Administering Information Security in Microsoft 365 Questions and Answers
You need to meet the retention requirement for the users' Microsoft 365 data.
What is the minimum number of retention policies required to achieve the goal?
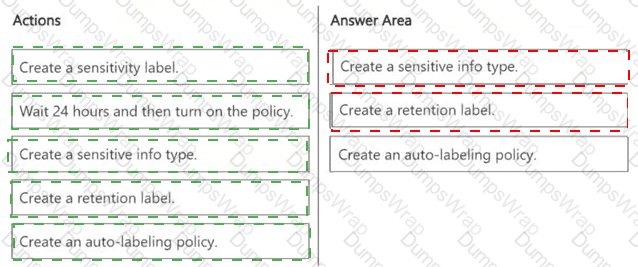
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

HOTSPOT
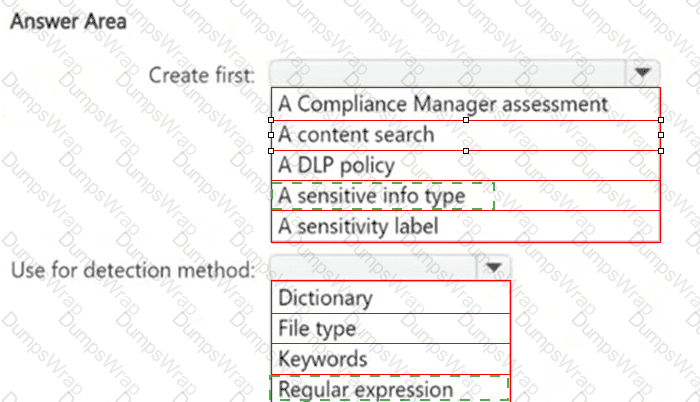
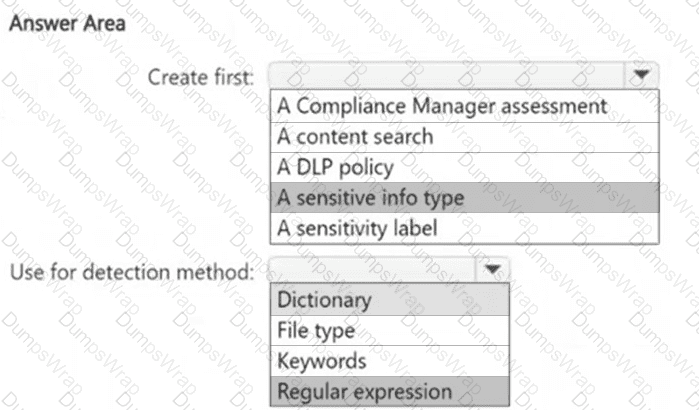
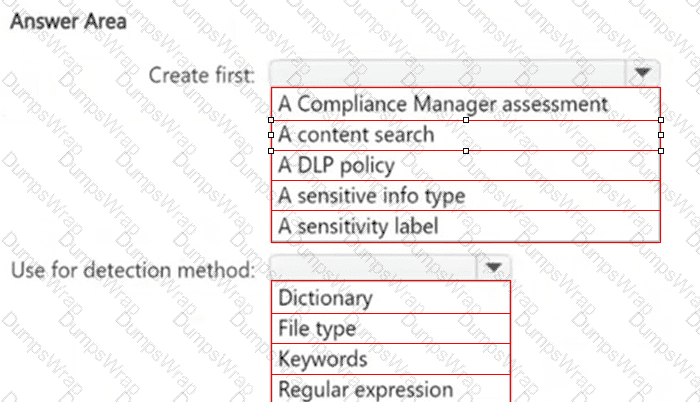
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
HOTSPOT
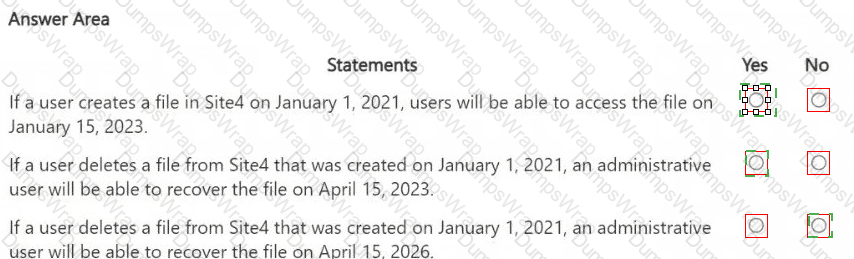
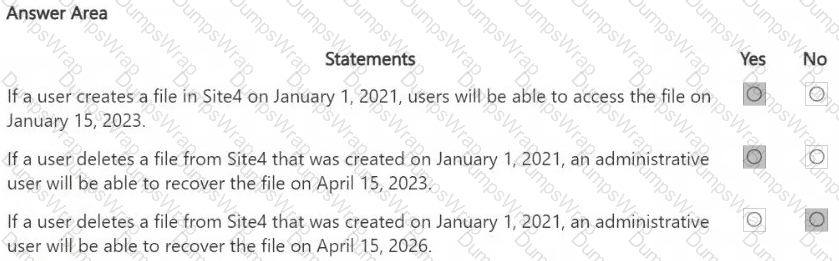
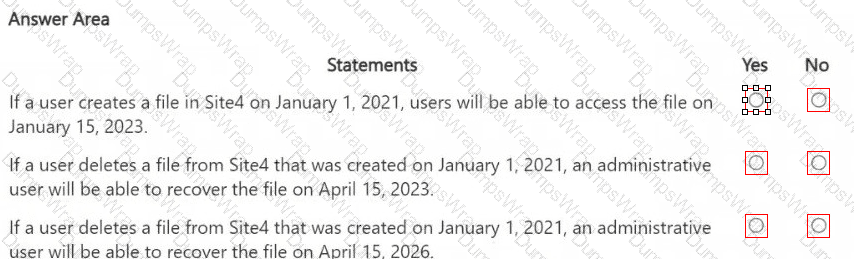
