Network Security Expert 8 Written Exam Questions and Answers
Refer to the exhibit showing a FortiView monitor screen.
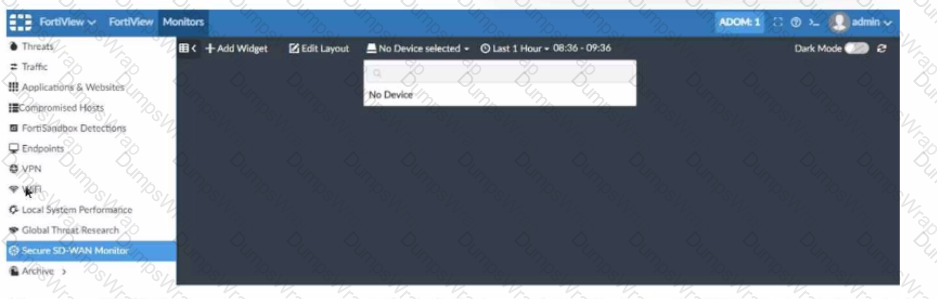
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection.
What can cause this issue?
You are designing a setup where the FortiGate device is connected to two upstream ISPs using BGP. Part of the requirement is that you must be able to refresh the route advertisements manually without disconnecting the BGP neighborships.
Which feature must you enable on the BGP neighbors to accomplish this goal?
Refer to the exhibit.
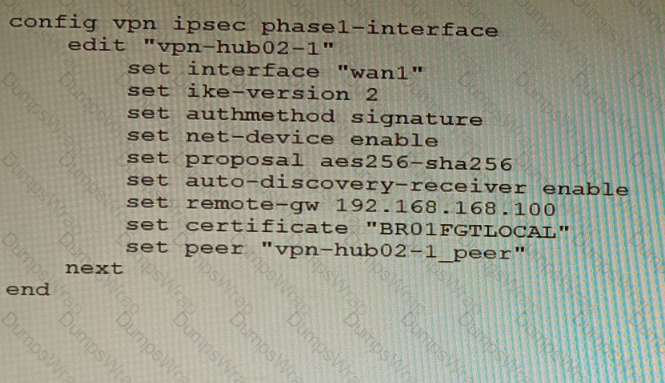
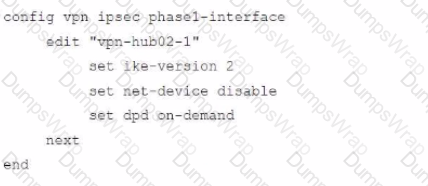
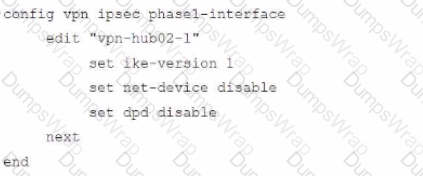
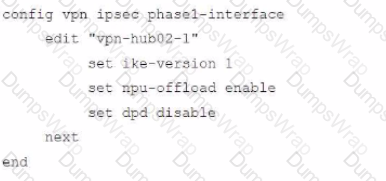
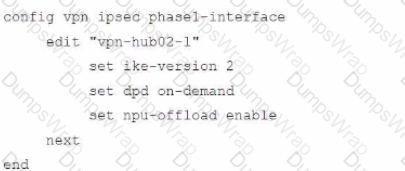
To facilitate a large-scale deployment of SD-WAN/ADVPN with FortiGate devices, you are tasked with configuring the FortiGate devices to support injecting of IKE routes on the ADVPN shortcut tunnels.
Which three commands must be added or changed to the FortiGate spoke config vpn ipsec phasei-interface options referenced in the exhibit for the VPN interface to enable this capability? (Choose three.)
Refer to The exhibit, which shows a topology diagram.
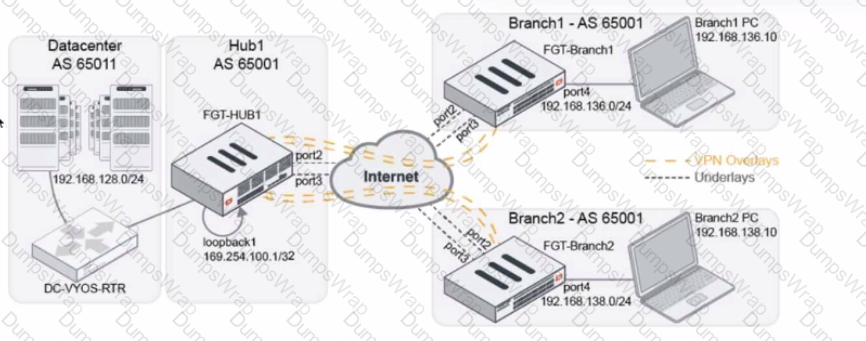
A customer wants to use SD-WAN for traffic generated from the data center towards Branches. SD-WAN on HUB should follow the underlay condition on each Branch and the solution should be scalable for hundreds of Branches.
Which SD WAN-Rules strategy should be used?
Refer to the CLI output:
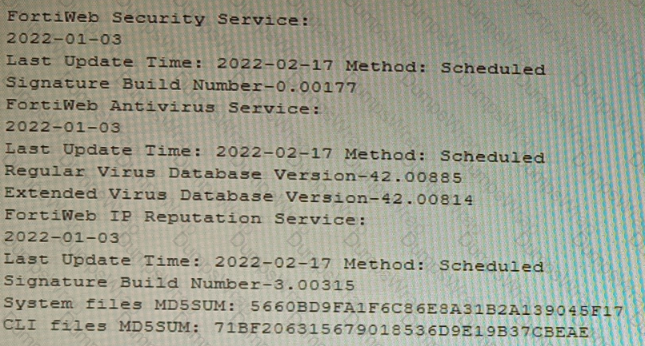
Given the information shown in the output, which two statements are correct? (Choose two.)
