Microsoft Identity and Access Administrator Questions and Answers
You need to resolve the issue of the guest user invitations. What should you do for the Azure AD tenant?
You need to implement the planned changes for Package1. Which users can create and manage the access review?
You need to resolve the issue of the sales department users. What should you configure for the Azure AD tenant?
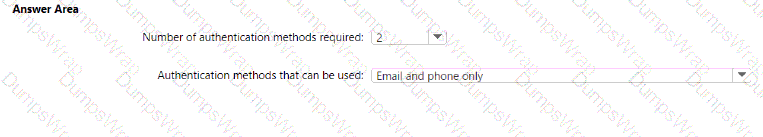
You implement the planned changes for SSPR.
What occurs when User3 attempts to use SSPR? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need implement the planned changes for application access to organizational data. What should you configure?
You need to implement the planned changes for litware.com. What should you configure?
You need to modify the settings of the User administrator role to meet the technical requirements. Which two actions should you perform for the role? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
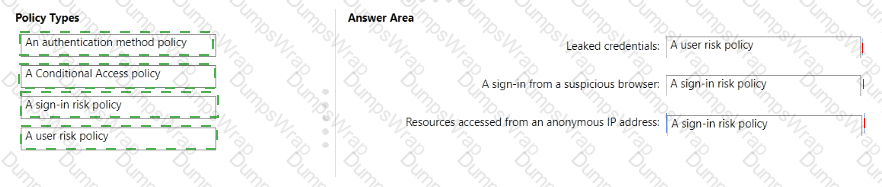
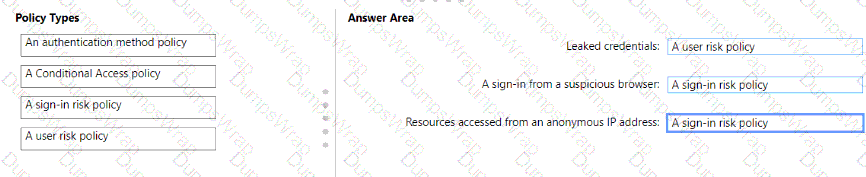
You need to resolve the recent security incident issues.
What should you configure for each incident? To answer, drag the appropriate policy types to the correct issues. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to resolve the issue of I-.Group1. What should you do first?
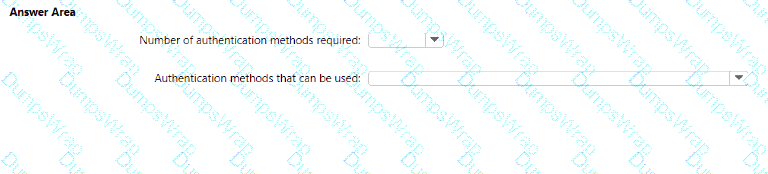
You need to meet the authentication requirements for leaked credentials.
What should you do?
You need to configure the detection of multi-staged attacks to meet the monitoring requirements.
What should you do?
You need to configure the MFA settings for users who connect from the Boston office. The solution must meet the authentication requirements and the access requirements.
What should you configure?
You need to create the LWGroup1 group to meet the management requirements.
How should you complete the dynamic membership rule? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You many need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
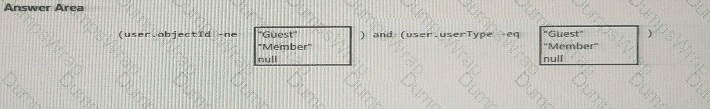
You need to track application access assignments by using Identity Governance. The solution must meet the delegation requirements.
What should you do first?
