HCIP-Datacom-Campus Network Planning and Deployment V1.5 Questions and Answers
(The Huawei CloudCampus Solution divides the network architecture into three layers: network layer, management layer, and application layer.)
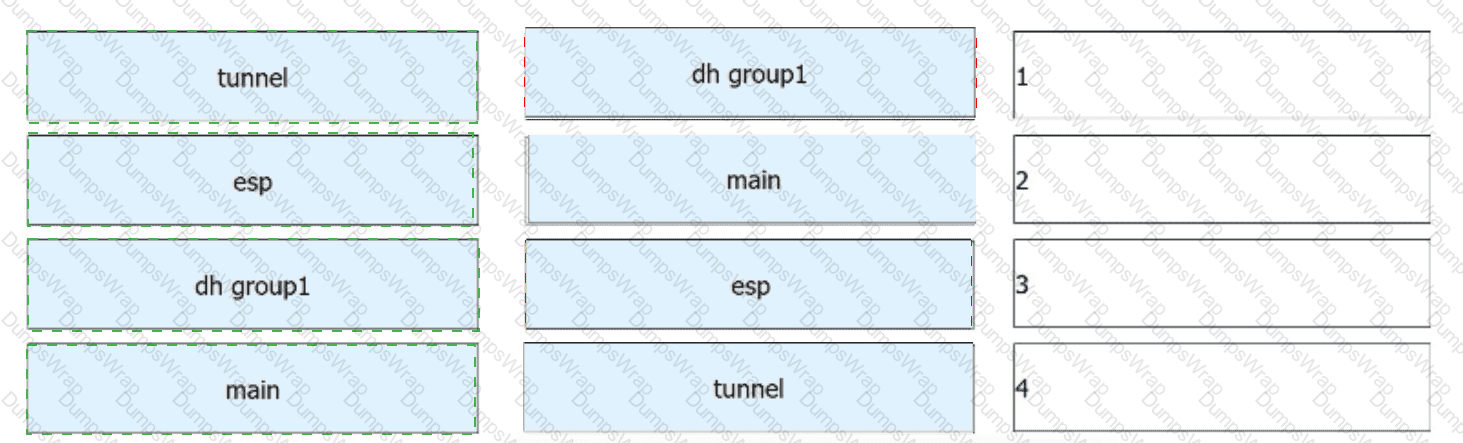
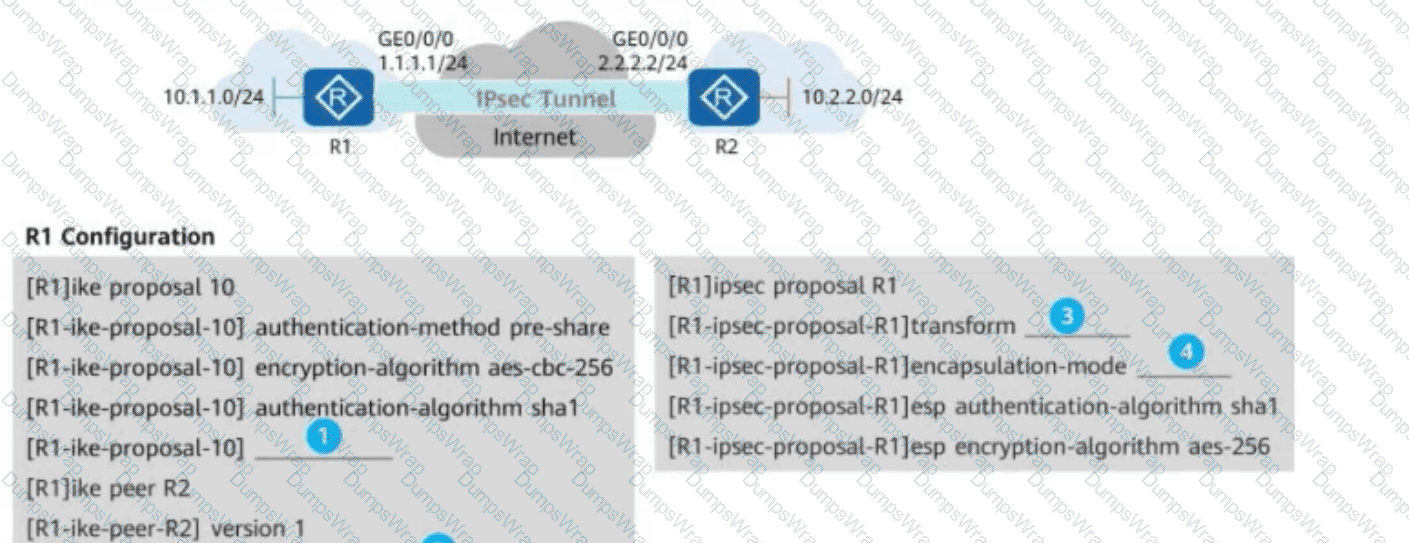
(As shown in the following figure, R1 and R2 establish an IPsec VPN in ISAKMP mode for communication. For IPsec proposals on R1 and R2, ESP is used, the encapsulation mode is set to tunnel mode, SHA1 is configured as the authentication algorithm, and AES-256 is configured as the encryption algorithm. In addition, IKEv1 is configured for IKE peers, the main mode is configured for IKEv1 negotiation phase 1, and the PSK Huawei@123 is configured for PSK authentication between IKE peers. For IKE proposals on R1 and R2, SHA1 is configured as the authentication algorithm, AES-256 is configured as the encryption algorithm, and DH group 1 is configured for IKE negotiation. Based on these configurations on R1 and R2, drag the configuration items on the left to the correct locations on the right.)

