Fortinet NSE 5 - FortiAnalyzer 7.6 Analyst Questions and Answers
Exhibit.
What can you conclude about these search results? (Choose two.)
Exhibit.
Assume these are all the events that exist on the FortiAnalyzer device.
How many events will be added to the incident created after running this playbook?
Which statement about exporting items in Report Definitions is true?
After a generated a repot, you notice the information you were expecting to see in not included in it. However, you confirm that the logs are there:
Which two actions should you perform? (Choose two.)
You mustfind a specific security event log in the FortiAnalyzer logs displayed in FortiView, but, so far, you have been uncuccessful.
Which two tasks should you perform to investigate why you are having this issue? (Choose two.)
Which statement about sending notifications with incident updates is true?
Which statement about automation connectors in FortiAnalyzer is true?
As part of your analysis, you discover that a Medium severity level incident is fully remediated.
You change the incident status to Closed:Remediated.
Which statement about your update is true?
Which two actions should an administrator take to vide Compromised Hosts on FortiAnalyzer? (Choose two.)
Exhibit.
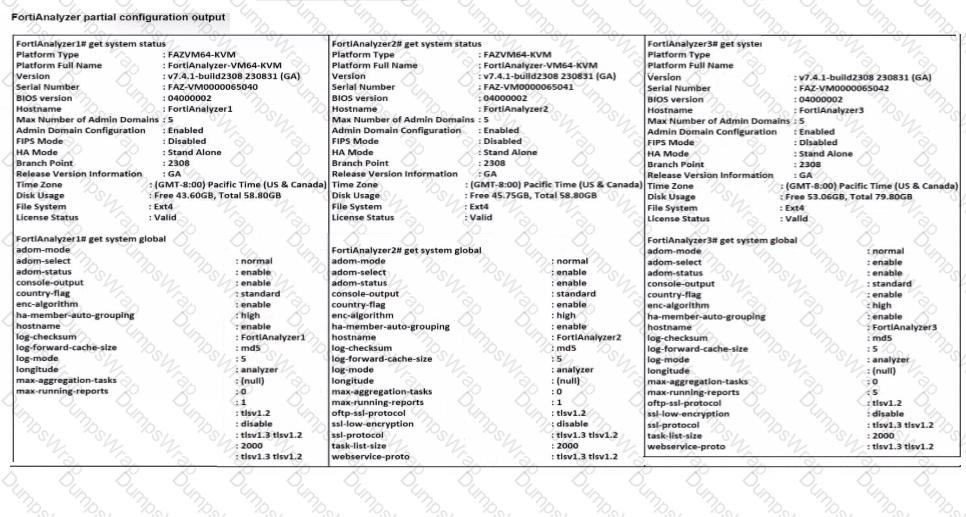
Based on the partial outputs displayed, which devices can be members of a FotiAnalyzer Fabric?
You are tasked with finding logs corresponding to a suspected attack on your network.
You need to use an interface where all identified threats within timeframe are listed and organized. You also need to be able to quickly export the information to a PDF file.
Where can you go to accomplish this task?
Refer to Exhibit:
Client-1 is trying to access the internet for web browsing.
All FortiGate devices in the topology are part of a Security Fabric with logging to FortiAnalyzer configured. All firewall policies have logging enabled. All web filter profiles are configured to log only violations.
Which statement about the logging behavior for this specific traffic flow is true?
(In a FortiAnalyzer Fabric deployment, which three modules from Fabric members are available for analysis on the supervisor? (Choose three answers))
(Refer to the exhibit.

Which statement about the displayed event is correct? (Choose one answer))
(Refer to the exhibit.
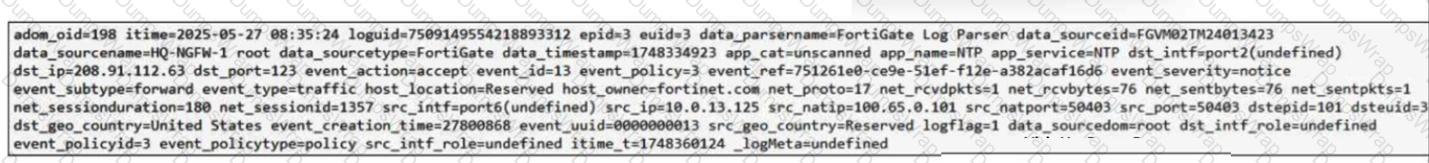
Which two observations can you make after reviewing this log entry? (Choose two answers))
Which two statement regarding the outbreak detection service are true? (Choose two.)
Exhibit.
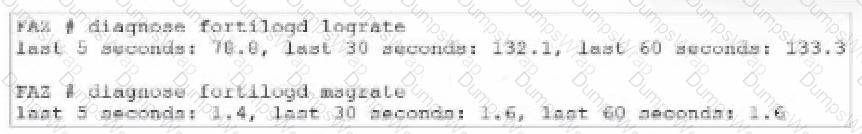
What can you conclude about the output?
Refer to Exhibit:
Whatdoes the data point at 21:20 indicate?
(When there are no matching parsers for a device log, what does FortiAnalyzer do? (Choose one answer))
Whathappens when the indicator of compromise (IOC) engine on FortiAnalyzer finds web logs that match blacklisted IP addresses?

