Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect Questions and Answers
You must add an Amazon Web Services (AWS) network access list (NACL) rule to allow SSH traffic to a subnet for temporary testing purposes. When you review the current inbound and outbound NACL rules, you notice that the rules with number 5 deny SSH and telnet traffic to the subnet.
What can you do to allow SSH traffic?
Refer to the exhibit.
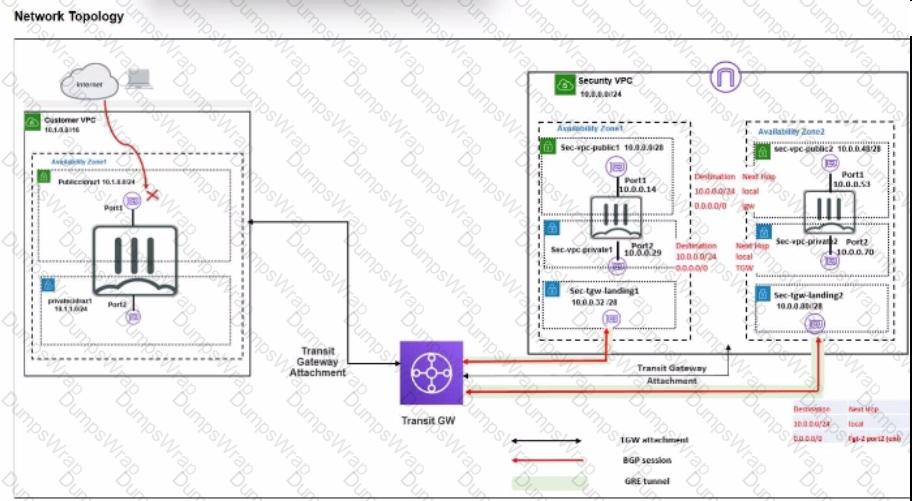
In your Amazon Web Services (AWS), you must allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet. However, your HTTPS connection to the FortiGate VM in the Customer VPC is not successful.
Also, you must ensure that the Customer VPC FortiGate VM sends all the outbound Internet traffic through the Security VPC.
How do you correct this issue with minimal configuration changes? (Choose three.)
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost.
Which solution meets the requirements?
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure. However, the SDN connector is failing on the connection.
What must the administrator do to correct this issue?
What are two main features in Amazon Web Services (AWS) network access control lists (NACLs)? (Choose two answers)
Refer to the exhibit.

Which FortiCNP policy type generated the finding shown in the exhibit? (Choose one answer)
Refer to the exhibit.
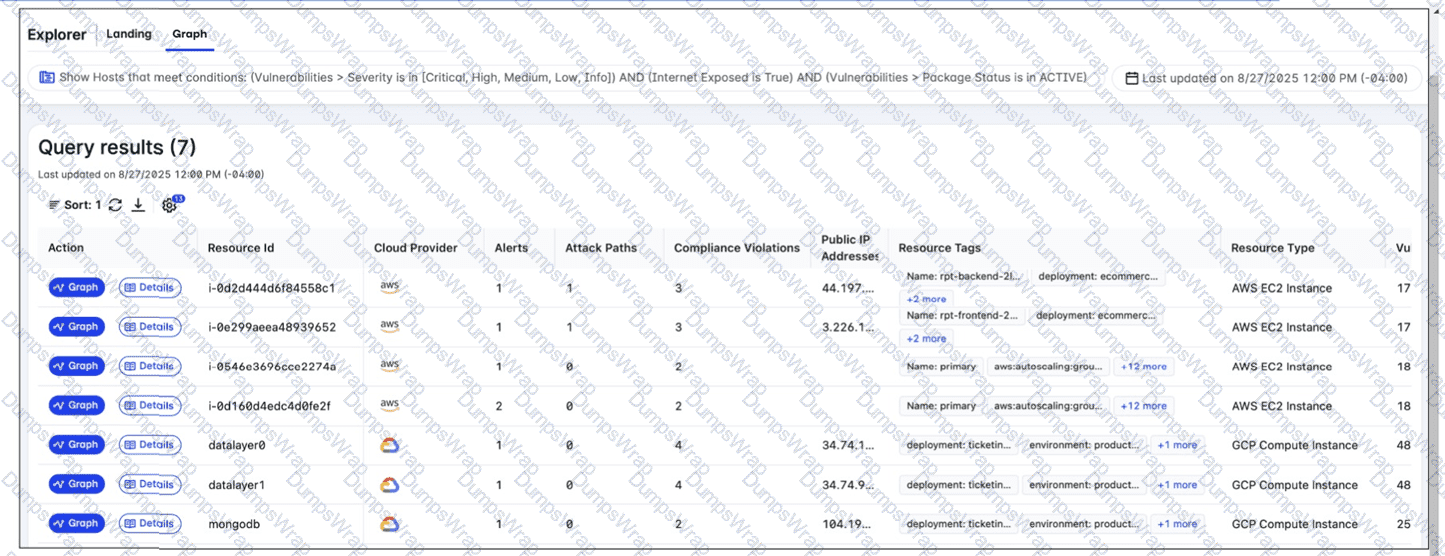
A FortiCNAPP administrator used the FortiCNAPP Explorer to reveal all hosts exposed to the internet that are running active packages with vulnerabilities of all severity levels. Why do only the first two results have an attack path? (Choose one answer)
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
Refer to the exhibit.