(If the number of MAC addresses learned on an interface enabled with port security reaches the upper limit, which of the following actions may the switch take?)
(Which of the following fields is not carried in a BGP EVPN Type 5 route?)
(Which of the following technologies can be used to isolate users in the same VLAN, enhance user communication security, and prevent invalid broadcast packets from affecting services?)
(A supermarket chain wants to manage all its branch networks through iMaster NCE-Campus. However, it does not want to purchase physical servers or software. In this case, which of the following deployment modes is recommended?)
(On the Device Management page of iMaster NCE-Campus, which of the following functions will automatically enable the SSH proxy tunnel of the network device?)
(On a small- or medium-sized campus network deployed based on the Huawei CloudCampus Solution, if a single AP is used as the network egress and needs to be managed by iMaster NCE-Campus, in which of the following modes should the AP work?)
(In the Huawei CloudCampus Solution, which of the following provisioning modes isnot supportedby firewalls?)
(Which of the following statements about static VXLAN tunnel configuration are true?Choose all that apply.)
(Huawei iMaster NCE-Campus provides the financial SD-WAN SRv6 solution to help the financial industry implement end-to-end scheduling. To use this function, you need to obtain the SRv6 function package license.)
(APs in the Agile Distributed Wi-Fi Solution include central APs and RUs. A central AP can manage multiple RUs, so no AC is needed in the Agile Distributed Wi-Fi Solution.)
(On a virtualized campus network deployed using iMaster NCE-Campus, implementing mutual access between users in different virtual networks only requires the administrator to deploy a policy control matrix on iMaster NCE-Campus.)
(Huawei CloudEngine S series switches can provide PoE using Cat5e cables over a distance of up to 200 m.)
(DHCP dynamically configures and centrally manages IP addresses of hosts. Which of the following statements about DHCP is false?)
(When configuring access authentication, you need to define the items authorized to users in the authorization result. Which of the following items does not need to be defined?)
(In the admission design for large- and medium-sized campus networks, which of the following authentication modes can be used for PCs connected to IP phones?)
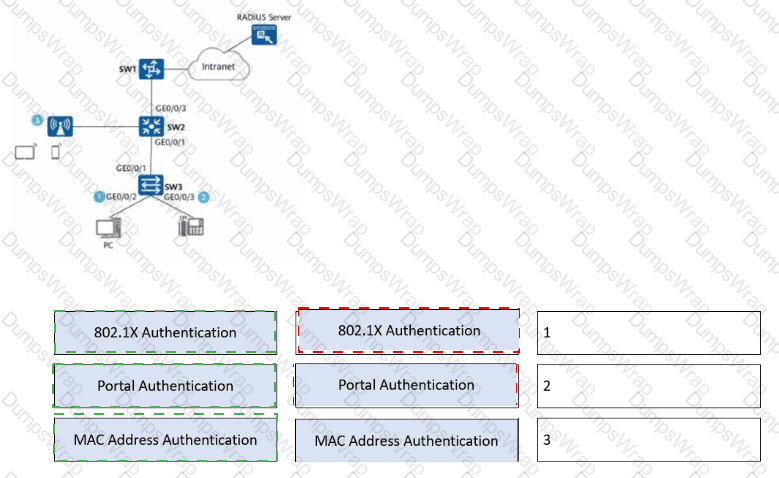
(Refer to the figure.
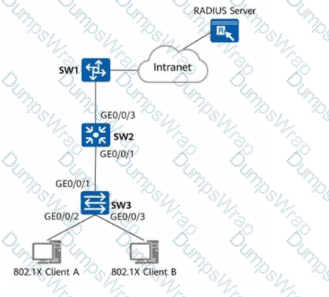
Which of the following steps aremandatoryto enable 802.1X authentication on GE0/0/2 and GE0/0/3 of SW3 and configure a RADIUS server to authenticate and deliver network access rights to users?Choose all that apply.)