A customer has FortiAP devices in three branch offices managed from a FortiGate in the HQ. Each FortiAP is connected to a dedicated management VLAN.
The customer wants the users connected to the FortiAP SSIDs to use the branch local internet connection, but each branch uses a different VLAN ID for the bridge. HQ users travel to different branches and connect to the same SSID.
Which configuration option will solve this requirement?
Refer to the exhibit.
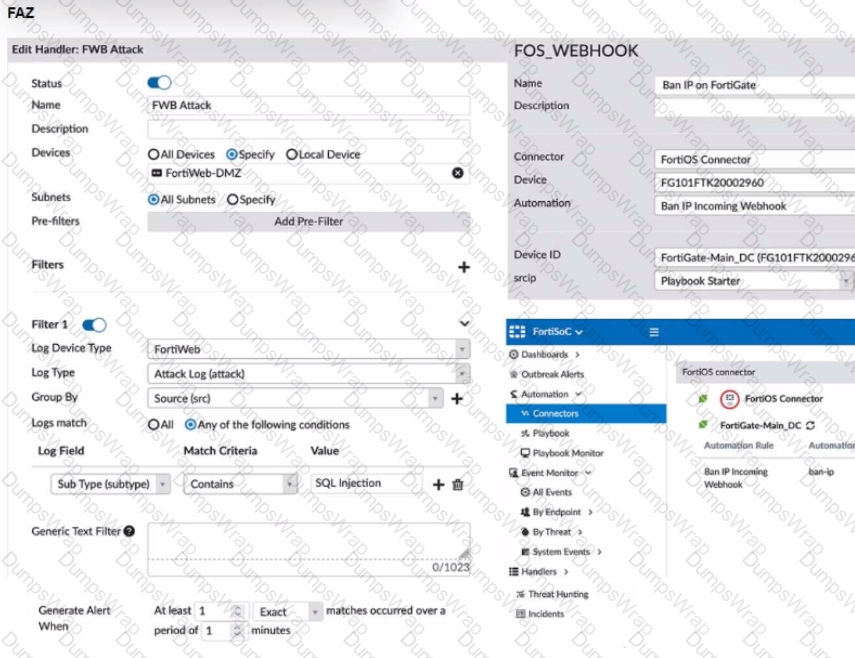
A customer is trying to setup a Playbook automation using a FortiAnalyzer, FortiWeb and FortiGate. The intention is to have the FortiGate quarantine any source of SQL Injection detected by the FortiWeb. They got the automation stitch to trigger on the FortiGate when simulating an attack to their website, but the quarantine object was created with the IP 0.0.0.0. Referring to the configuration and logs in the exhibits, which two statements are true? (Choose two.)
Refer to the exhibit.
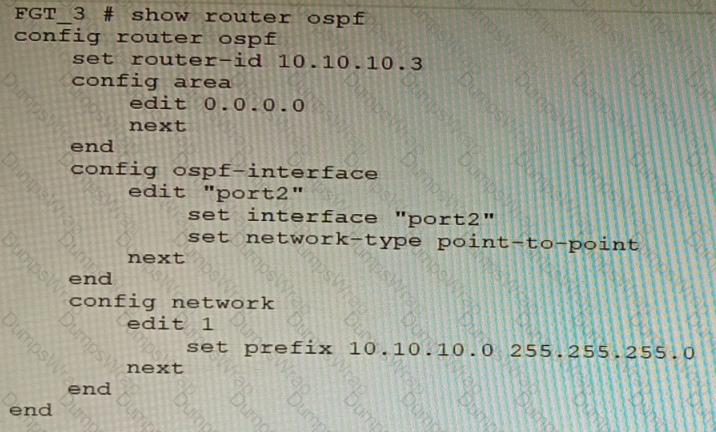
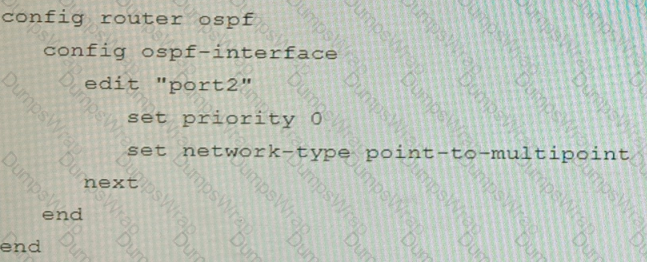
You are operating an internal network with multiple OSPF routers on the same LAN segment. FGT_3 needs to be added to the OSPF network and has the configuration shown in the exhibit. FGT_3 is not establishing any OSPF connection.
What needs to be changed to the configuration to make sure FGT_3 will establish OSPF neighbors without affecting the DR/BDR election?
