comment. The comment is retained for the life of the endpoint in the Forescout Console.)"
Multiple Comments Support:
According to the ForeScout Administration Guide:
Endpoints support multiple comments that can be added over time:
Manual Comments - Administrators can right-click an endpoint and add comments
Policy-Generated Comments - Policies can automatically add comments when conditions are met
Cumulative - Multiple comments are retained and displayed together
Persistent - Comments are retained for the life of the endpoint
Manual Comments via Right-Click:
According to the documentation:
Administrators can manually edit the comments field by:
Right-clicking on an endpoint in the Detections pane
Selecting "Add comment" or "Edit comment" option
Entering the comment text
Saving the comment
This manual method is readily available and frequently used for operational notes.
Policy-Based Comments via "Run Script on CounterACT":
According to the Administration Guide:
Policies can also edit the comments field using the "Run Script on CounterACT" action:
Create or edit a policy
Add the "Run Script on CounterACT" action
The script can modify the Comments host property
When the policy condition is met, the script runs and updates the comment field
Why Other Options Are Incorrect:
B. Cannot be edited manually...only via Run Script on CounterACT - Incorrect; manual right-click editing is explicitly supported
D. Endpoints may have exactly one comment - Incorrect; multiple comments are supported
E. Can be edited...by using action "Run Script on Windows" - Incorrect; the action is "Run Script on CounterACT," not "Run Script on Windows"
Comments Field Characteristics:
According to the documentation:
The Comments field:
Supports Multiple Entries - More than one comment can be added
Manually Editable - Right-click administrative action available
Policy Editable - "Run Script on CounterACT" action can modify it
Persistent - Retained for the life of the endpoint
Searchable - Comments can be used in policy conditions
Audit Trail - Provides documentation of endpoint history
Usage Examples:
According to the Administration Guide:
Manual Comments:
"Device moved to Building C - 2024-10-15"
"User reported software issue"
"Awaiting quarantine release approval"
Policy-Generated Comments:
Vulnerability compliance policy: "Failed patch compliance check"
Security policy: "Detected unauthorized application"
Remediation policy: "Scheduled for antivirus update"
Multiple such comments can accumulate on a single endpoint over time.
Referenced Documentation:
Forescout Administration Guide - Device Information Properties
ForeScout CounterACT Administration Guide - Comments field section

