JNCIS-MistAI-Wired Questions and Answers
What is meant when aMarvis Actionis shown as “AI Validated”?
Options:
The issue which triggered an alert has been set to Resolved status.
Marvis has observed a new issue.
Marvis has observed a recurring issue.
Marvis has observed an issue that is no longer present.
Answer:
DExplanation:
WhenMarvis Actionsdisplay “AI Validated,” it indicates the issue was detected earlier but is nowresolved.
Marvis automatically validates remediation and marks the action closed once the anomaly clears.
What is the purpose of an EPVN Type 4 route?
Options:
to provide a mass withdraw
to provide MAC advertisement
to provide BUM flooding
to provide a designated forwarder election
Answer:
DExplanation:
According to Juniper Networks' EVPN documentation, an EVPN Type 4 route, also known as an Ethernet Segment route, is a critical component of the BGP EVPN control plane used specifically in multihoming scenarios. When a Customer Edge (CE) device is connected to two or more Provider Edge (PE) routers via a Link Aggregation Group (LAG), these PE routers must coordinate to manage traffic flow and prevent network loops.
The primary purpose of the Type 4 route is to enable Designated Forwarder (DF) election. In a multihomed Ethernet Segment (identified by a unique Ethernet Segment Identifier or ESI), only one PE router—the Designated Forwarder—is permitted to forward Broadcast, Unknown unicast, and Multicast (BUM) traffic from the EVPN core to the CE device. Without this election process, multiple PE routers would forward the same BUM packets to the CE, leading to traffic duplication and potential broadcast storms.
The workflow begins when a PE router is configured with an ESI on a physical or logical interface; it then generates and advertises a Type 4 route to all other PE routers in the network. This route carries the ESI and an "ES-import" extended community, which allows other PEs connected to the same segment to automatically discover their peers. Once these "peering" PEs are discovered, they collectively execute a DF election algorithm—such as the default modulo-based algorithm or the newer preference-based algorithm—to select the DF and Backup Forwarder (BDF) for each VLAN or bridge domain. By ensuring a deterministic and synchronized selection of the forwarder, Type 4 routes provide the foundational stability required for active-active and active-standby multihoming in modern campus and data center fabrics.
Which two statements are correct aboutJuniper Mist Dynamic Packet Capture? (Choose two.)
Options:
No configuration is necessary for Mist’s Dynamic Packet Capture.
It is automatically attached to a client event displayed on the Insights page.
It must be globally configured at the organization level.
It is automatically attached to the Affected Items list in the Successful Connects SLE.
Answer:
A, BExplanation:
Dynamic Packet Capture (DPC)requires no manual setup.
It is automatically linked to relevantclient eventson theInsights page, enabling fast root-cause analysis without extra configuration.
Which action would site-level network administrators be able to perform?
Options:
create a config template
modify an RF template
reboot an access point
assign access points to the site
Answer:
CExplanation:
In Juniper Mist role-based access control (RBAC),site-level administratorshave limited privileges to manage devices within their assigned sites.
They cannot modify organization-level templates or global settings but can performoperational tasks, includingrebooting APs or switchesand monitoring their status.
This ensures proper delegation of duties while maintaining centralized configuration control.
A customer has purchased five new switches and assigned them to a site.
In the configuration hierarchy, how should a user configure the name or role of each switch?
Options:
Configure names and roles on the site-specific configuration.
Configure additional CLI commands on each switch.
Configure each switch individually on the Switch Configuration menu under the Switches menu.
Add names and roles of each switch to the organization-level templates.
Answer:
CExplanation:
InJuniper Mist Cloud, configuration hierarchy includesorganization-level templates,site-level configurations, andindividual switch configuration. Site and organization levels provide shared settings, while per-device details such as hostname or role are set individually.
“Device-specific attributes such as hostname, role, or management IP are configured under the individual switch configuration menu. Templates and site configurations apply globally, while individual configurations override device-level parameters.”
Option A:Incorrect — site configuration applies to all switches at a site, not unique details.
Option B:Incorrect — CLI configuration is not used when switches are managed by Mist Cloud.
Option C:Correct— each switch’s name and role are configured individually underSwitches → Switch Configuration.
