Netskope Certified Cloud Security Administrator (NCCSA) Questions and Answers
Your organization has implemented Netskope Private Access (NPA) for all users. Users from the European region are reporting that they are unable to access many of their applications. You suspect that the publishers for the European data center may be disconnected and you want to verify the Publishers' status.
Which two methods describe how you would accomplish this task? (Choose two.)
Which compliance standard should a company consider if both controllers and processors have legal entities in the EU?
In which two scenarios would you use SD-WAN technology? (Choose two.)
What are two uses for deploying a Netskope Virtual Appliance? (Choose two.)
Your department is asked to report on GDPR data publicly exposed in Microsoft 365, Salesforce. and Slack-sanctioned cloud applications. Which deployment model would you use to discover this data?
As an administrator, you need to configure the Netskope Admin UI to be accessible by specific IP addresses and to display a custom message after the admin users have been authenticated.
Which two statements are correct in this scenario? (Choose two.)
You are adding a new tenant administrator in the Admins page. Which additional security measure would you be able to enable for only this new account?
Your organization has recently implemented Netskope Private Access. During an investigation, your security team has asked you to provide a list of all hosts including domains and IP addresses that a user accessed through Netskope Private Access for the past seven days.
Which two locations in the Netskope Web UI would allow you to obtain and export the requested data? (Choose two.)
You are setting up a real-time threat protection policy for patient zero to block previously unseen files until a benign verdict is produced by the Netskope Threat Protection Service. In this scenario, which two policy parameters must you configure? (Choose two)
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
A customer wants to detect misconfigurations in their AWS cloud instances.
In this scenario, which Netskope feature would you recommend to the customer?
How does a cloud security solution achieve visibility into TLS/SSL-protected Web traffic?
Click the Exhibit button.
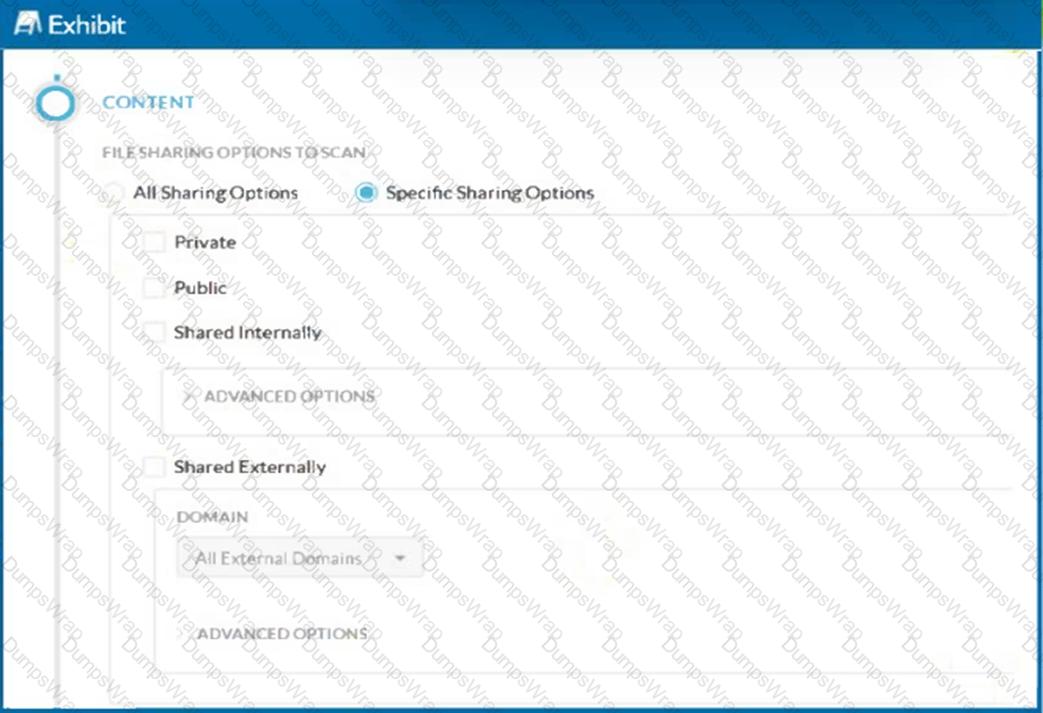
A customer has created a CASB API-enabled Protection policy to detect files containing sensitive data that are shared outside of their organization.