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
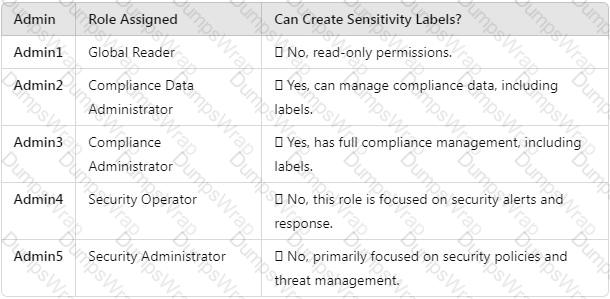
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?
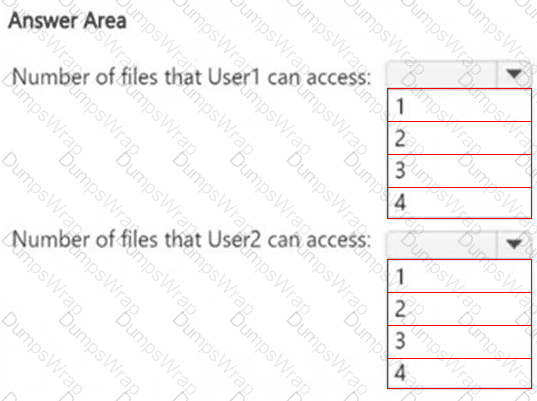
HOTSPOT
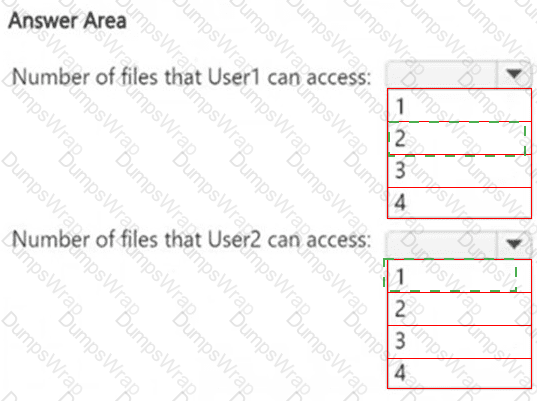
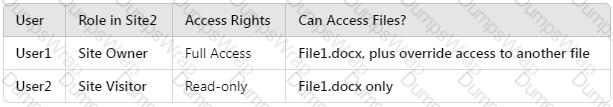
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a user named User1. You deploy Microsoft Purview Data Security Posture Management for AD (DSPM for AD). You need to ensure that User1 can verify the auditing status of the subscription. The solution must follow the principle of least privilege. To which role group should you add User1?