A)
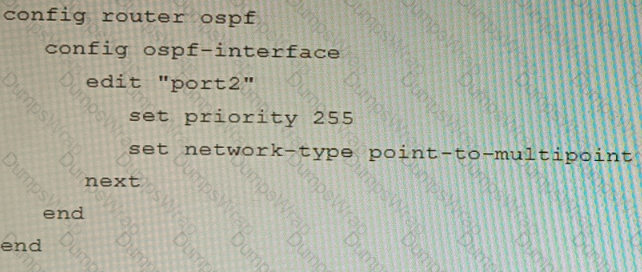
B)
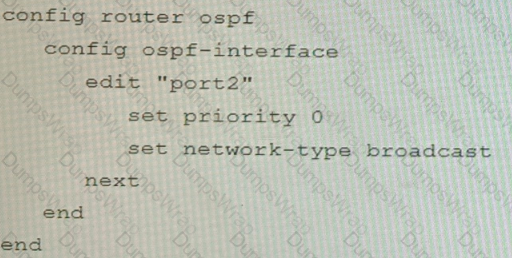
C)
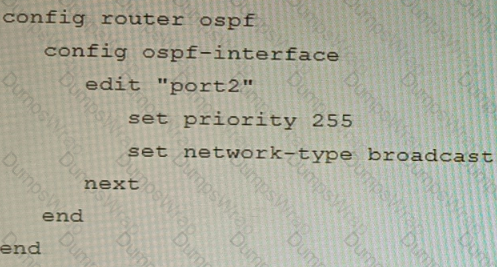
D)
Refer to the exhibits.
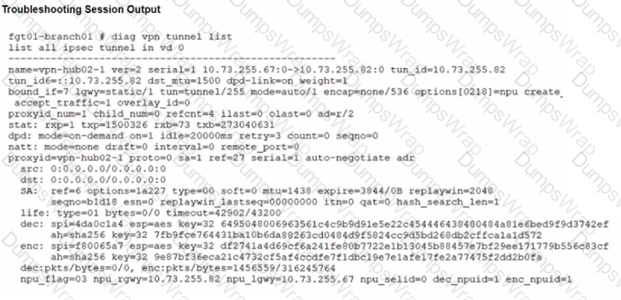
A customer is trying to restore a VPN connection configured on a FortiGate. Exhibits show output during a troubleshooting session when the VPN was working and the current baseline VPN configuration.
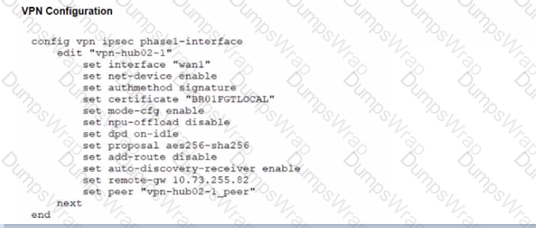
Which configuration parameters will restore VPN connectivity based on the diagnostic output?
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
Refer to the exhibits.
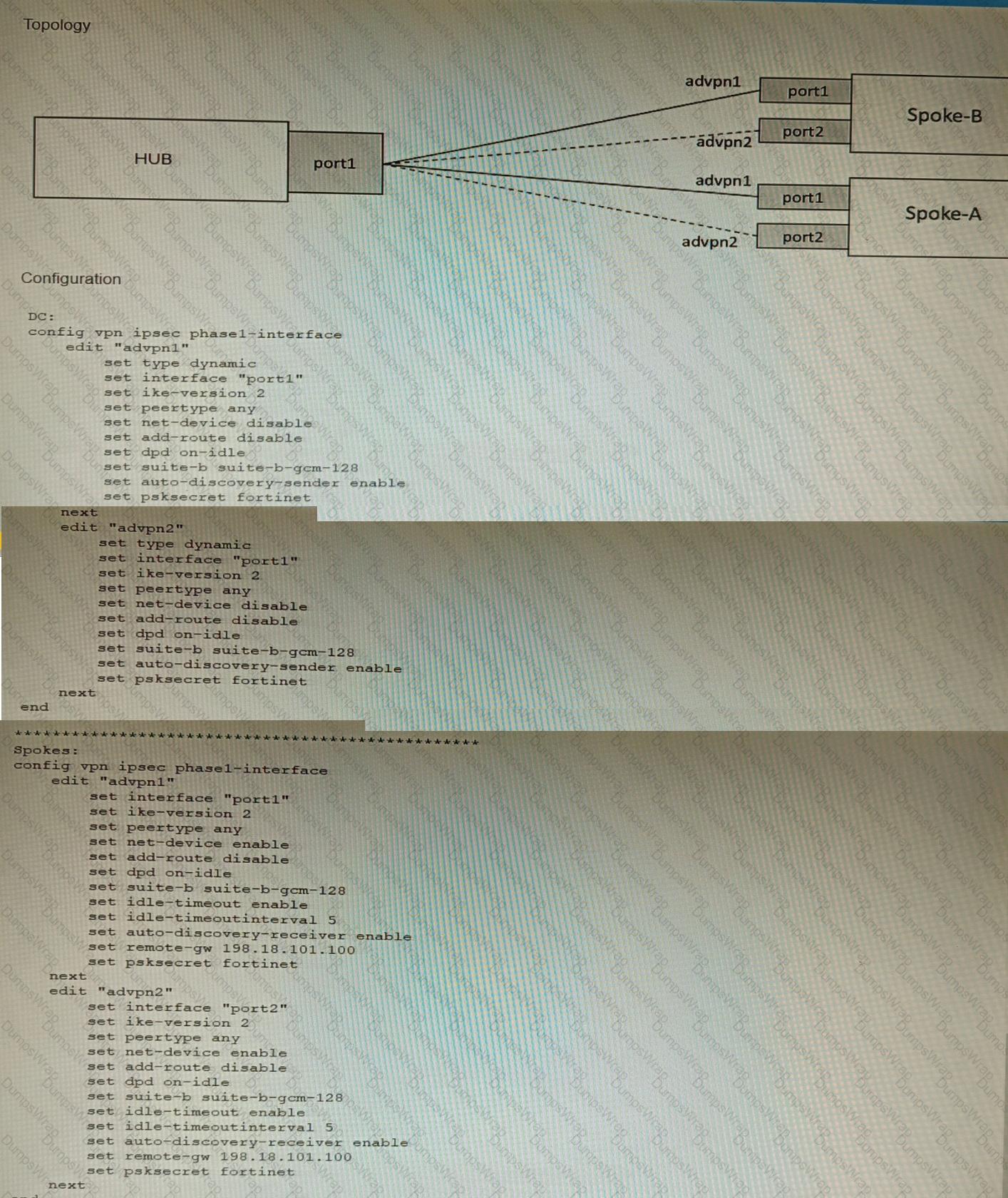
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
A FortiGate must be configured to accept VoIP traffic which will include session initiation protocol (SIP) traffic. Which statement about the VoIP configuration options is correct?
