Aruba Certified Network Security Professional Exam Questions and Answers
You are using Wireshark to view packets captured from HPE Aruba Networking infrastructure, but you are not sure that the packets are displaying correctly.
In which circumstance does it make sense to ensure that Wireshark has GRE enabled as one of its analyzed protocols?
What is a typical use case for using HPE Aruba Networking ClearPass Onboard to provision devices?
A company wants you to create a custom device fingerprint on CPPM with rules for profiling a group of specialized devices. What is one requirement?
You need to set up an HPE Aruba Networking VIA solution for a customer who needs to support 2100 remote employees. The customer wants employees to
download their VIA connection profile from the VPNC. Only employees who authenticate with their domain credentials to HPE Aruba Networking ClearPass Policy
Manager (CPPM) should be able to download the profile. (A RADIUS server group for CPPM is already set up on the VPNC.)
How do you configure the VPNC to enforce that requirement?
You are setting up HPE Aruba Networking SSE. Which use case requires you to apply a non-default device posture in a rule?
A company needs to enforce 802.1X authentication for its Windows domain computers to HPE Aruba Networking ClearPass Policy Manager (CPPM). The
company needs the computers to authenticate as both machines and users in the same session.
Which authentication method should you set up on CPPM?
Refer to Exhibit:
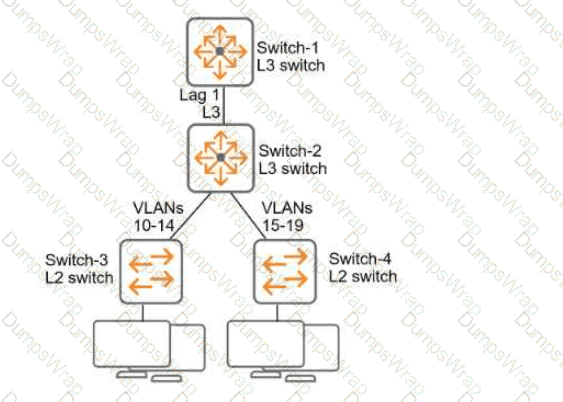
All of the switches in the exhibit are AOS-CX switches.
What is the preferred configuration on Switch-2 for preventing rogue OSPF routers in this network?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI) and has integrated the
two. CPDI admins have created a tag. CPPM admins have created rules that use that tag in the wired 802.1X and wireless 802.1X services' enforcement policies.
The company requires CPPM to apply the tag-based rules to a client directly after it learns that the client has that tag.
What is one of the settings that you should verify on CPPM?
An AOS-CX switch has this admin user account configured on it:
netadmin in the operators group.
You have configured these commands on an AOS-CX switch:
tacacs-server host cp.example.com key plaintext &12xl,powmay7855
aaa authentication login ssh group tacacs local
aaa authentication allow-fail-through
A user accesses the switch with SSH and logs in as netadmin with the correct password. When the switch sends a TACACS+ request to the ClearPass server at cp.example.com, the server does not send a response. Authentication times out.
What happens?
You manage AOS-10 APs with HPE Aruba Networking Central. A role is configured on these APs with these rules (in order):
Allow UDP on port 67 to any destination
Allow any to network 10.1.4.0/23
Deny any to network 10.1.0.0/18 + log
Deny any to network 10.0.0.0/8
Allow any to any destination
You add this new rule immediately before rule 4:
Deny SSH to network 10.1.0.0/21 + denylist
After this change, what happens when a client assigned to this role sends SSH traffic to 10.1.7.12?
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to further protect itself from internal threats. What is one solution that you can recommend?
A company wants to use the HPE Aruba Networking ClearPass OnGuard agent to assign posture to clients.
How do you define the conditions by which a client receives a particular posture?
A company needs you to integrate HPE Aruba Networking ClearPass Policy Manager (CPPM) with HPE Aruba Networking ClearPass Device Insight (CPDI). What is one task you should do to prepare?
You have configured an AOS-CX switch to implement 802.1X on edge ports. Assume ports operate in the default auth-mode. VolP phones are assigned to the
"voice" role and need to send traffic that is tagged for VLAN 12.
Where should you configure VLAN 12?
A company has HPE Aruba Networking Central-managed APs. The company wants to block all clients connected through the APs from using YouTube.
Which steps should you take?
A company has HPE Aruba Networking infrastructure devices. The devices authenticate clients to HPE Aruba Networking ClearPass Policy Manager (CPPM). You want CPPM to track information about clients, such as their IP addresses and their network bandwidth utilization. What should you set up on the network infrastructure devices to help that happen?