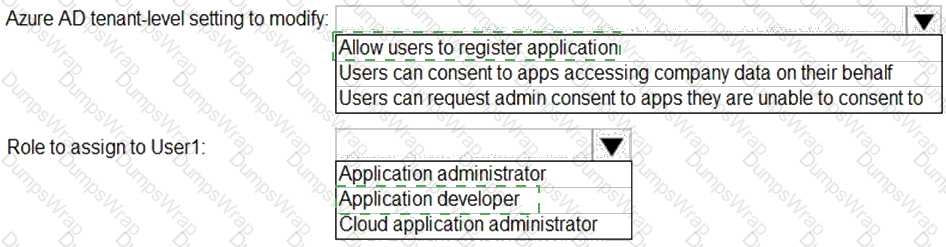
You need to configure app registration in Azure AD to meet the delegation requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
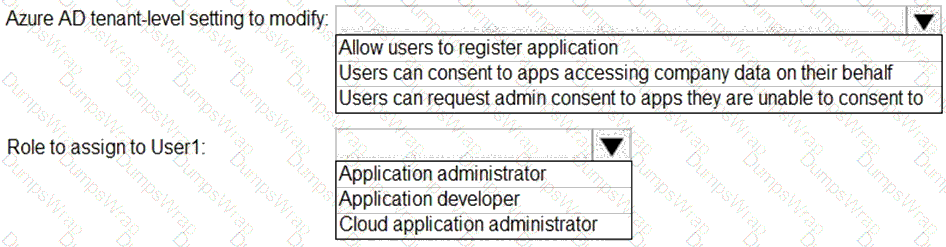
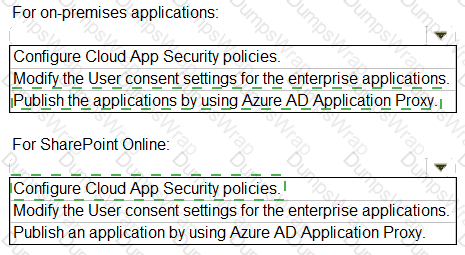
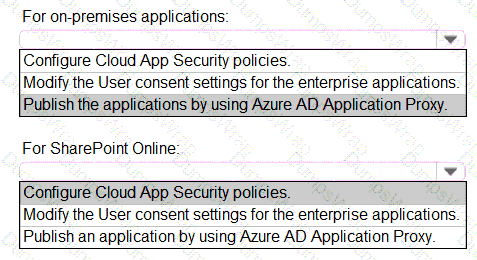
You need to implement on-premises application and SharePoint Online restrictions to meet the authentication requirements and the access requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
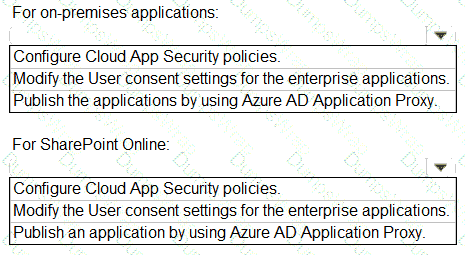
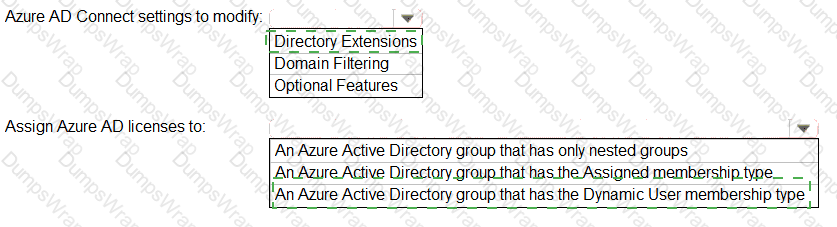
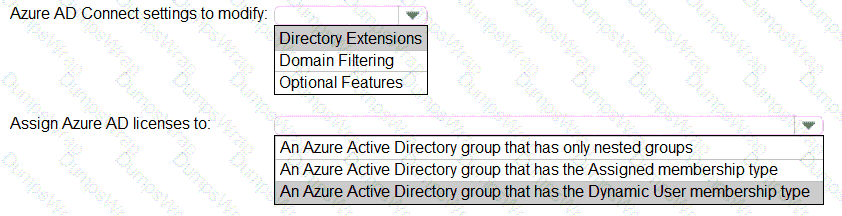
You need to configure the assignment of Azure AD licenses to the Litware users. The solution must meet the licensing requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
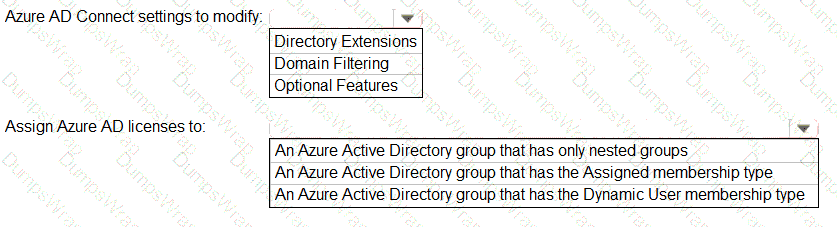
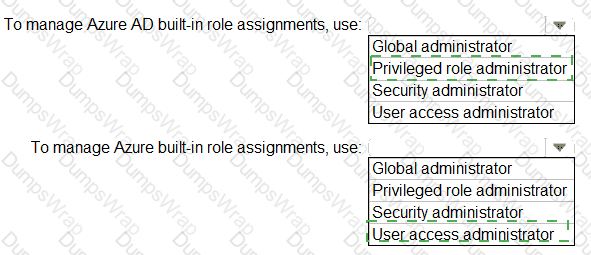
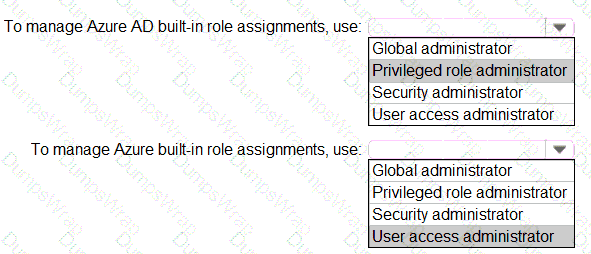
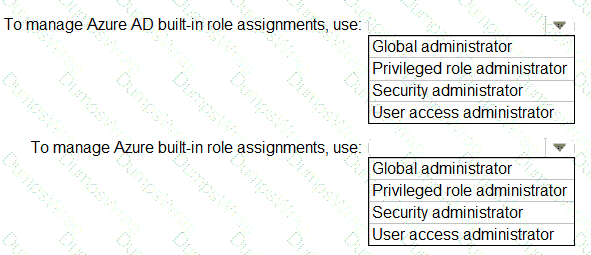
You need to identify which roles to use for managing role assignments. The solution must meet the delegation requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
You need to implement password restrictions to meet the authentication requirements.
You install the Azure AD password Protection DC agent on DC1.
What should you do next? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to meet the planned changes for the User administrator role.
What should you do?