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster. Which statement about this solution is true?
Refer to the exhibit.
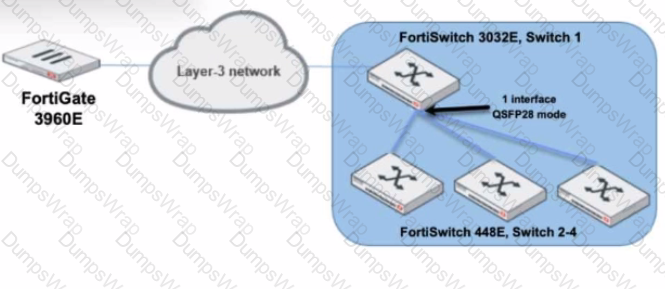
You are managing a FortiSwitch 3032E that is managed by FortiLink on a FortiGate 3960E. The 3032E is heavily utilized and there is only one port free.
The requirement is to add an additional three FortiSwitch 448E devices with 10Gbps SFP+ connectivity directly to the 3032E. The plan is to use split port (phy-mode) with QSFP28 mode to connect the new 448E switches.
In this scenario, which statement about the switch deployment is correct?
Refer to the exhibit showing a firewall policy configuration.
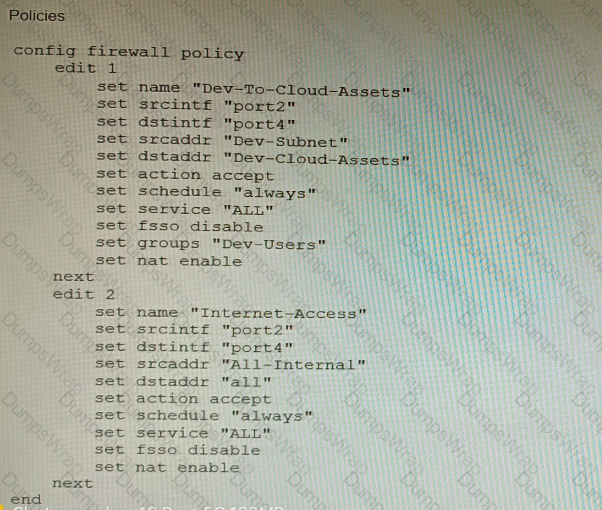
To prevent unauthorized access of their cloud assets, an administrator wants to enforce authentication on firewall policy ID 1.
What change does the administrator need to make?

Refer to the exhibit.
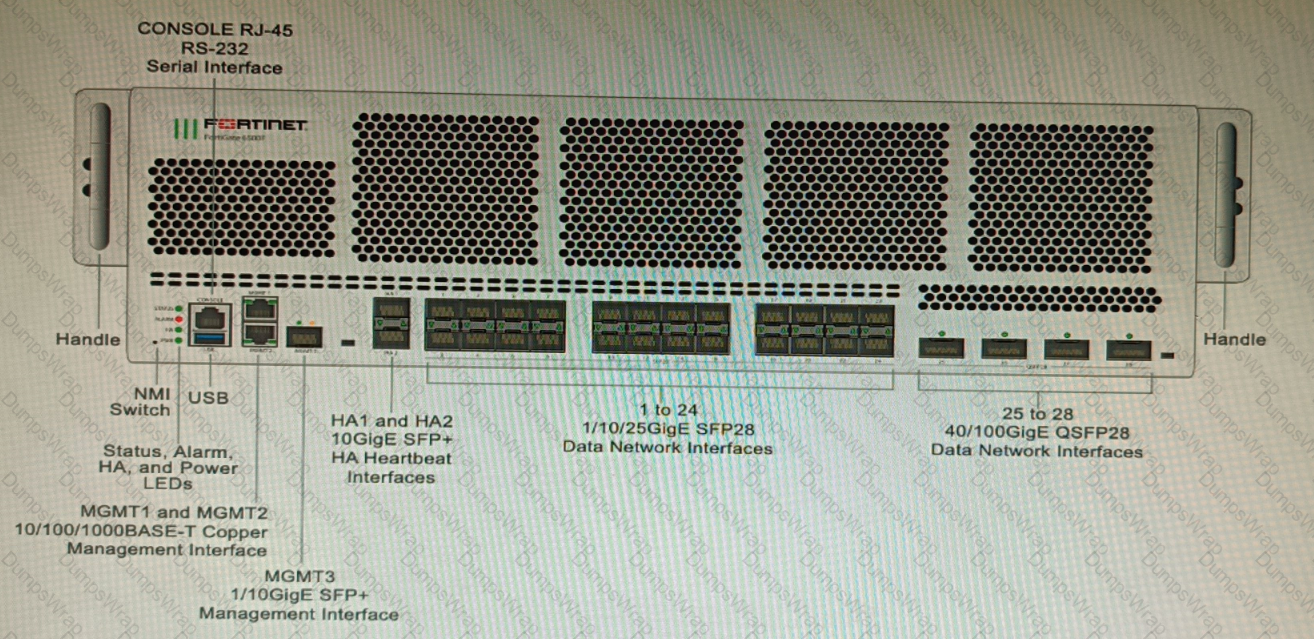
You are deploying a FortiGate 6000F. The device should be directly connected to a switch. In the future, a new hardware module providing higher speed will be installed in the switch, and the connection to the FortiGate must be moved to this higher-speed port.
