Security, Professional (JNCIP-SEC) Questions and Answers
Exhibit
Which two statements are correct about the output shown in the exhibit? (Choose two.)
You are asked to control access to network resources based on the identity of an authenticated device
Which three steps will accomplish this goal on the SRX Series firewalls? (Choose three )
Exhibit
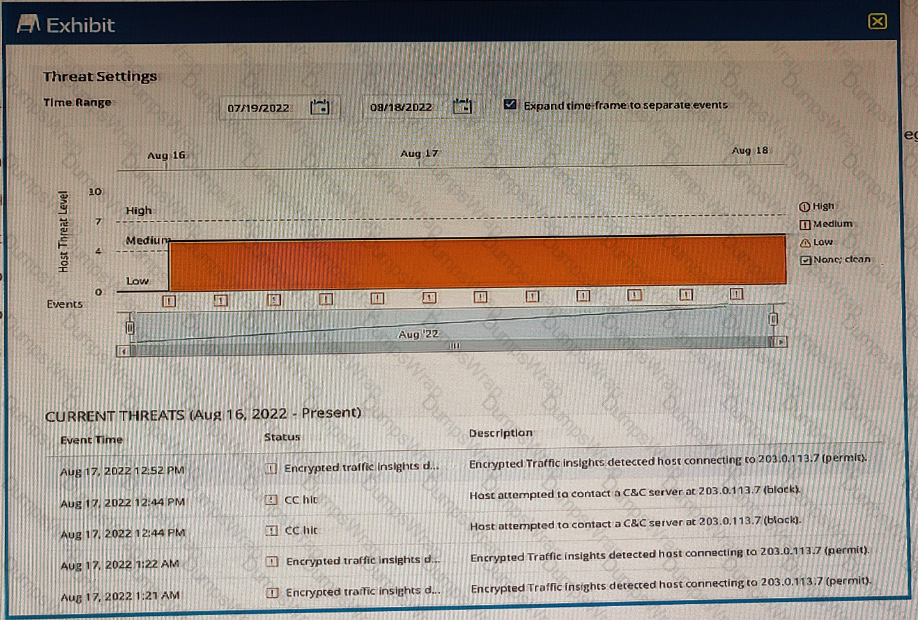
You are using ATP Cloud and notice that there is a host with a high number of ETI and C&C hits sourced from the same investigation and notice that some of the events have not been automatically mitigated.
Referring to the exhibit, what is a reason for this behavior?
you configured a security policy permitting traffic from the trust zone to the untrust zone but your
traffic not hitting the policy.
In this scenario, which cli command allows you to troubleshoot traffic problem using the match criteria?
What are two valid modes for the Juniper ATP Appliance? (Choose two.)
Which two modes are supported on Juniper ATP Cloud? (Choose two.)
Exhibit
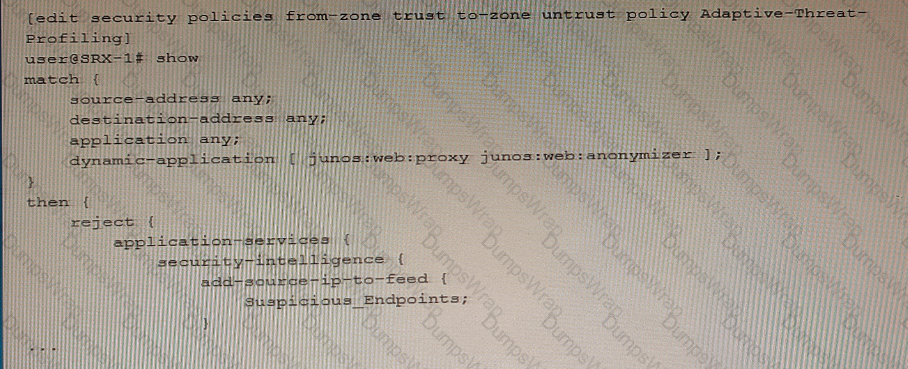
Referring to the exhibit, which two statements are true? (Choose two.)
Which two log format types are supported by the JATP appliance? (Choose two.)
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?
You are asked to allocate security profile resources to the interconnect logical system for it to work properly.
In this scenario, which statement is correct?
What is the purpose of the Switch Microservice of Policy Enforcer?
