Fortinet NSE 6 - Network Security 7.6 Support Engineer Questions and Answers
Which Iwo troubleshooting steps should you perform lf you encounter issues with intermittent web filter behavior? (Choose two.)
What is an accurate description of LDAP authentication using the regular bind type?
In the SAML negotiation process, which section does the Identity Provider (IdP) provide the SAML attributes utilized in the authentication process to the Service Provider (SP)?
Exhibit.
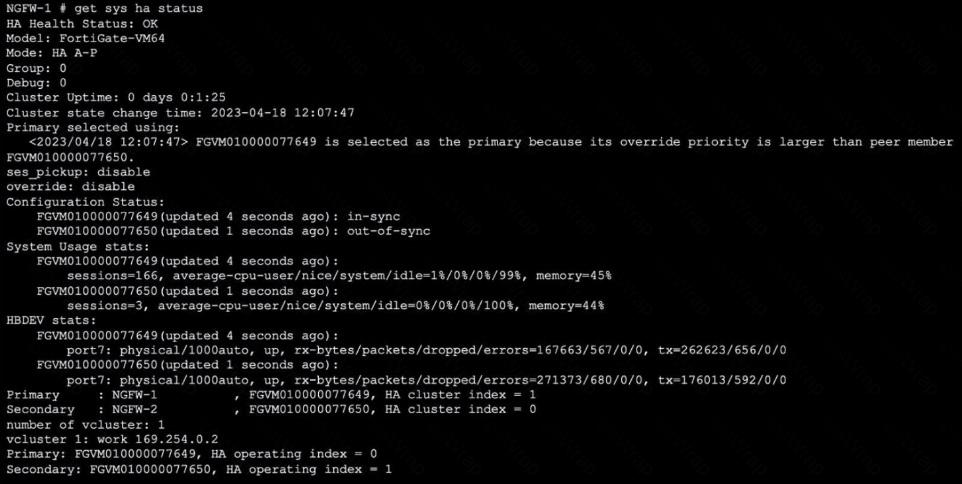
Refer to the exhibit, which shows the output of get system ha status.
NGFW-1 and NGFW-2 have been up for a week.
Which two statements about the output are true? (Choose two.)
Refer to the exhibit, which shows the output of the command get router info bgp neighbors 100.64.2.254 advertised-routes.
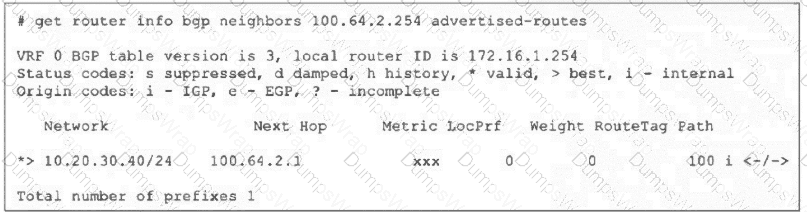
What can you conclude from the output?
Refer to the exhibit, which shows the output of a debug command.
Which two statements about the output are true? (Choose two.)
Refer to the exhibit.
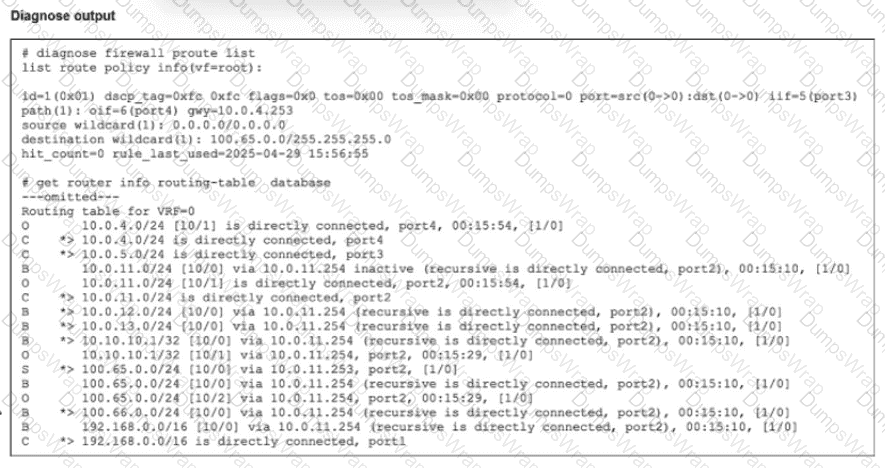
Which route will traffic take to get to the 100.65.0.0/24 network considering the routes are all configured with the same distance?