Option D:Incorrect — organization templates define global settings, not per-switch names.
Which configuration step is required to create a network in Juniper Mist Wired Assurance?
Options:
Enable traffic steering.
Name the VLAN and corresponding VLAN ID.
Create a unique port profile.
Create a unique access policy.
Answer:
BExplanation:
According to the Juniper Mist Wired Assurance Configuration Guide, the foundational step for implementing Layer 2 segmentation within the Mist UI is the creation of a "Network". In the context of Mist Wired Assurance, a Network is logically synonymous with a Virtual Local Area Network (VLAN). To define a network, a user must navigate to the Networks section—located within an organization-level template, a site-level configuration, or an individual switch configuration—and click to add a new entry.
The two mandatory parameters for this step are naming the VLAN and providing the corresponding VLAN ID. The name serves as a human-readable alias (such as "Corporate_Data" or "IoT_Devices") that allows administrators to easily reference the segment across different parts of the configuration without constantly tracking numeric IDs. The VLAN ID is the specific numeric value (ranging from 1 to 4094) that will be used by the switch for 802.1Q tagging on the physical wire.
This step is a prerequisite for more advanced configurations. Once a network is created with its name and ID, it can then be selected within a Port Profile. While creating a port profile (Option C) or an access policy (Option D) are common tasks in the deployment workflow, they are dependent on the prior existence of a defined Network. For instance, a Port Profile defines how a port behaves (e.g., access vs. trunk), but it must point to a specific Network name to know which VLAN to assign to that interface. Similarly, site variables can be used to override these VLAN IDs at specific locations, but the base definition requires the initial pairing of a name and a default ID in the portal.
What does Juniper Mist's dashboard show for pre-connection metrics compared to post-connection metrics?
Options:
Both pre-connection and post-connection metrics concentrate on detecting network errors for comprehensive troubleshooting.
Pre-connection metrics include successful connects and authentication, while post-connection metrics cover network errors.
Pre-connection metrics focus on network errors, while post-connection metrics measure successful connects and authentication.
Pre-connection metrics solely measure throughput, while post-connection metrics detect network errors for simplified troubleshooting.
Answer:
BExplanation:
According to Juniper Mist documentation, Wired Service Level Expectations (SLEs) are designed to provide operational visibility into the wired experience by monitoring Juniper EX and QFX Series switches. These SLEs leverage pre-connection and post-connection performance metrics to ensure network reliability and performance.
Pre-connection metrics are specifically focused on the initial phase of a client's journey to join the network. These metrics show the total number and the time required for successful connects and authentication. By tracking 802.1X events and DHCP snooping data, Mist can identify if clients are failing to onboard due to RADIUS issues, authentication timeouts, or failures in the DHCP binding process. This allows administrators to proactively address onboarding hurdles before they impact the broader user base.
Post-connection metrics, conversely, measure the network experience once a client is already "on the wire" and attempting to pass data. These metrics primarily measure throughput and focus on detecting various network errors and operational anomalies. Specifically, post-connection monitoring detects issues such as Spanning Tree Protocol (STP) loops, interface errors, and congestion. Additional post-connection insights include identifying cable issues, negotiation failures, and MTU mismatches that might occur during active data transmission.
In summary, Juniper Mist divides its telemetry into these two distinct categories to simplify troubleshooting. Pre-connection metrics ensure that users can get on the network, while post-connection metrics ensure that the network can sustain their traffic requirements without errors. This combined approach enables the Mist AI-driven Predictive Analytics and Correlation Engine (PACE) to provide a holistic view of the end-user experience, moving beyond traditional "up/down" monitoring to a deeper understanding of the quality of the client experience.
InJuniper Mist cloud services, service level expectation (SLE) telemetry is collected from every device and stored for up to how long?
Options:
1 month
2 months
7 days
24 hours
Answer:
AExplanation:
Juniper Mist AI collectstelemetry for Service Level Expectations (SLEs)across wired and wireless devices. This telemetry includes metrics such as time-to-connect, throughput, coverage, and switch performance.
“Service Level Expectation (SLE) data is collected from every device and stored for up toone monthin the Mist Cloud. This allows administrators to analyze historical performance trends and troubleshoot issues based on real-time and historical data.”
