Fortinet NSE 5 - FortiSASE and SD-WAN 7.6 Core Administrator Questions and Answers
You have a FortiGate configuration with three user-defined SD-WAN zones and one or two members in each of these zones. One SD-WAN member is no longer used in health-check and SD-WAN rules. This member is the only member of its zone. You want to delete it.
What happens if you delete the SD-WAN member from the FortiGate GUI?
Options:
FortiGate displays an error message. SD-WAN zones must contain at least one member.
FortiGate accepts the deletion and removes static routes as required.
FortiGate accepts the deletion with no further action.
FortiGate accepts the deletion and places the member in the default SD-WAN zone.
Answer:
BExplanation:
Questions no:9Verified Answer: B
Comprehensive and Detailed Explanation with all FortiSASE and SD-WAN 7.6 Core Administrator curriculum documents: According to theSD-WAN 7.6 Core Administratorstudy guide andFortiOS 7.6 Administration Guide, the behavior for deleting an SD-WAN member from the GUI when it is the only member in its zone is governed by the following operational logic:
Reference Checks: Before allowing the deletion of any SD-WAN member, FortiOS performs a "check for dependencies." If an interface is being used in an activePerformance SLAor anSD-WAN Rule, the GUI will typically prevent the deletion or gray out the option until those references are removed. However, the question specifies that this member isno longer usedin health-checks or rules.
Zone Integrity: Unlike some other network objects, an SD-WAN zone is permitted to exist without any members. When you delete the final member of a user-defined zone through the GUI, the zone itself remains in the configuration as an empty container.
Route Management: When an SD-WAN member is deleted, any static routes that were specifically tied to that interface's membership in the SD-WAN bundle are automatically updated or removed by the FortiGate to prevent routing loops or "black-holing" traffic. This is part of the automated cleanup process handled by the FortiOS management plane.
GUI vs. CLI: In the GUI, the process is streamlined to allow the removal of the member interface. Once the member is deleted, the interface returns to being a "regular" system interface and can be used for standard firewall policies or other functions.
Why other options are incorrect:
Option A: There is no requirement that a zone must contain at least one member; "empty" zones are valid configuration objects in FortiOS 7.6.
Option C: While the deletion is accepted, it is not with "no further action"—the system must still reconcile the routing table and interface status.
Option D: FortiGate does not automatically move deleted members into the default zone (virtual-wan-link). Once deleted, the interface is simply no longer an SD-WAN member.
How does the FortiSASE security dashboard facilitate vulnerability management for FortiClient endpoints? (Choose one answer)
Options:
It automatically patches all vulnerabilities without user intervention and does not categorize vulnerabilities by severity.
It shows vulnerabilities only for applications and requires endpoint users to manually check for affected endpoints.
It displays only critical vulnerabilities, requires manual patching for all endpoints, and does not allow viewing of affected endpoints.
It provides a vulnerability summary, identifies affected endpoints, and supports automatic patching for eligible vulnerabilities.
Answer:
DExplanation:
According to theFortiSASE 7.6 Administration Guideand theFCP - FortiSASE 24/25 Administratortraining materials, the security dashboard is a centralized hub for monitoring and remediating security risks across the entire fleet of managed endpoints.
Vulnerability Summary: The dashboard includes a dedicatedVulnerability summary widgetthat categorizes risks by severity (Critical, High, Medium, Low) and by application type (OS, Web Client, etc.).
Identifying Affected Endpoints: The dashboard is fully interactive; an administrator candrill downinto specific vulnerability categories to view a detailed list ofCVE dataand, most importantly, identify the specificaffected endpointsthat require attention.
Automatic Patching: FortiSASE supportsautomatic patching for eligible vulnerabilities(such as common third-party applications and supported OS updates). This feature is configured within theEndpoint Profile, allowing the FortiClient agent to remediate risks without requiring the user to manually run updates.
Why other options are incorrect:
Option A: While it supports automatic patching, it does not do so forallvulnerabilities (only eligible/supported ones), and it specificallydoescategorize them by severity.
Option B: The dashboard shows vulnerabilities for theOperating Systemas well as applications, and it allows theadministratorto identify affected endpoints rather than requiring the end-user to check.
Option C: The dashboard displaysall levels of severity(not just critical) and explicitly allows the viewing of affected endpoints.
Which secure internet access (SIA) use case minimizes individual endpoint configuration? (Choose one answer)
Options:
Agentless remote user internet access
SIA for FortiClient agent remote users
Site-based remote user internet access
SIA using ZTNA
Answer:
CExplanation:
According to theFortiSASE 7.6 Architecture GuideandAdministration Guide, theSite-based remote user internet accessuse case is the only deployment model that completely eliminates the need for individual endpoint configuration.