What is the correct order of the IKEv2 request-and-response protocol?
Refer to the exhibit, which contains partial output from an IKE real-time debug.
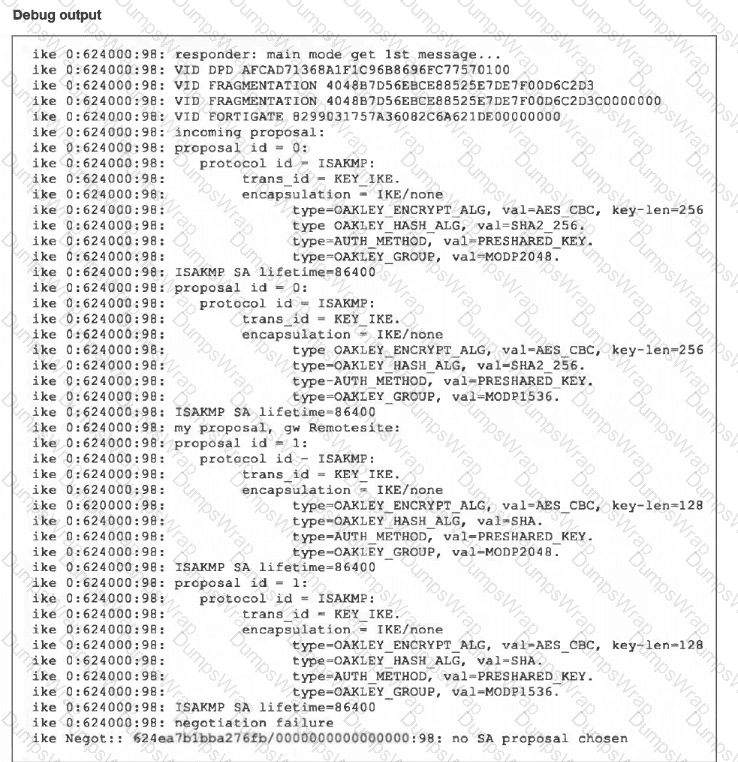
The administrator does not have access to the remote gateway.
Based on the debug output, which configuration change the administrator make to the local gateway to resolve the phase 1 negotiation error?
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)
Exhibit.
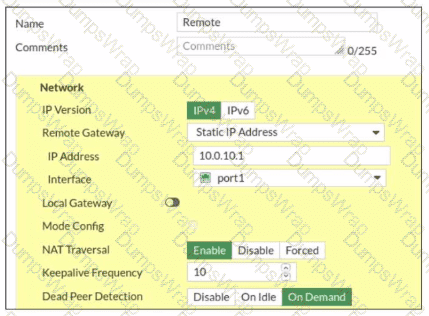
Refer to the exhibit, which contains a screenshot of some phase 1 settings.
The VPN is not up. To diagnose the issue, the administrator enters the following CLI commands on an SSH session on FortiGate:
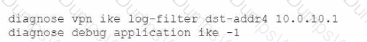
However, the IKE real-time debug does not show any output. Why?
Refer to the exhibit.
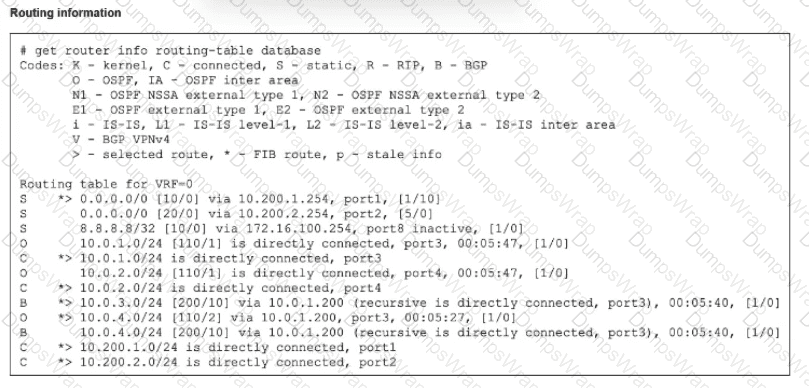
The modified output of live routing kemel is shown
Which two statements about the output are (rue? (Choose two.)
Refer to the exhibit.
Partial output of diagnose sys session stat command is shown.