(To isolate communication between wired terminals, you can enable port isolation on the access switches. However, APs cannot implement wireless user isolation.)
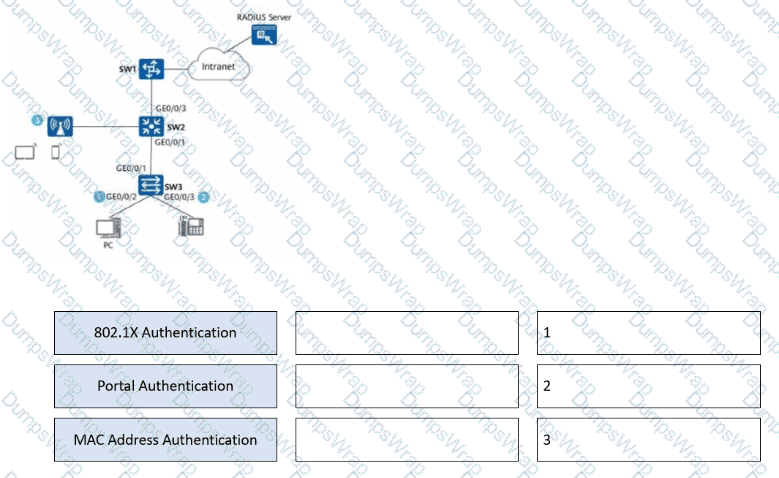
Network admission control (NAC) needs to be deployed on the network shown in the figure. Drag a proper authentication mode to each authentication point.
(Refer to the following routing entries queried using a command on the VTEP. Which of the following statements about these routes are true?)
Network(EthTagId/IpPrefix/IpPrefixLen) NextHop
*>i 0:172.16.2.0:24 1.1.1.2
*>i 0:172.16.13.0:24 1.1.1.2
*>i 0:192.168.122.0:30 1.1.1.2
(On a campus network, iMaster NCE-Campus is used to deploy two VNs: R&D VN and marketing VN, users in these two VNs belong to two security groups, respectively. The campus network requires R&D personnel and sales personnel to communicate with each other. To meet this requirement, which of the following tasks does a network administrator need to perform?)
(Which of the following roles is not a core role in Huawei's free mobility solution?)
(Which of the following statements about the underlay network of a VXLAN-based virtualized campus network isfalse?)
(The Huawei CloudCampus Solution supports various rate limiting modes for wireless users in small- and medium-sized campus scenarios. Which of the following modes is suitable for refined traffic control of each user?)
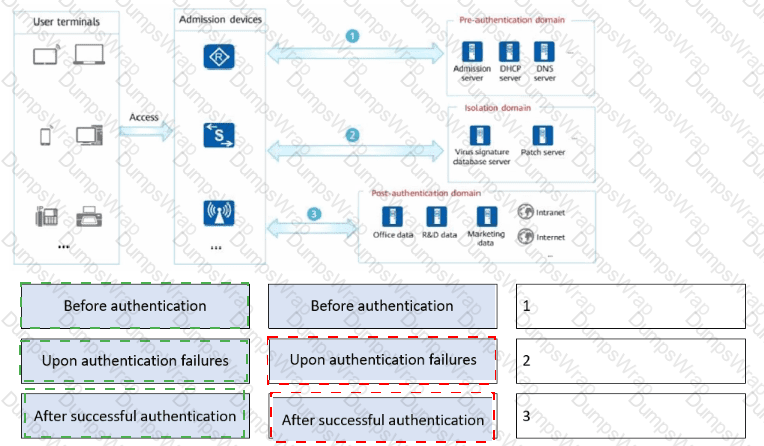
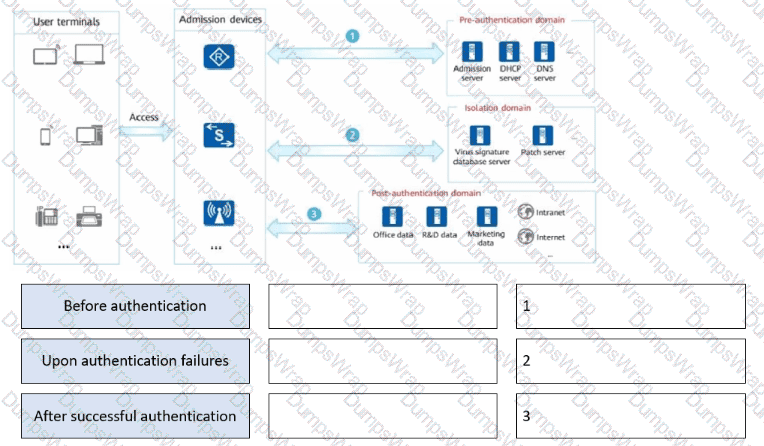
Drag the user authentication results to the corresponding network access rights.