Centralized Enforcement: In a site-based deployment, a "thin edge" device (such as aFortiExtenderor aFortiGatein LAN extension mode) is installed at the remote site. This device establishes a secure tunnel to the FortiSASE Point of Presence (PoP).
Zero Endpoint Configuration: Because the traffic redirection happens at the network gateway level, individual devices (laptops, IoT devices, mobile phones) behind the site-based device do not require any specialized software or settings. They simply connect to the local network as they would normally, and their traffic is automatically secured by the SASE cloud.
Comparison with Other Modes:
Agent-based (Option B): Requires the installation and maintenance ofFortiClientsoftware on every device, often managed via MDM tools.
Agentless (Option A): While it doesn't need an agent, it typically requires the configuration ofExplicit Web Proxysettings or the distribution of aPAC (Proxy Auto-Configuration) filevia GPO or SCCM to each device's browser.
ZTNA (Option D): Generally requires an endpoint agent (FortiClient) to perform posture checks and identity verification, involving significant endpoint-level configuration.
Why other options are incorrect:
Option A: Agentless mode is often confused with being "configuration-free," but it still requires endpoints to be pointed toward the FortiSASE proxy.
Option B: This is the most configuration-intensive mode, requiring full software lifecycles for every endpoint.
Option D: ZTNA is an access methodology that adds configuration complexity (tags, certificates, posture checks) rather than minimizing it.
You want FortiGate to use SD-WAN rules to steer ping local-out traffic. Which two constraints should you consider? (Choose two.)
Options:
You must configure each local-out feature individually to use SD-WAN.
By default, FortiGate uses SD-WAN rules only for local-out traffic that corresponds to ping and traceroute.
You can steer local-out traffic only with SD-WAN rules that use the manual strategy.
By default, FortiGate uses SD-WAN rules only for local-out traffic that corresponds to ping and traceroute.
Answer:
A, BExplanation:
In theSD-WAN 7.6 Core Administratorcurriculum, steering "local-out" traffic (traffic generated by the FortiGate itself, such as DNS queries, FortiGuard updates, or diagnostic pings) requires specific configuration because this traffic follows a different path than "forward" traffic.
Individual Configuration (Option A): By default, local-out traffic bypasses the SD-WAN engine and uses the standard system routing table (RIB/FIB). To use SD-WAN rules for specific features like DNS or RADIUS, you must individually enable the sdwan interface-select-method within that feature's configuration (e.g., config system dns or config user radius).
Default Steerable Traffic (Option B): In FortiOS 7.6, while most local-out traffic is excluded from SD-WAN by default, the system is designed so that when SD-WAN is active, it primarily considers SD-WAN rules for specific diagnostic local-out traffic—specificallypingandtraceroute—to allow administrators to verify path quality using the same logic as user traffic.
Why other options are incorrect:
Option C: Local-out traffic can be steered using any SD-WAN strategy (Manual, Best Quality, etc.), provided the interface-selection-method is set to sdwan.
Refer to the exhibit.
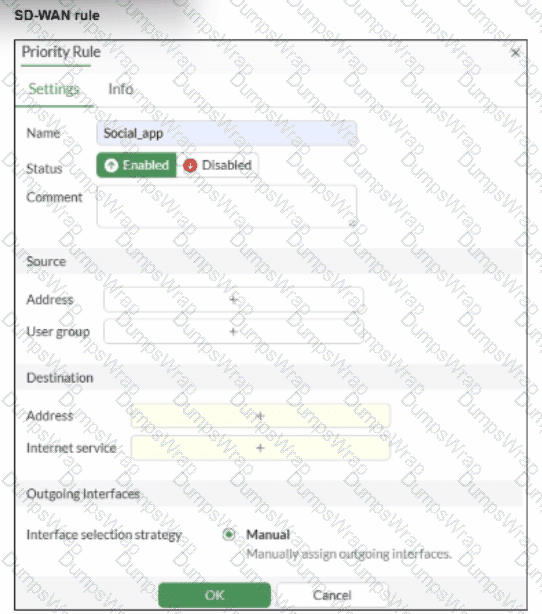
You configure SD-WAN on a standalone FortiGate device. You want to create an SD-WAN rule that steers traffic related to Facebook and LinkedIn through the less costly internet link. What must you do to set Facebook and LinkedIn applications as destinations from the GUI?
Options:
Install a license to allow applications as destinations of SD-WAN rules.
In the Internet service field, select Facebook and LinkedIn.