Option B (2 months):Incorrect — data is not retained this long.
Option C (7 days):Incorrect — telemetry retention is longer.
Option D (24 hours):Incorrect — too short for Mist SLE analytics.
Option A (1 month):Correct — Mist Cloud retains SLE telemetry for30 days (1 month).
Which three switch testing tools are available when using Wired Assurance?(Choose three.)
Options:
bounce port
iPerf
ping
load factory-default
cable test
Answer:
A, C, EExplanation:
According toJuniper Mist Wired Assurance documentation, three built-in diagnostic tools available for testing switch functionality areBounce Port,Ping, andCable Test.
Bounce Portallows you to disable and re-enable a port to reset connectivity.
Pingverifies Layer 3 reachability between the switch and target IPs.
Cable Testperforms diagnostics to detect wiring faults, impedance mismatches, or cable lengths.
These tools are accessed directly from theSwitch Testing Toolssection in the Mist dashboard and are available for EX Series and QFX Series switches onboarded to the Mist cloud.
Which service level expectation (SLE) metric measures congestion on the uplink interface of a switch?
Options:
Switch Health
Successful Connect
Asymmetric Uplink
Throughput
Answer:
DExplanation:
According to Juniper Mist documentation, the Throughput Service Level Expectation (SLE) is the primary metric used to represent the ability of wired users to pass traffic across the network without impedance. This SLE provides a comprehensive oversight of network performance by identifying issues that degrade the user experience, such as storm control events, interface anomalies, and specifically uplink congestion.
Within the Throughput SLE, the Congestion classifier (also referred to as Congestion Uplink) is specifically designed to monitor for buffer saturation and packet drops (TxDrops). When traffic arriving at an interface exceeds its processing or forwarding capacity, packets are queued in a buffer; if this buffer becomes full, the switch begins dropping packets. Juniper Mist utilizes a specific formula considering the ratios of TxDrops to TxPackets, Transmitted bps to Link Speed, and Received Speed to Link Speed to determine if a "Bad User Minute" has occurred due to congestion.
A critical feature of Wired Assurance is the automatic identification of uplink interfaces. Mist identifies these high-capacity ports by analyzing switch telemetry for characteristics such as having a switch or router as an LLDP neighbor, being designated as a Spanning Tree Protocol (STP) root port, or exhibiting significantly higher packet counts compared to access ports. When congestion is detected on an interface identified as an uplink, the system recognizes that this bottleneck impacts every user on that switch. By correlating these drops with the Throughput SLE, network administrators can proactively identify when a site requires more bandwidth or a different fabric architecture to handle current traffic demands, rather than simply monitoring if the link is physically "up" or "down".
What information does Mist use to determine if the port is classified as an uplink?(Choose two.)
Options:
if TX and RX are higher than the rest of the ports
if the port has an MTU greater than 1500 configured
if the port is an STP root port
if the port has a description configured
Answer:
A, CExplanation:
Juniper Mist automatically classifies ports to simplify visibility and automation withinWired Assurance. The Mist cloud analyzesport telemetryandlink behaviorto determine port roles, including uplinks.
“Mist uses machine learning and switch telemetry to automatically detect uplinks by analyzing traffic behavior and topology information. Uplink ports typically exhibit higher TX/RX utilization and are identified as spanning-tree root or forwarding ports connecting upstream devices.”
Option A:Correct — Mist examines traffic statistics. Ports with significantly higher TX/RX utilization relative to others are likely uplinks.
Option B:Incorrect — MTU size is not a classification criterion.
Option C:Correct — Mist usesSTP information(root or designated port status) to identify uplinks.
Option D:Incorrect — port description fields are for administrative purposes only and are not used by Mist analytics.
A system administrator wants to onboard switches to a greenfield site.
In this scenario, which three actions will accomplish this task?(Choose three.)
Options:
Use the Juniper Networks switch serial number.
Use the Juniper Networks switch QR claim code.
Use bulk claiming switches from a Juniper Mist sale order.
Use the API to automate autoprovisioning of the switches to Juniper Mist.
Use the Juniper Networks system MAC address number.