You must ensure that the initial FortiGate interface connected to the switch does not affect any other port when the new module is installed and the new port speed is defined.
How should the initial connection be made?
You are migrating the branches of a customer to FortiGate devices. They require independent routing tables on the LAN side of the network.
After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments.
Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the Online Certificate Status Protocol (OCSP) server.
Part of the FortiGate configuration is shown below:
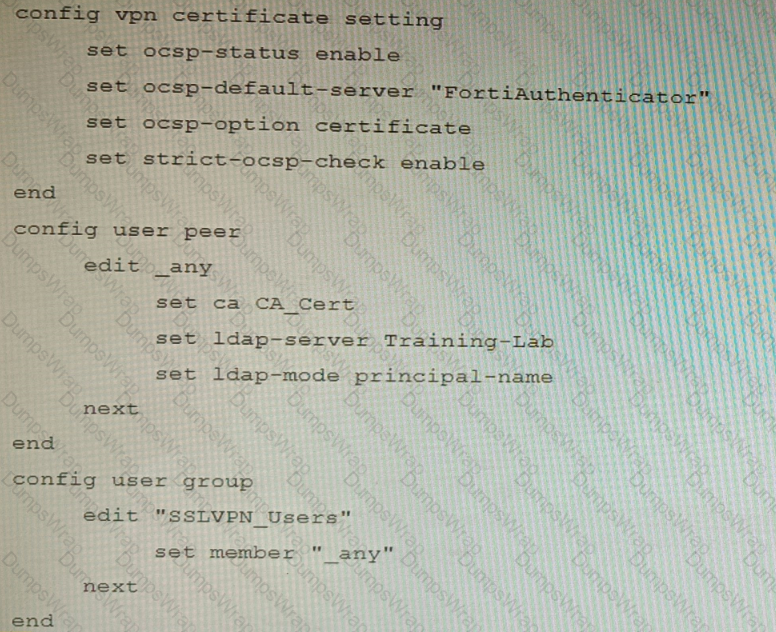
Based on this configuration, which two statements are true? (Choose two.)
An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
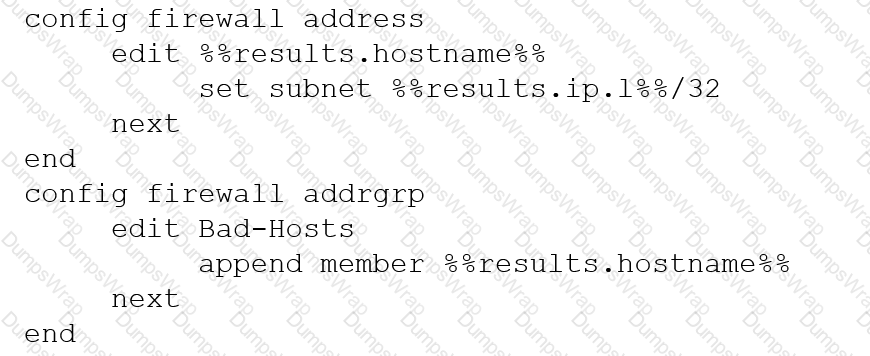
Refer to the exhibits.
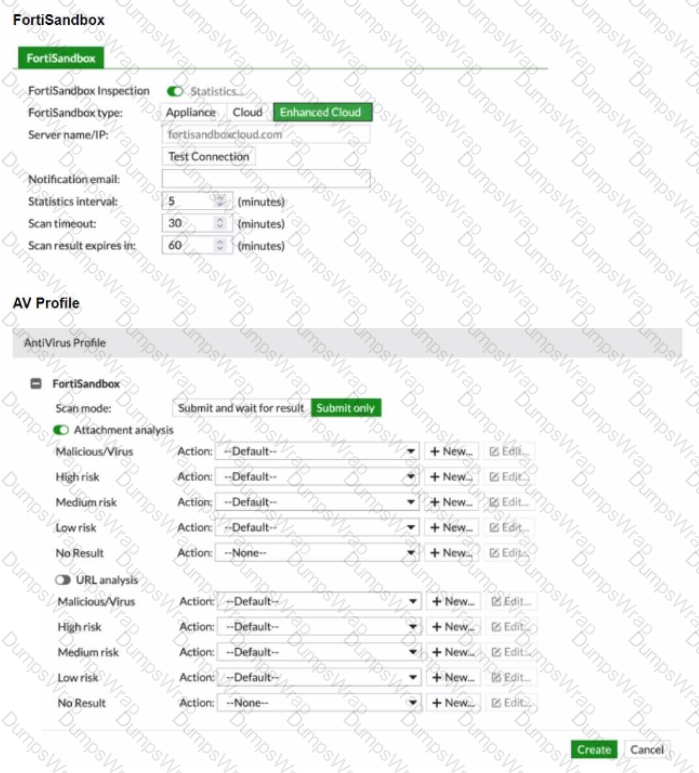
You must integrate a FortiMail and FortiSandbox Enhanced Cloud solution for a customer who is concerned about the e-mails being delayed for too long.
