HCIP-Security V4.0 Exam Questions and Answers
Which of the following statements is false about the ATIC system architecture?
When a user accesses the virtual gateway, the user can access the SSL VPN only after the user terminal passes the host check policy.
Which of the following parameters is not required for an IKE proposal?
*In the data filtering profile on the firewall, keyword group "Keyword" is invoked in the upload direction of HTTP applications, the action is block, and the keyword group is invoked in the security policy. Given this, if the regular expression "b.d" is configured in the keyword group "Keyword,” which of the following texts can be posted by internal employees on the forum?
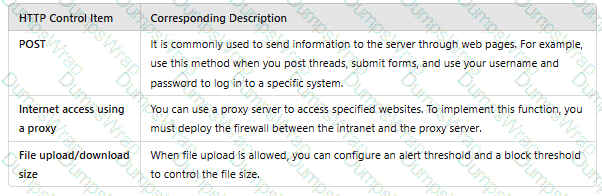
Match the HTTP control items with the corresponding descriptions.

On a WLAN where the WAC has Portal authentication configured, VLAN authorization can be implemented with no additional configuration required. After Portal authentication is complete, the WAC forwards STA traffic based on the authorized VLANs.
Which of the following statements is false about RADIUS and HWTACACS?
Multiple links can be deployed at the egress of an enterprise network to improve network reliability.
Which of the following statements is false about the restrictions on configuring bandwidth profiles in parent and child policies on a firewall?
Network Access Control (NAC) is an end-to-end security control technology that works in combination with AAA to implement access authentication. Which of the following statements about NAC and AAA are true?(Select All that Apply)
The figure shows the defense mechanism of an HTTP flood attack. Which source IP detection technology is displayed in the figure?

HWTACACS is a centralized information exchange protocol based on the client/server structure. It uses UDP for transmission and performs authentication, authorization, and accounting for users accessing the Internet through Point-to-Point Protocol (PPP) or Virtual Private Dial-up Network (VPDN) and administrative users logging in to devices.
The Nginx application is deployed on a Linux host. By checking Nginx logs, O&M engineers can obtain the complete URL information submitted by users and determine whether the Linux host is under SQL injection attacks.
: 51 DRAG DROP
Match the description about virtual systems and VPN instances.

Authentication rules configured on iMaster NCE-Campus support multiple matching conditions, such as matching account information, SSID information, and terminal IP address ranges, so that different authentication rules can be executed for different users.
In the figure, if 802.1X authentication is used for wired users on the network, the network admission device and terminals must be connected through a Layer 2 network.
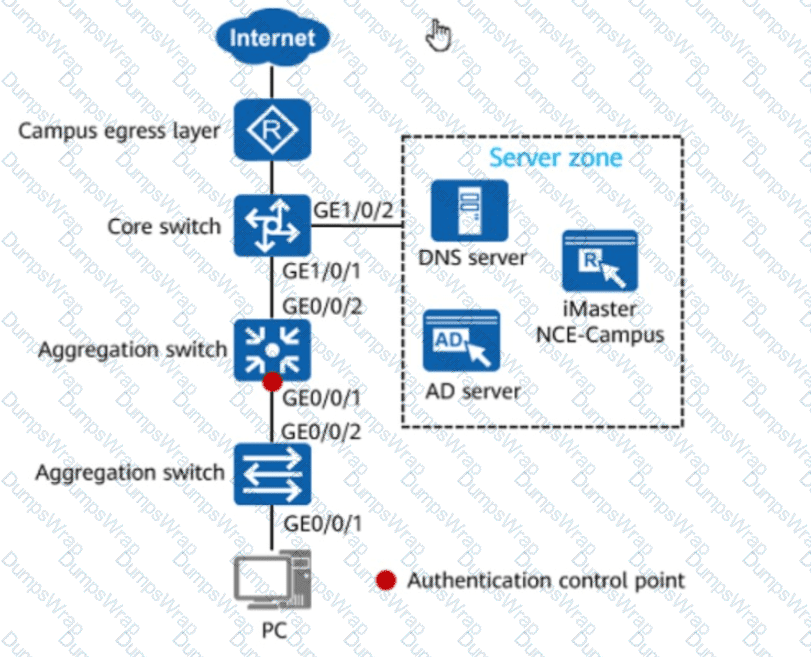
Options:
Which of the following statements are true about SYN scanning attacks?(Select All that Apply)
In SSL VPN, the firewall performs access authorization and control based on which of the following dimensions?


 A screenshot of a computer error message
AI-generated content may be incorrect.
A screenshot of a computer error message
AI-generated content may be incorrect.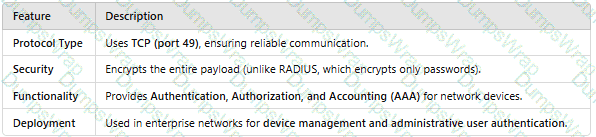 A screenshot of a computer
AI-generated content may be incorrect.
A screenshot of a computer
AI-generated content may be incorrect.