Referring to the exhibit, which statement is correct?
Which two statements are correct about Netskope’s NewEdge Security Cloud Network Infrastructure? (Choose two.)
You want to deploy Netskope's zero trust network access (ZTNA) solution, NPA. In this scenario, which action would you perform to accomplish this task?
Which statement is correct about Netskope's Instance Awareness?
You have applied a DLP Profile to block all Personally Identifiable Information data uploads to Microsoft 365 OneDrive. DLP Alerts are not displayed and no OneDrive-related activities are displayed in the Skope IT App Events table.
In this scenario, what are two possible reasons for this issue? (Choose two.)
Exhibit
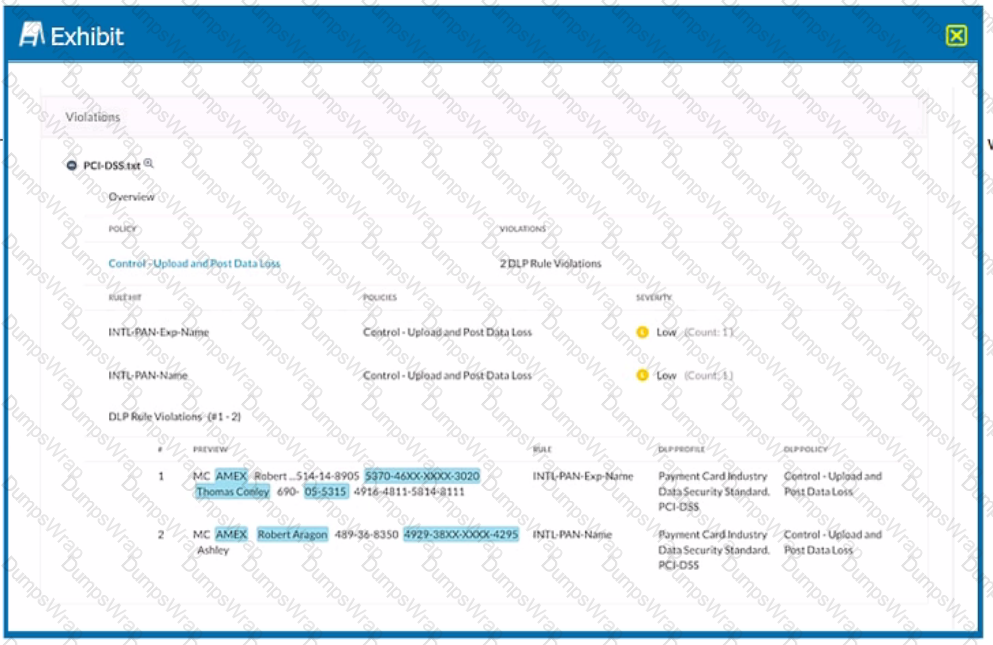
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
You are required to create a policy that will notify and allow users to log into their personal Google Drive instance.
Which two policy components must be configured to enforce this use case? (Choose two.)
You are creating a real-time policy for cloud applications.
In addition to users, groups, and organizational units, which two source criteria would support this scenario? (Choose two.)
Which two cloud security and infrastructure enablement technologies does Secure Access Service Edge (SASE) combine into its unified platform? (Choose two.)
You want to enable Netskope to gain visibility into your users' cloud application activities in an inline mode.
In this scenario, which two deployment methods would match your inline use case? (Choose two.)
Click the Exhibit button.
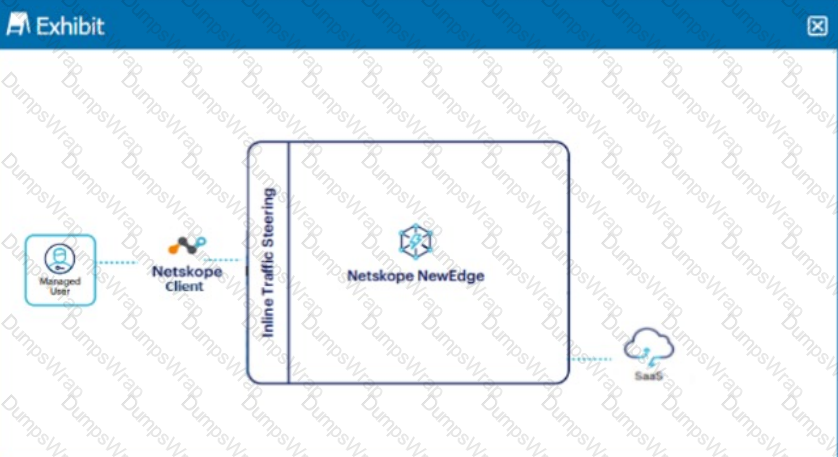
A user is connected to a SaaS application through Netskope's Next Gen SWG with SSL inspection enabled. In this scenario, what information is available in SkopeIT? (Choose three.)