Exhibit:
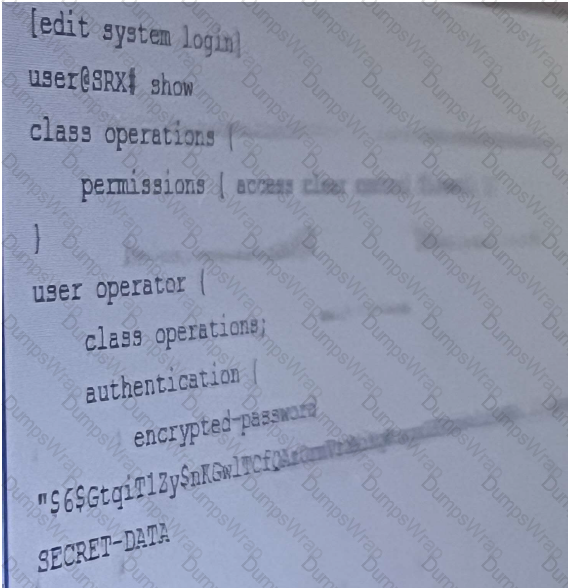
Referring to the exhibit, the operator user is unable to save configuration files to a usb stick the is
plugged into SRX. What should you do to solve this problem?
While troubleshooting security policies, you added the count action. Where do you see the result of this action?
Exhibit
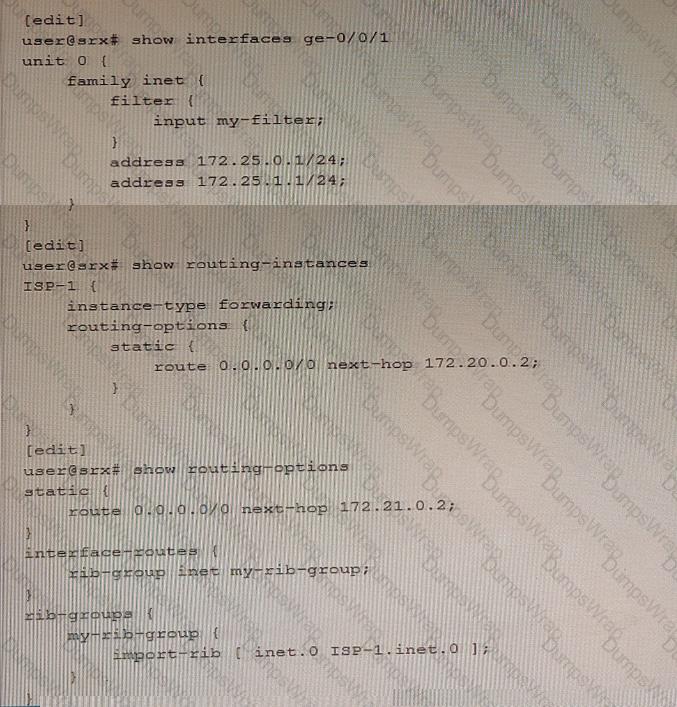
You are implementing filter-based forwarding to send traffic from the 172.25.0.0/24 network through ISP-1 while sending all other traffic through your connection to ISP-2. Your ge-0/0/1 interface connects to two networks, including the 172.25.0.0/24 network. You have implemented the configuration shown in the exhibit. The traffic from the 172.25.0.0/24 network is being forwarded as expected to 172.20.0.2, however traffic from the other network (172.25.1.0/24) is not being forwarded to the upstream 172.21.0.2 neighbor.
In this scenario, which action will solve this problem?
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
You are requested to enroll an SRX Series device with Juniper ATP Cloud.
Which statement is correct in this scenario?
