Palo Alto Networks Cloud Security Professional Questions and Answers
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud? (Choose two.)
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying.
How should the customer automate vulnerability scanning for images deployed to Fargate?
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
What are the two ways to scope a CI policy for image scanning? (Choose two.)
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
Where can a user submit an external new feature request?
What must be created in order to receive notifications about alerts generated when the operator is away from the Prisma Cloud Console?
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
In Prisma Cloud Software Release 22.06 (Kepler), which Registry type is added?
How often do Defenders share logs with Console?
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
The Compute Console has recently been upgraded, and the administrator plans to delay upgrading the Defenders and the Twistcli tool until some of the team’s resources have been rescaled. The Console is currently one major release ahead.
What will happen as a result of the Console upgrade?
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
The attempted bytes count displays?
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
Console is running in a Kubernetes cluster, and you need to deploy Defenders on nodes within this cluster.
Which option shows the steps to deploy the Defenders in Kubernetes using the default Console service name?
Which three incident types will be reflected in the Incident Explorer section of Runtime Defense? (Choose three.)
What are the three states of the Container Runtime Model? (Choose three.)
An administrator has added a Cloud account on Prisma Cloud and then deleted it.
What will happen if the deleted account is added back on Prisma Cloud within a 24-hour period?
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
Which two filters are available in the SecOps dashboard? (Choose two.)
Which two actions are required in order to use the automated method within Amazon Web Services (AWS) Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose two.)
Which three types of runtime rules can be created? (Choose three.)
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
Given the following audit event activity snippet:
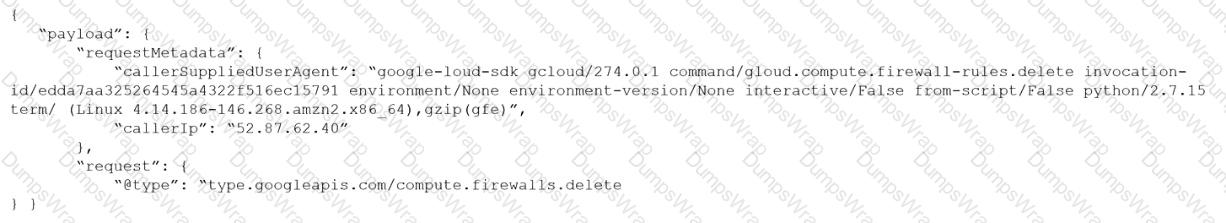
Which RQL will be triggered by the audit event?
A)
B)
C)
D)
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
A Prisma Cloud Administrator onboarded an AWS cloud account with agentless scanning enabled successfully to Prisma Cloud. Which item requires deploying defenders to be able to inspect the risk on the onboarded AWS account?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects.
Which setting does the administrator enable or configure to accomplish this task?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Anomaly policy uses which two logs to identify unusual network and user activity? (Choose two.)
Which container image scan is constructed correctly?
Which two CI/CD plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
What is the reason for the error message?
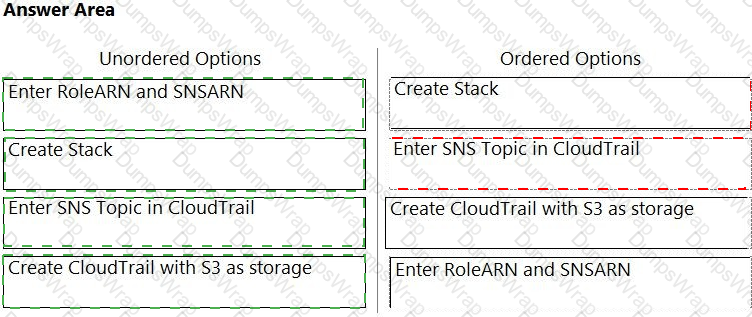
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
A Prisma Cloud administrator is tasked with pulling a report via API. The Prisma Cloud tenant is located on app2.prismacloud.io.
What is the correct API endpoint?
A user from an organization is unable to log in to Prisma Cloud Console after having logged in the previous day.
Which area on the Console will provide input on this issue?
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[? (@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
On which cloud service providers can you receive new API release information for Prisma Cloud?
Which action must be taken to enable a user to interact programmatically with the Prisma Cloud APIs and for a nonhuman entity to be enabled for the access keys?
A DevOps lead reviewed some system logs and notices some odd behavior that could be a data exfiltration attempt. The DevOps lead only has access to vulnerability data in Prisma Cloud Compute, so the DevOps lead passes this information to SecOps.
Which pages in Prisma Cloud Compute can the SecOps lead use to investigate the runtime aspects of this attack?