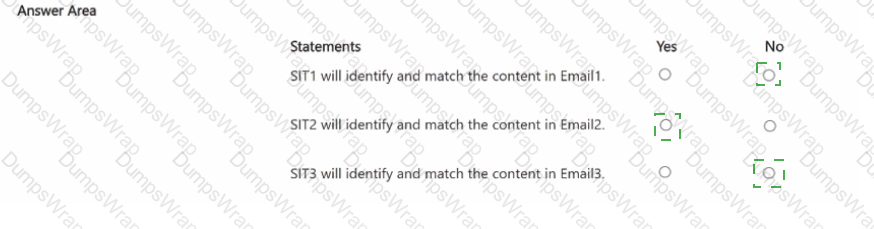
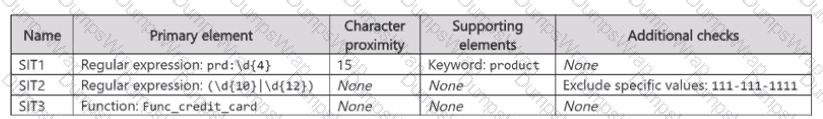
You have a Microsoft 365 E5 subscription that contains the sensitive information types (SITs) shown in the following table.
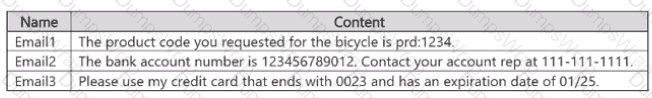
A user sends the email messages shown in the following table.
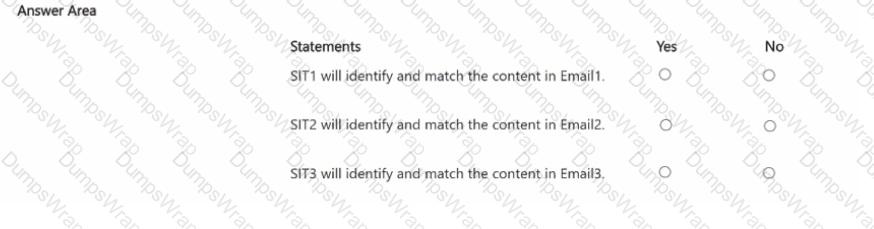
For each of the following statements, select Yes if the statement is true. Otherwise, select No
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You create a data loss prevention (DLP) policy and select.
Use Notifications to inform your users and help educate them on the proper use of sensitive info.
Which apps will show the policy tip?
You have a Microsoft 365 tenant
You need to create a new sensitive into type for items that contain the following:
• An employee ID number that consists of the hire date of the employee followed by a three digit number
• The words "Employee", "ID", or "Identification" within 300 characters of the employee ID number
What should you use for the primary and secondary elements? To answer, select the appropriate options m the answer area
NOTE: Each correct selection is worth one point

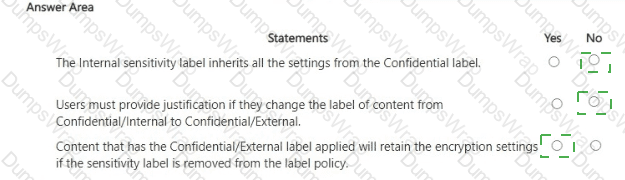
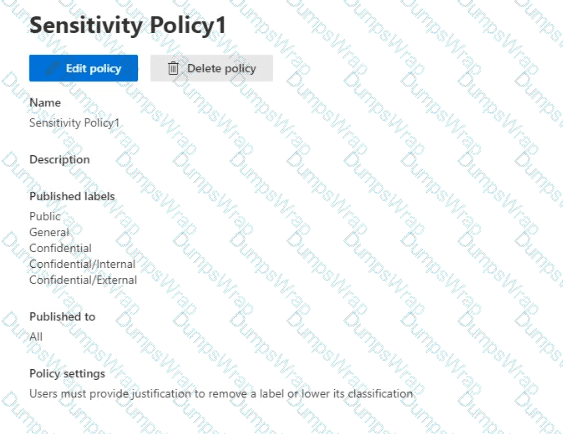
You have a Microsoft 365 E5 tenant.
You have sensitivity labels as shown in the Sensitivity Labels exhibit. (Click the Sensitivity Labels tab.)

The Confidential/External sensitivity label is configured to encrypt files and emails when applied to content.
The sensitivity labels ate published as shown in the Published exhibit. (Click the Published tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 36515 subscription tha1 contains a Microsoft SharePoint Online site named Site1 Site1 contains three tiles named File1. File2 and File3.
You create the data loss prevention (DIP) policies shown in the following table.
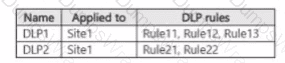
The DIP rule matches for each tile are shown in the following table.