You need to use "Tips:Posture" conditions within an 802.1X service's enforcement policy.
Which guideline should you follow?
You have created this rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) service's enforcement policy: IF Authorization [Endpoints Repository]
Conflict EQUALS true THEN apply "quarantine_profile"
What information can help you determine whether you need to configure cluster-wide profiler parameters to ignore some conflicts?
You are setting up HPE Aruba Networking SSE to prohibit users from uploading and downloading files from Dropbox. What is part of the process?
The security team needs you to show them information about MAC spoofing attempts detected by HPE Aruba Networking ClearPass Policy Manager (CPPM).
What should you do?
A company wants to apply role-based access control lists (ACLs) on AOS-CX switches, which are implementing authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants to centralize configuration as much as possible. Which correctly describes your options?
A company has wired VolP phones, which transmit tagged traffic and connect to AOS-CX switches. The company wants to tunnel the phones' traffic to an HPE
Aruba Networking gateway for applying security policies.
What is part of the correct configuration on the AOS-CX switches?
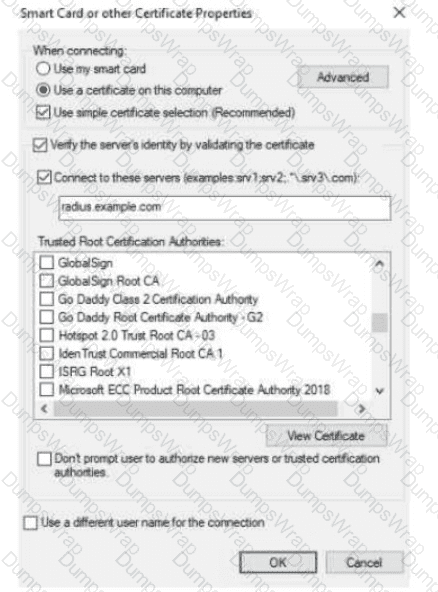
The exhibit shows the 802.1X-related settings for Windows domain clients. What should admins change to make the settings follow best security practices?
What correctly describes an HPE Aruba Networking AP's Device (TPM) certificate?
A company has AOS-CX switches and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants switches to implement 802.1X
authentication to CPPM and download user roles.
What is one task that you must complete on the switches to support this use case?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. The company wants CPPM to control which commands managers are allowed to enter.
Which service must you add to the managers' TACACS+ enforcement profile?
What is one benefit of integrating HPE Aruba Networking ClearPass Policy Manager (CPPM) with third-party solutions such as Mobility Device Management (MDM) and firewalls?
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy
Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to
further protect itself from internal threats.
What is one solution that you can recommend?
A company is using HPE Aruba Networking Central SD-WAN Orchestrator to establish a hub-spoke VPN between branch gateways (BGWs) at 1164 site and VPNCs at multiple data centers. What is part of the configuration that admins need to complete?
Which issue can an HPE Aruba Networking Secure Web Gateway (SWG) solution help customers address?
Your company wants to implement Tunneled EAP (TEAP).
How can you set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to enforce certificated-based authentication for clients using TEAP?
What is one use case that companies can fulfill using HPE Aruba Networking ClearPass Policy Manager’s (CPPM’s) Device Profiler?
A ClearPass Policy Manager (CPPM) service includes these settings:
Role Mapping Policy:
Evaluate: Select first
Rule 1 conditions:
Authorization:AD:Groups EQUALS Managers
Authentication:TEAP-Method-1-Status EQUALS Success
Rule 1 role: manager
Rule 2 conditions:
Authentication:TEAP-Method-1-Status EQUALS Success
Rule 2 role: domain-comp
Default role: [Other]
Enforcement Policy:
Evaluate: Select first
Rule 1 conditions:
Tips Role EQUALS manager AND Tips Role EQUALS domain-comp
Rule 1 profile list: domain-manager
Rule 2 conditions:
Tips Role EQUALS manager
Rule 2 profile list: manager-only
Rule 3 conditions:
Tips Role EQUALS domain-comp
Rule 3 profile list: domain-only
Default profile: [Deny access]
A client is authenticated by the service. CPPM collects attributes indicating that the user is in the Contractors group, and the client passed both TEAP methods.
Which enforcement policy will be applied?
A company has Aruba APs that are controlled by Central and that implement WIDS. When you check WIDS events, you see a "detect valid SSID misuse" event. What can you interpret from this event, and what steps should you take?
