Netskope Certified Cloud Security Administrator (NCCSA) Questions and Answers
You investigate a suspected malware incident and confirm that it was a false alarm.
You need to create a service request ticket for a client-related issue using the Netskope client Ul. In this scenario, you generate the client logs by right-clicking on the system tray icon and choosing
You are creating a real-time policy for cloud applications.
In addition to users, groups, and organizational units, which two source criteria would support this scenario? (Choose two.)
You want to deploy Netskope's zero trust network access (ZTNA) solution, NPA. In this scenario, which action would you perform to accomplish this task?
Your company asks you to obtain a detailed list of all events from the last 24 hours for a specific user. In this scenario, what are two methods to accomplish this task? (Choose two.)
Which three statements are correct about Netskope's NewEdge Security Cloud Network Infrastructure? (Choose three.)
What are two uses for deploying a Netskope Virtual Appliance? (Choose two.)
You need to provide a quick view under the Skope IT Applications page showing only risky shadow IT cloud applications being used.
In this scenario, which two filter combinations would you use to accomplish this task? (Choose two.)
What are two CASB inline interception use cases? (Choose two.)
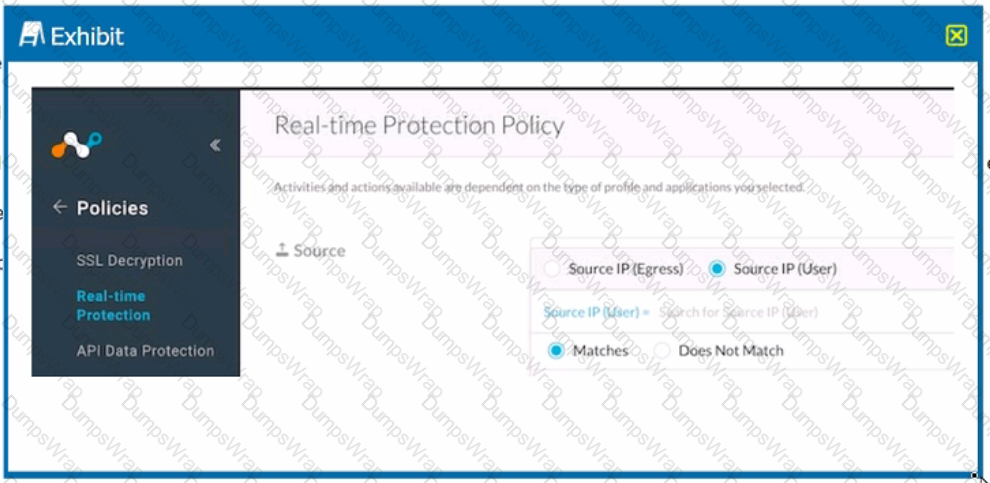
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
What is the limitation of using a legacy proxy compared to Netskope's solution?
Which two common security frameworks are used today to assess and validate a vendor's security practices? (Choose two.)
Which three security controls are offered by the Netskope Cloud platform? (Choose three.)
Which two functions are available for both inline and API protection? (Choose two.)
Exhibit
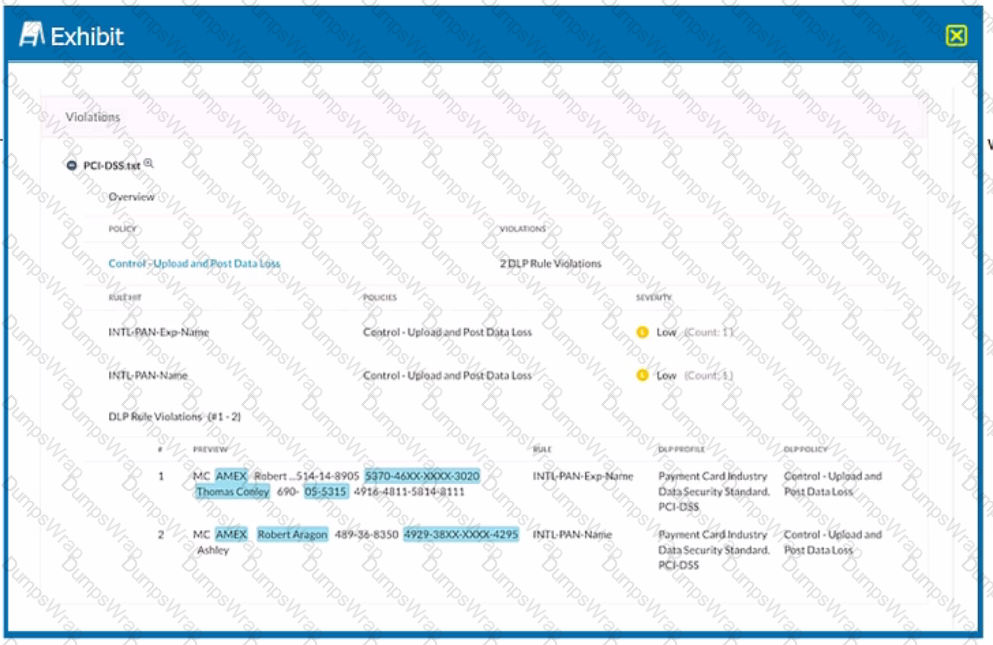
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
You want to use an out-of-band API connection into your sanctioned Microsoft 365 OneDrive for Business application to find sensitive content, enforce near real-time policy controls, and quarantine malware.
In this scenario, which primary function in the Netskope platform would you use to connect your application to Netskope?