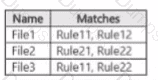
How many DIP policy matches events will be added to Activity explorer, and how many policy matches will be added to the DLP incidents report? To answer, select the appropriate options m the answer area.

You have a Microsoft 365 E5 subscription that contains the data loss prevention (DLP) policies shown in the following table.
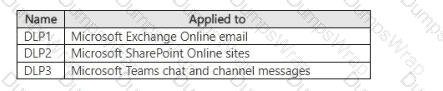
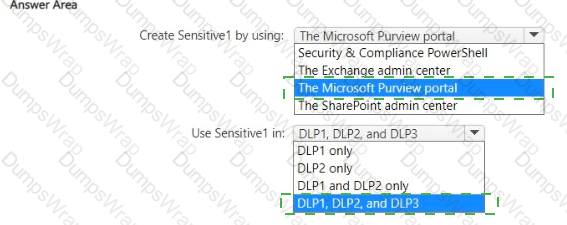
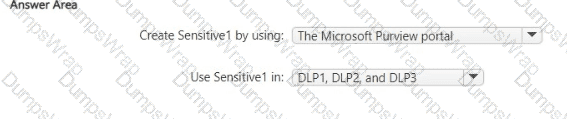
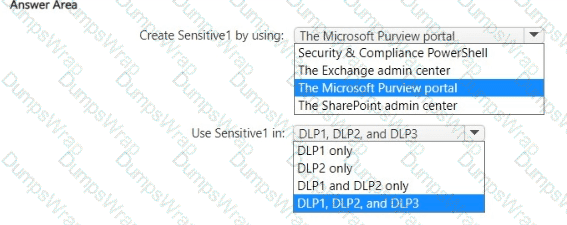
You have a custom employee information form named Template1 .docx.
You plan to create a sensitive info type named Sensitive! that will use the document fingerprint from Template1.docx.
What should you use to create Sensitive1, and in which DLP policies can you use Sensitive1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to implement Microsoft Purview data lifecycle management.
What should you create first?
You have a Microsoft 565 E5 tenant that uses Microsoft Teams and contains two users named User1 and User2. You create a data Joss prevention (DIP) policy that is applied to the Teams chat and channel messages location for User1 and User?
Which Teams entities will have DLP protection?
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to deploy a Microsoft Purview insider risk management solution that will generate an alert when users share sensitive information on Site1 with external recipients.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct answer is worth one point.
You have a Microsoft 36S ES subscription.
You need to create the Microsoft Purview insider risk management policies shown in the following table.

Which policy template should you use for each policy? To answer, drag the appropriate policy templates to the correct polices
Each template may be used once more than once or not at all. You may need to drag the split bar between panes or scroll to view..

You have a Microsoft 365 E5 subscription that contains 500 Windows devices.
You plan to deploy Microsoft Purview Data Security Posture Management for AI (DSPM for AI).
You need to ensure that you can monitor user activities on third-party generative AI websites.
Which two prerequisites should you complete for DSPM for AI? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription. The subscription contains a user named User1 and the sensitivity labels shown in the following table.

You publish the labels to User1.
The subscription contains the files shown in the following table.
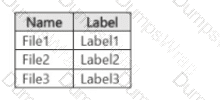
Which files can Microsoft 365 Copilot summarize for User1?
You have a Microsoft 365 alert named Alert2 as shown in the following exhibit.
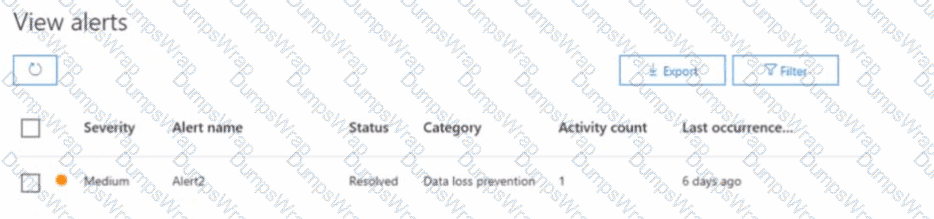
You need to manage the status of Alert? To which status can you change Alette?
You have a Microsoft 365 subscription that contains the devices shown in the following table.
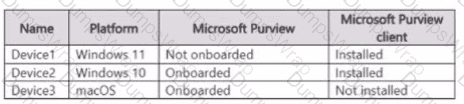
From which devices can Microsoft Purview Insider Risk Management capture forensic evidence?