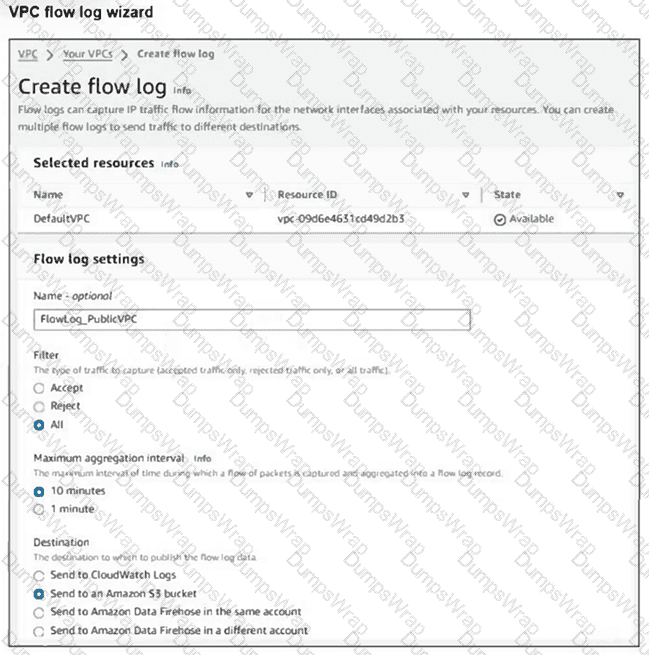
Your team notices an unusually high volume of traffic sourced at one of the organizations FortiGate EC2 instances. They create a flow log to obtain and analyze detailed information about this traffic. However, when they checked the log, they found that it included traffic that was not associated with the FortiGate instance in question.
What can they do to obtain the correct logs? (Choose one answer)
Refer to the exhibit.

You are managing an active-passive FortiGate HA cluster in AWS that was deployed using CloudFormation. You have created a change set to examine the effects of some proposed changes to the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
Your monitoring team reports performance issues with a web application hosted in Azure. You suspect that the bottleneck might be due to unexpected inbound traffic spikes.
Which method should you use to identify and analyze the traffic pattern?
Which statement about Transit Gateway (TGW) in Amazon Web Services (AWS) is true?
Refer to the exhibit.
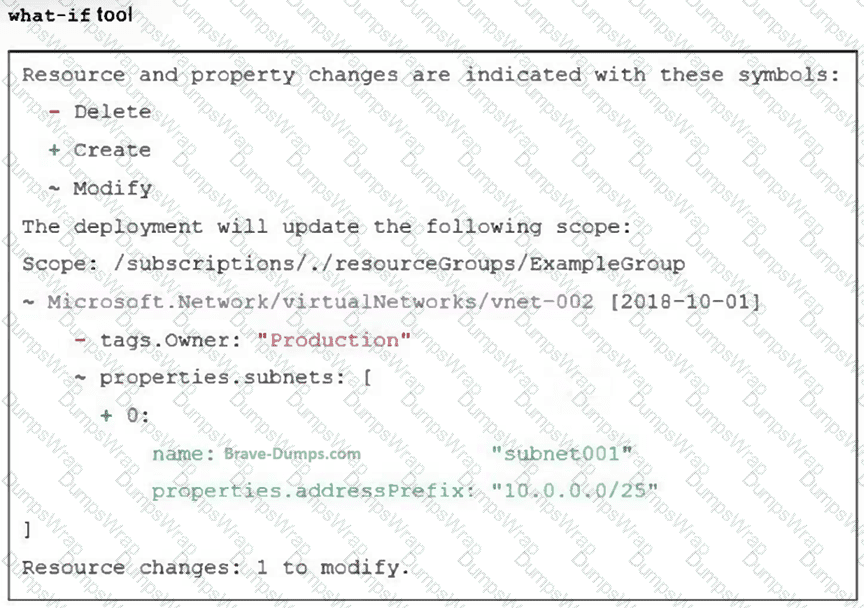
An administrator used the what-if tool to preview the changes to an Azure Bicep file. What will happen if the administrator applies these changes in Azure? (Choose one answer)
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
Refer to the exhibit.
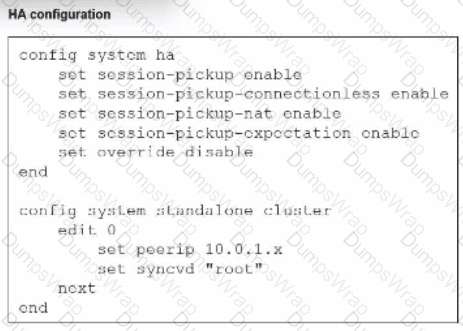
You deployed an HA active-active load balance sandwich with two FortiGate VMs in Microsoft Azure.
After the deployment, you prefer to use FGSP to synchronize sessions, and allow asymmetric return traffic. In the environment, FortiGate port 1 and port 2 are facing external and internal load balancers respectively.
What IP address must you use in the peerip configuration?