Exhibit
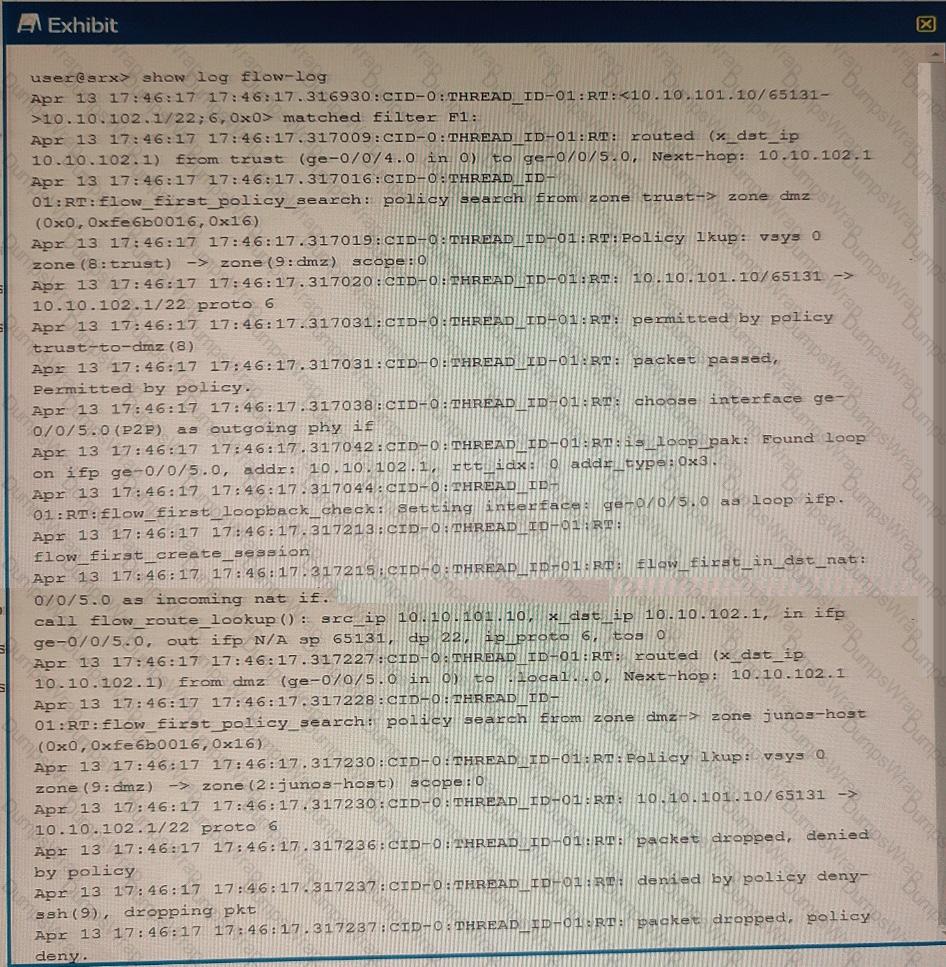
Referring to the exhibit, which three statements are true? (Choose three.)
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
You must implement an IPsec VPN on an SRX Series device using PKI certificates for authentication. As part of the implementation, you are required to ensure that the certificate submission, renewal, and retrieval processes are handled
automatically from the certificate authority.
In this scenario, which statement is correct.
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)
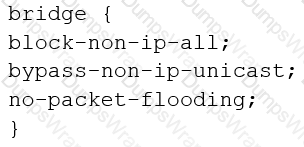
B)
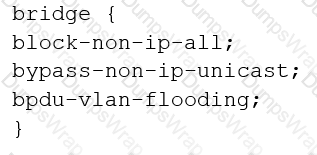
C)
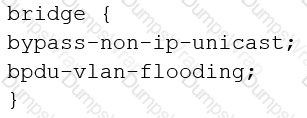
D)
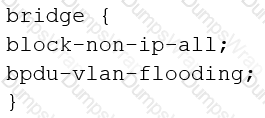
Exhibit
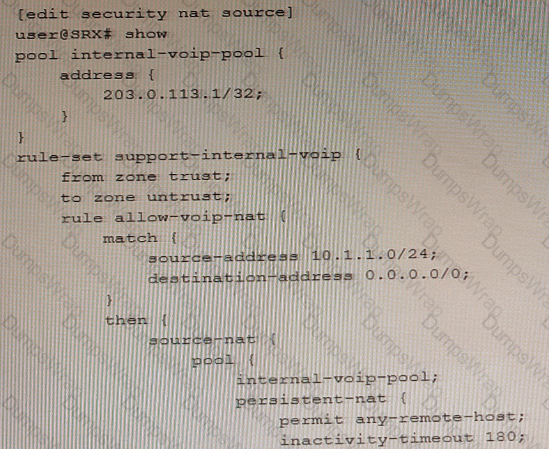
Referring to the exhibit, an internal host is sending traffic to an Internet host using the 203.0.113.1 reflexive address with source port 54311.
Which statement is correct in this situation?
Click the Exhibit button.