You create a Log Analytics workspace.
You need to implement the technical requirements for auditing.
What should you configure in Azure AD?
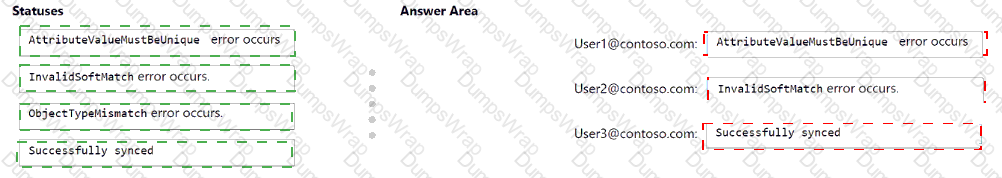
Your network contains an on-premises Active Directory domain named contoso.com that syncs with a Microsoft Entra tenant by using Microsoft Entra Connect. The domain contains the users shown in the following table.
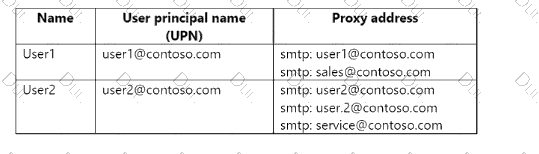
From Active Directory Users and Computers, you add the following user
• Name: User3
• UPN: user3@contoso.com
• Proxy addresses: smtp: user3@contoso.com, smtp: sales@contoso.com
From Active Directory Users and Computers, you update the proxyAddresses attribute for eachuser as shown in the following table.
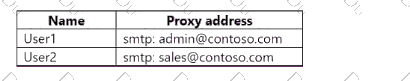
You trigger a manual synchronization.
Which sync status will Microsoft Entra Connect sync return for each user? To answer, drag the appropriate status to the correct users. Each status may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You have an Azure subscription that contains a virtual machine named VM1. VM1 has the following configurations:
• Private IP address: 172.16.1.5
• Public IP address 10fl.143.16U5
• System-assigned managed identity status: On
You install an app named App1 on VM1.
You need to configure App1 to request a managed identity app-only access token. Which IP address should App1 use for the request?