Answer:
B, C, DExplanation:
Forgreenfield onboarding, switches are newly deployed and must be claimed into Mist Cloud. Juniper Mist offers multiple claim options to simplify large-scale onboarding.
“You can claim switches using the device’s QR claim code, by bulk importing from a sales order, or through API-based automation for large deployments. Each of these methods securely associates the devices to your organization in Mist Cloud.”
Option A:Incorrect — serial number alone is not sufficient for claiming.
Option B:Correct— claim codes (QR) uniquely identify switches.
Option C:Correct— bulk claim from a sale order streamlines large deployments.
Option D:Correct— APIs support automated claiming and provisioning workflows.
Option E:Incorrect — MAC address alone cannot be used to claim devices.
Which statement is correct about a 3-stage campus fabric IP Clos?
Options:
The distribution layer is connected to the access layer.
The distribution layer is connected to the core layer.
The core layer is connected to the access layer.
The core layer devices are connected to each other.
Answer:
CExplanation:
Juniper’s official Campus Fabric IP Clos designfor Mist Wired Assurance defines that the3-stage IP Clostopology eliminates the traditionaldistribution layerentirely. This architecture is intended for smaller campus environments that do not need an intermediate distribution layer between the access and core.
“Juniper’s Wired Assurance supports 3-Stage and 5-Stage IP Clos deployments. The 3-Stage IP Clos is targeted towards deployments that do not require a Distribution Layer and have smaller scale requirements.”
Because the distribution layer is not present, the only hierarchical connection in a 3-stage campus fabric is between thecore and access layers. Traffic is routed directly at the access layer, and each access switch acts as a Layer-3 gateway (IRB) for its VLANs.
“In a campus fabric IP Clos architecture, Mist provisions Layer-3 (L3) integrated routing and bridging (IRB) interfaces on the access layer. All the access switches are configured with the same IP address for each L3 subnet.”
Additionally, the Juniper documentation explains that point-to-point links are configuredbetween layers, and in the case of the 3-stage design (with no distribution), this means between thecore and accessdevices:
“The point-to-point links between each layer utilize /31 addressing to conserve addresses.”
Therefore, the correct statement isC: The core layer is connected to the access layer.
OptionsAandBincorrectly mention a distribution layer that does not exist in this topology.
OptionDis incorrect because core (spine) devices in a Clos fabric are not interconnected with each other.
Under which hierarchy level would you create a new site configuration?
Options:
clients
location
access points
organization
Answer:
BExplanation:
In Mist,sitesrepresent the physical or logical grouping of devices within an organization.
You create and manage a site configuration under theLocationhierarchy in the Mist UI.
Each site inherits organization-level settings but can override or customize specific configurations such as VLANs, templates, or switch settings.
Click the Exhibit button.
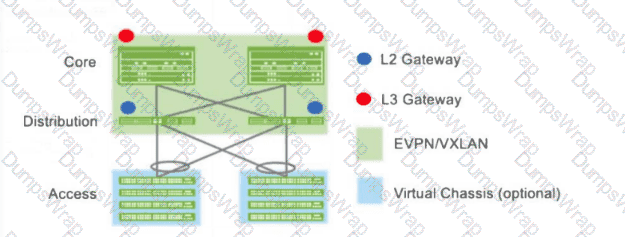
Which campus fabric architecture is shown in the exhibit?
Options:
core-distribution – edge-routed bridging (ERB)
5-stage IP Clos
3-stage IP Clos
core-distribution – centrally-routed bridging (CRB)
Answer:
DExplanation:
The exhibit shows:
L2 gateways (blue dots)positioned at the distribution layer.
L3 gateways (red dots)positioned at thecore layer.
EVPN/VXLAN providing fabric connectivity between layers.
Access switches forwarding traffic into the fabric without acting as gateways.
This directly maps to thecentrally-routed bridging (CRB)model, where:
Bridging occurs at the access/distribution layer.
Routing (L3 gateway) occurs centrally at the core layer.
“In the core-distribution CRB model, Layer 2 gateways are deployed at the distribution switches, and Layer 3 gateways are deployed centrally at the core switches.”
Option A (ERB)is incorrect because ERB places the L3 gateway at the edge/access.