According to the configuration shown in the exhibits, which would be an expected behavior?
Refer to the exhibits, which show a firewall policy configuration and a network topology.
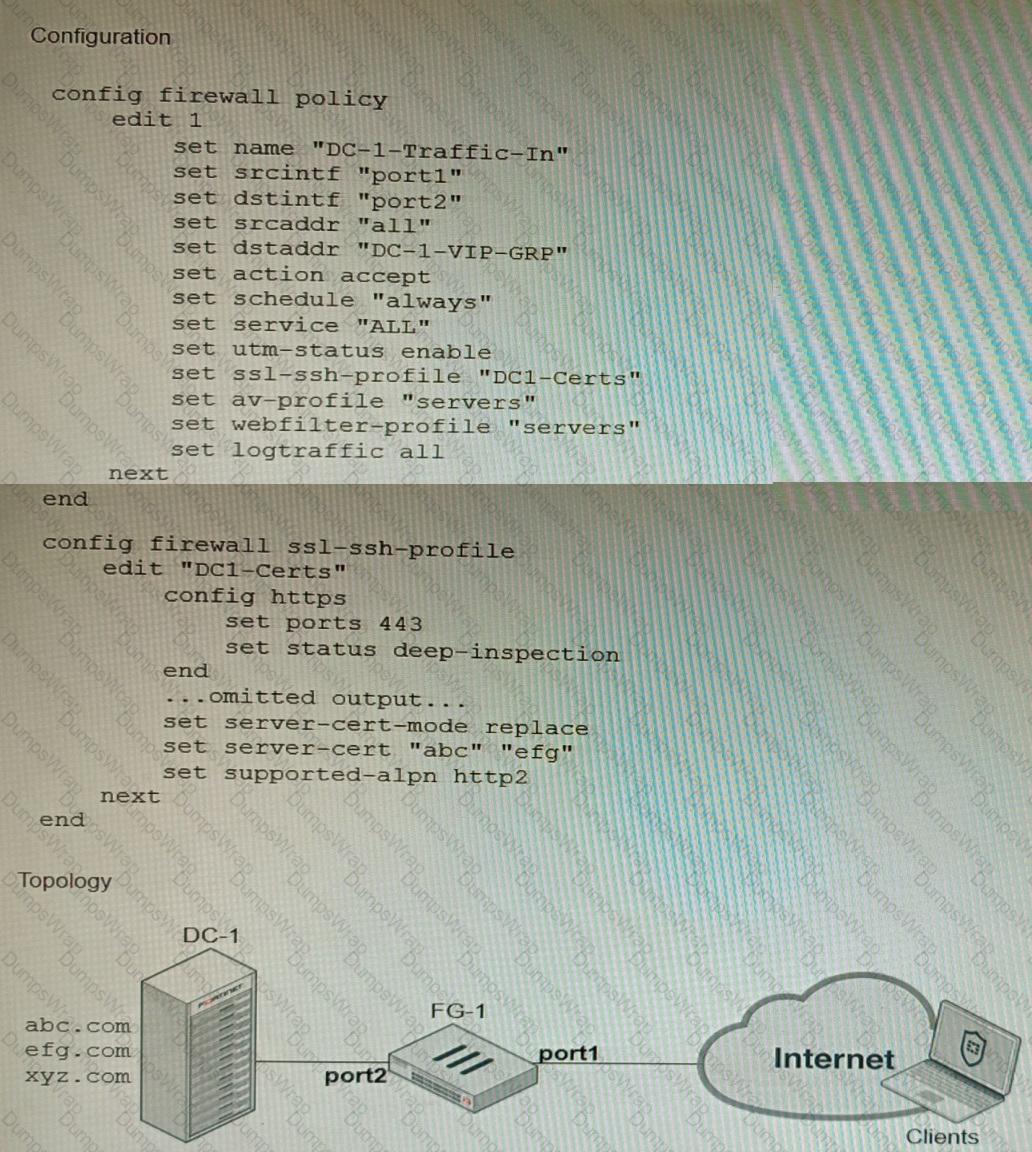
An administrator has configured an inbound SSL inspection profile on a FortiGate device (FG-1) that is protecting a data center hosting multiple web pages-Given the scenario shown in the exhibits, which certificate will FortiGate use to handle requests to xyz.com?
Refer to the exhibit showing the history logs from a FortiMail device.
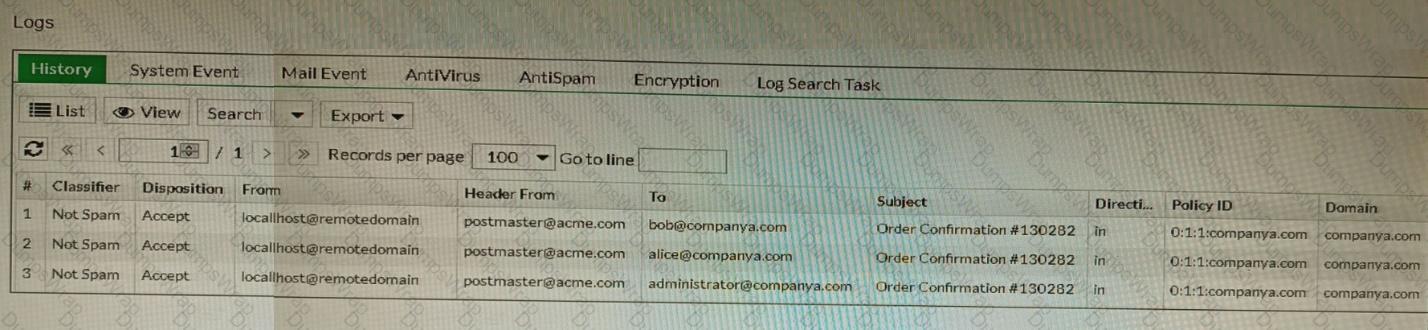
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
Refer to the exhibits.