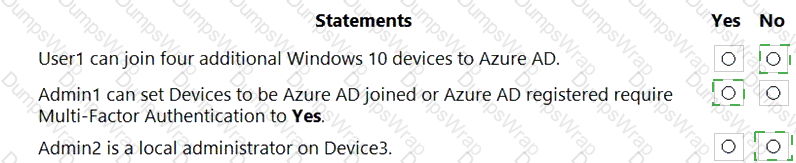
You have an Azure Active Directory (Azure AD) tenant that has an Azure Active Directory Premium Plan 2 license. The tenant contains the users shown in the following table.
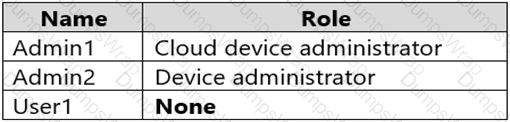
You have the Device Settings shown in the following exhibit.
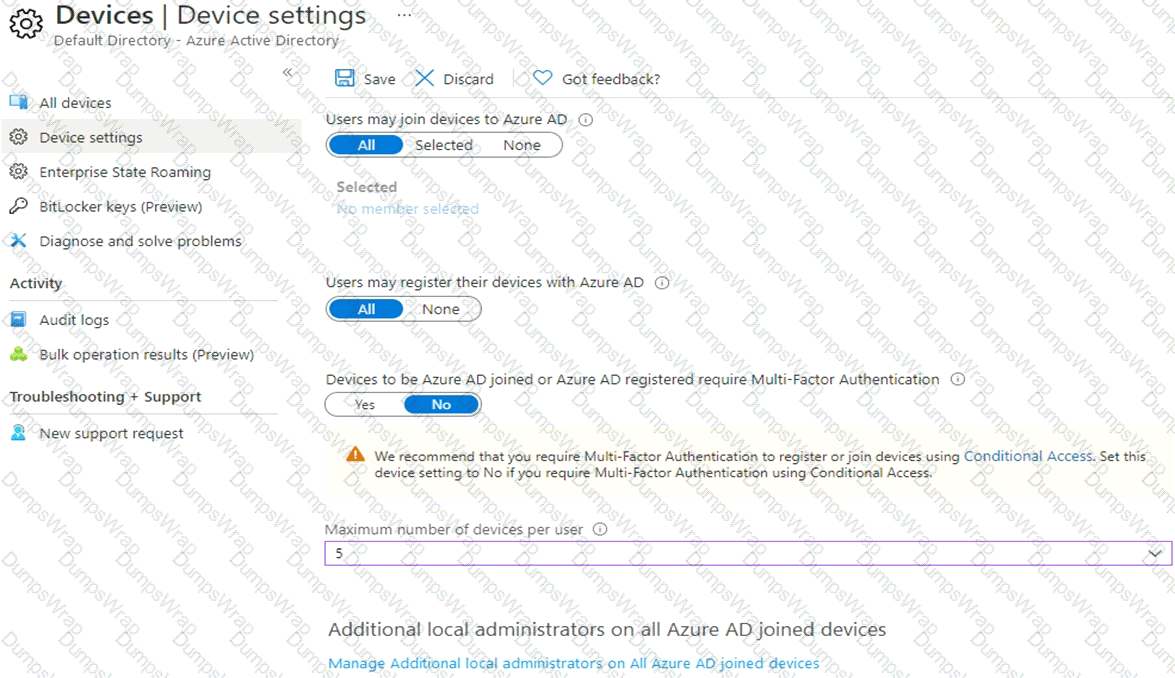
User1 has the devices shown in the following table.
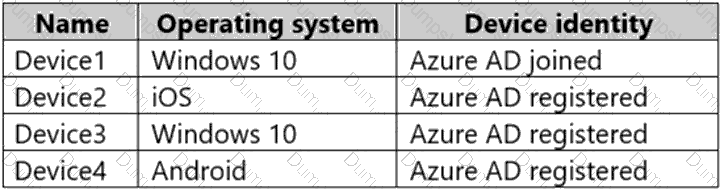
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.
You have an Azure subscription named Sub1 that contains a virtual machine named VM1.
You need to enable Microsoft Entra login for VM1 and configure VM1 to access the resources in Sub1.
Which type of identity should you assign to VM1?