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
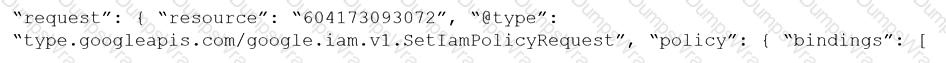
B)
C)
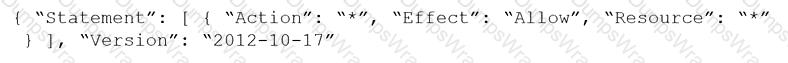
D)

Which two attributes are required for a custom config RQL? (Choose two.)
Which Prisma Cloud policy type can protect against malware?
How are the following categorized?
Backdoor account access Hijacked processes Lateral movement
Port scanning
An administrator sees that a runtime audit has been generated for a host. The audit message is:
“Service postfix attempted to obtain capability SHELL by executing /bin/sh /usr/libexec/postfix/postfix- script.stop. Low severity audit, event is automatically added to the runtime model”
Which runtime host policy rule is the root cause for this runtime audit?
If you are required to run in an air-gapped environment, which product should you install?
Given this information:
The Console is located at The username is: cluster
The password is: password123
The image to scan is: myimage:latest
Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
Which policy type provides information about connections from suspicious IPs in a customer database?
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
An administrator has been tasked with a requirement by your DevSecOps team to write a script to continuously query programmatically the existing users, and the user’s associated permission levels, in a Prisma Cloud Enterprise tenant.
Which public documentation location should be reviewed to help determine the required attributes to carry out this step?
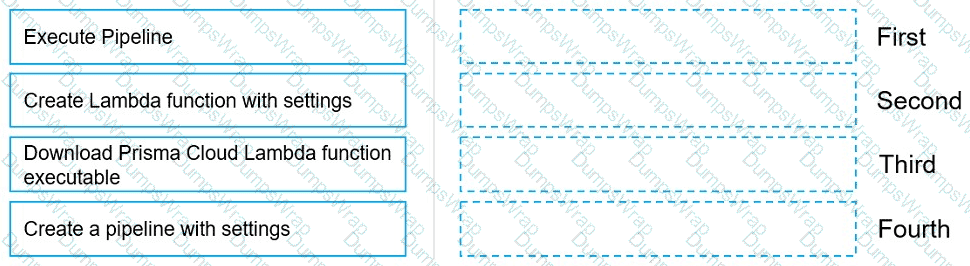
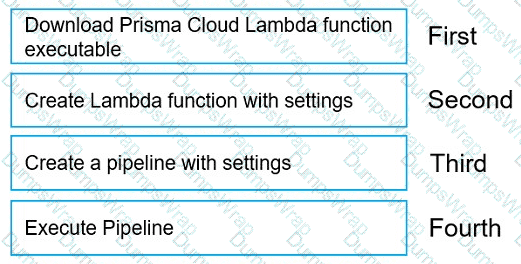
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
Which categories does the Adoption Advisor use to measure adoption progress for Cloud Security Posture Management?
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
What is a benefit of the Cloud Discovery feature?
The administrator wants to review the Console audit logs from within the Console.
Which page in the Console should the administrator use to review this data, if it can be reviewed at all?
Who can access saved searches in a cloud account?
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
What is the primary purpose of Prisma Cloud Code Security?
A customer wants to be notified about port scanning network activities in their environment. Which policy type detects this behavior?
Which two required request headers interface with Prisma Cloud API? (Choose two.)
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
A Systems Engineer is the administrator of a self-hosted Prisma Cloud console. They upgraded the console to the latest version. However, after the upgrade, the console does not show all the policies configured. Before they upgraded the console, they created a backup manually and exported it to a local drive. Now they have to install a Prisma Cloud to restore from the backup that they manually created. Which Prisma Cloud version can they can restore with the backup?
A customer has serverless functions that are deployed in multiple clouds.
Which serverless cloud provider is covered be “overly permissive service access” compliance check?
A customer has a requirement to scan serverless functions for vulnerabilities.
Which three settings are required to configure serverless scanning? (Choose three.)
Which two offerings will scan container images in Jenkins pipelines? (Choose two.)
You are tasked with configuring a Prisma Cloud build policy for Terraform. What type of query is necessary to complete this policy?
Which three AWS policy types and identities are used to calculate the net effective permissions? (Choose three).
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
On which cloud service providers can new API release information for Prisma Cloud be received?
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)


 Graphical user interface, text, application Description automatically generated
Graphical user interface, text, application Description automatically generated