CrowdStrike Certified Falcon Responder Questions and Answers
What happens when you create a Sensor Visibility Exclusion for a trusted file path?
Which of the following is NOT a filter available on the Detections page?
The function of Machine Learning Exclusions is to___________.
What happens when a quarantined file is released?
In the "Full Detection Details", which view will provide an exportable text listing of events like DNS requests. Registry Operations, and Network Operations?
When reviewing a Host Timeline, which of the following filters is available?
What does pivoting to an Event Search from a detection do?
When examining a raw DNS request event, you see a field called ContextProcessld_decimal. What is the purpose of that field?
What happens when a hash is allowlisted?
You receive an email from a third-party vendor that one of their services is compromised,thevendor names a specific IP address that the compromised service was using. Where would you input this indicator to find any activity related to this IP address?
What are Event Actions?
Which Executive Summary dashboard item indicates sensors running with unsupported versions?
From the Detections page, how can you view 'in-progress' detections assigned to Falcon Analyst Alex?
Which option indicates a hash is allowlisted?
Within the MITRE-Based Falcon Detections Framework, what is the correct way to interpret Keep Access > Persistence > Create Account?
Aside from a Process Timeline or Event Search, how do you export process event data from a detection in .CSV format?
When looking at the details of a detection, there are two fields called Global Prevalence and Local Prevalence. Which answer best defines Local Prevalence?
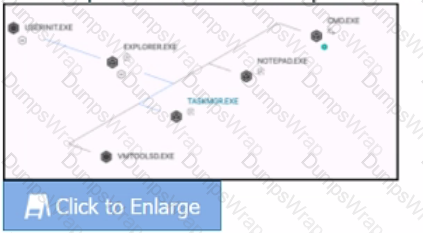
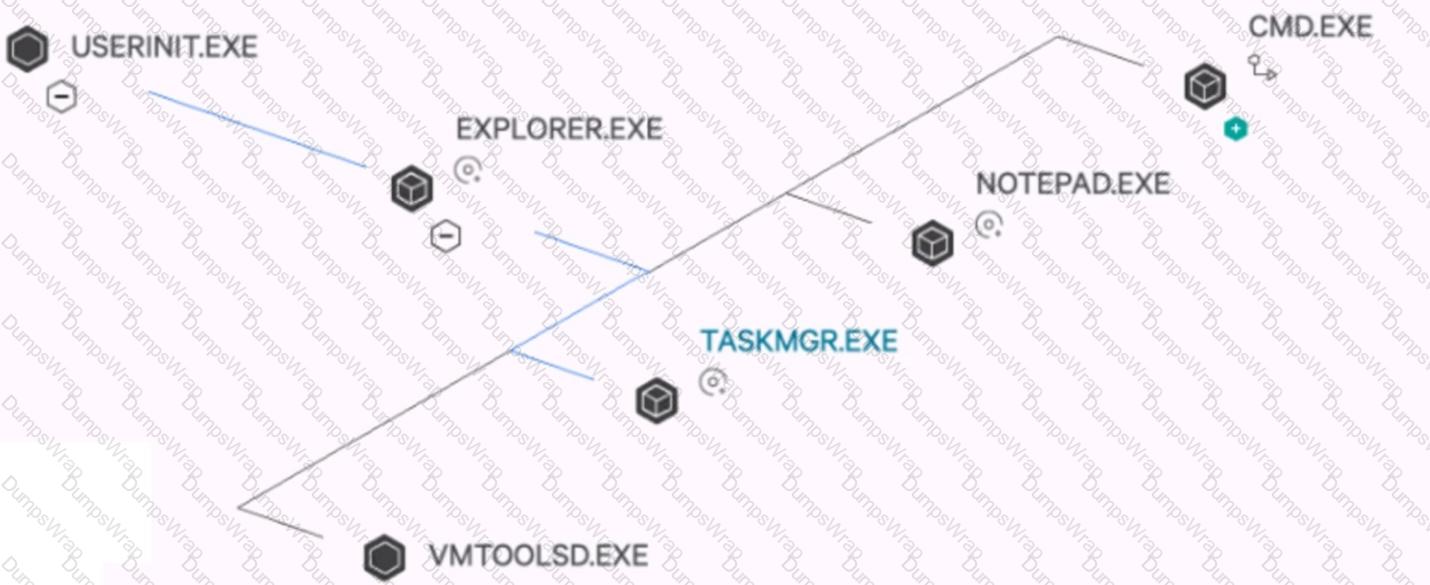
How are processes on the same plane ordered (bottom 'VMTOOLSD.EXE' to top CMD.EXE')?