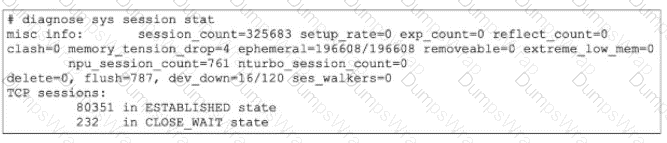
An administrator has noticed unusual behavior from FortiGate. It appears that sessions are randomly removed. Which two reasons could explain this? (Choose two.)
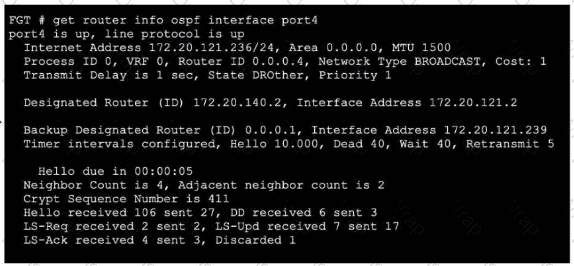
Refer to the exhibit, which shows the output of get router info ospf neighbor.

What can you conclude from the command output?
Refer to the exhibit.
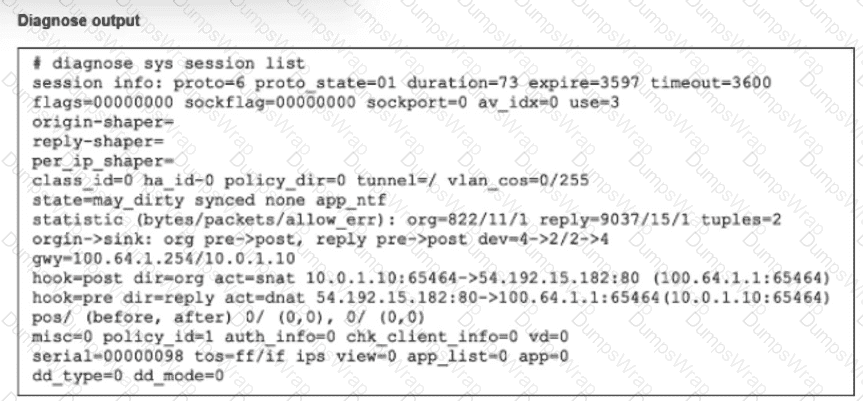
The output of diagnose sys session list command is shown.
If the HA ID for the primary device is 9, what happens if the primary fails and the secondary becomes the primary?
Refer to the exhibit.
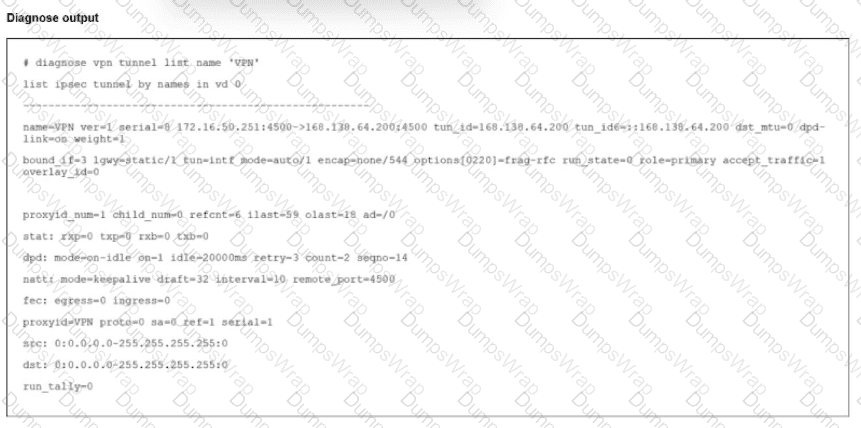
The output of the command diagnose vpn tunnels liar is shown.
Which two statements accurately describe the status of the tunnel? (Choose two.)
Exhibit.