You have a Microsoft 365 E5 subscription.
You deploy a third-party web gateway named Gateway1.
You need to integrate Gateway1 with Microsoft Defender for Cloud Apps. The solution must meet the following requirements:
Ensure that data flows automatically to Defender for Cloud Apps.
Minimize administrative effort.
What should you do first?
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant contains the groups shown in the following table.
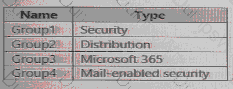
In Azure AD. you add a new enterprise application named Appl. Which groups can you assign to App1?
You create a conditional access policy that blocks access when a user triggers a high-seventy sign-in alert. You need to test the policy under the following conditions;
• A user signs in from another country.
• A user triggers a sign-in risk.
What should you use to complete the test?
You have an Azure subscription named Sub1.
You purchase a Microsoft Entra Permissions Management license.
You need to onboard Permissions Management.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE; Each correct selection is worth one point.
You have a Microsoft Entra tenant that contains a user named User1.
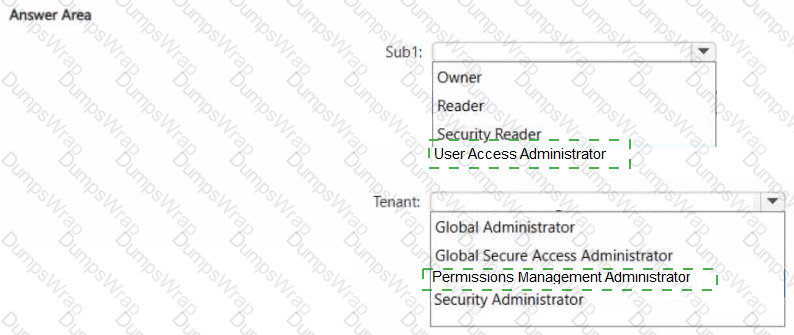
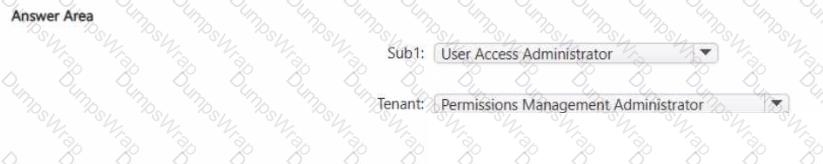
You have an Azure subscription named Sub1. User1 is assigned the Owner role for Sub1.
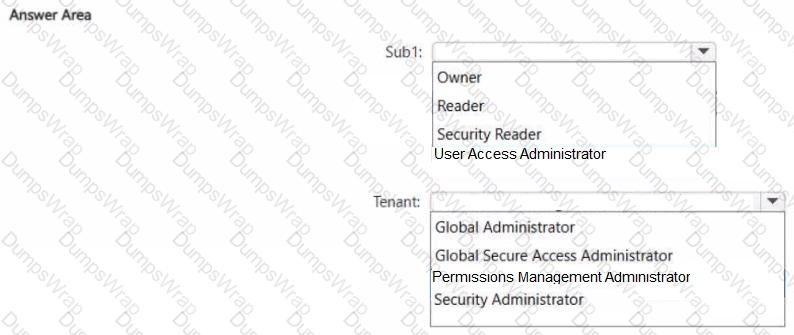
You need to ensure that User1 can onboard Sub1 to Microsoft Entra Permissions Management The solution must follow the principle of least privilege.
Which role should you assign for Sub1, and which role should you assign to User1 for the tenant? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
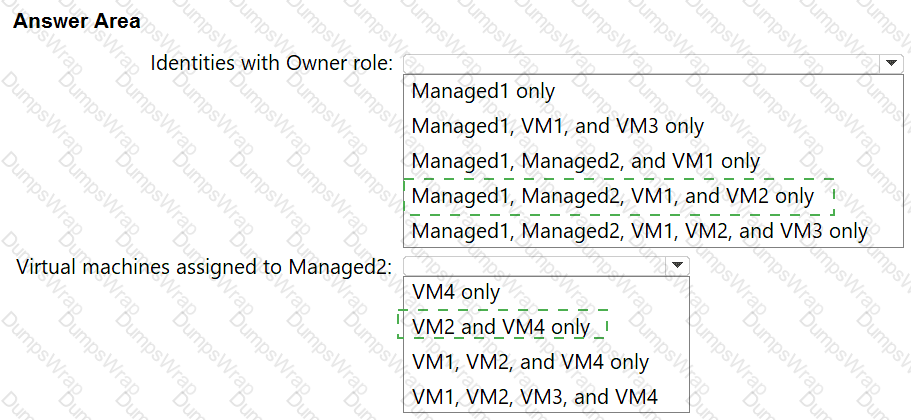
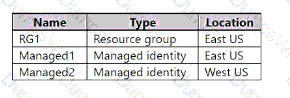
You have an Azure subscription that contains the resources shown in the following table.