You cannot configure applications as destinations of an SD-WAN rule on a standalone FortiGate device.
Enable the visibility of the applications field as destinations of the SD-WAN rule.
Answer:
BExplanation:
According to theSD-WAN 7.6 Core Administratorcurriculum and theFortiOS 7.6 Administration Guide, setting common web-based services like Facebook and LinkedIn as destinations in an SD-WAN rule is primarily accomplished through theInternet Service Database (ISDB).
Internet Service vs. Application Control: In FortiOS, there is a distinction betweenInternet Services(which use a database of known IP addresses and ports to identify traffic at the first packet) andApplications(which require the IPS engine to inspect deeper into the packet flow to identify Layer 7 signatures).
SD-WAN Efficiency: Fortinet recommends using theInternet service fieldfor services like Facebook and LinkedIn in SD-WAN rules because it allows the FortiGate to steer the traffic immediately upon the first packet. If the "Application" signatures were used instead, the first session might be misrouted because the application is not identified until after the initial handshake.
GUI Configuration: As shown in the exhibit (image_b3a4c2.png), the "Destination" section of an SD-WAN rule includes anInternet servicefield by default. To steer Facebook and LinkedIn traffic, the administrator simply clicks the "+" icon in that field and selects the entries for Facebook and LinkedIn from the database.
Feature Visibility (Alternative): While youcanenable a specific "Application" field inSystem > Feature Visibility(by enabling "Application Detection Based SD-WAN"), this is typically used for less common applications that do not have dedicated ISDB entries. For the specific "applications" mentioned (Facebook and LinkedIn), they are natively available in theInternet servicefield, making Option B the most direct and common implementation.
Why other options are incorrect:
Option A: Licensing for application signatures is part of the standard FortiGuard services and is not a prerequisite specific only to "applications as destinations" in SD-WAN rules.
Option C: Standalone FortiGate devices fully support application-based and ISDB-based steering in SD-WAN rules.
Option D: While enabling feature visibility would add anadditionalfield for L7 applications, it is not a "must" for Facebook and LinkedIn, which are already accessible via the Internet Service field provided in the default GUI layout.
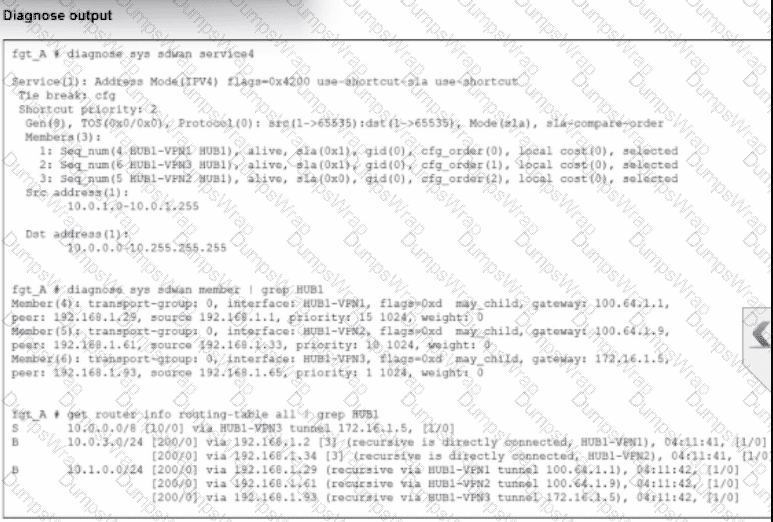
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over HUB1-VPN1. However, the traffic is routed over HUB1-VPN3.
Based on the output shown in the exhibit, which two reasons, individually or together, could explain the observed behavior? (Choose two.)
Options:
HUB1-VPN1 does not have a valid route to the destination.
HUB1-VPN3 has a higher member configuration priority than HUB1-VPN1.
HUB1-VPN3 has a lower route priority value (higher priority) than HUB1-VPN1.
The traffic matches a regular policy route configured with HUB1-VPN3 as the outgoing device.
Answer:
A, CExplanation:
According to theSD-WAN 7.6 Core Administratorcurriculum and the diagnostic outputs shown in the exhibit, the reason traffic is steered toHUB1-VPN3instead of the expectedHUB1-VPN1(defined in SD-WAN rule ID 1) can be explained by two core routing principles in FortiOS:
Valid Route Requirement (Option A): In thediagnose sys sdwan service 4output (which corresponds to Rule ID 1), it shows the rule has membersHUB1-VPN1,HUB1-VPN2, andHUB1-VPN3. A key principle of SD-WAN steering is that for a member to be "selectable" by a rule, itmust have a valid route to the destinationin the routing table (RIB/FIB). If the routing table output (the third section of the exhibit) shows a route to 10.0.0.0/8 viaHUB1-VPN3butnotthroughHUB1-VPN1, the SD-WAN engine will skip HUB1-VPN1 entirely because it is considered a "non-reachable" path for that specific destination.