Option B (5-stage IP Clos)is incorrect — that topology has a leaf/spine architecture, not core/distribution.
Option C (3-stage IP Clos)is incorrect — that eliminates the distribution layer.
Option D (CRB)is correct, matching the diagram exactly.
When do you need to "adopt a switch"?
Options:
in a brownfield environment
immediately upon arrival after it ships from the factory
in a greenfield environment
immediately upon arrival after it ships from distribution
Answer:
AExplanation:
According to Juniper Mist documentation, the term "Adopting a Switch" specifically refers to the process of bringing an existing, already-configured switch—often termed a brownfield device—under the management of the Juniper Mist cloud. This is distinct from the "claiming" process, which is reserved for greenfield environments where new, factory-default switches are added using a QR code or activation code.
In a brownfield scenario, the switch is typically already in production or has a pre-existing local configuration that must be preserved or integrated into the Mist AI-driven dashboard. To adopt such a switch, the administrator must manually interact with the switch's Command Line Interface (CLI). The Mist portal provides a unique adoption command—a string of Junos OS configuration—that includes the specific URL for the Mist cloud and the organization’s unique registration token. Once this command is pasted into the switch's CLI and committed, the switch initiates an outbound connection to the Mist cloud via TCP port 2200 or 443.
Upon successful connection, the switch's status changes from "Unassigned" to "Connected" in the Mist dashboard. This transition allows the Mist AI engine to begin collecting telemetry, monitoring Service Level Expectations (SLEs), and performing automated troubleshooting. While the adoption process allows for "monitoring only" mode to avoid disrupting existing services, it is the fundamental first step for transitioning legacy Juniper infrastructure into a modern, cloud-managed Wired Assurance environment. This workflow is essential for organizations looking to leverage Marvis AI and automated operations without having to factory-reset their entire existing network.
You are asked to forward event messages from Mist to an external log collector.
Which feature enables this capability?
Options:
Syslog
Webhooks
NETCONF
SNMP Traps
Answer:
AExplanation:
Syslogis the standard method for exporting Mist AI event and telemetry messages to third-party collectors.
It supports both UDP and TCP delivery for centralized log correlation.
Which three steps should be part of the campus fabric deployment?(Choose three.)
Options:
Define the physical connections.
Define the networks of interest.
Configure the DNS server.
Choose the topology.
Configure the group-based policy (GBP) tag.
Answer:
A, B, DExplanation:
According to theJuniper Mist AI for Wired – Campus Fabric IP Clos Deployment Workflow, deploying a campus fabric involves a defined sequence of planning and configuration steps within the Mist Cloud interface. The key stages include:
“To deploy a campus fabric, you must first define the topology type, identify the physical connections between devices, and define the networks of interest that will be extended across the fabric.”
Breaking this down:
Choose the topology (D):Selecting the correct fabric type (3-Stage or 5-Stage IP Clos) determines how access, distribution, and core switches will interconnect.
Define the physical connections (A):This step involves specifying the uplink and downlink relationships between switches so that Mist can auto-generate EVPN-VXLAN and routing configurations.
Define the networks of interest (B):These are the VLANs and subnets that need to be extended across the fabric for user and device connectivity.
Steps such asconfiguring DNS serversordefining GBP tagsarenot part of the campus fabric deployment workflowin Mist Wired; they are optional or separate configurations outside the main deployment flow.
Which two statements are correct about switch adoption?(Choose two.)
Options:
Greenfield switch adoption requires cloud-enabled switches with a claim or activation code.
Switch adoption uses SSH over TCP port 443.
Switch adoption requires Mist AP.
Brownfield switch adoption requires manual adoption and is used for switches that do not have a claim or activation code.
Answer:
A, DExplanation:
In Juniper Mist,Greenfield adoptionapplies to new, cloud-ready switches (such as EX4100, EX4400, and QFX series) using aclaim or activation codeto securely connect to the Mist cloud.
Brownfield adoption, however, supports switches already deployed or not factory-fresh. These are manually onboarded by configuring outbound management connectivity and adopting them through the Mist portal.
This distinction enables both new and legacy EX/QFX environments to be cloud-managed under Wired Assurance.
You must provide physical connectivity between thecore and access devices.