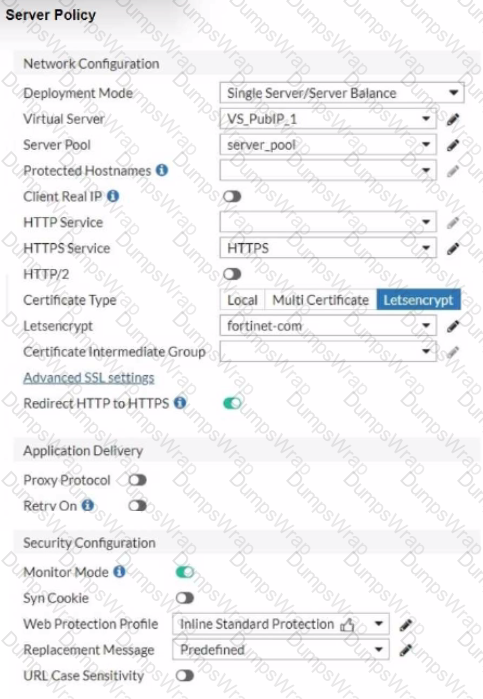
You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.

Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)
You are performing a packet capture on a FortiGate 2600F with the hyperscale licensing installed. You need to display on screen all egress/ingress packets from the port16 interface that have been offloaded to the NP7.
Which three commands need to be run? (Choose three.)
Refer to the exhibits.

During the implementation of a Fortinet Security Fabric configuration, CLI commands were issued in the order shown in the exhibit. On the next day, the local admin for FGTC issues the following command:
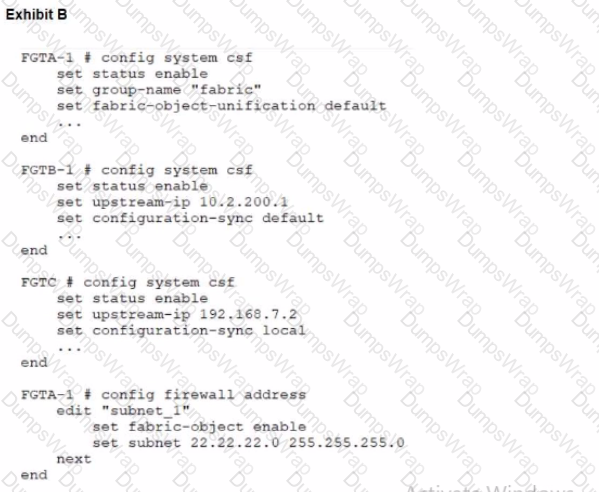
FGTC # config system csf
set configuration-sync default
end
In this scenario, which outcome is true regarding the "subnet_1" firewall address object on FGTC?
Review the VPN configuration shown in the exhibit.
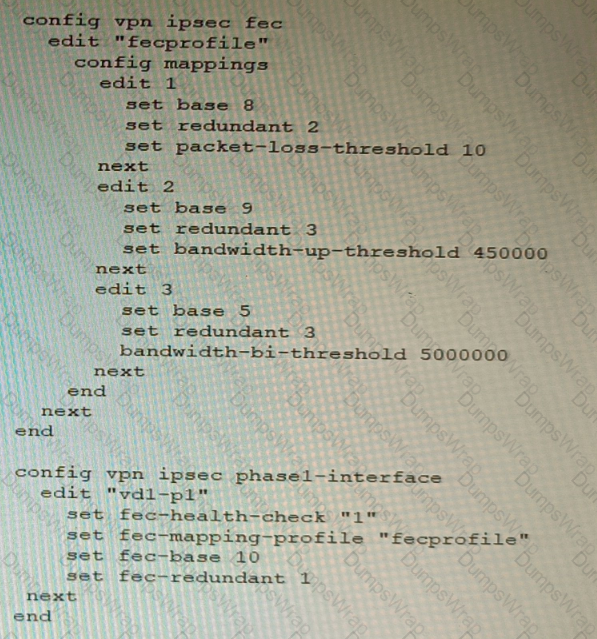
What is the Forward Error Correction behavior if the SD-WAN network traffic download is 500 Mbps and has 8% of packet loss in the environment?
Refer to the exhibit of a FortiNAC configuration.
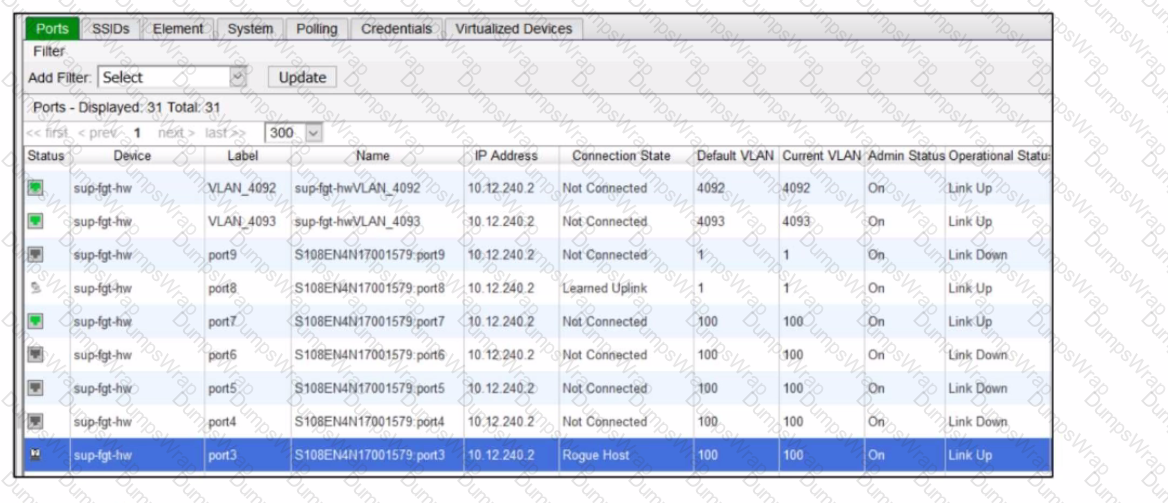
In this scenario, which two statements are correct? (Choose two.)