Policy Route Precedence (Option D): In the FortiOS route lookup hierarchy,Regular Policy Routes (PBR)are evaluatedbeforeSD-WAN rules. If an administrator has configured a traditional Policy Route (found underNetwork > Policy Routes) that matches traffic destined for 10.0.0.0/8 and specifiesHUB1-VPN3as the outgoing interface, the FortiGate will forward the packet based on that policy route and willnever evaluate the SD-WAN rulesfor that session. This "bypass" occurs regardless of whether the SD-WAN rule would have chosen a "better" link.
Why other options are incorrect:
Option B: While member configuration priority (cfg_order) is a tie-breaker in some strategies, the SD-WAN rule logic is only applied if the routing table allows it or if a higher-priority policy route doesn't intercept the traffic first.
Option C: Lower route priority (which means higher preference in the RIB) affects theImplicit Rule(standard routing). However, SD-WAN rules are designed tooverrideRIB priority for matching traffic. If HUB1-VPN1 was a valid candidate and no Policy Route existed, the SD-WAN rule would typically ignore RIB priority to enforce its own steering strategy.
Which two delivery methods are used for installing FortiClient on a user's laptop? (Choose two.)
Options:
Use zero-touch installation through a third-party application store.
Download the installer directly from the FortiSASE portal.
Send an invitation email to selected users containing links to FortiClient installers.
Configure automatic installation through an API to the user's laptop.
Answer:
B, CExplanation:
TheFortiSASE 7.6 Administration Guideoutlines the standard onboarding procedures for deploying theFortiClientagent to remote endpoints. There are two primary user-facing delivery methods:
Download from the FortiSASE portal (Option B):Administrators can provide users with access to the FortiSASE portal where they can directly download apre-configured installer. This installer is uniquely tied to the organization’s SASE instance, ensuring the client automatically registers to the correct cloud EMS upon installation.
Invitation Email (Option C):This is the most common administrative method. The FortiSASE portal (via its integrated EMS) allows administrators to send an invitation email to specific users or groups. This email contains direct download links for various operating systems (Windows, macOS, Linux) and the necessary invitation code for zero-touch registration.
Why other options are incorrect:
Option A:While third-party stores (like the App Store or Google Play) are used for mobile devices, "zero-touch installation through a third-party store" is not the standard curriculum-defined method forlaptops(Windows/macOS) in a SASE environment.
Option D:FortiSASE does not use a direct "API to the user's laptop" for automatic installation. While MDM/GPO (centralized deployment) is supported, it is not described as an API-based auto-installation in the core curriculum.
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two answers)
Options:
Traffic is load balanced using the algorithm set for the v4-ecmp-mode setting.
Traffic does not match any of the entries in the policy route table.
FortiGate flags the session with may_dirty and vwl_default.
The traffic is distributed, regardless of weight, through all available static routes.
The session information output displays no SD-WAN service id.
Answer:
B, EExplanation:
According to theSD-WAN 7.6 Core Administratorstudy guide andFortiOS 7.6 Administration Guide, the "implicit rule" is the default rule at the bottom of the SD-WAN rule list (ID 0). It is only evaluated if traffic does not match any manually configured SD-WAN rules.
Policy Route Table Context (Option B): SD-WAN rules are technically a specialized form of policy-based routing. For a packet to match theimplicit rule, it must first pass through the routing hierarchy. If traffic matches the implicit rule, it indicates that it did not match any higher-priority user-defined SD-WAN rules or any specific entries in the manualpolicy route tablethat would have intercepted the traffic earlier.
Session Information (Option E): When you use the CLI to inspect an active session (e.g., diagnose sys session list), the output contains a field for theSD-WAN Service ID. If traffic is steered by a user-defined rule, it displays the ID of that rule (e.g., service_id=1). However, when traffic falls through to theimplicit rule, the session information displaysno SD-WAN service ID(it often shows as 0 or is omitted), because the implicit rule does not function as a "service" in the same way user-defined rules do.
Routing Behavior: The implicit rule follows the standard routing table (RIB/FIB) logic. It uses thepriorityanddistanceof the static routes to determine the path. If multiple paths have the same distance and priority, it uses the algorithm set by v4-ecmp-mode, but this is a function of the routing engine, not the SD-WAN engine itself.