Which step of the campus fabric deployment process would allow you to accomplish this task?
Options:
Define the topology type and select the devices.
Configure the underlay network.
Configure the overlay network.
Apply the intent.
Answer:
AExplanation:
In theCampus Fabric Deployment Wizard, the first step is defining thetopology type(3-stage or 5-stage IP Clos) and mapping thephysical connectionsbetween devices (core, distribution, and access).
“The first step in the campus fabric deployment process is to define the topology and identify physical connections between devices. This ensures correct port mapping between core, distribution, and access tiers.”
Option A:Correct— topology definition and physical connectivity mapping occur in the initial step.
Option B:Incorrect — the underlay network configuration happens after topology definition.
Option C:Incorrect — overlay configuration handles EVPN/VXLAN and routing setup, not physical cabling.
Option D:Incorrect — applying intent finalizes the deployment but does not define connectivity.
A company is planning to deploy a Juniper Mist campus fabric and wants to implement group-based policy (GBP)for micro segmentation.
Which statement is correct in this scenario?
Options:
GBP requires access switches to be EX4100 or EX4400 switches.
GBP configuration should be repeated on every individual switch in the fabric.
GBP configuration must be applied to each individual switch in the fabric using the CLI.
GBP can be implemented on any Juniper Networks switch that supports EVPN-VXLAN.
Answer:
AExplanation:
Group-Based Policy (GBP)is a Juniper EVPN-VXLAN feature that enablesmicrosegmentationwithout requiring multiple VRFs or VLANs. It is implemented within Juniper Mist’sWired Assurance and Campus Fabricframeworks.
“GBP provides scalable, identity-based segmentation for campus fabrics and is supported on EX4100 and EX4400 Series switches operating in EVPN-VXLAN mode under Mist management.”
The feature requires hardware and software support forEVPN-VXLAN and GBP tagging, which is currently available on specific EX models managed by Mist Cloud.
Option A:Correct— GBP requires compatible access switches, specifically EX4100 and EX4400 models.
Option B:Incorrect — GBP is centrally managed through Mist Cloud, not configured per switch.
Option C:Incorrect — GBP is provisioned via Mist Cloud, not the CLI.
Option D:Incorrect — GBP is not supported onallEVPN-capable switches; only on defined platforms (EX4100/EX4400).
What are the two ways to forward BUM traffic when using EVPN?(Choose two.)
Options:
Use static routes.
Use BGP neighborship.
Use ingress replication.
Use underlay replication.
Answer:
C, DExplanation:
InEVPN-VXLAN,BUM (Broadcast, Unknown unicast, and Multicast)traffic is handled differently than unicast traffic. EVPN provides two main forwarding mechanisms to distribute BUM traffic betweenVTEPs(VXLAN Tunnel Endpoints):
“BUM traffic in EVPN-VXLAN fabrics is replicated using eitheringress replicationorunderlay multicast(PIM-based). Both methods ensure that broadcast and unknown unicast frames reach all remote VTEPs within the same VXLAN segment.”
Option A:Incorrect — static routes are unrelated to BUM forwarding.
Option B:Incorrect — BGP is thecontrol plane, not a data-plane forwarding method.
Option C:Correct—Ingress replicationreplicates BUM packets to all remote VTEPs in the same VNI using unicast tunnels.
Option D:Correct—Underlay replication (multicast)uses multicast groups in the IP underlay to distribute BUM frames efficiently.
Click the Exhibit button.
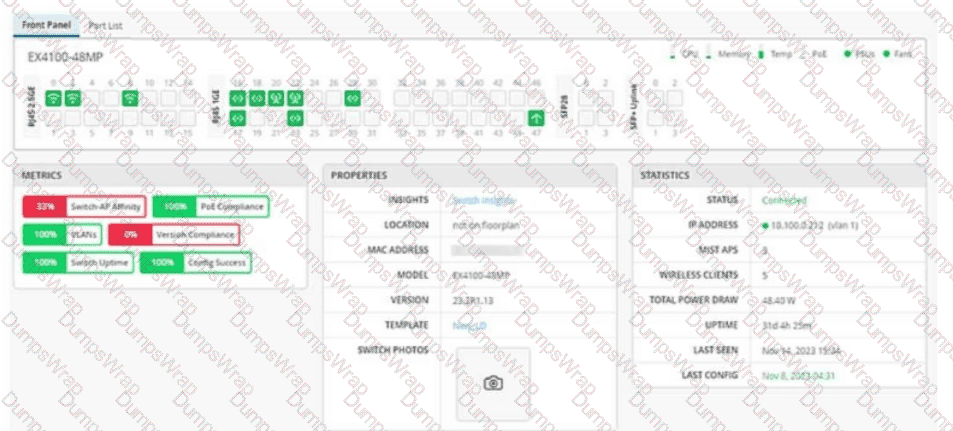
Which two statements are correct about the switch shown in the exhibit? (Choose two.)