You are required to restrict cloud users from uploading data to any risky cloud storage service as defined by the Cloud Confidence Index. In the Netskope platform, which two policy elements would enable you to implement this control? (Choose two)
You are deploying TLS support for real-time Web and SaaS transactions. What are two secure implementation methods in this scenario? (Choose two.)
Digital Experience Management (DEM) allows an administrator to monitor which two areas? (Choose two.)
What are two characteristics of Netskope's Private Access Solution? (Choose two.)
A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
What information is displayed in an application's Cloud Confidence Index (CCI) page? (Choose two.)
You want to prevent Man-in-the-Middle (MITM) attacks on an encrypted website or application. In this scenario, which method would you use?
Click the Exhibit button.
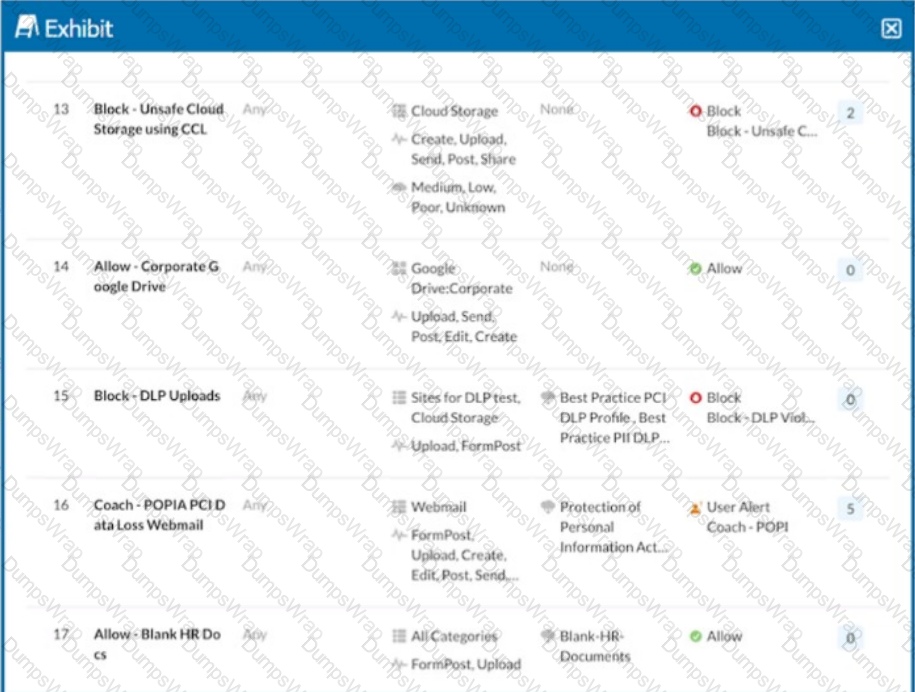
A user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. You notice that the upload is not blocked by the policy shown in the exhibit. Which statement is correct in this scenario?
Which three components make up the Borderless SD-WAN solution? (Choose three)
Which two technologies form a part of Netskope's Threat Protection module? (Choose two.)
Which two functions are available for both inline and API protection? (Choose two.)
There is a DLP violation on a file in your sanctioned Google Drive instance. The file is in a deleted state. You need to locate information pertaining to this DLP violation using Netskope. In this scenario, which statement is correct?
Which two capabilities are part of Netskope's Adaptive Zero Trust Data Protection? (Choose two.)
Which two controls are covered by Netskope's security platform? (Choose two.)
You want to block access to sites that use self-signed certificates. Which statement is true in this scenario?