The subscription contains the virtual machines shown in the following table.
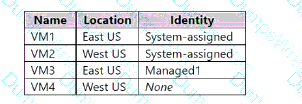
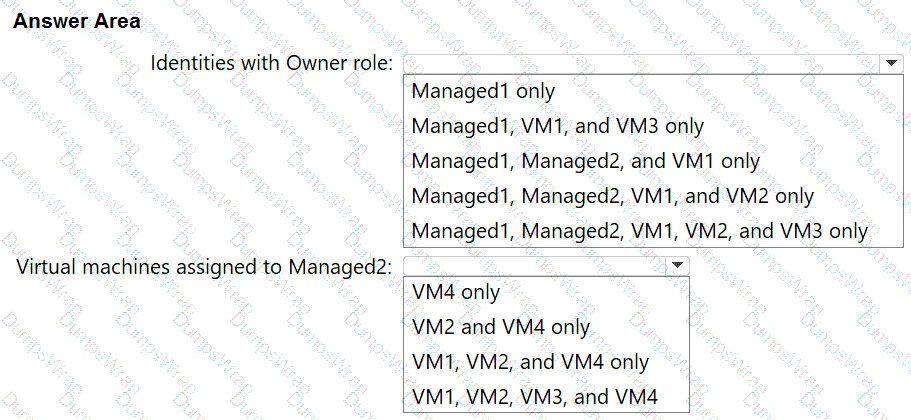
Which identities can be assigned the Owner role for RG1, and to which virtual machines can you assign Managed2? To answer, select the appropriate options in the answer area NOTE: Each correct selection is worth one point.
You have a Microsoft Exchange organization that uses an SMTP' address space of contoso.com.
Several users use their contoso.com email address for self-service sign up to Azure Active Directory (Azure AD).
You gain global administrator privileges to the Azure AD tenant that contains the self-signed users.
You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services.
Which PowerShell cmdlet should you run?
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
All users who run applications registered in Azure AD are subject to conditional access policies.
You need to prevent the users from using legacy authentication.
What should you include in the conditional access policies to filter out legacy authentication attempts?
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the objects shown in the following table.
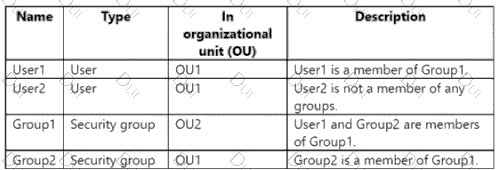
You install Microsoft Entra Connect. You configure the Domain and OU filtering settings as shown in the Domain and OU Filtering exhibit. (Click the Domain and OU Filtering tab.)
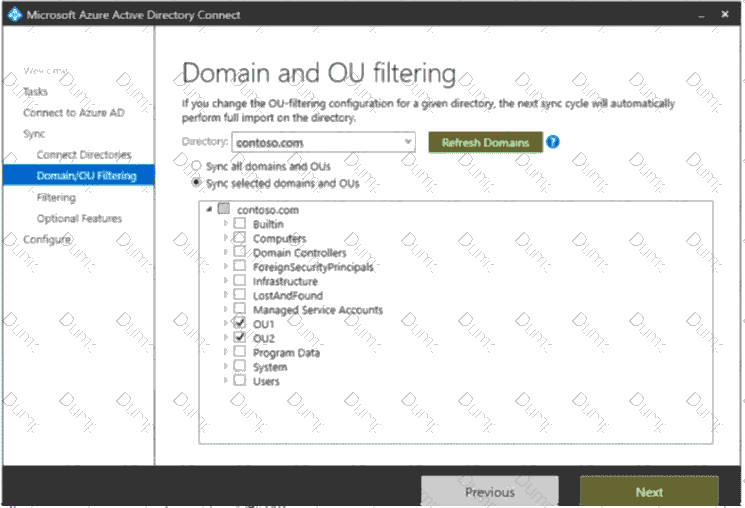
You configure the Filter users and devices settings as shown in the Filter Users and Devices exhibit. (Click the Filter Users and Devices tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft Entra tenant that contains the users shown in the following table:
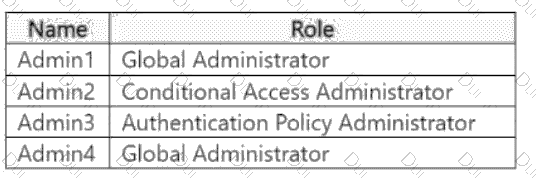
Admin4 creates a Conditional Access policy named Policy1 by using the "Require multifactor authentication for Azure management" template.