Options:
PoE is enabled.
The Junos OS version on this switch is not compliant with the other switches in the site.
The Mist APs are connected to ge interfaces.
The Junos OS version on this switch is compliant with the other switches in the organization.
Answer:
A, BExplanation:
According to the provided exhibit, several visual indicators confirm the operational status and compliance of the EX4100-48MP switch within the Juniper Mist dashboard1.
First, the statement that PoE is enabled is verified by multiple sections of the dashboard2. In the Front Panel view, several ports display a green icon representing a wireless access point, and the PoE status indicator in the top right is lit green, indicating the subsystem is active. Furthermore, the Statistics panel shows a "Total Power Draw" of 48.40 W, and the Metrics section displays "100% PoE Compliance," confirming that the switch is successfully delivering Power over Ethernet to connected devices such as the three Mist APs listed in the summary.
Second, the exhibit indicates that the Junos OS version on this switch is not compliant with the other switches in the site5. This is explicitly shown in the Metrics section, where the Version Compliance tile is highlighted in red with a value of 0%6. In the Mist AI-driven interface, a red compliance tile signifies that the current software version running on the device (identified as 23.2R1.13 in the Properties panel) does not match the "Configured Version" or the "Approved Version" set at the Site or Organization level.
The other options are incorrect based on the visual evidence. While Mist APs are connected, the Front Panel shows them connected to 2.5GbE (mGig) ports (ports 0, 2, 8, etc.) and standard 1GbE ports, not specifically just "ge" interfaces in a traditional sense8. Additionally, the 0% Version Compliance score directly contradicts the idea that the switch is compliant with the organization's standards.
Which subscription is required to use Marvis?
Options:
Access Assurance
IoT Assurance
Virtual Network Assistant
Wired Assurance
Answer:
CExplanation:
Marvis is Juniper’s Virtual Network Assistant (VNA) that leverages AI to provide natural language queries, anomaly detection, and proactive troubleshooting across wireless, wired, and WAN networks.
“Marvis, the AI-driven Virtual Network Assistant, requires a Virtual Network Assistant subscription. The subscription enables Marvis to provide insights, recommendations, and natural language queries for Mist-managed networks.”
Option A (Access Assurance) is related to NAC/802.1X enforcement.
Option B (IoT Assurance) applies to profiling and securing IoT devices.
Option D (Wired Assurance) enables switch telemetry, onboarding, and assurance, but does not unlock Marvis.
Option C (Virtual Network Assistant) is correct — this subscription is required to enable Marvis AI.
You want to receivee-mail notifications when there are issues with your switches.
Where would you configure this capability in the Mist dashboard?
Options:
Marvis conversational interface
Wired SLEs
Alerts Configuration
Marvis Actions
Answer:
CExplanation:
TheAlerts Configurationsection in the Mist dashboard allows administrators to definenotification rules and recipientsfor various network events, including switch issues, site-level incidents, and SLE threshold violations. Notifications can be sent viaemail, webhook, or third-party integrations.
“Use the Alerts Configuration page to enable alerts for specific device events, assign severity levels, and define e-mail or webhook recipients for switch and site notifications.”
Option A (Marvis conversational interface):Used for querying issues via AI, not for email alerts.
Option B (Wired SLEs):Provides analytics and thresholds but does not manage notifications.
Option D (Marvis Actions):Offers suggested remediation steps, not alert setup.
Option C (Alerts Configuration):Correct— this is where email notifications are configured.

