Palo Alto Networks Cybersecurity Practitioner (PCCP) Questions and Answers
In SecOps, what are two of the components included in the identify stage? (Choose two.)
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
Which two descriptions apply to an XDR solution? (Choose two.)
Which aspect of a SaaS application requires compliance with local organizational security policies?
What type of address translation does a NAT perform?
Which SOAR feature coordinates across technologies, security teams, and external users for centralized data visibility and action?
Why is it important to protect East-West traffic within a private cloud?
What are three benefits of the cloud native security platform? (Choose three.)
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
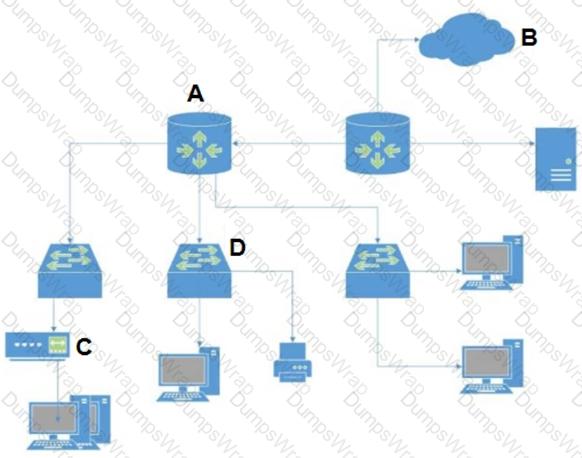
In the attached network diagram, which device is the switch?
What is an event-driven snippet of code that runs on managed infrastructure?
Under which category does an application that is approved by the IT department, such as Office 365, fall?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
Which of the following is a Routed Protocol?
Which product functions as part of a SASE solution?
Which IPsec feature allows device traffic to go directly to the Internet?
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
Which of these ports is normally associated with HTTPS?
What type of attack redirects the traffic of a legitimate website to a fake website?
What is an advantage of virtual firewalls over physical firewalls for internal segmentation when placed in a data center?
Which feature of cloud-native security platforms (CNSPs) focuses on protecting virtual machine (VM), container, and serverless deployments against application-level attacks during runtime?
Which option is an example of a North-South traffic flow?
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
Organizations that transmit, process, or store payment-card information must comply with what standard?
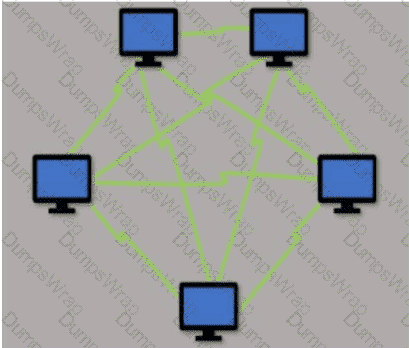
Which type of LAN technology is being displayed in the diagram?
TCP is the protocol of which layer of the OSI model?
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
Which security component can detect command-and-control traffic sent from multiple endpoints within a corporate data center?
Which of the following is an AWS serverless service?
Which option is a Prisma Access security service?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
What is the purpose of host-based architectures?
Which two workflows are improved by integrating SIEMs with other security solutions? (Choose two.)
Which network firewall primarily filters traffic based on source and destination IP address?
What is a characteristic of the National Institute Standards and Technology (NIST) defined cloud computing model?
Which native Windows application can be used to inspect actions taken at a specific time?
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
Which type of malware replicates itself to spread rapidly through a computer network?
Which component of the AAA framework verifies user identities so they may access the network?
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?
Which type of attack obscures its presence while attempting to spread to multiple hosts in a network?
What is a key benefit of Cortex XDR?
An administrator finds multiple gambling websites in the network traffic log.
What can be created to dynamically block these websites?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
What type of area network connects end-user devices?
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
How can local systems eliminate vulnerabilities?
What are two limitations of signature-based anti-malware software? (Choose two.)
What is the function of an endpoint detection and response (EDR) tool?
Which Palo Alto Networks solution has replaced legacy IPS solutions?
What are two capabilities of identity threat detection and response (ITDR)? (Choose two.)
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Which component of cloud security is used to identify misconfigurations during the development process?
What does “forensics” refer to in a Security Operations process?
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
Which type of system collects data and uses correlation rules to trigger alarms?
Which technology helps Security Operations Center (SOC) teams identify heap spray attacks on company-owned laptops?
What are three benefits of SD-WAN infrastructure? (Choose three.)
Which tool supercharges security operations center (SOC) efficiency with the world’s most comprehensive operating platform for enterprise security?
Which three services are part of Prisma SaaS? (Choose three.)
Which two network resources does a directory service database contain? (Choose two.)
Which capability does Cloud Security Posture Management (CSPM) provide for threat detection within Prisma Cloud?
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?