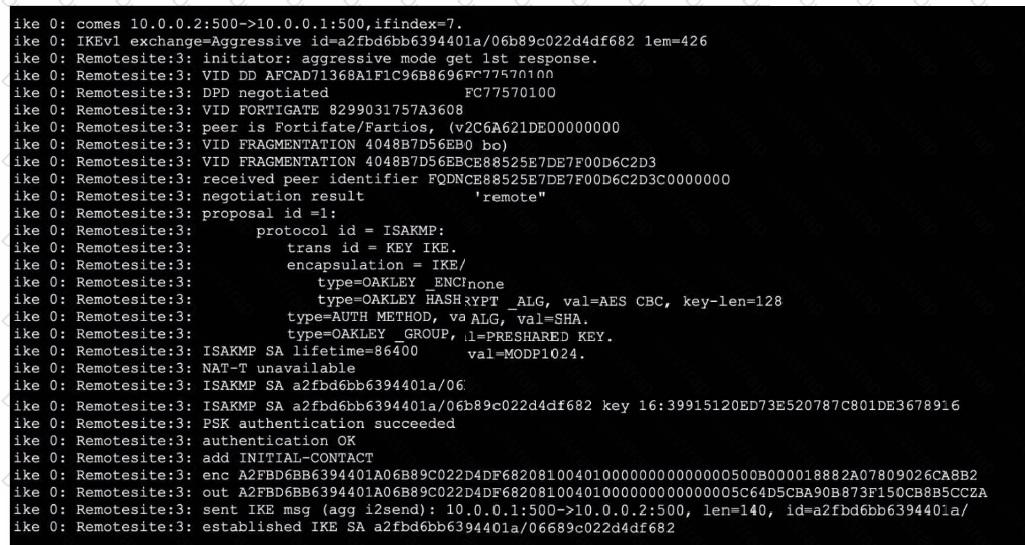
Refer to the exhibit, which contains partial output from an IKE real-time debug.
Which two statements about this debug output are correct? (Choose two.)
Exhibit.

Refer to the exhibit, which shows two entries that were generated in the FSSO collector agent logs.
What three conclusions can you draw from these log entries? {Choose three.)
Refer to the exhibit, which shows a partial output of the real-time LDAP debug.
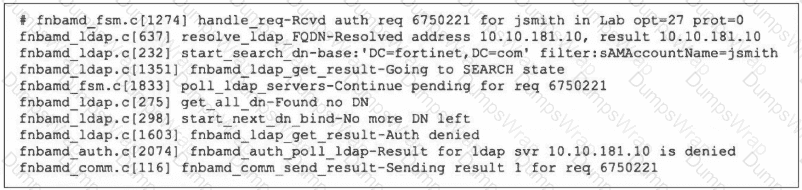
What two actions can the administrator take to resolve this issue? (Choose two.)
Which two statements about conserve mode are true? (Choose two.)
Which statement about IKEv2 is true?
A FortiGate administrator is troubleshooting a VPN that is failing to establish.
As a first step, the administrator is attempting to sniff the traffic using the command:
# diagnose sniffer packet any ‘’udp port 500 or udp port 4500 or esp’’ 4
After several minutes there is still no output. What is the most Likely reason for this?
Which two statements about Security Fabric communications are true? (Choose two.)
Refer to the exhibit, which shows the modified output of the routing kernel.
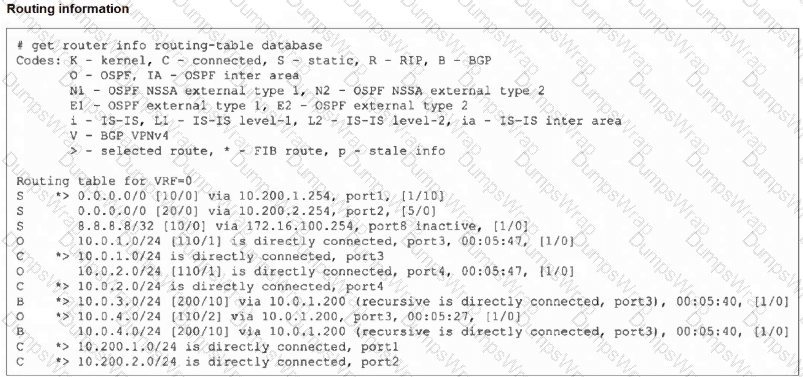
Which statement is true?