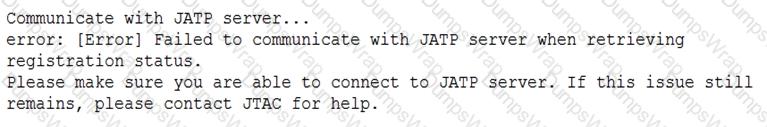
When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
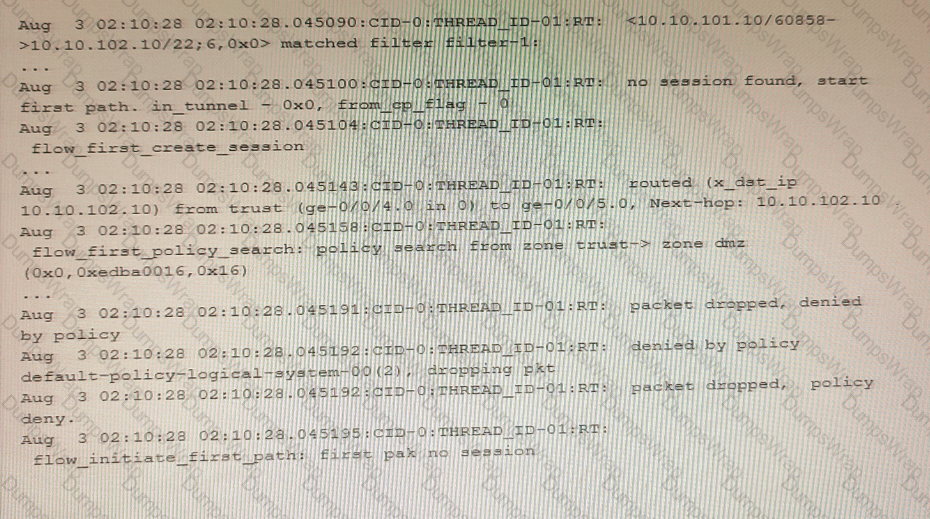
Exhibit
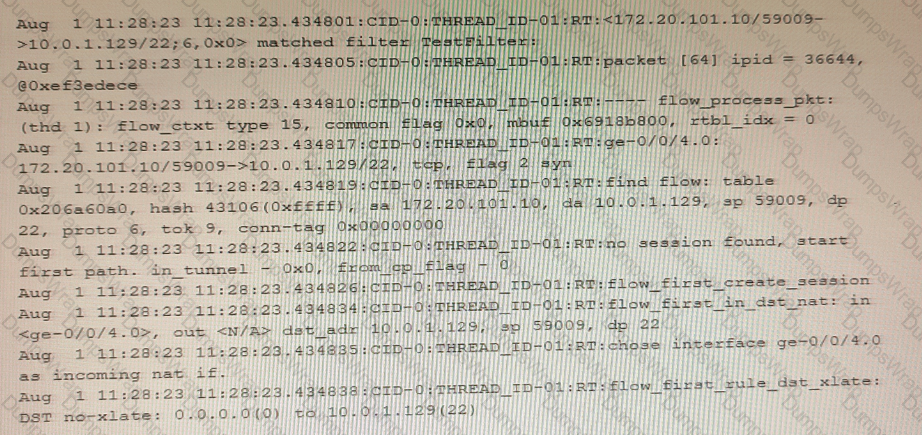
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)
Exhibit:
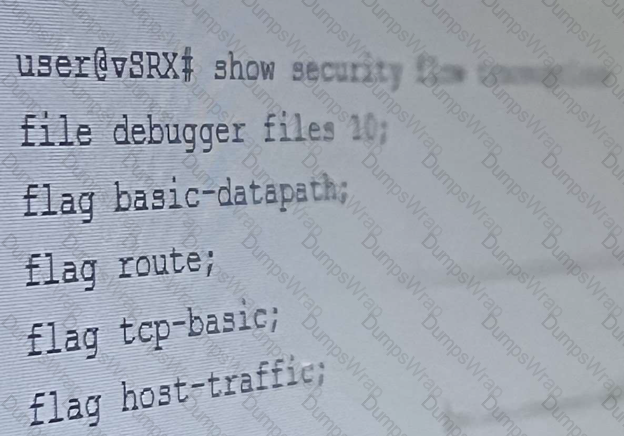
The security trace options configuration shown in the exhibit is committed to your SRX series firewall. Which two statements are correct in this Scenario? (Choose Two)
Exhibit
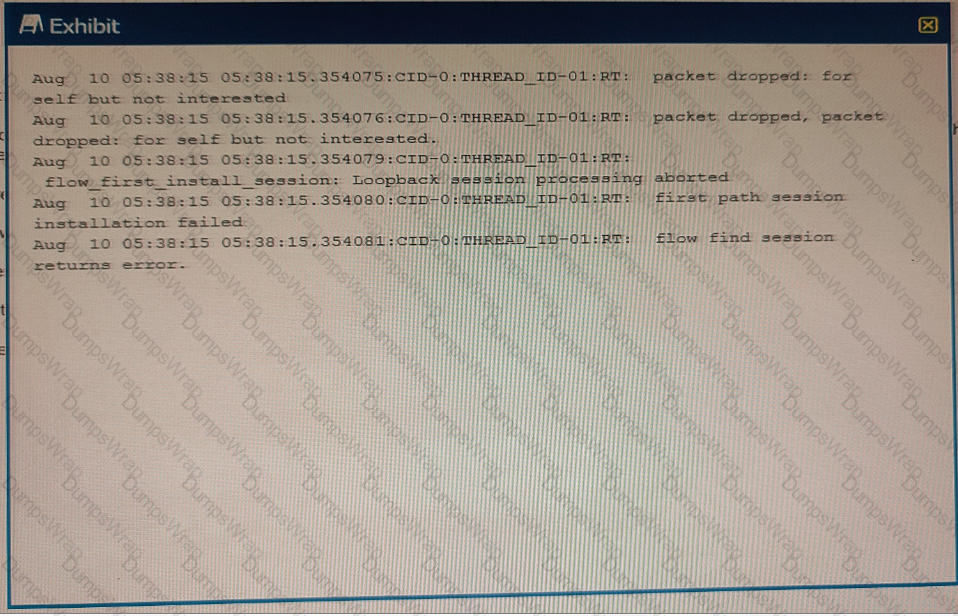
You are asked to establish an IBGP peering between the SRX Series device and the router, but the session is not being established. In the security flow trace on the SRX device, packet drops are observed as shown in the exhibit.