Which users will be required to use multi-factor authentication (MFA) the next time they sign in?
You have an Azure subscription.
You are evaluating enterprise software as a service (SaaS) apps.
You need to ensure that the apps support automatic provisioning of Microsoft Entra users.
Which specification should the apps support?
You have an Azure subscription.
You need to use Microsoft Entra Permissions Management to automatically monitor permissions and create and implement right-size roles. The solution must follow the principle of least privilege.
Which role should you assign to the service principal of Permissions Management?
You have an Azure AD tenant named Contoso that contains a terms of use (ToU) named Terms1 and an access package. Contoso users collaborate with an external organization named Fabrikam. Fabrikam users must accept Terms1 before being allowed to use the access package.
You need to identify which users accepted or declined Terms1.
What should you use?
You have a Microsoft Entra tenant that contains the groups shown in the following table.
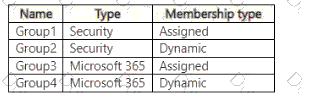
You need to implement Privileged Identity Management (PIM) for the groups.
Which groups can be managed by using PIM?
You configure a new Microsoft 365 tenant to use a default domain name of contoso.com.
You need to ensure that you can control access to Microsoft 365 resources by using conditional access
policies.
What should you do first?
You have a Microsoft 365 subscription that contains the users shown in the following table.
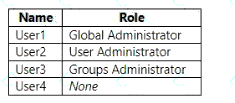
From the tenan1, you configure a naming policy for groups.
Which users are affected by the naming policy?
You have a Microsoft 365 E5 subscription.
You need to ensure that users are prompted to accept a custom terms of use (Toll) agreement when they sign in to the subscription.
What should you configure?
Task 7
You need to lock out accounts for five minutes when they have 10 failed sign-in attempts.
Task 9
You need to ensure that when users in the Sg-Operations group go to the My Apps portal a tab named Operations appears that contains only the following applications:
• Unkedln
• Box
Task 1
You need to deploy multi factor authentication (MFA). The solution must meet the following requirements:
• Require MFA registration only for members of the Sg-Finance group.
• Exclude Debra Berger from having to register for MFA.
• Implement the solution without using a Conditional Access policy.
Task 5
You need to assign a Windows 10/11 Enterprise E3 license to the Sg-Retail group.
Task 3
You need to add the Linkedln application as a resource to the Sales and Marketing access package. The solution must NOT remove any other resources from the access package.
Task 4
You need to ensure that all users can consent to apps that require permission to read their user profile. Users must be prevented from consenting to apps that require any other permissions.
Task 10
You need to create a group named Audit. The solution must ensure that the members of Audit can activate the Security Reader role.
Task 6
You need to implement additional security checks before the members of the Sg-Executive can access any company apps. The members must meet one of the following conditions:
• Connect by using a device that is marked as compliant by Microsoft Intune.
• Connect by using client apps that are protected by app protection policies.
Task 2
You need to implement a process to review guest users who have access to the Salesforce app. The review must meet the following requirements:
• The reviews must occur monthly.
• The manager of each guest user must review the access.
• If the reviews are NOT completed within five days, access must be removed.
• If the guest user does not have a manager, Megan Bowen must review the access.
Task 8
You need to prevent all users from using legacy authentication protocols when authenticating to Microsoft Entra ID.