HOTSPOT
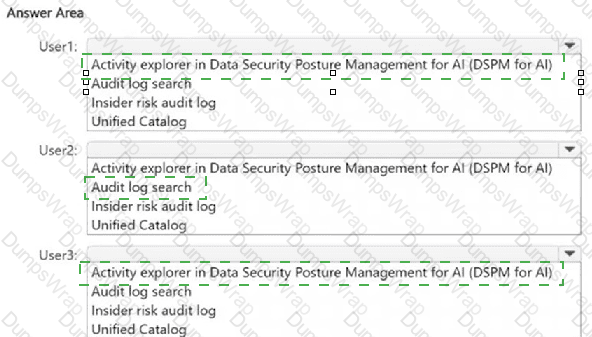
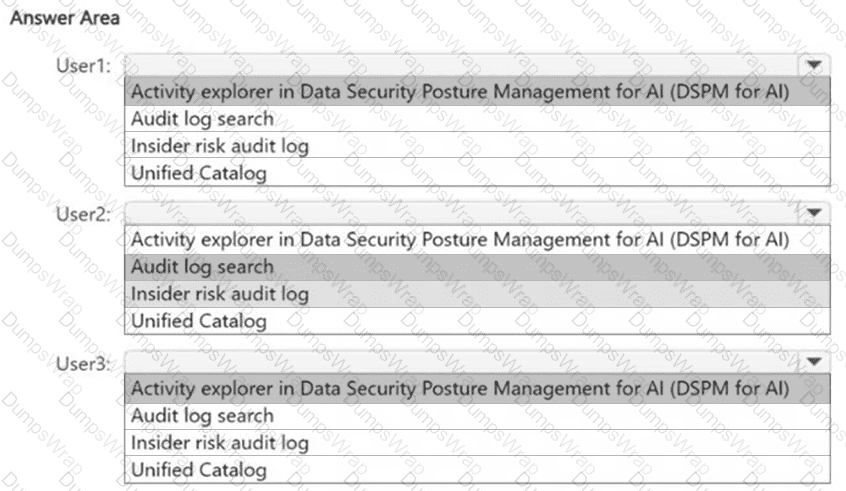
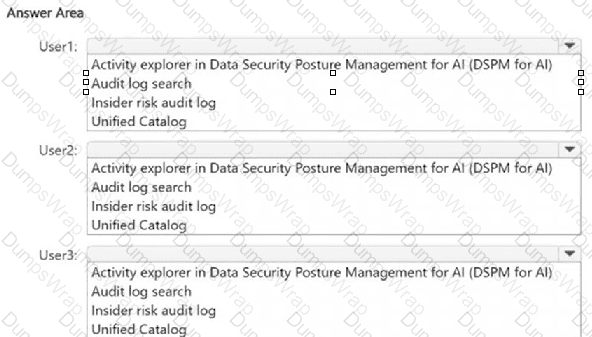
You have a Microsoft 365 E5 subscription. The subscription contains devices that are onboarded to Microsoft Purview and configured as shown in the following table.
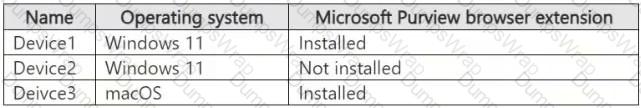
The subscription contains the users shown in the following table.

You need to review the activities.
What should you use for each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 36S subscription that contains the users shown in the following table.

You create the data loss prevention (DLP) policies shown in the following table.
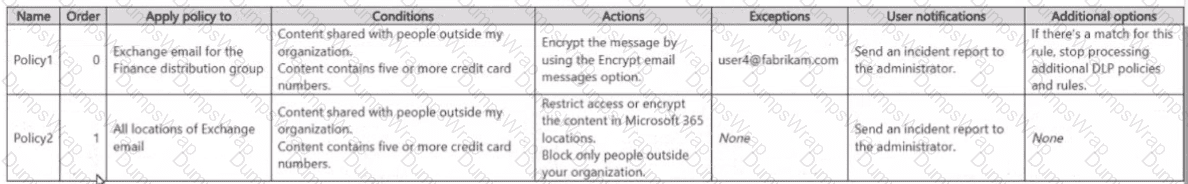
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to ensure that you receive an alert when a user uploads a document to a third-party cloud storage service.
What should you use?
You have a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management and contains three users named User1, User2, and User3.
All insider risk management policies have adaptive protection enabled and the default conditions for insider risk levels configured.
The users perform the following activities, which trigger insider risk policy alerts:
User1 performs at least one data exfiltration activity that results in a high severity risk score.