Refer to the exhibit.
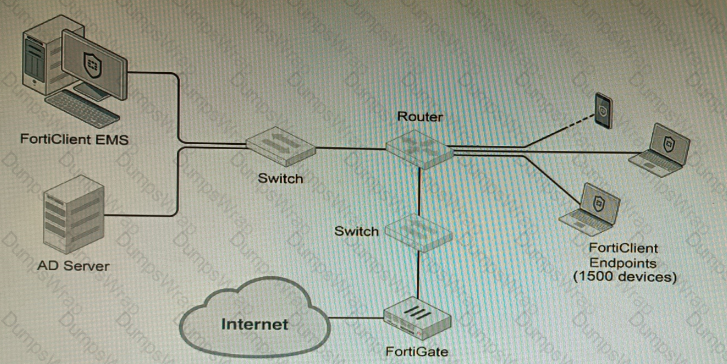
A customer wants FortiClient EMS configured to deploy to 1500 endpoints. The deployment will be integrated with FortiOS and there is an Active Directory server.
Given the configuration shown in the exhibit, which two statements about the installation are correct? (Choose two.)
You are responsible for recommending an adapter type for NICs on a FortiGate VM that will run on an ESXi Hypervisor. Your recommendation must consider performance as the main concern, cost is not a factor. Which adapter type for the NICs will you recommend?
You have configured a Site-to-Site IPsec VPN tunnel between a FortiGate and a third-party device but notice that one of the error counters on the tunnel interface keeps increasing.
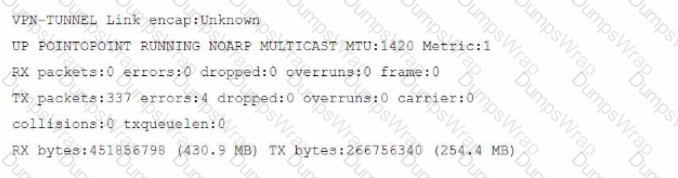
Which two configuration options can resolve this problem? (Choose two.)
Refer to the exhibits, which show a network topology and VPN configuration.
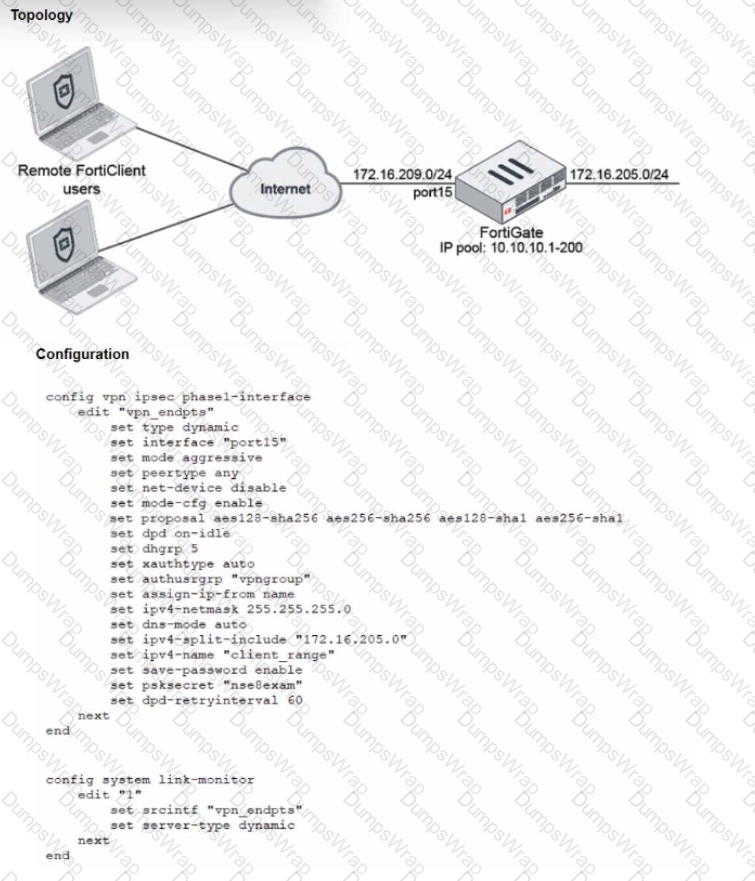
A network administrator has been tasked with modifying the existing dial-up IPsec VPN infrastructure to detect the path quality to the remote endpoints.
After applying the configuration shown in the configuration exhibit, the VPN clients can still connect and access the protected 172.16.205.0/24 network, but no SLA information shows up for the client tunnels when issuing the diagnose sys link-monitor tunnel all command on the FortiGate CLI.
What is wrong with the configuration?