(iMaster NCE-CampusInsight uses SNMP technology to collect metrics and logs of network devices and detects network exceptions based on real service traffic.)
(In Huawei's free mobility solution, if one device functions as both an authentication point and a policy enforcement point, the administrator needs to subscribe to IP-security group entries to view user information.)
(Fabric nodes need to be planned during fabric design on a CloudCampus virtualized campus network. Which of the following statements about node planning on a fabric is false?)
(Which of the following statements about configuring user access authentication is false?)
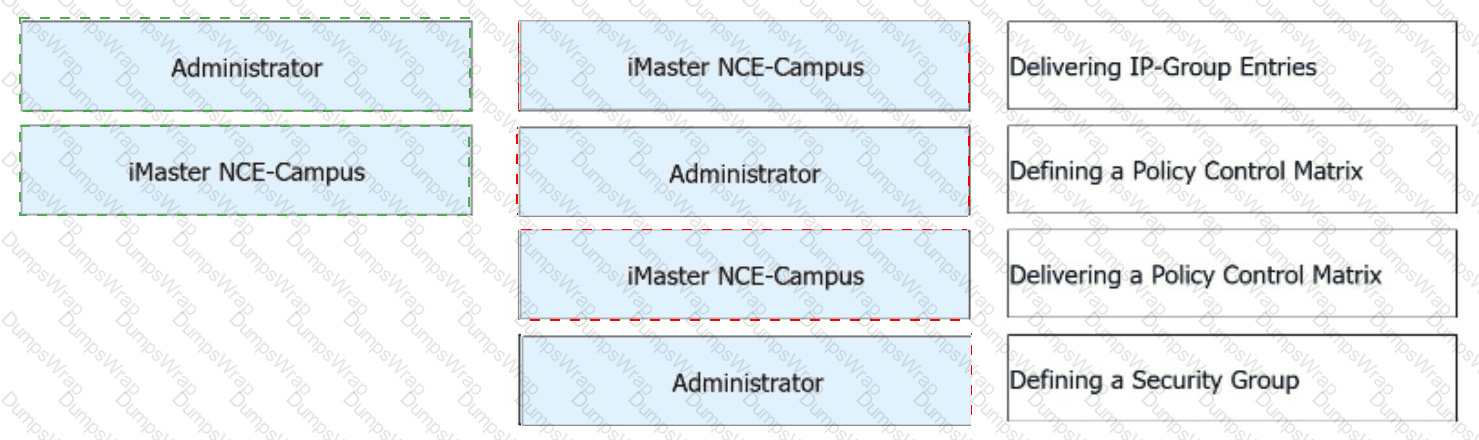
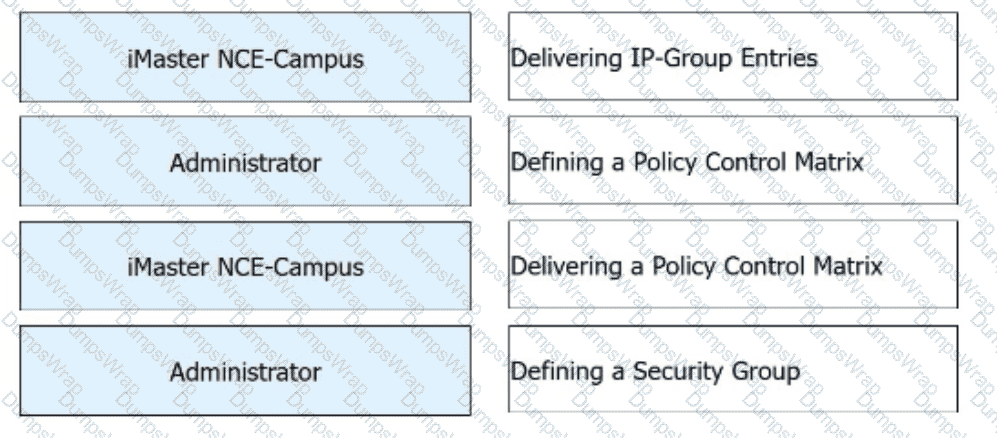
Free mobility is deployed on a campus network through iMaster NCE-Campus. During this deployment, which of the following steps are performed by administrators and which are automatically performed by iMaster NCE-Campus?