User2 performs at least three risky user activities within seven days, that each results in a high severity risk score.
User3 performs at least bwo data exfiltration activities within seven days, that each results in a high severity risk score.
Which insider risk level is assigned to each user? To answer, drag the appropriate levels to the correct users. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or seroll to view content.
NOTE: Each correct selection is worth one point.

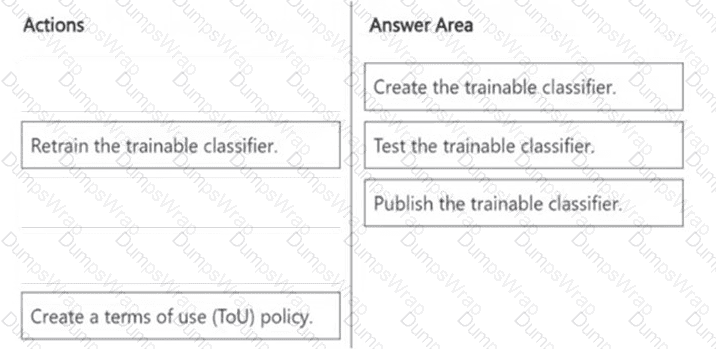
You have a sensitive information type based on a trainable classifier.
You are unsatisfied with the result of the trainable classifier.
You need to retrain the classifier.
What should you use in the Microsoft Purview portal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-MailboxFolderPermission -Identity "User1" -User User1@contoso.com -AccessRights Owner command.
Does that meet the goal?
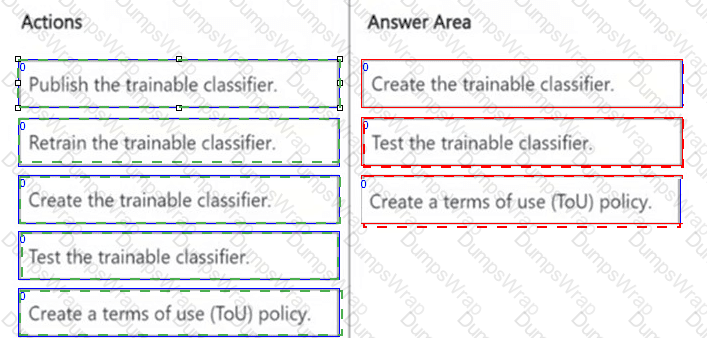
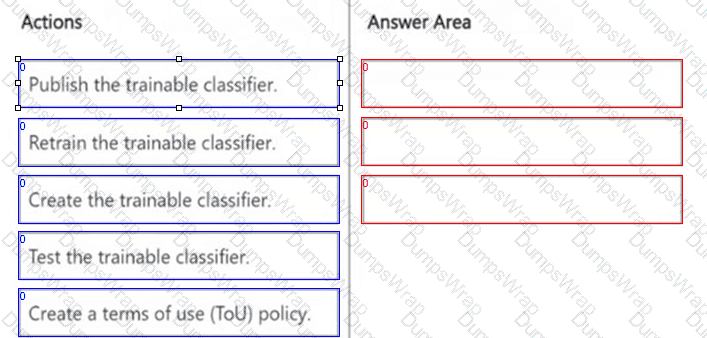
DRAG DROP
You need to create a trainable classifier that can be used as a condition in an auto-apply retention label policy.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
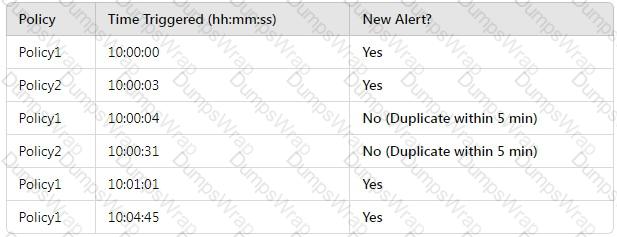
You have Microsoft 365 E5 subscription.
You create two alert policies named Policy1 and Policy2 that will be triggered at the times shown in the following table.
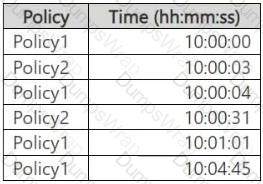
How many alerts will be added to the Microsoft Purview portal?
You need to create a retention policy to delete content after seven years from the following locations:
• Exchange Online email
• SharePoint Online sites
• OneDrive accounts
• Microsoft 365 Groups
• Teams channel messages
• Teams chats
What is the minimum number of retention policies that you should create?