What is the correct action to solve the problem on the SRX device?
you must find an infected host and where the a?ack came from using the Juniper ATP Cloud. Which two monitor workspaces will return the requested information? (Choose Two)
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?
You are deploying a virtualization solution with the security devices in your network Each SRX Series device must support at least 100 virtualized instances and each virtualized instance must have its own discrete administrative domain.
In this scenario, which solution would you choose?
Exhibit.
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit
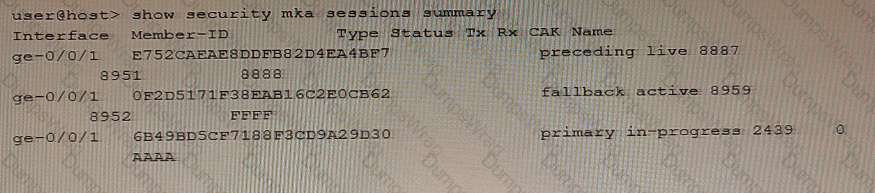
Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
Your organization has multiple Active Directory domain to control user access. You must ensure that security polices are passing traffic based upon the user’s access rights.
What would you use to assist your SRX series devices to accomplish this task?
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
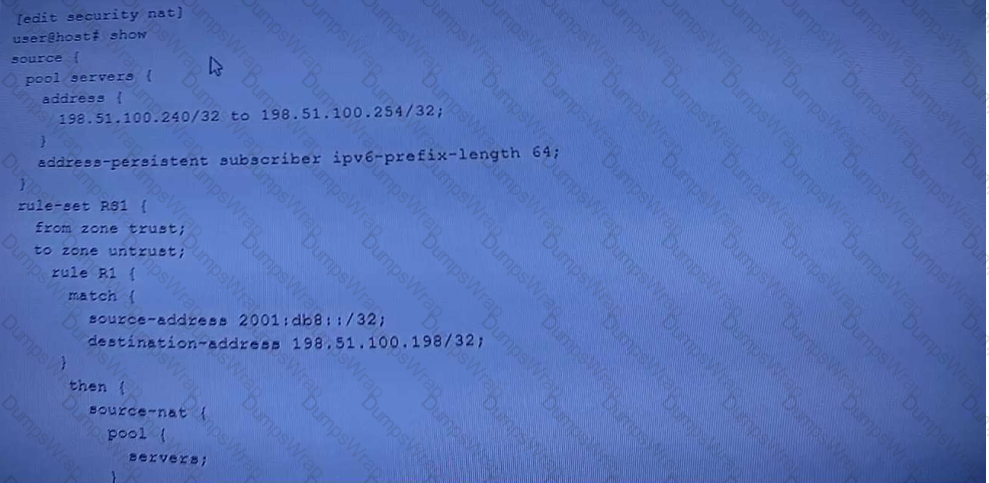
Click the Exhibit button.
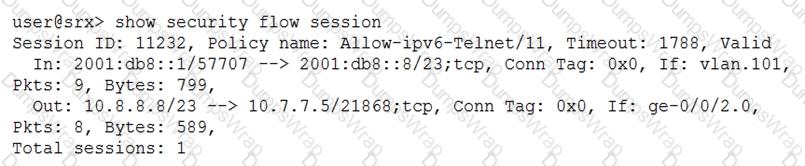
Which type of NAT is shown in the exhibit?