Refer to the exhibit:
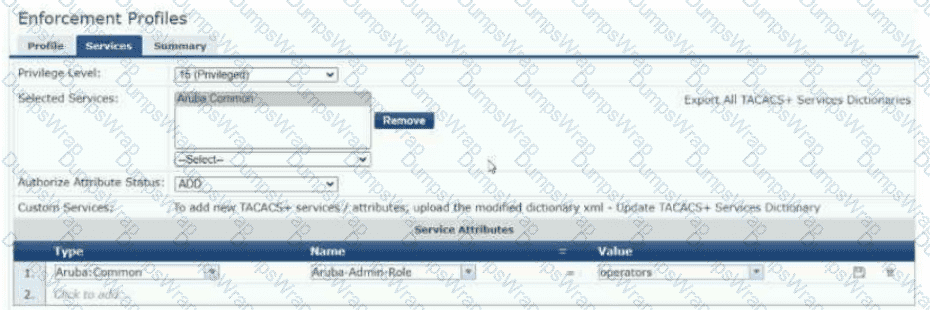
The exhibit shows the TACACS+ enforcement profile that HPE Aruba Networking ClearPass Policy Manager (CPPM) assigns to a manager. When this manager logs into an AOS-CX switch, what does the switch do?
Refer to the Exhibit:
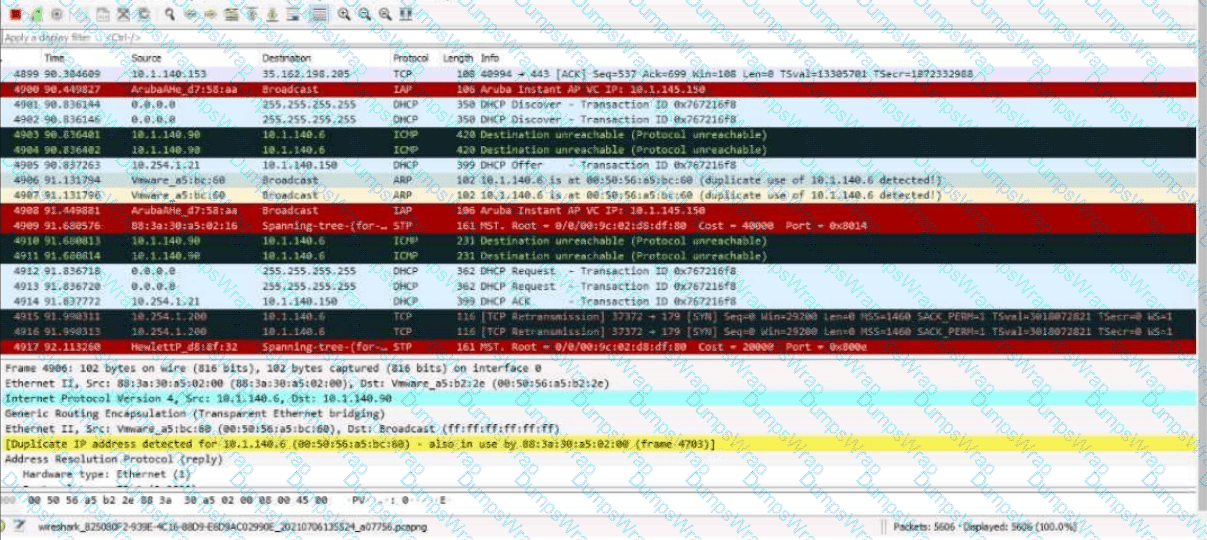
These packets have been captured from VLAN 10. which supports clients that receive their IP addresses with DHCP.
What can you interpret from the packets that you see here?
These packets have been captured from VLAN 10, which supports clients that receive their IP addresses with DHCP. What can you interpret from the packets that you see here?
What is a use case for the HPE Aruba Networking ClearPass OnGuard dissolvable agent?
HPE Aruba Networking ClearPass Policy Manager (CPPM) uses a service to authenticate clients. You are now adding the Endpoints Repository as an
authorization source for the service, and you want to add rules to the service's policies that apply different access levels based, in part, on a client's device
category. You need to ensure that CPPM can apply the new correct access level after discovering new clients' categories.
What should you enable on the service?
A company uses both HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI). What is one way integrating the two solutions can help the company implement Zero Trust Security?
You are proposing HPE Aruba Networking ZTNA to an organization that currently uses a third-party, IPsec-based client-to-site VPN.
What is one advantage of ZTNA that you should emphasize?

