HCIA-Security V4.0 Exam Questions and Answers
____- The goal is to provide a rapid, composed and effective response in emergency situations, thereby enhancing the ability of the business to recover immediately from a disruptive event.[fill in the blank]*
Digital envelope technology means that the sender uses the receiver's public key to encrypt the data, and then sends the ciphertext to the receiver ( )[Multiple choice]*
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution. 1. Inhibition stage, 2. recovery phase, 3. Detection stage, 4. eradication phase[fill in the blank]*
Using the ___ method of the Web proxy, the virtual gateway will encrypt the real URL that the user wants to access, and can adapt to different terminal types.[fill in the blank]*
Data monitoring can be divided into two types: active analysis and passive acquisition.
Which of the following NAT technologies can implement a public network address to provide source address translation for multiple private network addresses ( )*
Which of the following attack methods is to construct special SQL statements and submit sensitive information to exploit program vulnerabilities
IKE SA is a one-way logical connection, and only one IKE SA needs to be established between two peers.
SSL VPN is a VPN technology that realizes remote secure access through SSL protocol. Which of the following software must be installed when using SSL VPN?
Which of the following descriptions about the main implementation of single sign-on is wrong? ( )[Multiple choice]*
As shown, in transmission mode, which of the following locations should the AH header be inserted in?
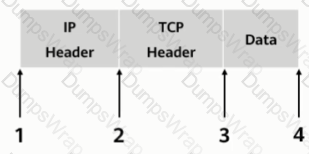
Which of the following protocols is a file transfer protocol?
Which of the following operating modes does NTP support?