Why other options are incorrect:
Option A: While v4-ecmp-mode (e.g., source-ip-based) is used for ECMP routing, this is part of the general FortiOS routing behavior for equal-cost paths in the FIB, whereas the implicit rule simply "hands over" the decision to that routing table.
Option C: When traffic matches the implicit rule, the session is actually flagged with vwl_id=0 and potentially dirty if a route change occurs, but vwl_default is not the standard flag name used in this specific context in the curriculum.
Option D: This is incorrect because the implicit ruledoes respect weight, distance, and priorityas defined in the static routes within the routing table; it does not distribute traffic "regardless" of these values.
Refer to the exhibit.

Which two statements about the Vulnerability summary dashboard in FortiSASE are correct? (Choose two.)
Options:
The dashboard shows the vulnerability score for unknown applications.
Vulnerability scan is disabled in the endpoint profile.
The dashboard allows the administrator to drill down and view CVE data and severity classifications.
Automatic vulnerability patching can be enabled for supported applications.
Answer:
C, DExplanation:
Based on theFortiSASE 7.6 (and later 2025 versions)curriculum and administration guides, the Vulnerability summary dashboard is a key component of the endpoint security posture management.
Drill Down Capability (Option C): According to theFortiSASE Administration Guide, the Vulnerability summary widget on the Security dashboard is interactive. An administrator can click on specific risk categories (e.g., Critical, High) or application types (e.g., Operating System, Web Client) todrill down. This action opens a detailed pane showing the specific affected endpoints, associatedCVE identifiers, and severity classifications based on the CVSS standard.
Automatic Vulnerability Patching (Option D): In theFortiSASE 7.6/2025feature sets, the endpoint profile configuration (underEndpoint > Configuration > Profiles) includes an "Automatic Patching" section. This feature allows the system to automatically install security updates for supported third-party applications and the underlying operating system (Windows/macOS) when vulnerabilities are detected. Furthermore, administrators can schedule these patches directly from theVulnerability Summarywidget by selecting specific vulnerabilities.
Why other options are incorrect:
Option A: The dashboard categories (Operating System, Web Client, Microsoft Office, etc.) are based on known software signatures. While there is an "Other" category, the dashboard primarily provides scores for recognized applications where CVE data is available.
Option B: The exhibit shows active data (157 total vulnerabilities), which indicates that thevulnerability scan is enabledand currently reporting data from the endpoints. If it were disabled, the widget would be empty or show zeros.
Which three FortiSASE use cases are possible? (Choose three answers)
Options:
Secure Internet Access (SIA)
Secure SaaS Access (SSA)
Secure Private Access (SPA)
Secure VPN Access (SVA)
Secure Browser Access (SBA)
Answer:
A, B, CExplanation:
According to theFortiSASE 7.6 Architecture Guideand theFCP - FortiSASE 24/25 Administratorstudy materials, the FortiSASE solution is structured around three primary pillars or "use cases" that address the security requirements of a modern distributed workforce.
Secure Internet Access (SIA) (Option A): This use case focus on protecting remote users as they browse the public internet. It utilizes a full cloud-delivered security stack includingWeb Filtering,DNS Filtering,Anti-Malware, andIntrusion Prevention (IPS)to ensure that users are protected from web-based threats regardless of their physical location.
Secure SaaS Access (SSA) (Option B): This use case addresses the security of cloud-based applications (like Microsoft 365, Salesforce, and Dropbox). It leveragesInline-CASB (Cloud Access Security Broker)to identify and control "Shadow IT"—unauthorized cloud applications used by employees—and appliesData Loss Prevention (DLP)to prevent sensitive information from being leaked into unsanctioned SaaS platforms.
Secure Private Access (SPA) (Option C): This use case provides secure, granular access to private applications hosted in on-premises data centers or private clouds. It can be achieved through two main methods:ZTNA (Zero Trust Network Access), which provides session-specific access based on identity and device posture, or throughSD-WAN integration, where the FortiSASE cloud acts as a spoke connecting to a corporate SD-WAN Hub.
Why other options are incorrect:
Secure VPN Access (SVA) (Option D): While SASE uses VPN technology (SSL or IPsec) as a transport for the Endpoint mode, "SVA" is not a formal curriculum-defined use case. The SASE framework is intended to evolve beyond traditional "Secure VPN Access" into the SIA and SPA models.
Secure Browser Access (SBA) (Option E): Although FortiSASE offersRemote Browser Isolation (RBI), it is considered a feature or a component of the broaderSecure Internet Access (SIA)use case rather than a separate, standalone use case in the core administrator curriculum.