Refer to the exhibits,
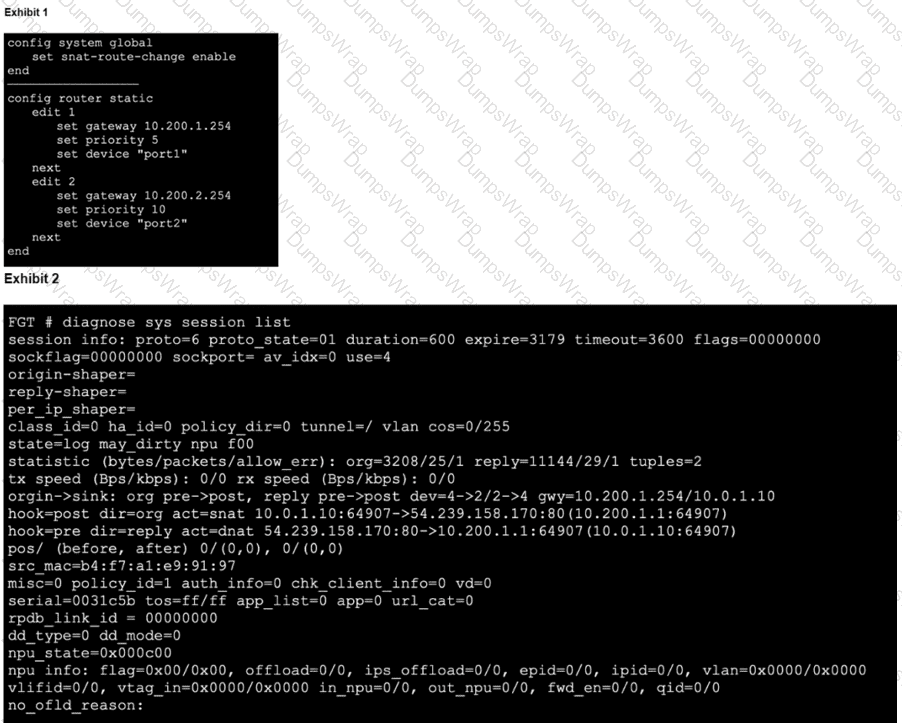
which show the configuration on FortiGate and partial session information for internet traffic from a user on the internal network. If the priority on route ID 2 were changed from 10 to 0, what would happen to traffic matching that user session? (Choose one answer)
Consider the scenario where the server name indication (SNI) does not match either the common name (CN) or any of the subject alternative names (SAN) in the server certificate. Which two actions will FortiGate take when using the default settings for SSL certificate inspection? (Choose two answers)
Which statement about parallel path processing is correct (PPP)?
Refer to the exhibit, which shows a truncated output of a real-time LDAP debug.
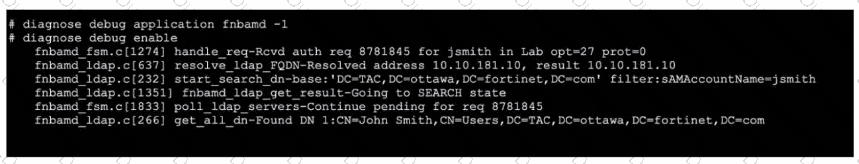
What two conclusions can you draw from the output? (Choose two.)
Exhibit 1.
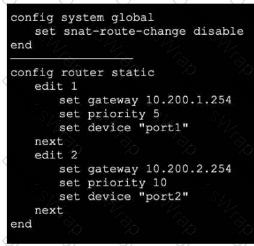
Exhibit 2.
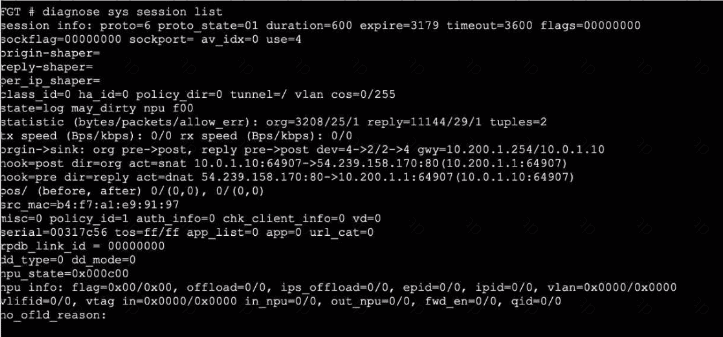
Refer to the exhibits, which show the configuration on FortiGate and partial internet session information from a user on the internal network.
An administrator would like to lest session failover between the two service provider connections.
Which two changes must the administrator make to force this existing session to immediately start using the other interface? (Choose two.)
What are two reasons that an OSPF router does not have any type 5 tank-state advertisements (LSAs) In its link-stale database (LSD6)? (Choose two.)

