Palo Alto Networks System Engineer Professional - Strata Questions and Answers
A customer has business-critical applications that rely on the general web-browsing application. Which security profile can help prevent drive-by-downloads while still allowing web-browsing traffic?
What are two presales selling advantages of using Expedition? (Choose two.)
What are three sources of malware sample data for the Threat Intelligence Cloud? (Choose three)
When HTTP header logging is enabled on a URL Filtering profile, which attribute-value can be logged?
In an HA pair running Active/Passive mode, over which interface do the dataplanes communicate?
Which built-in feature of PAN-OS allows the NGFW administrator to create a policy that provides autoremediation for anomalous user behavior and malicious activity while maintaining user visibility?
A customer is looking for an analytics tool that uses the logs on the firewall to detect actionable events on the network. They require something to automatically process a series of related threat events that, when combined, indicate a likely compromised host on their network or some other higher level conclusion. They need to pinpoint the area of risk, such as compromised hosts on the network, allows you to assess the risk and take action to prevent exploitation of network resources.
Which feature of PAN-OS can you talk about to address their requirement to optimize their business outcomes?
Prisma SaaS provides which two SaaS threat prevention capabilities? (Choose two)
Which three settings must be configured to enable Credential Phishing Prevention? (Choose three.)
What are two benefits of the sinkhole Internet Protocol (IP) address that DNS Security sends to the client in place of malicious IP addresses? (Choose two.)
Access to a business site is blocked by URL Filtering inline machine learning (ML) and
considered as a false-positive.
How should the site be made available?
Decryption port mirroring is now supported on which platform?
Which profile or policy should be applied to protect against port scans from the internet?
Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
A)

B)

C)
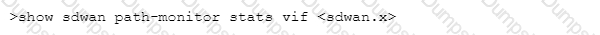
D)
Which four steps of the cyberattack lifecycle does the Palo Alto Networks Security Operating Platform prevent? (Choose four.)
A packet that is already associated with a current session arrives at the firewall.
What is the flow of the packet after the firewall determines that it is matched with an existing session?
A customer is designing a private data center to host their new web application along with a separate headquarters for users.
Which cloud-delivered security service (CDSS) would be recommended for the headquarters only?
in which step of the Palo Alto Networks Five-Step Zero Trust Methodology would an organization's critical data, applications, assets, and services (DAAS) be identified?
Which three components are specific to the Query Builder found in the Custom Report creation dialog of the firewall? (Choose three.)
When having a customer pre-sales call, which aspects of the NGFW should be covered?
Match the functions to the appropriate processing engine within the dataplane.

Which CLI command allows visibility into SD-WAN events such as path Selection and path quality measurements?
For customers with high bandwidth requirements for Service Connections, what two limitations exist when onboarding multiple Service Connections to the same Prisma Access location servicing a single
Datacenter? (Choose two.)
Which two components must be configured within User-ID on a new firewall that has been implemented? (Choose two.)
As you prepare to scan your Amazon S3 account, what enables Prisma service permission to access Amazon S3?
What are two benefits of using Panorama for a customer who is deploying virtual firewalls to secure data center traffic? (Choose two.)
Which solution informs a customer concerned about zero-day targeted attacks whether an attack is specifically targeted at its property?
Which component is needed for a large-scale deployment of NGFWs with multiple Panorama Management Servers?
A customer requests that a known spyware threat signature be triggered based on a rate of occurrence, for example, 10 hits in 5 seconds.
How is this goal accomplished?
Which two network events are highlighted through correlation objects as potential security risks? (Choose two.)
A price-sensitive customer wants to prevent attacks on a Windows Virtual Server. The server will max out at 100Mbps but needs to have 45.000 sessions to connect to multiple hosts within a data center
Which VM instance should be used to secure the network by this customer?
An administrator wants to justify the expense of a second Panorama appliance for HA of the management layer.
The customer already has multiple M-100s set up as a log collector group. What are two valid reasons for deploying Panorama in High Availability? (Choose two.)
How frequently do WildFire signatures move into the antivirus database?
Which three actions should be taken before deploying a firewall evaluation unt in a customer environment? (Choose three.)
Which two types of security chains are supported by the Decryption Broker? (Choose two.)
Which statement applies to Palo Alto Networks Single Pass Parallel Processing (SP3)?
What are the three possible verdicts in WildFire Submissions log entries for a submitted sample? (Choose four.)
An SE is preparing an SLR report for a school and wants to emphasize URL filtering capabilities because the school is concerned that its students are accessing inappropriate websites. The URL categories being chosen by default in the report are not highlighting these types of websites. How should the SE show the customer the firewall can detect that these websites are being accessed?
Which three methods used to map users to IP addresses are supported in Palo Alto Networks firewalls? (Choose three.)
What are three key benefits of the Palo Alto Networks platform approach to security? (Choose three)
What is the recommended way to ensure that firewalls have the most current set of signatures for up-to-date protection?


